The Browlock ransomware (Trojan.Ransomlock.AG) is likely the simplest adaptation of ransomware that is presently dynamic.
It doesn't download child abusive material, for example, Ransomlock.AE, or encode documents on your PC, as Trojan.Cryptolocker. It doesn't run in the background as a program on the compromised PCs. This ransomware is rather a plain old Web page, with JavaScript traps that keep users from shutting down a specific tab on their browser.
It tracks the user's location and makes the standard threat, saying that the user has violated the law by getting to smut sites and orders that they pay a fine to the local police.
What is considerable are the number of users getting diverted to the Browlock site. In November, Symantec blocked more than 650,000 redirects to the Browlock's target website.
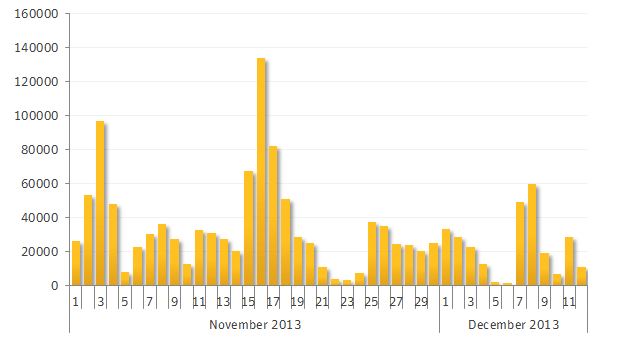
A similar pattern proceeds in December. More than 220,000 redirects were blocked in just 11 days. Altogether, around 1.8 million redirects have been terminated since trailing commenced in September.
ALSO READ: HOW TO REMOVE BACKDOOR.TEAMVIEWER TROJAN VIRUS FROM COMPUTER
These numbers may not appear to be especially huge for those familiar with traffic redirection operations and exploit kits, however, they exclusively speak to Symantec users. The 650,000 redirects identified in November is just a fraction of the pie, however, the genuine number is presumably going to be considerably bigger.
The preceding figures demonstrate the measure of movement identified every day. The attacks happened in waves, with two especially recognizable tops on November 3 and November 16. On November 16, somewhere around 130,000 PCs were hindered from being redirected to the Browlock site.
How do they hit?
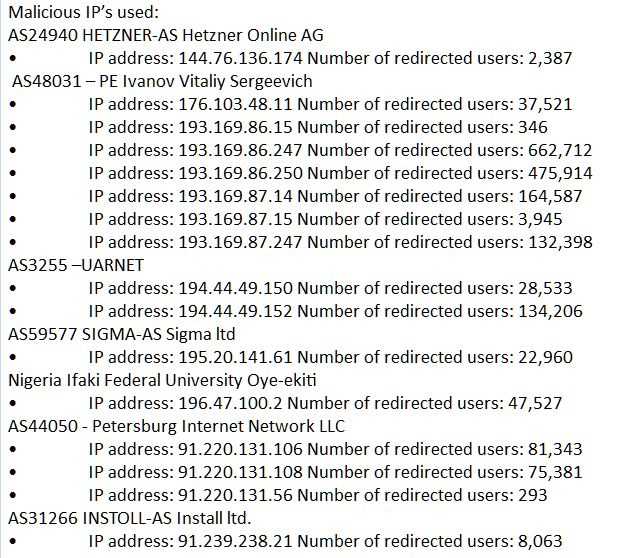
These hackers appear to be purchasing traffic that redirects users to their malicious website. They are utilizing malvertising, an inevitably even approach which includes purchasing advertisements from legitimate networks.
The ad is coordinated to what has all the earmarks of being an adult Website, which at that point redirects to the Browlock site.
The traffic that the Browlock developers purchased comes from several different sources, but the majority of traffic is redirected from adult advertising networks. Many security experts have been working on tracking its activity from last few months, notably Malekal and Dynamoo.
Structure of Browlock
At the point when a user is redirected to the Browlock site, a URL specific to the victim and their country’s law enforcement is generated.
Summary
The Browlock ransomware strategy is basic however viable. hackers save money by not utilizing a malevolent executable or getting to an exploit kit.
As the casualty essentially needs to close their program to escape from the Web page, one may imagine that nobody will pay up.
In any case, the Browlock developers are unmistakably burning through cash to buy traffic thus they should make be making a profit from that.
The typical ransomware strategy of centering users of porn sites keeps on profiting from a victim's embarrassment and may account for the success rate.
ALSO READ: HOW TO REMOVE CLEAN GRILL GRATES ADWARE FROM COMPUTER
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update. By doing this you can keep your device free from virus. According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection. Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like McAfee or a good Malware Removal Tool like Download Free Virus RemovalTool
- Install a powerful ad- blocker for Chrome, Mozilla, and IE.
