Smoke Loader Malware In-Depth Analysis
Earlier this year in March 2018 a massive malware campaign distributing a dropper/loader was documented in many cybersecurity reports. The primary purpose of the campaign was to infect Windows-based computers by distributing coin miners payload in them.
These payloads were unique in many terms as they exhibited persistence mechanism, cross-process injection and evasion mechanisms. One such payload is Smoke Loader Malware also known as Dofoil which incorporate coin miners in attacks.
The malware can enter your system from anywhere and is a typical example of crypto miners. In this article, you will understand the working of smoke loader malware and what is it? Along with the methods to remove it.
What is Smoke Loader Malware?
Also known as Dofoil, this malware is relatively small, and employes a bot that drops various malware families into the computer. Even though it’s designed to drop malware, it has some of its own capabilities that categorize it as a malware.
Despite being old, it’s still a strong cyber threat which was recently dropped from RigEK and MalSpam campaigns. In this article, we’ll learn how the malware unpacks itself and how does it interact on the online servers?
Detected in June 2011, the malware was advertised for sale by a user called SmokeLdr. Cybersecurity reports considered it as a trojan-type malware through which cybercriminals use to infiltrate the computer system without user’s consent.
After successful infiltration, it performs three main actions;
- Self-update
- Remove traces
- Download other malicious threats
However, nowadays the dropper/loader is being used for downloading cryptojacking malware. Thus, the issue of the smoke loader is getting serious in the cyber world.
It uses propagate injection technique in its campaign thus considering this malware a small application is a big mistake. The initial infection vector is a malicious Word and Excel document that enables macros and initiates a downloading chain of malicious threats.
How Smoke Loader Works?
Immediately after infiltrating user system, Smoke Loader malware connects to a remote C2 server for download the latest version. It modifies the date of its executable file so that no security tool can detect it. Since it removes read/write permissions, a user can't access the file as it gets blocked.
By sending request continuously to legitimate URLs, it disguises its connection to the C2 server and encrypts the traffic online to remain undetected. Judging this behaviour, we can put this threat under the class of advanced trojan.
Smoke Loader spread a variety of other viruses like Coinhive Malware and other cryptocurrency miners only to gather sensitive information;
- It employs system resources to mine cryptocurrencies like Bitcoins and Monero and makes a system unstable. This might lead to a permanent data loss due to which hardware running at its fullest capacity generates excessive heat which then damages hardware. All the obtained revenue goes to the cybercriminals and users suffer from their system problems.
- It is a data-tracking malware that records sensitive information by collecting data types such as keystrokes, saved login Ids and passwords, banking and payment gateway information, websites visited, and other saved files. Therefore, it poses a significant threat to users' privacy and can lead to serious privacy issues including financial losses.
- It also spread itself from victims' identities and hijack web browsers to use social networks like facebook, skype, etc. On such networks, it sends maliciously disguised files/URLs to all of the contacts. For example, the malware sends messages like Check my new photo. The is a bogus message which seems suspicious and one should not open it, especially if it is not in your native language.
There are many malware that performs the above actions to generate revenue for their developers. In short, the presence of Smoke Loader malware leads to a number of issues which must be eliminated immediately with the use of a legitimate anti-virus/anti-malware suite.

How To Avoid Installation Of Smoke Loader Malware?
Smoke Loader installs its original sample and then replaces it with a fresh version. On analyzing samples, we found an online path at C2 servers that download the updated version.
http://<CnC address>/system32.exe.
Replacing the original sample with the latest version makes its detection more difficult and a new crypter repacks the updated sample. This trick also changes C2 servers and save the server in a hidden subfolder located in %APPDATA%.
Few initial samples of Smoke Loader malware are:
- D363e8356c82a1043bb300c12c6c7603
- F60ba6b9d5285b834d844450b4db11fd
- Efa7f95edacec888f39e5ce0ee675a95
To prevent this, always be very cautious while browsing the Internet and especially when downloading/installing software. Carefully analyze each suspicious and unrecognizable email attachment. If you find such file, do not open it and delete the email immediately.
