What is CryptoLocker?
CryptoLocker is a ransomware infection which was first seen in 2013. A year after, a body of researchers figured out how to control and stop this infection by locking down its major suppliers — the Game over Zeus botnet. From that point forward, the first venture was, however, to be dead, yet different CryptoLocker versions have been developing.
Things being said that CryptoLocker the worst nightmare to the Web Community is coming back to reality to regain its position among the most dangerous ransomware. Put together those cyber criminals who are in charge of discharging it may be out of their 3-million-dollar profit.
By any chance, if you believe that your computer could be infected with this infection, do not hesitate to eliminate CryptoLocker. This is the most straightforward approach to end its movement on your operating system. If you let this malware remain on your PC, this ransomware can cause significantly more harm by encoding another bit of your documents. Since quite possibly this infection is back online, we highly recommend you to run a full system scan with malware removal tool.
How does CryptoLocker function?
The principal objective of a CryptoLocker ransomware is to evade your computer's firewall. And to achieve that, malware depends on the email messages that pretend to be legit or from a known party. These emails contain malicious programs, attached to it is the actual payload of ransomware. Once the user is fooled into opening it, the infection enters the targeted PC, then it encrypts the victim's data and leaves a ransom note on the screen.
Regardless of that, it is a twin to belongs to the same category as Department of Justice virus or Police Central e-crime Unit virus and FBI virus, and this infection tries to persuade its casualties that they need to pay a ransom amount by encrypting their systems data. CryptoLocker is the file-encrypting ransomware, so it utilizes RSA public key cryptography to bolt the victim's data of these following extension type:
exe, XLS, DOCX, 3fr, bay, crw, xlk, xlsm, pem, docm, dwg, ods, pptm, pef, ptx, xlsx, r3d, dxg, indd, mef, odb, ppt, p7c, p12, orf, odm, xlsb, raf, r3d, jpg, cr2, pdd, ods, xlsb, wpd, p7b, ods, wps, wb2, wpd, srw, rwl, r3d, srf, rw2, rtf, accdb, arw, docm, ai, cdr, pdd, mef, mdf, kdc, jpeg, mrw, ODP, nrw, erf, nef, pdf.
As should be obvious, this rundown is cramming the broadly utilized file types, for example, doc, exe, XLS and other comparative extension types. To restore and decrypt the user's data this ransomware demands a ransom to be paid through Money Pak, Ukash, cashU, or Bitcoin. Commonly, this threat would ask from $100 to $500, yet the cost can be raised at any point shortly.
The ransom note has a clear warning which says if the victim fails to pay the ransom in the allowed time then the decryption key would be destroyed, and the user would stand no chance to retrieve the wasted data.
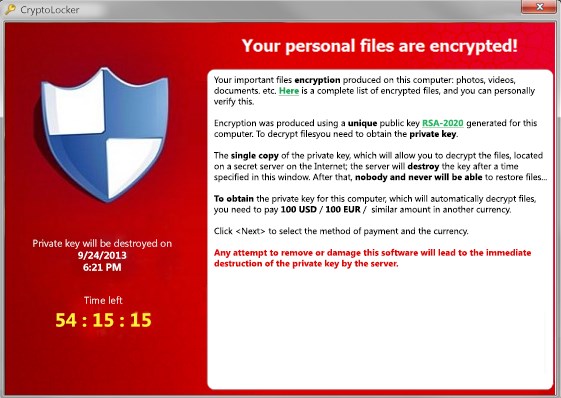
Below you can see one of the ransom note.
Your records are now encrypted!
[All your necessary files present in the computer is now compromised: Videos, images, and other documents. Here you can verify the list of encrypted documents.
Encryption is carried through a unique public key RSA-2048 which was explicitly generated for this computer. To gain the control of your files, you need to buy the decryption key.
The only copy of your decryption key that will help you decrypt your files is located in the secret server. The key would be destroyed in the specified time. After which, nobody or no one can help you to recover your files
To obtain the decryption key of this computer that will automatically decrypt the files you have to pay [a specific ransom in EUR or USD].
