Princess Ransomware Overview
A new variant Princess Ransomware has been found by the security researcher which is being distributed called Princess evolution. Like its previous variant, Princess Evolution is a RAAS (Ransomware-As-A-Service), this ransomware is promoted on an underground forum.
This variant encrypts the victim's machine data by using AES Encryption method & target all connected drives.
It generates unique file extension for every individual machine, it appends the filename of the affected file by adding .0wjUj extension in the last. It drops the ransom note on the desktop and every processed folder. Ransom note contains the payment information with an instruction “How to contact an Attacker”.
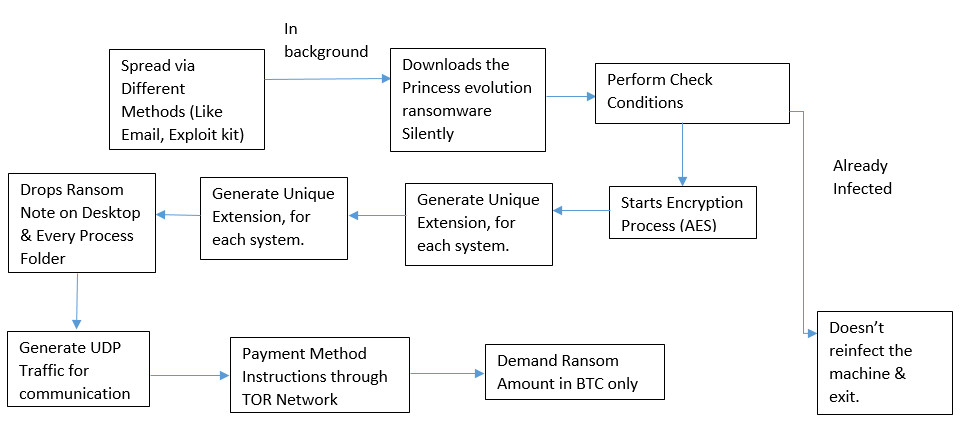
Flow Chart
Technical Analysis of PRINCESS Ransomware
File Name: princess_ransom.exe
MD5: ACAEAF1E1FF0B043A37D2A3E3F9F3FBE
File Type: .EXE
Spread Via: Exploit Kit, Phishing Email & Malvertising Campaign.
Detail Description of PRINCESS Ransomware with Screenshots
On execution of this ransomware, first it checks the 2 condition, if it found that system is already infected by Princess Ransomware then it doesn’t reinfect the victim machine. Following are the 2 conditions checks:
- C:\Documents and Settings\admin-pc\Application Data\MeGEZan.VDE
- Mutex name: hoJUpcvgHA
In case, if the system is not infected with the Princess Ransomware then it starts the encryption process, it’s using AES encryption method to the encrypt the victim system files. It targets all the connected drives on the victim machine.
This ransomware gathers the Username, Computer Name and generates UDP traffic to sends the data on their C&C (Command and control server). While the ransomware is running in the background it appends the affected filename with .0wjUj Extension. For each individual victim machine, it generates the unique file extension. In our case generates .0wjUj Extension.
This ransomware drops 3 ransom notes (.TXT File, .HTML File & .URL File) on desktop location & every processed folder. As you can see in below process tree, once the encryption has been completed it launches the ransom note in the browser.
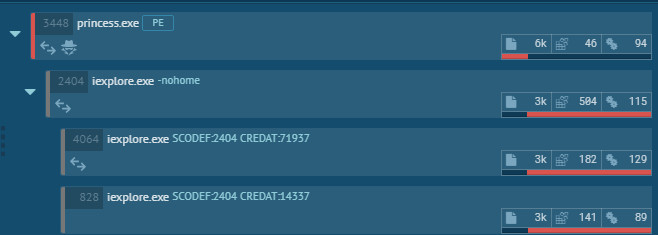
Figure 1 Process Tree
While opening the (_H0W_TO_REC0VER_0wjUj.txt) in notepad it shows the following ransom note information.