The intrusive ads seem legitimate but once clicked, redirect the user to dubious websites like gambling, adult dating, pornography, etc. These ads are from adware-type PUPs downloaded by smoke loader malware.
Therefore, it is advised to remove all suspicious apps and browser plug-ins from your browsers.
We strongly recommend analyzing download/installation processes such that you can opt-out of all additionally-included programs. Third party downloaders/installers include rogue programs and thus should never be used. The same applies to the software updates.
New smoke loader attack targets multiple credentials and is mostly distributed by phishing spam messages, email attachments and infected documents.
How To Remove Smoke Loader Malware?
Cybercriminals infiltrate your computer manually and the smoke loader virus overrides the other applications while creating a backdoor to enter other malicious threats. It is a win-win situation for the attackers because smoke loader virus somehow infiltrates the system with a motive to collect information.
Therefore, to keep your system clean, we had prepared a smoke loader removal guide that checks the presence of malware code in and authentically removes it. Our guide is divided into two different segments;
Automatic Preventive Method
By reading this article, you already got a brief idea on the working smoke loader malware and how the infection spreads into your computer. To create a shield against the malware attack, we suggest you an antivirus + antimalware + PC protection tool: Malware Crusher that fights, prevents and remove smoke loader malware completely from your system.
Following are it's few removal capabilities which makes it a solution to everyone's cybersecurity need;
- Real-time protection feature: The tool performs a deep scan to detects malicious software and persistent threats and identifies all suspicious behaviour on your computer that deviates it away from normal functioning.
- Quarantine feature: Once the threats are identified, the tool removes all malicious files from your computer. Additionally, it keeps a record of all deleted malicious program and allows the user to choose important programs so that he/she can restore at a later time.
- Creates shield: The tool creates static protection against Ransomware, Adware, Malware, Browser Hijackers, Viruses, Extensions and Trojans from entering into your system.
- The 24X7 online protective shield works as an anti-exploit technology and blocks the ransomware component before they hold files as a hostage.
- The anti-malware tool tirelessly visits all the domains, URLs and web pages to secure your online presence from fraudulent entities. Furthermore, it detects the vulnerabilities of online fraudulent entities effortlessly.
- It also becomes fiercer in detecting keylogging, remote connections and saving your session data from being recorded.
The continuous monitoring of the cyber world updates Malware Crusher everytime a new threat is found. Henceforth, it deeply diagnoses the threat and neutralizes it by writing antimalware code. Its 5-minute function would become a saviour to remove CamuBot malware!
Once you are done with the download, installation, scanning and removal of the smoke loader and other similar malware, you won’t need any other method. The automatic method is a key in itself to remove the threat.
However, if you plan on removing the threat manually, then you can follow the below-mentioned process. The below guide includes small tasks like uninstalling programs, ending the task manager process, clearing browsing history etc.

Manual Preventive Methods
- Press Ctrl + Shift + ESC together to open Task Manager. Look for suspicious files, right click on it and click End Task.
- Now, press Windows Key + R to open RUN box window. Type appwiz.cpl on it, this opens Programs and Features window.
- Select each suspicious program and uninstall it one by one. Once the uninstallation is complete, restart your computer and again redirect yourself to Programs and Features window to check whether the application is present or not.
- When convinced, press Windows key + R to open RUN box window. Type regedit on it, hit OK and then click Yes.
- Go through HKEY, HKLM, etc. files and find all suspicious files and delete them.
- You can also delete malicious extensions from your browsers like Chrome and Firefox.