Click To select the method of payment and the currency.
Any attempt you make to close or remove the encryption will immediately destroy the decryption key.]
Luckily, CryptoLocker cannot hurt those individuals who have been going down their information and making additional backups of their documents. If you have a backup of your photographs, business records, and different documents, you don't have to pay a payment. You simply need to expel this ransomware from your PC and stay away from further damages.
To eliminate CryptoLocker, we wholly suggest you utilize malware removal tool, which has been confirmed incredible outcomes while taking out such infection from the system. To gain control of your files again, we kindly ask you to go through the removal guide by the end of the article.
Nevertheless, it appears that hackers in their new update have made few changes in favor of those victims who cannot pay the ransom. Now a user can use an Antivirus and an Antimalware program to get rid of the ransomware, and then they no longer have to pay the ransom.
However, this newly introduced feature is only to be used when you have made up your mind to lose all your data. Here, in this case, once your computer is infected with the ransomware the wallpaper of your computer changes, and the Antivirus comes up with a warning to fix it. In such case, either by using the Antivirus, you get rid of the ransomware and lose all your data or pay the ransom to get the decryption key.
Despite the fact that we highly suggest not paying the ransom, we understand that a few organizations would not have the capacity to get by without the information that has been put away on the encrypted PCs, so unfortunately in such cases, paying the ransom will be the only option to advance the business. Also, we can just advice you to not pay the amount. Remember that you can never make sure whether criminals would give you a working decryption tool or key.
Also See:
Anti Malware : Read More About What Is Malware and How To Use Anti Malware To Remove All kinds Of Malware.
How does Ransomware spread?
Among all the crypto-ransomware CryptoLocker is considered as one of the most effectively circulated ransomware. Talking about its distribution, we would like to state that developers of this infection adapt few unique methods to spread the virus. It has been seen that they utilize both old and new distribution procedures, neglecting to conform to any ethical standards.
As indicated by specialists, CryptoLocker infection is broadcasted using formal resembling emails, bogus pop-ups, and other similar methods. Earlier, ransomware had been distributed through offensive email letters that contained malicious attachments, malware-loaded promotions, which promote software or updates that certainly contains the payload of the infection, or exploit kits, which enables criminals to infect user's PCs by misusing their PCs vulnerabilities.
Be careful that this risk can evade your PC through a false pop-up that recommends that you need to update your Flash player, Java or any such program, so reassure you install such software from their authentic websites, not from some suspicious third-party sites.
On September 2016, a few new ransomware distribution strategies were been spotted. The first depends on malicious email messages acting like letters from electricity provider VERBUND. This organization isn't connected with these con artists in any manner – they simply utilize a trustworthy organization's name to persuade users to tap on the malicious emails, attachments or open persuasive email attachments containing CryptoLocker ransomware.
Subject used by the distributors is Detailaufstellung zu Rechnung Nr. [numbers].BY any chance if you have received any such mail, erase it instantly without tapping on any links mentioned in the body of the mail or before downloading any attachments
The second ransomware distribution technique that has been found is an offensive and frightful approach to trap the user and force them to open the malicious document containing the infection. Con artists act like workers of human services organizations and send tricky messages that can put a user in the worst of the situations. They convey a false blood test report, expressing that the casualty may be experiencing the ill effects of cancer because of the absence of white platelets.
The message requests to print out the blood test that is in an attached report and convey these to the family doctor ASAP. Such news can influence anybody to frenzy, and drive them to open the attached report without feeling this could be a scam. At the point when the victim opens the attachment, the ransomware takes control over the system and encrypts every document in the victim’s PC without any regret. As should be obvious, cyber thieves can go low since all they think about is money.
Read More About Search Encrypt Virus
How to protect the data from being encrypted?