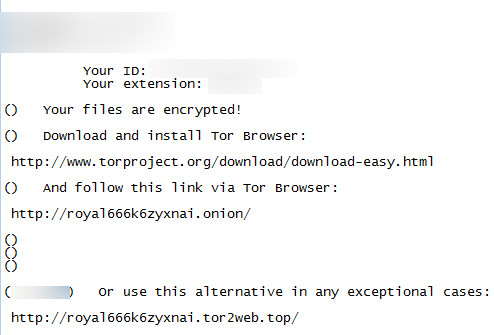
Figure 2 Ransom Note
Following is the HTML version of the Ransom Note:
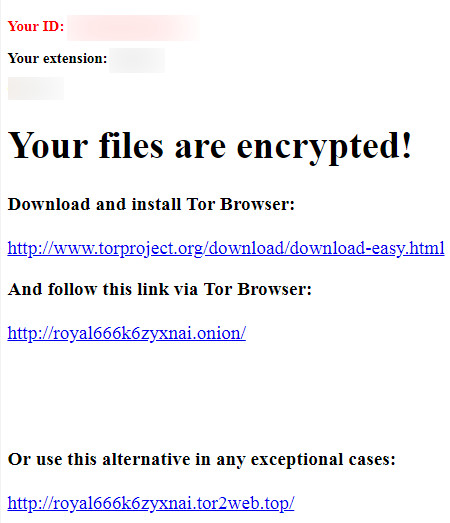
Figure 3 HTML Version of Ransom Note
Once the files have encrypted this ransomware it appends the filename by adding .<random generated> extension in the last.
Princess ransomware doesn’t delete Volume Shadow Copies from the system nor it deletes the System Restore Point. The victim can easily restore their files by going back to the Previous Versions Folder option or going to the system restore point option, if available. As shown below, after getting infected with Princess Ransomware, we can still recover our files without contacting to malware actor, if the system has any restore point available or Folder Snapshots are available then we can easily recover our files.
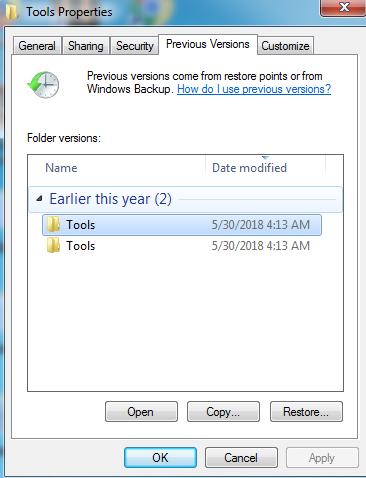
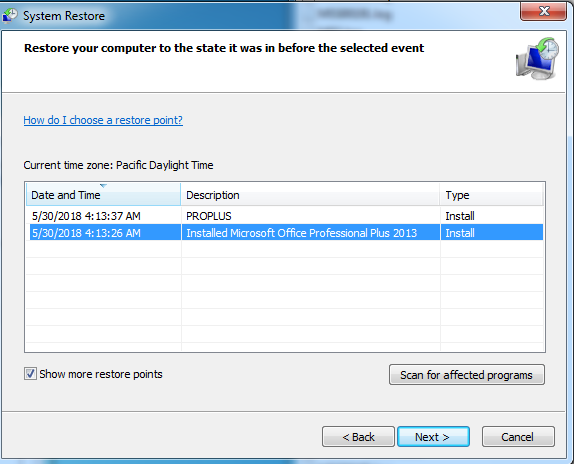
Figure 9 Restore Point
This ransomware generates UDP Traffic, as shown below:
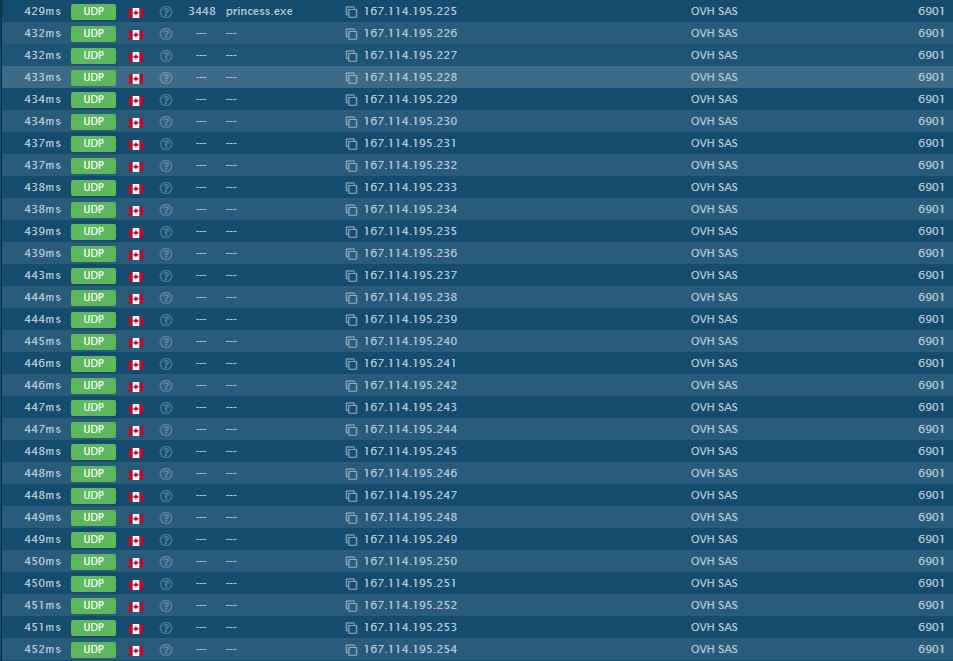
Figure 4 Generates UDP Traffic