1. Click on the Customize and control menu icon at the top right corner of Google Chrome.
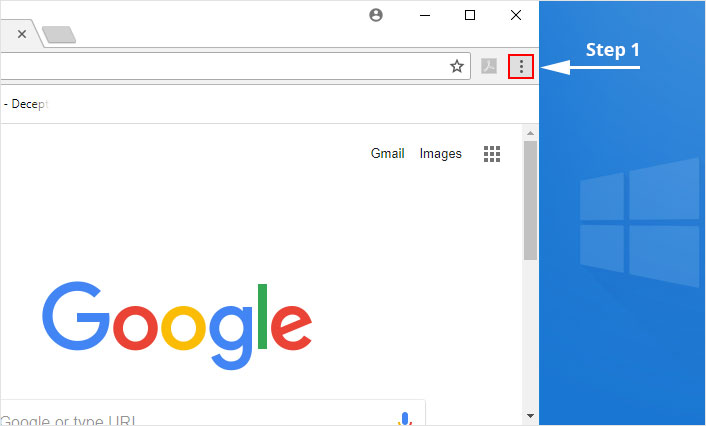
2. Select "More tools" from the menu.
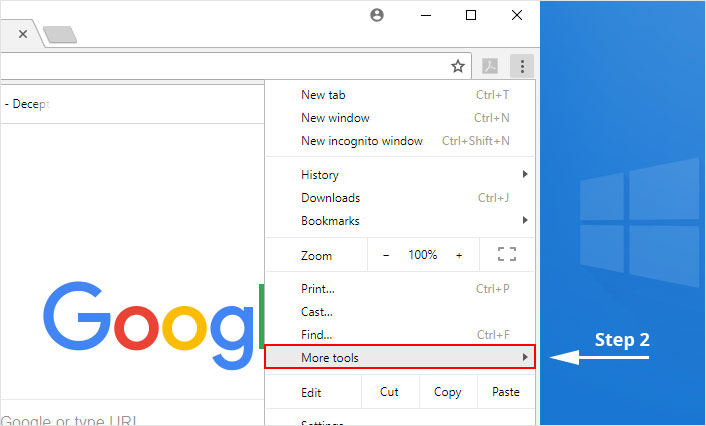
3. Select "Extensions" from the side menu.
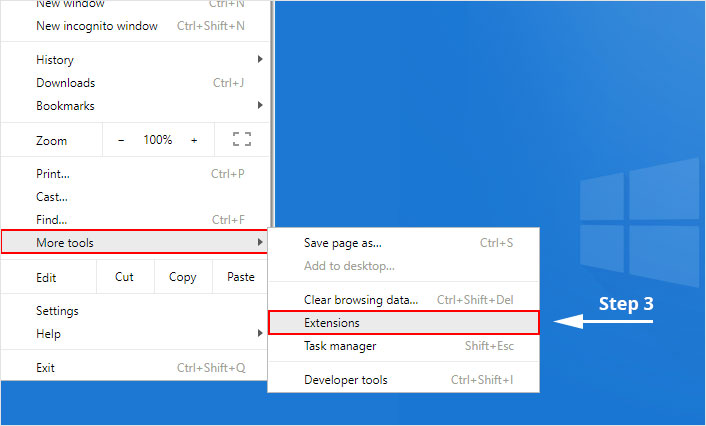
4. Click the remove button next to the extension you wish to remove.
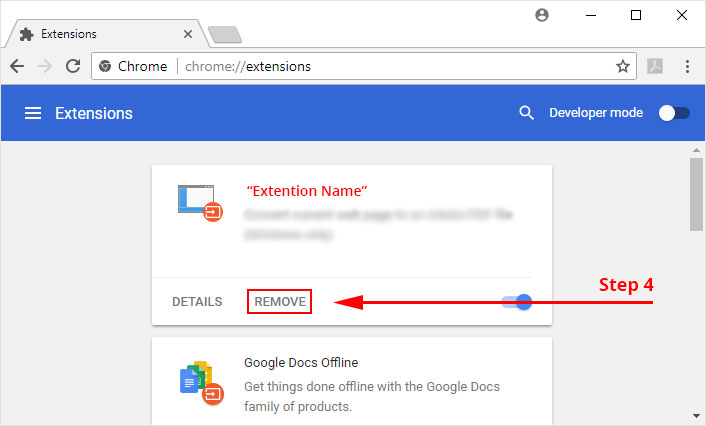
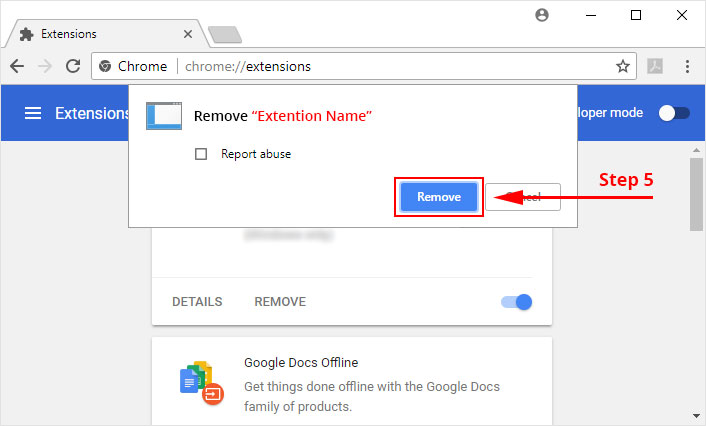
5. It will confirm again, click “remove” and the extension is finally out of the system.
Now that we have successfully eliminated the malicious browser extension, we need to create a robust firewall to avoid any such thing that makes our system and privacy vulnerable to various online threats.
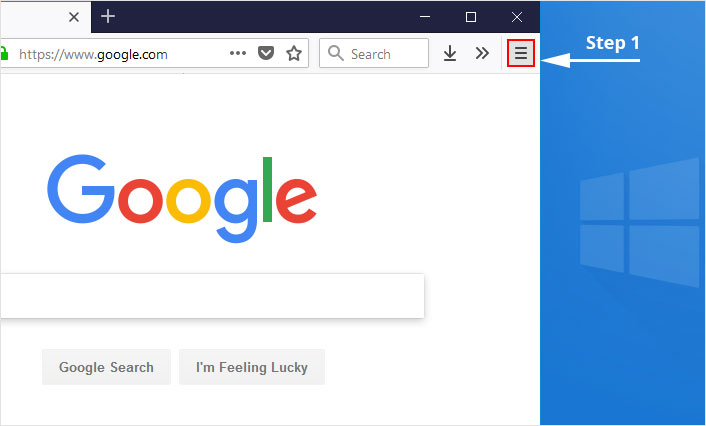
1. Click on the “menu” button at the top right corner.
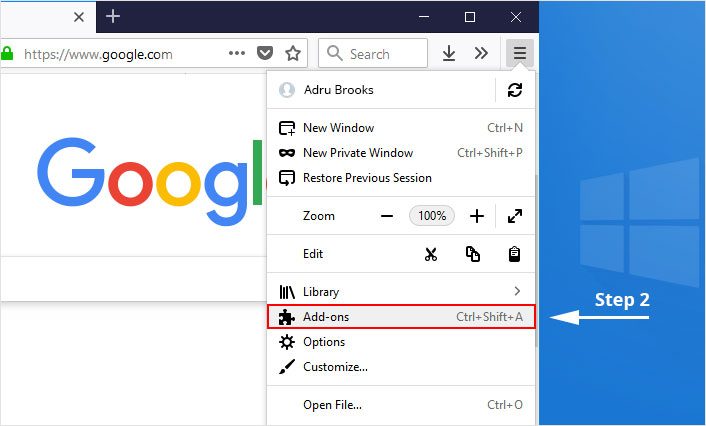
2. Select “Add-ons” from the menu.
3. Click the “Remove” button next to the extension you wish to get rid of.
Now that we have successfully eliminated the malicious browser extension, we need to create a robust firewall to avoid any such thing that makes our system and privacy vulnerable to various online threats.
Sometimes manual methods don't work at Windows OS because finding and deleting suspicious and modified registry files in registry editors is a difficult task. On the other hand, if a useful file deletes, then the operating system windows stops working properly.
Note: Once you successfully perform the above steps, download, install and scan your computer with Malware Crusher. The manual methods can’t protect the entry of a threat though you can clean threats with such steps.
That is why it is highly recommended to use an automatic tool in order to prevent your computer from cyber threats.
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
