DarkHydrus Hacking group Uses Microsoft Excel To Inject RogueRobin Malware
RogueRobin Malware is an infamous threat developed by APT hacking group DarkHydrus. The new malicious campaign attributed to this group abuse Google Drive and Microsoft Excel via C2 servers for worldwide attacks.
According to cybersecurity reports, the targeted attacks involved sending macro-enabled Excel documents (VBA code) and .xlsm files via phishing emails in the Arabic language.
DarkHydrus - a malicious hackers group is targetting middle east countries. Macros download a .txt file document and regsvr32.exe application then a c# file drops down onto the victims' computer.
Once the file executes, it fetches a payload dubbed as RogueRobin malware which is a fully featured backdoor providing varieties of functionalities to the threat authors.
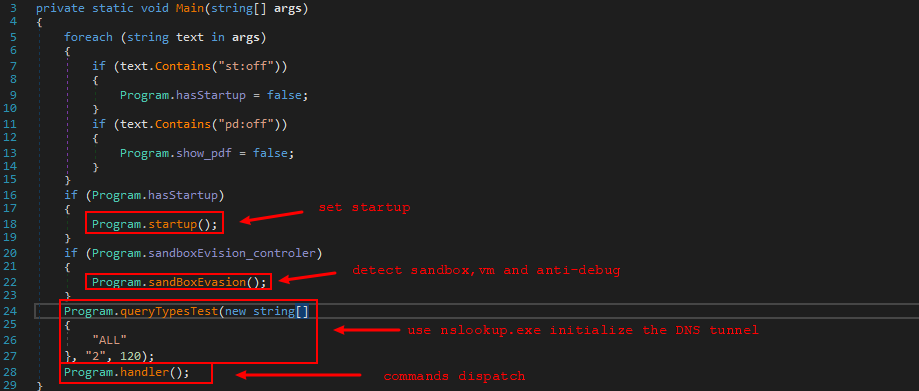
It allows the operators of DarkHydrus to execute PowerShell scripts such that it takes advantage of PowerShell features and add functionality by generating new scripts.
Before carrying out any functionality, the payload checks whether it is executing in a sandbox. If the payload is not running in a sandbox, then it tries installing itself persistently into the system.
The payload interacts with C2 server and then inject and communicate with DarkHydrus’ Malware. RogueRobin malware uses Google Drive as C2 Channel which we are going to describe later in this article.
What is RogueRobin Malware?
It is a high-risk trojan which distributes via email spam campaigns and delivers malicious attachments like Microsoft Excel documents into the victims' computer.
After the successful infiltration, RogueRobin connects to the remote server, downloads several files and run the number of commands from that file. Cyber criminals or malware attackers basically gain remote access to the system and perform various actions inside it without user permission.
The malware uses Google Drive as a second method to send malicious instructions via DNS tunneling channel and activates x_mode command. Once the values are assigned to every variable of the command, RogueRobin uploads file to Google Drive.
The malware continuously uses DNS tunneling to communicate on C2 servers. It also repeatedly checks for debuggers everytime it does a DNS query. If a debugger is identified, the query generates a hex-coded subdomain (676f6f646c75636b.gogle[.]co) which means 'goodluck.'
In order to remain safe from RogueRobin Trojan attacks, one must know all the possible cases where it damages your computer. Below listed symbols are the early symptoms that tell you the dangers of virus infection.
- Slow and sluggish computer performance
- Irrelevant pop-ups keep coming back to back to your browser
- Few programs run on their own even if you close them
- File multiplies and duplicates itself on its own
- Files or programs are new and unknown
- Deny access to files and folders
- Hard drive corrupts
- Infect and delete backup files
- If attacks are more severe then mail system shutdowns
- Modifies Windows registry editors files
- Disable firewall settings and drops other malicious threats into the system.
These annoyances put your computer at great risk. Even more, such virus attacks are getting larger day by day in terms of complexity and have easily established itself as a tool to victimize cybersecurity.

Uninstall Malware Related Files and Programs
Somehow this malware has entered into your computer and successfully infiltrated the security vulnerabilities of your computer’s operating system. There are high chances that it could have installed other malicious file and programs on the computer without letting you know.
Therefore, the below steps will help you to uninstall and delete all the unwanted programs and files that entered under the shadow of malware.
- Press Ctrl + Shift + ESC together to open Task Manager. Look for suspicious files, right click on it and click End Task.
- Now, press Windows key + R to open RUN box window. Type appwiz.cpl on it, this opens Programs and Features window.
- Select each suspicious program and uninstall it one by one. Once the uninstallation is complete, restart your computer and again redirect yourself to Programs and Features window to check whether the application is present or not.
Does Resetting Browser Help to Delete RogueRobin Malware?
Resetting browser is a very good option because it gives you a chance to delete all the manipulated settings done on the browser by the malware. Below steps will help to reset Chrome and Firefox settings.
Reset Google Chrome
- Click three dots on Chrome Window.
- Select Settings, scroll down to the bottom of the page and click Advanced.
- Again scroll down to the end, click Restore settings to their original defaults > Reset Settings.
Reset Mozilla Firefox
- Open Firefox Menu (in the right corner of the Window)
- Select Help > Troubleshooting Information > Refresh Firefox > Finish.
- You can also try Safe Mode to disable the add-on.
The above manual methods are stepwise techniques which only helps you to get back your default settings. Therefore, we suggest you to use computer security tools that are capable to remove RogueRobin malware easily.
Malware attackers are very advanced and had learned to gain illegal access to the computer. The variants of malware are now more adaptable, resilient and damaging. On the other hand, in the era of cyber warfare, it is difficult to stop cyber attacks by using common antivirus software.
Thus, the best preventive step is to upgrade our cyber defense systems at home and office computers with such security tools that provide real-time protection feature, quarantine feature, web protection and anti-exploit technology.
Note: If your computer doesn’t have such security software, then download ITL Total Security and Malware Crusher to prevent malware attacks on your system. Both are reputable, vigilant and robust in creating a shield 24X7 against any cyberthreat.
These tools are highly recommended if you are willing to give advanced security to your PC. Their 5-minute function could be a savior for your computer!

Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
