BackSwap, a new banking trojan discovered.
This newly discovered malware uses highly sophisticated and innovative methods to empty victim’s bank account.
It employs several new techniques to bypass the firewall of the system.
These days banking malware attacks are evolving with various techniques. Such malware endlessly targets victim’s bank account which makes the prevention more and more complex.
BackSwap trojan evolves in regards to the regular complex process used to infect a system.
It uses newly innovated methods for infecting the browser and monitoring browsing activities.
Attackers accomplish their end goal by injecting the malicious JavaScript into the web page either through the address bar or via the JavaScript console.

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
Fascinatingly all of the operations are being carried on with the user’s consent. This is how the malware developers evade the detection and maintain the persistence from the victim’s side.
This is deceptively a basic trick considering all the advanced browser protection mechanisms against such attacks.
BackSwap Trojan exposed as Win32/BackSwap.A has had malicious scripts aiming at five Polish banks altogether– Bank Zachodni WBK S.A., mBank, PKO Bank Polski, Pekao and ING.
This banking Trojan is being distributed by the same criminal group which is behind the Malware that steals cryptocurrency.
How does this banking Trojan vacate bank accounts?
To begin with its distribution technique, it runs multiple spam campaigns to distribute a malicious email with heavily obfuscated JavaScript downloader as an attachment to it.
After the trojan has been pushed into the targeted system, the payload is dropped via a malicious version of the legitimate application and it will be overwritten by the payload.
This Malware exploits genuine applications such as SQLMon, TPVCGateway, WinRAR Uninstaller, DbgView, OllyDbg, 7Zip, FileZilla Server – to accomplish its malicious deeds.
This BackSwap Malware uses fake internet banking interface to steal money from a victim’s account.
Malware developers are using dedicated methods and patterns that only work for a definite version of the browser due to the complications of exporting the function in various browsers to manipulate users browsing activities.
once the BackSwap Banking Trojan finds the required function and triggers it successfully, the malware then begins to modify the HTTP traffic or redirect the victim to a different website imitating a bank while faking the validity of a certificate.
Malware developers use hacked WordPress website as a Command and Control Center to retrieve the receiving bank account numbers.
The attacker will only steal money if the wire transfer amount is in a certain range – they usually target payments between 10,000 and 20,000 PLN, which is around 2,800 – 5,600 USD.
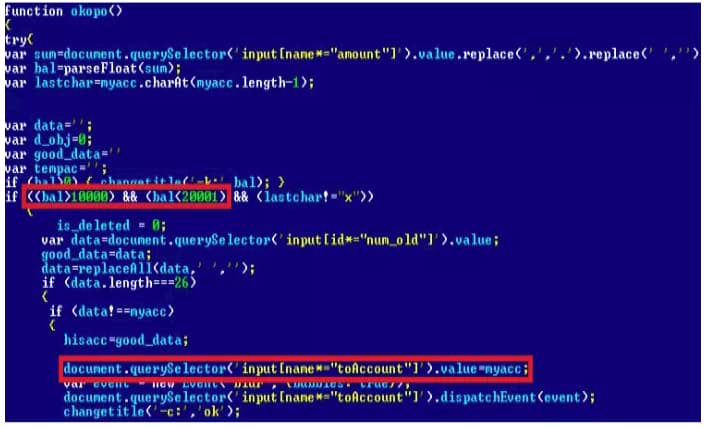
In this case, the same technique used by other sophisticated banking trojans like Ursnif, Dridex, Trickbot, and many others.
IoCs

Are you worried about your PC health?
Check your PC Health for Free!
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