Remain safe, and you ought to never trust misleading promotions that put on a show to be useful because the main thing what they do is spread infections and other malicious programs. Likewise, ensure you erase spam and double check each email that was sent to you by some random sender. Additionally, bear in mind to disable hidden extensions (if you are utilizing Windows OS). And to maintain a strategic distance from the loss of your records, you should consider getting a security software for your computer.
The principal thing that you must do is to download a reliable Antivirus and Antimalware software for your PC. We suggest utilizing Free malware removal tool. What's more, ensure you perform reinforcements as frequently as conceivable because this could help you to recover your encrypted records. Eventually, you should utilize the cloud storage, i.e., Google Drive, Dropbox, Flickr, etc. - this assures the security of your files. Nonetheless, remember this powerful infection may have the ability to get to these cloud storages using your computer and your IP address.
Hence, it is recommended that you make the back up of all your data at least back up your extremely important files and store them in a removable storage device like hard drives and USB sticks. Unfortunately, just by any chance if your PC is infected with this ransomware at present, you should realize that there is no official CryptoLocker decrypter tool yet. Further, you can check the guide given below by the end of this post and secure your device with a robust firewall. Keep in mind to expel ransomware before copying your documents back to the computer since it might encrypt them once more!
Viruses that are linked to CryptoLocker:
- CryptoLocker infection is one of document encrypting ransomware's that has a potential to evade PCs firewall through bogus Java updates or through malicious email attachments. Once the user's data is encrypted, this infection adds. encrypted or .enc extension to each of them and begins to display a ransom message demanding ransom from the victim.
This infection was first seen in 2015. But, after a long time, it is still currently infecting computers. Crypt0l0cker 2017 variant requests 2.2 Bitcoin for allowing the victim to get their files decrypted. Kindly, don't pay the payment and utilize a guide beneath to settle your PC. You can simply regain your documents from the back up for nothing.
- CryptoLocker-v3 This ransomware would infect your computer through bogus pop-ups or through infected links or at times you would see alerts asking you to update your Flash Player or Java plugin. Once your computer is infected with this ransomware it would block most of your data.
For encrypting the documents, this threat utilizes RSA-2048 (a unique public key) and asks 1 BTC ransom which is equivalent to $350 US dollars in 2015. Making this installment is the same as supporting the hackers and their future criminal activities, so you ought to never do that. This malware utilizes. crypted record technique which is added to each document it encrypts.
- Cryptographic Locker is basically the same as CryptoLocker ransomware. It tells its victim what records are encrypted by including .clf file extension to all the document it encrypts. Every one of these documents are saved in %Temp%\CryptoLockerFileList.txt. Directly after showing up on the Internet, this ransomware will ask 0.2 BTC ransom in return for the decryption key which is required for regaining access to your files.
In the middle of its dynamic circulation, the measure of installment was proportional to $100. In any case, likewise, all know, the cost of bitcoins keeps advancing. If you realize that your PC is infected with this malware, kindly, don't pay the fine because there is no assurance that this will help you recover your encrypted data. Instead of doing what they say, you must use the guide underneath to secure your data in build a strong firewall.
- PCLock ransomware is another ransomware that tries to frighten its casualties by encoding their records. This technique is commonly originated with the support of XOR encryption. Luckily, it isn't as forceful as the first CryptoLocker variant, so your computer should have an Antivirus software to remove its primary file WinCL.exe.
Kindly, don't pay one bitcoin ransom which is required to be paid in the ransom note called last_chance.txt for unblocking encoded documents. To eliminate this threat and create a robust firewall, you need to follow the removal guide below.
- CryptoTorLocker2015 is capable of infecting Windows OS and Android OS. When it does that, it utilizes XOR encryption for corrupting casualty's documents. On the off chance that your system is loaded with valuable photographs or business documents, you can lose them. Infected documents are blocked by marking them to .CryptoTorLocker2015 file extension. You might also find the ransom note named as "FOLLOW TO DECRYPT.txt" on your PC.
