FOX Ransomware Overview
FOXRansom is a part of the ransomware family. This ransomware is currently targeting the Hungary Country, found by the security researcher; it encrypts the victim's machine by using AES Encryption method.
It appends the filename of the affected file by adding .FOX extension in the last. It Only targets the C Drive along with more than 20 file extensions.
This ransomware using Hidden Tear Library which is easily available on GitHub.
This ransomware doesn’t contain any ransom amount information. It drops the ransom note on the desktop. By looking at the code it seems it contains lots of bugs in the code which can be easily rectified by anyone.
Flow Chart
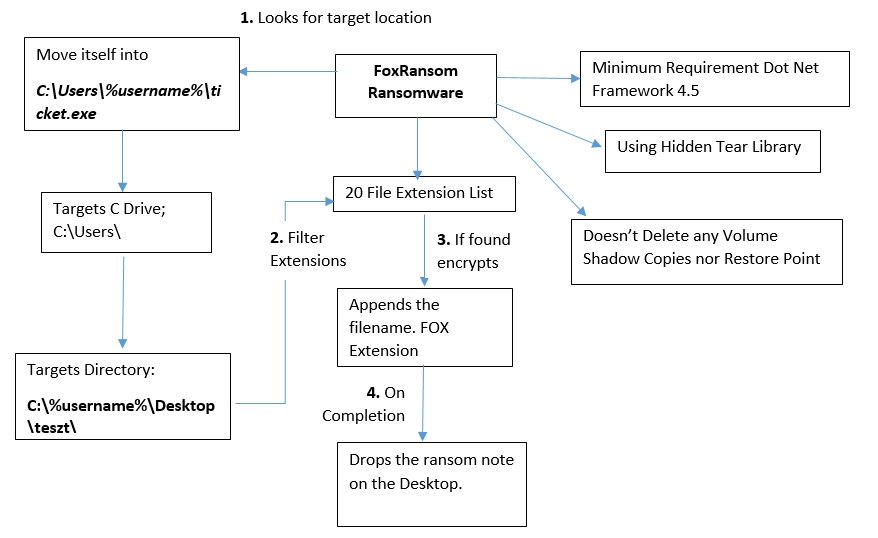
Technical Analysis of FOX Ransomware
File Name: ticket.exe
MD5: 457758293DA02BB95B232ECF767246E6
File Type: .EXE
Spread Via: Not Known Yet.
Detail Description of FOX Ransomware with Screenshots
Static Analysis
This ransomware has minimum requirement Dot Net Framework 4.5
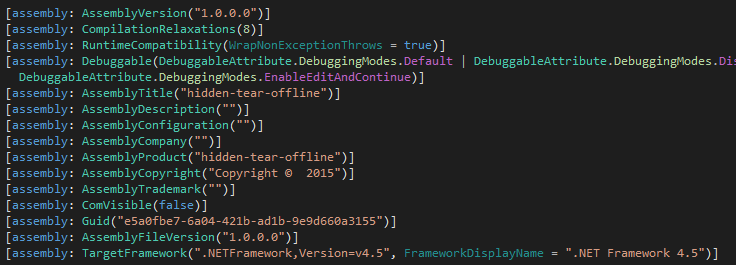
Figure 1 Assembly Information
As shown below, this ransomware has flag condition which checks whether the file already exists on the given location or not, if the file already exists on the given location, in that case, it throws an exception error of path already exist due to bugs in the code. On execution of this ransomware, it also looks for the ticket.pdf file on the system, if it founds the ticket.pdf file it attempts to launch the ticket.pdf file in pdf application viewer.
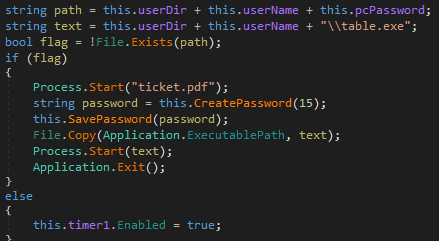
Figure 2 Flag Condition
As shown below, this ransomware gathers the Username, Computer Name and targets the User Directory C:\Users; While the ransomware is running in the background it appends the affected filename with .FOX Extension.
This ransomware using the Hidden Tear Library which is easily available on the GitHub. As shown below this ransomware is using AES Encryption Method to encrypt the files.
