CamuBot Malware Attacks On Brazillian Bank Accounts
A highly sophisticated cyber threat named CamuBot Malware attacked bank customers of Brazil. CamuBot banking malware steals your banking credentials though it looks like a legitimate security module from the bank.
Developers of the threat are actively targetting the companies, banks and public sector organizations using a number of social engineering techniques only to bypass system security controls.
At the time of our research we found, it caused a great damage to the Brazillian banks and computers of home networks. Thus, we decided to create a CamuBot Malware removal guide whose contents are given in the below table.
Localities of Brazil are calling it as CamuBot Brazillian Banking trojan disguised as a bank’s security module featuring official logos of bank to lure the users. It appears as if the malware is a part of the security module.
However, it bypasses the biometric account protections and unauthentically controls the security of the banking system. In some cases, the banking malware also hijacks a one-time password and disguise itself as a branded security software.
How CamuBot Malware Surpass Biometric Protections?
According to cybersecurity experts, the malware fetches and installs the driver in the targeted PC attached to biometric authentication hardware. Attackers take advantage of malware’s advanced features and create a new firewall and antivirus.
A communication is established between attackers and targeted computer via the SSH-based SOCKS proxy network. And through CamuBot malware code, the malware disguises itself as a trusted security program.
Now the CamuBot attackers talks to the users of Brazillian banks and asks them to remotely access their USB-connected device. The victim authorizes the access thinking that a bank representative is guiding them to install a legitimate bank security tool.
However, the matter is entirely different! The attackers have computer’s authentication, biometric hardware authentication and now they are in direct contact with the bank users.
It allows the attackers to intercept the one-time passwords for making fraudulent transactions through the victim’s account on the basis of a fake IP address obtained from a proxy network.
The biometric authentication is important for making transactions, but attackers surpass it from a one-time password and hijack the accounts. The CamuBot malware is sophisticated to overlay accounts using fraud tactics, fake screens and remote access tools.
Few Samples of CamuBot Malware
It should be noticed that the unique infectious threat directly contacts the victims to trick them into downloading the malware. Later on, they steal users money! A few samples of CamuBot Brazillian banking trojan are as follows:
- 9eab7ea297ea71057691c09b485d646f
- a000fe90363517e0fc4c8d02f7830825
- 684AAA16C9B54E4645C8B5778DB7562F
- CD27C9FC659B50776E3BD208A42F1E3F
- 7D50411C9621F1AD00996C8CE0F1AC20
How CamuBot Banking Malware Is Different From Other?
It is a mix of elements that lure victims into installing the malware on their device and unknowingly authorize a fraud transaction.
To carry out their attacks, its operators first find businesses related to the financial institution. They then initiate phone calls to the person having business’s bank account credentials.
The attackers identify themselves as bank employees and trick the victims into installing a new security setup for online banking activity. Those lured into downloading suffers from the attacks of banking malware. Such users are advised to close all programs and scan the computer with Malware Crusher to eliminate the threat.

Continue use of the fake security module, blocks the access to your account and successfully steals all the money.
The fake application featuring bank logo execute the victim's device and with every attack, the IP address of attacker changes. It protects them from getting caught by the security organizations.
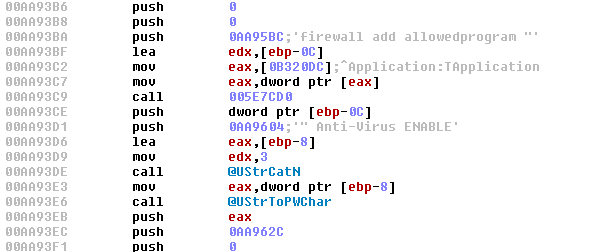
You can find the files of CamuBot in C drive of your computer whose path is as follows;
C:\Windows\System32\netsh.exe” firewall add allowedprogram “<malware_dropper_directory>” Anti-Virus ENABLE
The delivery of CamuBot is personalised and targets business account holders in Brazil, not in any other geographies of the world.