Luckily, Android users just have to uninstall the infected application, which was used by CryptoTorLocker to infect their device, to delete this infection from their gadgets. Windows users are suggested to utilizing trustworthy Antivirus and Antimalware software for CryptoTorLocker2015 expulsion.
- Crypt0 ransomware found in September 2016, this ransomware version additionally endeavors to utilize a piece of CryptoLocker's name to appear to be scarier than it is. This adaptation adds ._crypt0 extension after the real file name renaming its original extension, while other infections add the extension name after actual file extension.
This ransomware leaves a ransom note named "HELP_DECRYPT.txt," which informs the victims about the infection and gives the only option to utilize contactfndimaf@gmail.com for further details to decrypt the computer. This infection is a stupid duplicate of CryptoLocker and can be eliminated just by using the Antivirus and Antimalware programs.
- Il tuo PC e stato infettato da CryptoLocker! Ransomware This infection is yet another variant of CryptoLocker which is developed for Italian-speaking PC users. This version of ransomware demands less ransom compared to the other ransomwares– it asks for 130 euro from its victims. In any case, that does not imply that the user must pay the payment.
Just like all the other ransomware this ransomware also changes file extensions (it utilizes .locked file extension) and gives its casualty a predefined time duration to pay the ransom. As of now, Antimalware experts have nothing to say on the decryption tool as it has not been developed yet. However, the developments are under process. Meanwhile, you can secure your secure your computer by creating a firewall using Antivirus and Antimalware program before the ransomware hits your computer.
- CryptoLocker 5.1 ransomware: This ransomware has been released in 2016. Since its first appearance, it has been chipping away at infecting Italian PC users. On the other hand, it has been then again known as Il tuo PC e stato infettato da CryptoLocker! infection. In spite of the fact that it endeavors to mask under the name of famous digital threat, IT researchers still speculate that it isn't so intense as the first form.Talking about the present infection, it affixes .locked file extensions and requests 250€ in return for the decoding key. The exchange is to be made within 48 hours. Leave all the thoughts behind to exchange the cash and focus on its elimination.
- CryptoLocker3 ransomware is an imposter kind of malware which can likewise be called as lock screen ransomware. Such infections don't really encrypt the documents on the PC yet keep the users from getting to them and utilizing the standard PC function. However, in the new updates, CryptoLocker3 entered another level in which this malware acts like the original ransomware.This infection utilizes XOR encryption algorithm and adds .CryptoLocker file extensions. There is as of now no tool available to decrypt the bolted data, yet we can guarantee you that the experts are taking a shot at it effectively and you can expect that your records will be decrypted later on. In the meantime, you have to eliminate this malware from your PC immediately.
- MNS CryptoLocker is yet another ransomware which utilizes CryptoLocker's name. While there is no proof that it is associated with the wicked ransomware, it doesn't imply that this malware is less threatening. Once the ransomware encrypts the user's data, it drops a ransom note demanding that the victim send 0.2 BTC (USD $180) through Tor or different unidentified networks.This Infection does not add any new extension to the target documents, so the only way you would notice the infection on the computer is when you open the infected document. Shockingly, this malware can wipe out shadow volume duplicates of the target files with the extraordinary command known as vssadmin DELETE SHADOWS/all/quiet. On account of this feature, casualties discover Shadow Explorer pointless. The most intriguing truth is that MNS CryptoLocker can erase itself from the system.
- CryptoLockerEU ransomware was first seen in January 2017. It gives off an impression of being an improved duplicate of the already existing CryptoLocker infection. The infection calls itself CryptoLockerEU 2016 rusia, which gives a thought that it was produced in 2016 by Russian programmers. During the data encryption method, the infection encrypts records utilizing an RSA-2048 algorithm and provides each document with another extension .send 0.3 BTC sepulcher.The name of the payoff note looks somewhat like this: ???????????? ?????.txt. However, due to an error in infection's source code, it shows up as Ðrnrcôdî Rnü Ôréëu.txt. Right now, documents can't be decrypted. Casualties should utilize backup or sit tight with the expectation of complimentary decoding programs that malware scientists may discharge soon.