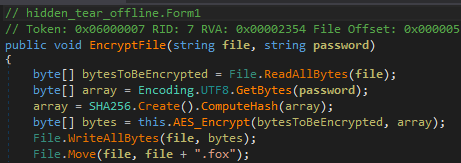
Figure 3 AES Encryption
As shown below, as per the code this ransomware is creating a random password based on predefined string and a fixed length of 15 for encrypting files and move the ransomware to a specific location with .fox extension.
Thereupon, this ransomware starts encrypting the folder based on their specific target directory, extension list, and password.
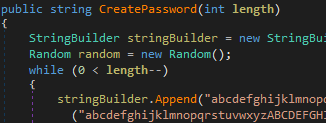
Figure 4 Random Password
As shown below, it targets the C:\Users Directory and also drops the 2 text files (adobe.txt and winsys.txt) at the following location
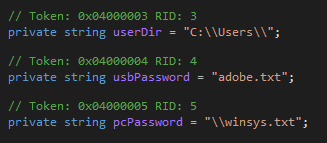
Figure 5 Static Fixed Values
As shown above, “adobe.txt” contains the following information which is dropped by the ransomware on the user’s machine.
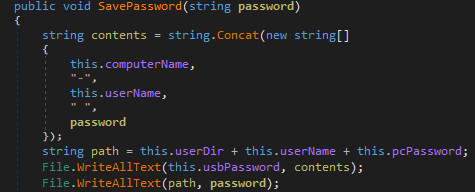
Figure 6 Adobe Text File Contains Computer name, Username, & Password
As shown below, this ransomware encrypts the files based on the extension list. It has more than 15 file extensions list.
".txt",".doc",".docx",".xls",".xlsx",".ppt",".pptx",".odt",".jpg",".png",".csv",".sql",".mdb",".sln",".php",".asp",".aspx", ".html",".xml",".psd"
It searches an above extension in the target drive and encrypts it.
This ransomware drops READ_IT.txt in C:\users\%username%\Desktop
While opening the READ_IT.txt in notepad it shows the following message, which is written in the Hungarian language.
“Az ön gépe és fájlai zárolva lettek a FoxRansom virus által!”
English Translation: Your machine and files have been locked by FoxRansom virus!
Once the files have encrypted this ransomware it appends the filename by adding .FOX extension in the last.
Figure 7 Fox File Extension
By looking at this ransomware code and behavior process it seems that’s it currently in development. Due to currently under development, this ransomware doesn’t delete Volume Shadow Copies from the system nor it deletes the System Restore Point.
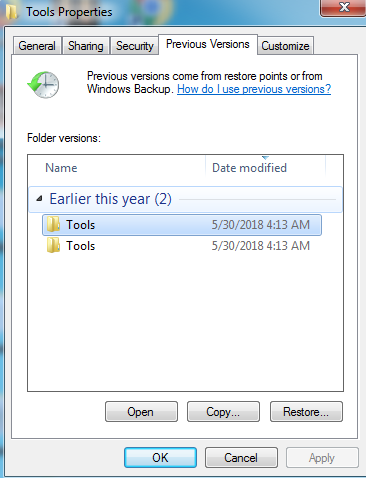
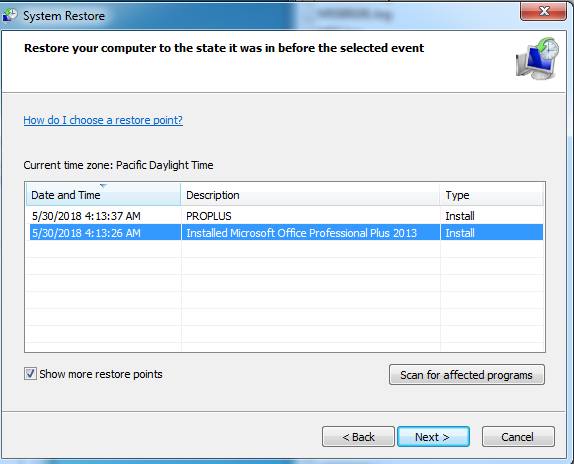
Figure 8 Previous Version & Restore Point
IOC’s
Hash
457758293DA02BB95B232ECF767246E6
Associated File Path:
C:\Users\Admin\table.exe
C:\Users\Admin\Desktop\teszt\
C:\Users\Admin\Desktop\adobe.txt
C:\Users\Admin\Desktop\Read_It.txt
C:\Users\Admin\Winsys.txt
Are you worried about your PC health?
Check your PC Health for Free!