Malware actor has chosen the anonymous channel mode so that it can hide their identity. Malware actor is using TOR Onion link; which is only accessible by TOR Browser.

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
If the victim wants to contact the malware actor then it needs to install the TOR Browser first and then navigate to the given onion link in the ransom note, or if the victim doesn’t want to go with the installation of TOR Browser malware actor also has given alternative option by giving TOR link (hxxp://royal666k6zyxnai.tor2web.top/) which is easily accessible in any normal browser. Thereafter it needs to put his personal ID to get further instructions for the payment.
But we will always suggest to our users to never pay any ransom to any malware actor as it encourages them.
It’s better to take backup on a regular interval. As we know this ransomware didn’t delete any system restore point or Previous folder option. So by going back to the system restore point, we can easily recover our files.
By entering the given link (hxxp://royal666k6zyxnai.onion) in TOR Browser to get the payment information, it shows the following screen

Figure 5 Princess Evolution Ransomware Page
As shown above, that malware actor has design the animated page of Princess Ransomware. By clicking on the animated screen it brings the following screen, which asks for the victim Personal ID.
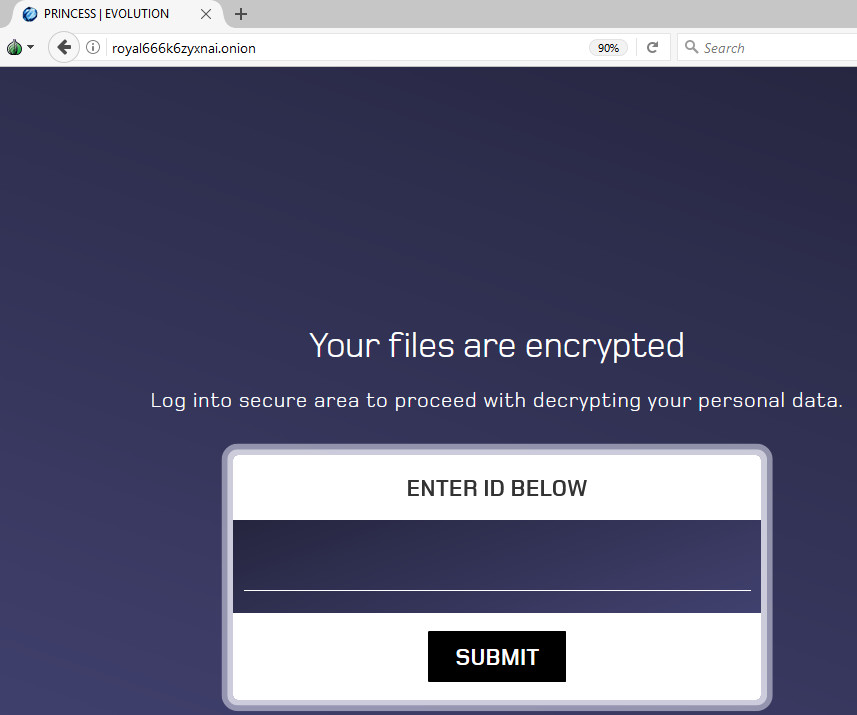
Figure 6 Victim Personal ID Page
After entering the personal ID, it redirects to another webpage
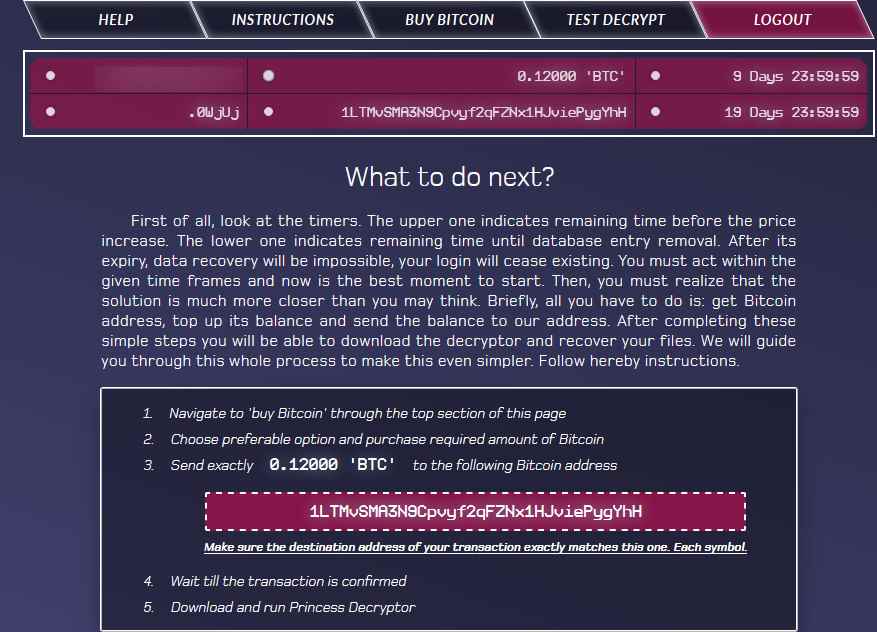
Figure 7 Payment Information BTC Address
As shown above, the malware actor has demanded “0.12000 BTC” ransom amount which is equal to 774.10 Dollar at today’s rate in exchange of decryption tool.
As shown above, in the payment page crooks has clearly mentioned that if the victim didn’t pay the ransom amount in 10 days then it will double the ransom amount & if the victim didn’t pay the ransom amount in 20 days then all the encrypted files will be deleted from their server.
As shown below by doing research we found that crooks are promoting and dealing the princess ransomware on an underground forum.