- CryptoLocker Portuguese ransomware or CryptON is the most recent variation of CryptoLocker-related ransomware. Some believe that it might be distributed by the same group of hackers since it uses a source code that resembles same as the original CryptoLocker.The interesting truth is that this infection has targeted Portuguese-speaking users since the ransom note and the payment installment interface are displayed in the same language. Specifically, the ransom note adopted by this malware is called COMO_ABRIR_ARQUIVOS.txt which primarily signifies "how to get to your records" in English. Likewise, the scrambled records are renamed in an accompanying way: [file_name].id-[victim's ID]_steaveiwalker@india.com_.
To gain the control back to the infected or encrypted files, the casualties are requested to pay 1 BTC. Do not hold on to the thought of paying the hackers. Instead, eliminate CryptON ransomware and attempt to retrieve your files using our recommended techniques.
FREQUENTLY ASKED QUESTIONS (FAQ)
- Question: CryptoLocker ransomware has contaminated my PC. The infection has additionally moved to my SD memory card in which I've some of my pictures. Now, I'm getting a notice saying that I have a specific time to pay the ransom. However, there is no particular period specified. Does anyone know to what extent documents stay accessible to recover after they are affected by ransomware?
Answer: We would like to inform the people who have the ransom note and to all the other people. You can never be sure that paying the ransom would get you a decryption key. However, you can face considerable money and data loss.The first thing you to do after getting the ransom note is to run a complete system scan if you still have the control of your computer using a reputed Antivirus and Antimalware removal software. After that verify if you can access your files if you find that your files are still locked then follow the removal guide below.
- Question: I've been hit by CryptoLocker ransomware twice! The second time was different, and I think it was a different version. Although, could you please tell me how could I prevent this in future? It's painful to pay $500 to these bastards every time. However, the only option that worked was to pay them. It would be appreciated if you could advise something.
Answer: It's a pity to hear that you have been assaulted by ransomware twice. We believe that the reason behind a rehashed assault may be improper CryptoLocker elimination. Anyway, now you are requesting that how to shield your PC from this threat. Honestly, there is no hundred percent reliable technique that would give you zero odds against any ransomware.
But, these are the few steps you could follow to secure your computer.
1. Keep distance from the illegal third-party websites.
2. Do not open any suspicious emails try to confirm the sender before opening such emails.
3. Your web browser may redirect your searches to alerts asking you for an update do not click on them as they are nothing but bogus pop-ups
4. Try not to view the websites with adult content 5. Finally, but the best way to stand a chance against any ransomware is to install a good Antivirus and a reputed malware removal software.
3. Question: I was browsing through the regular websites, and suddenly I saw a pop-up stating that your windows has been locked and all your data is now encrypted and that I have to pay the ransom to get the control back to my windows. Was this a joke or I have to pay $500 to throw away this ransomware.
Answer: Unfortunately, if CryptoLocker ransomware has brought the message that you've indicated, then possibly your computer is infected by ransomware. Presumably, you might have already checked some of the files stored on your computer is now blocked. Although, Paying the ransom does not assure that you all the encrypted data would be free from the infection.
Even though, some users claim to have received the decryption key after paying the ransom. But there is no guarantee that they would provide any key or by any chance if they do it doesn't mean that it would work for everyone.
Therefore, rather than spending your money for nothing, it is better that you install Antivirus and a malware removal tool and get rid of the infection first. About the lost files the researchers are still working on it once something is out we would update you on the same.
4. Question: Please help! My records were bolted by CryptoLocker infection the previous evening, and I constantly get a notice that contains guidelines how to make the installment. I feel defenseless as I can't stand to pay such a big amount of money despite the fact that photos put away on my PC are worth millions for me. Would anyone be able to offer assistance?!