What Are The Defenses Against CamuBot Malware?
Cybercriminals infiltrate your computer manually! The malware code overrides the bank’s security codes and gives a win-win situation to the attackers. The malware is stealthy and hides within the computer to access bank accounts.
Therefore, to save yourself from a banking malware, it is important to raise defenses against the threat. For this, we have two effective options that help to remove CamuBot malware permanently from your computer.
Automatic Preventive Method
With this article, you have got a brief idea about the working CamuBot and how it infects the computer. Your informative resources are complete and you must wisely act against the malware attack.
For this, we suggest you an antivirus + antimalware + PC protection tool: Malware Crusher that fights, prevents and remove the threat completely from your system. Following removal capabilities make it as a solution to everyone's cybersecurity need;
- It’s real-time protection feature, performs a deep scan to detects malicious software and persistent threats. Also, identifies suspicious behaviour on your computer.
- The Quarantine feature of the tool removes all infected files from your computer. Additionally, keeps a record of all deleted malicious program and allows you to choose important programs to restore at a later time.
- Malware Crusher also creates a shield against Ransomware, Adware, Malware, Browser Hijackers, Viruses, Extensions and Trojans from entering into your system.
- The 24X7 online protective shield works as an anti-exploit technology and blocks the ransomware component before they hold files as a hostage.
- Malware Crusher tirelessly visits all domains, URLs and web pages to secure your online presence from fraudulent entities. Furthermore, the tool detects the vulnerabilities of online fraudulent entities effortlessly.
- Malware Crusher becomes fiercer in detecting keylogging, remote connections and saving your session data from being recorded.
It continually monitors the cyber world, deeply diagnose the threat and neutralize it by writing antimalware code. Malware Crusher's 5-minute function would become a saviour to remove CamuBot malware!
However, for the ease, you can also follow the below manual removal guide for general purposes like uninstalling programs, ending task manager process, clearing browsing history etc. before you use the antimalware removal tool.
Manual Preventive Methods
- Press Ctrl + Shift + ESC together to open Task Manager. Look for suspicious files, right click on it and click End Task.
- Now, press it to open RUN box window. Type appwiz.cpl on it, this opens Programs and Features window.
- Select each suspicious program and uninstall it one by one. Once the uninstallation is complete, restart your computer and again redirect yourself to Programs and Features window to check whether the application is present or not.
- When convinced, press Windows key + R to open RUN box window. Type regedit on it, hit OK and then click Yes.
- Go through HKEY, HKLM, etc. files and find all suspicious files and delete them.
- You can also delete malicious extensions from your browsers like Chrome and Firefox.