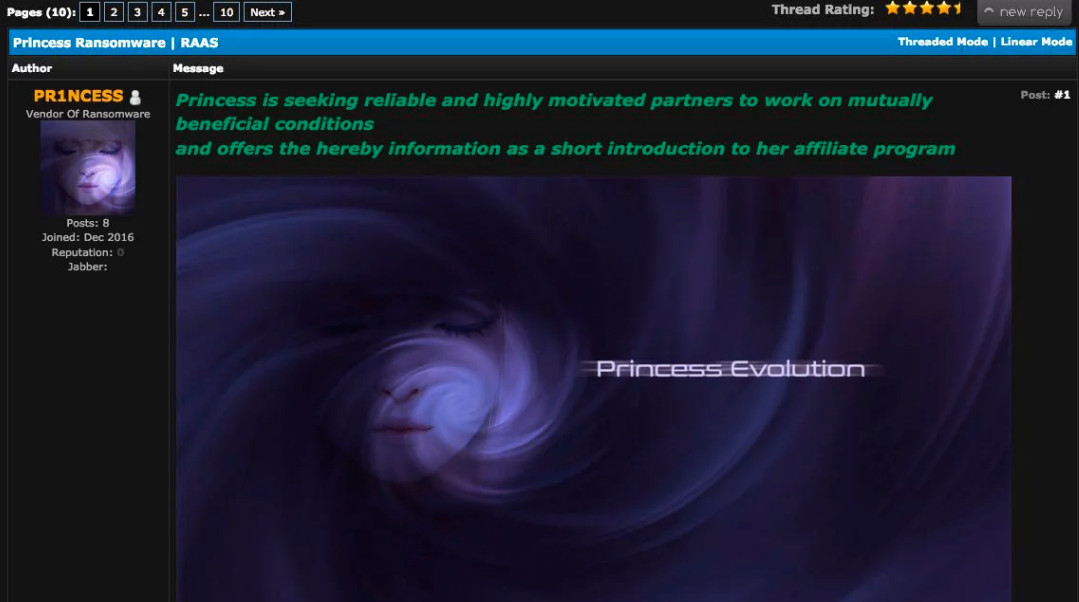
Figure 8 Promoting on Forum
As shown below, on forum crooks have mentioned the features like RaaS (Ransomware as a Service) of Princess Ransomware with revenue splits and support model with its configuration facilities.
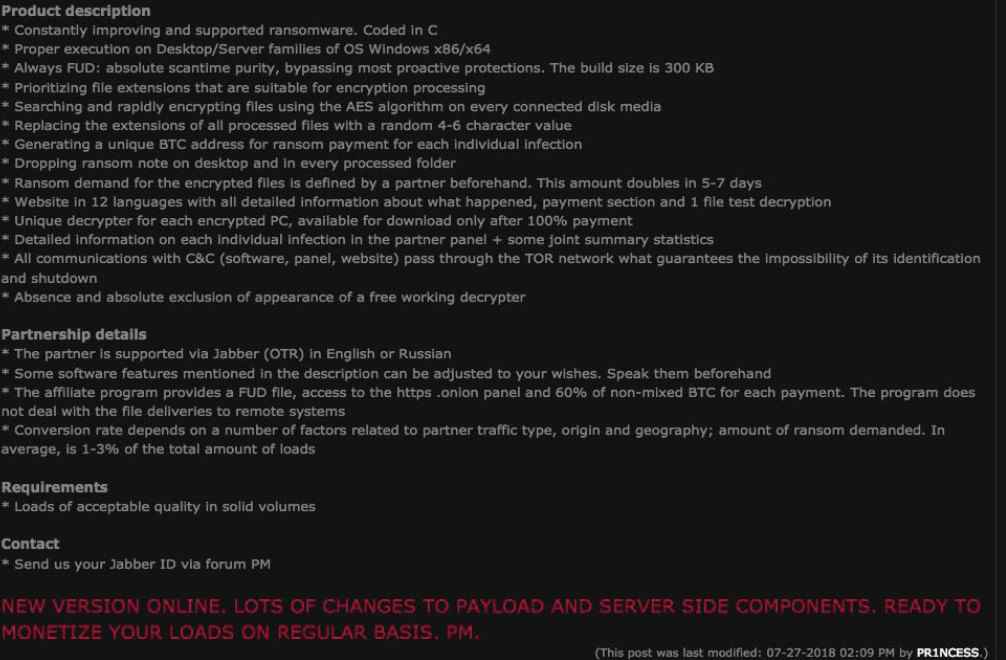
Figure 9 Princess Ransomware Product Description
IOC’s
Hash
04D5426462DBC02BBEC38145ABC749C5
Associated File Path:
- c:\(_H0W_TO_REC0VER_0wjUj.txt
- c:\(_H0W_TO_REC0VER_0wjUj.html
- c:\(_H0W_TO_REC0VER_0wjUj.url
- C:\Documents and Settings\admin-pc\Application Data\MeGEZan.VDE
Associated URL:
hxxp://royal666k6zyxnai.onion
Mutex:
hoJUpcvgHA
[btn_fix
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