Answer: CryptoLocker ransomware is an awful infection. The only objective was to scare the users and demand money from them. For you, and additionally, for other casualties of this ransomware, we need to feature that paying the ransom won't solve the issue. There is no certification that your data will be recovered.
The only way to remove the ransomware is by deleting the virus using the Antivirus and Antimalware software. But, doing this would not help you get your data back, but this would at least secure your computer from the future threats. And about your lost data, as we have already mentioned the best research team out there is working on it once the solution is out we would update you on that so stay connected keep reviewing the article for any further updates.
CryptoLocker elimination explained:
Kindly, don't pay a fine since this doesn't ensure that you will get a key required for documents' decrypting. To eliminate CryptoLocker infection from the system, you have to examine your PC with Antivirus and Antimalware.
In a case were your Antivirus and Antimalware does not begin because the ransomware is blocking it, you have to follow the steps that we arranged to help you.
Remove CryptoLocker in Safe Mode with Command Prompt
Step - 1
Steps to be followed to enter the safe mode Win XP/Vista/7
- Click start, then shutdown, then restart.
- While the computer is booting up at the very first screen start taping F8 until you see the advanced boot options.
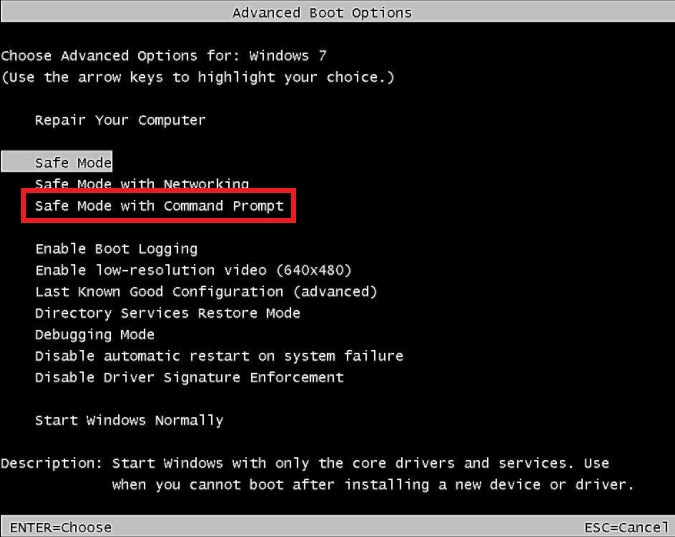
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10.
- On the windows login screen you need to press the power option.
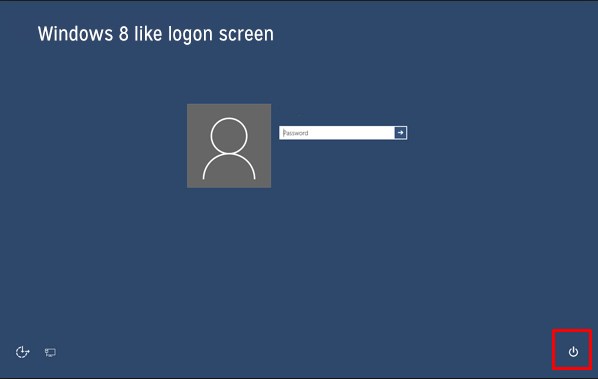
- Now, press and hold the shift key on the keyboard, and then click restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.