1. Click on the Customize and control menu icon at the top right corner of Google Chrome.
2. Select "More tools" from the menu.
3. Select "Extensions" from the side menu.
4. Click the remove button next to the extension you wish to remove.
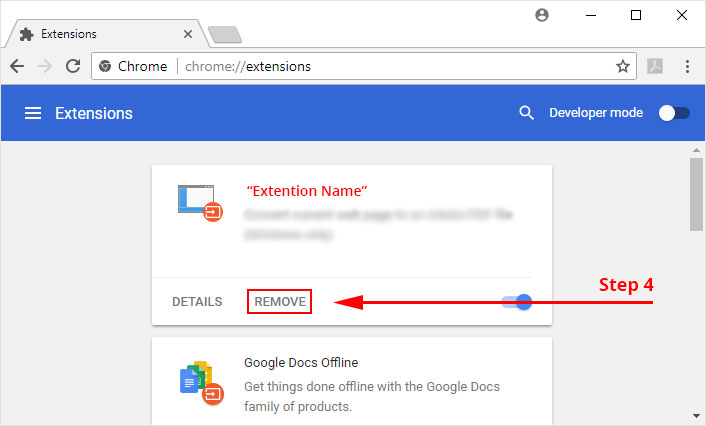
5. It will confirm again, click “remove” and the extension is finally out of the system.
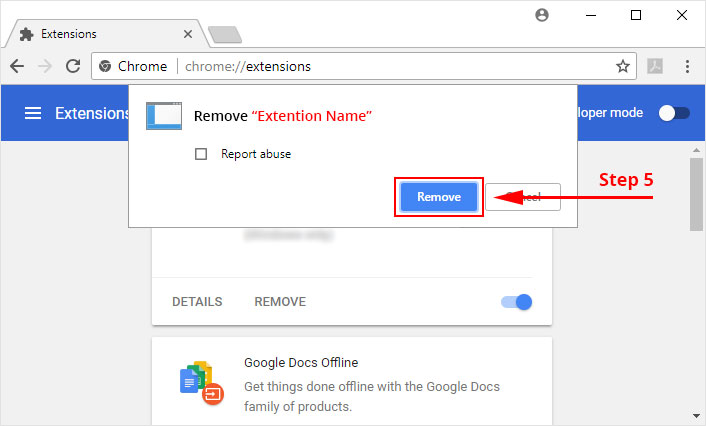
Now that we have successfully eliminated the malicious browser extension, we need to create a robust firewall to avoid any such thing that makes our system and privacy vulnerable to various online threats.
1. Click on the “menu” button at the top right corner.
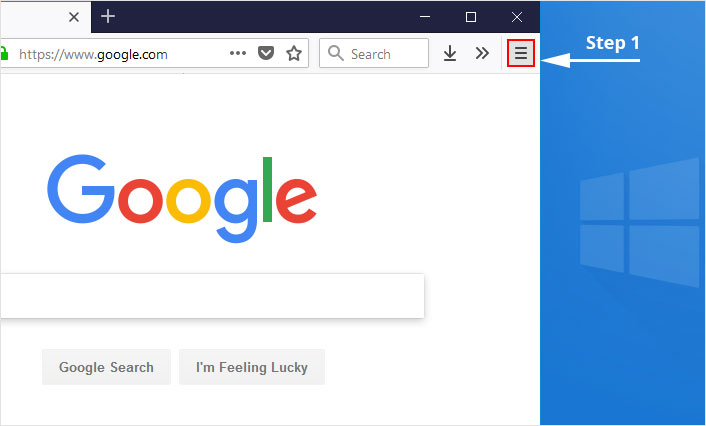
2. Select “Add-ons” from the menu.
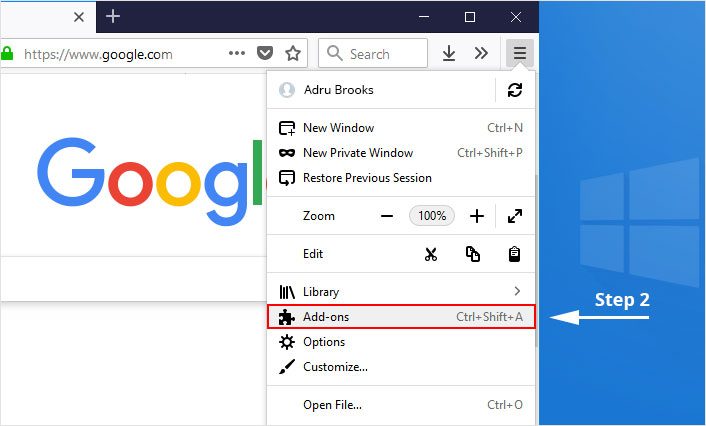
3. Click the “Remove” button next to the extension you wish to get rid of.
Now that we have successfully eliminated the malicious browser extension, we need to create a robust firewall to avoid any such thing that makes our system and privacy vulnerable to various online threats.
The manual method sometimes doesn't work at Windows OS because finding and deleting suspicious and modified registry files in registry editors is a difficult task. On the other hand, if a useful file deletes, then the operating system windows stops working properly.
That’s why it is highly recommended to use an automatic tool to prevent malware attacks on your computer. If you wish to get more news and awareness on the happenings of the cybersecurity, then keep visiting us.

Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