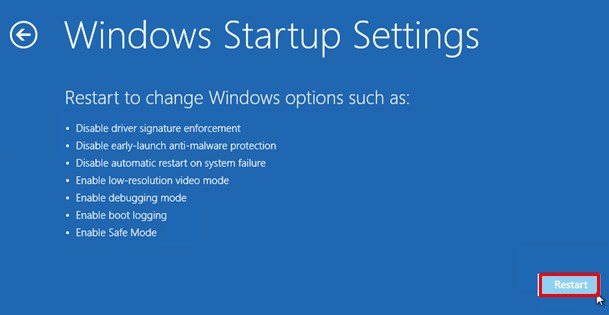
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Step – 2 (Restore system)
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
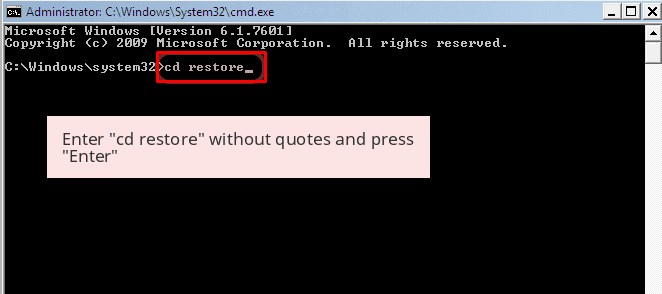
- Now, type rstrui.exe and hit Enter again.
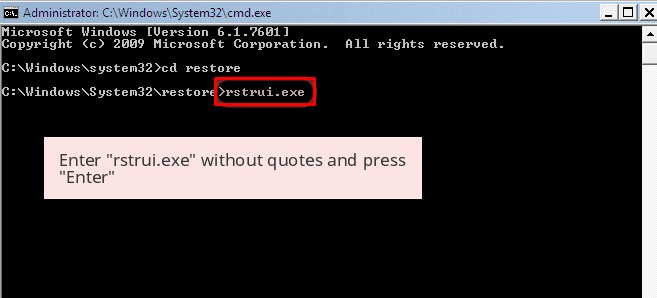
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
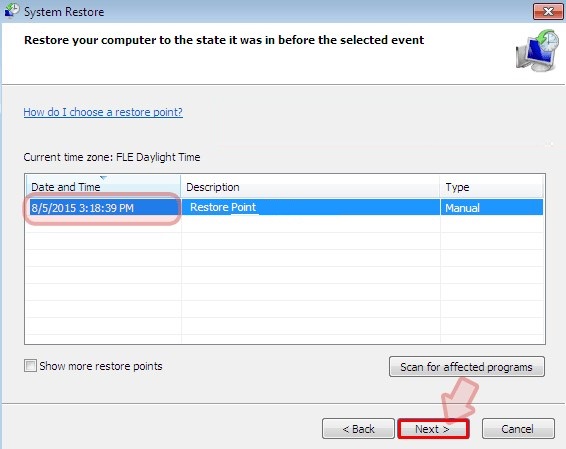
- Then, click next and followed by yes.

Following these steps will get your computer back but this does not mean that your computer is free from the infection.
Follow the steps below to build a robust firewall and prevent the further infection.
- Enable ad-blocker: Pop-ups and advertisements are the quickest and most reliable resources for the hackers to hijack the computer. So, enabling the ad-blocker would be a step towards blocking all the malicious websites or advertisements from popping up on the screen.
- Recommended Updates: Do not postpone any updates. If there is any recommendation from the computer to update the operating system, drivers or any security software you have do not delay it. Moreover, according to survey older version tend to be an easier target.
- Third-party installation: Avoid installing programs from untrusted websites because malware is bounded with such programs. If you still wish to install such program look for a trusted third-party website, read user review about the website before trying it.
- Frequent Back up: Make a habit of backing up all your personal data frequently as it assures the security of it, an attacker can crash your computer, wipe out all your personal data or might corrupt it so that the backup would be helpful in such emergency.
- Log out of all the websites once you are done using it, i.e., Banking websites, social websites. You could be leaving all your personal data vulnerable if you are using a public network.
- Make sure you are using a secure connection before viewing any website have a look for the padlock icon before the website URL.
- Use an authentic firewall, anti-malware, and Antivirus: It’s better to stay ahead, why wait for the malware to hit your computer. We recommend that you install an Antivirus like McAfee or a good Malware Removal software like Free Malware Removal tool. Apart from this, we would suggest a regular updating of these software’s to detect and avoid latest infections.
