Xbash Malware Combines Ransomware, Coinminer And Botnets
Team HTRI found a new malicious threat Xbash Malware targetting Windows and Linux based systems. Developed by a cyber attacker group named Iron Group, Xbash possesses capabilities of ransomware and coinminig which risks your computers and victimize you into paying money.
It also has similar characteristics related to worms and botnets that enables it to spread very quickly among networks of computers after finding vulnerabilities in the servers.
Being a data-destructive cyber threat, it is difficult to preserve data once the malware enters into your computer! And Xbash malware detects database on Linux and windows to target them.
We also found its functionality with ransomware because it claims to restore data after getting paid by the victims. In other words, we can call it, a multiplatform Xbash malware with self-propagating capabilities and attacking techniques.
Being a new kind of malware, it might become difficult for the users to remove Xbash malware, But, worry not because we have prepared a detailed Xbash malware removal guide to prevent its attack in your computer permanently.
However, before we learn ways to remove the malware, let’s first understand a few sources features and variants that could be present in your computer.
Features Of Xbash Malware
Xbash Malware targets Windows and deletes victim’s MySQL, PostgreSQL and MongoDB databases to get Bitcoins when paid. It has the following capabilities:
- It is a combination of a botnet, coinmining, self-propagation and ransomware.
- It mainly targets Microsoft Windows as crypto ransomware.
- The ransomware component helps the malware to target and delete Linux-based databases.
- There exists no such kind of functionality that could help to recover data through ransom payment.
- Xbash was first developed in Python and then was converted into self-contained Linux ELF executables.
- It targets IP address and domain names, exploits internet services.
- It sends malicious JavaScript or VBScript malicious codes to download and execute a coinminer in computers.
- It has the capability of scanning vulnerable servers which are then used to fetch malicious codes.
- The anti-detection capabilities help the malware to hide from malware removal tools.
- Being a cross-platform malware, it inserts the malicious python modules and compiles them successfully.
- There are approximately 48 incoming transactions related to Xbash wallets which have generated a total income of 0.964 bitcoins, i.e. US $6,000 till now.
- Till now there exist no solid pieces of evidence that the paid ransoms result in the recovery of victims data.
Important Versions Of Xbash Malware
- Ransom.Linux.XBASH.A
- Ransom.Linux.XBASH.AB
- Ransom.Linux.XBASH.AC
- Ransom.Linux.XBASH.AD
- Ransom.Linux.XBASH.AE
- Ransom.Linux.XBASH.AF
- Trojan.JS.POWLOAD.AA
- Trojan.VBS.POWLOAD.A
- Trojan.Win32.INFOSTEAL.TIDAOCN
- Coinminer.Win32.MALXMR.AX
- Coinminer_TOOLXMR.SMB-WIN64
- Coinminer.Unix.MALXMR.AA
Being equipped with different capabilities, Xbash brute forces its way into the system by inserting a weak username and combinations from open ports.
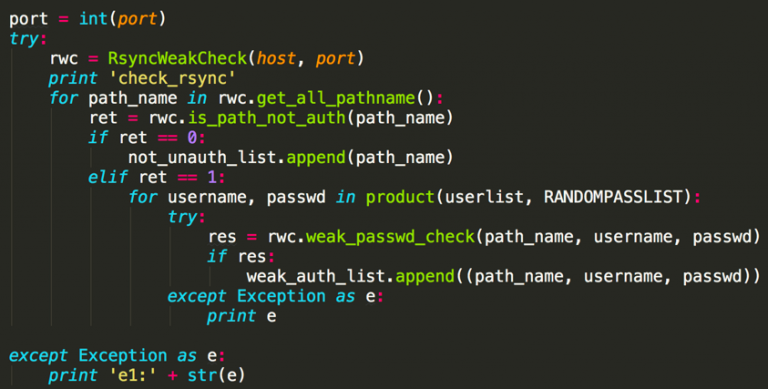
Once you are logged in, the malware deletes the database and creates a new with fake ID and password. After that, it locks the system, modifies the files and asks the victims to pay for ransom.
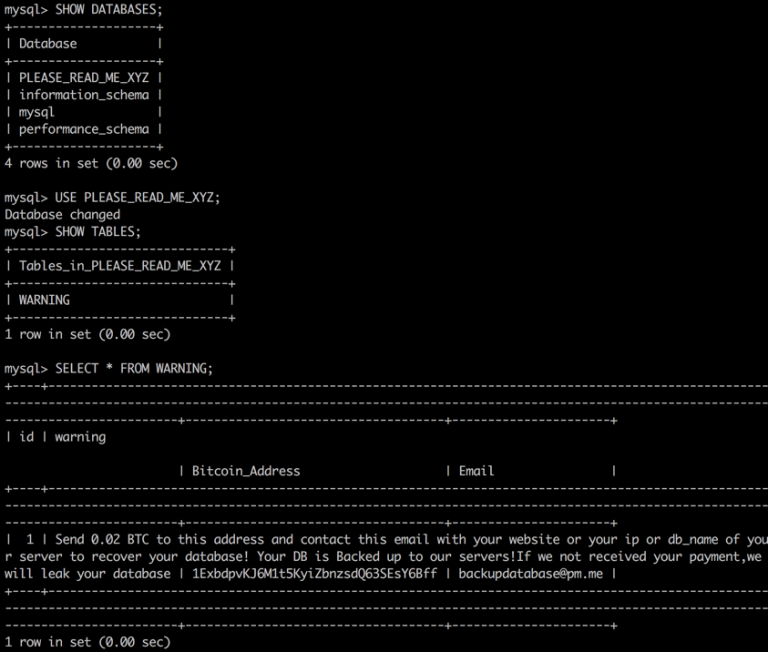
The researchers found malware samples for Windows and Linux which creates binary files while the system becomes vulnerable. Security researchers also found Xbash to be the first malware family bundled with Ransomware, Coinminer and Worms. Cyber experts also predicted that this malware will continue to evolve and might attack the online payment gateways soon.
In order to prevent the attacks, we would highly recommend Malware Crusher against Xbash Ransomware and its coinmining capabilities from protecting your home-based system.

Xbash is an advanced persistent threat that scans IP addresses and chooses their targets based on some criteria (still unknown). Unlike other Iron Group cyber attacks, it seems that making money is the sole motive of cyber attackers from ransomware and cryptomining.
It quickly spreads through spam emails, websites, peer to peer file sharing, freeware (fake software updates), cracked or pirated software and social hijacking. It degrades the computer performance and compels you to pay money for your own files within some time limit.
Once victimized, the attacks get severe, the malware changes web browsers settings and corrupts hard drive of the computer. Applications stop responding and sometimes misses a few important program files. Moreover, there is no way for the victims to know from where the attackers create malicious files and how they enter it into the system.
Hence, we suggest victims follow the below-mentioned detailed Xbash malware removal guide for making your system free from ransomware and cryptominer.
Due to the attacks of this advanced malware, your access to the computer might get blocked. Thus, our first aim would be to unblock your access before you start using an anti-malware tool. Below are few tricks to get entry into your computer.
Unblock Your Computer Access Before Xbash Malware Corrupts Everything
The below malware removal guide has two sections; first performs System Reboot in Safe Mode and second creates System Restore Point.
NOTE: Once you are into your system again, perform a full system scan of the malware removal tool after downloading it. To download it, click here.
Windows Safe Mode Options
Steps to be followed to enter the safe mode Win XP/Vista/7.
- Click start, then shut down, then restart.
- The computer boots up at the very first screen, start pressing the F8 key until you see the advanced boot options.
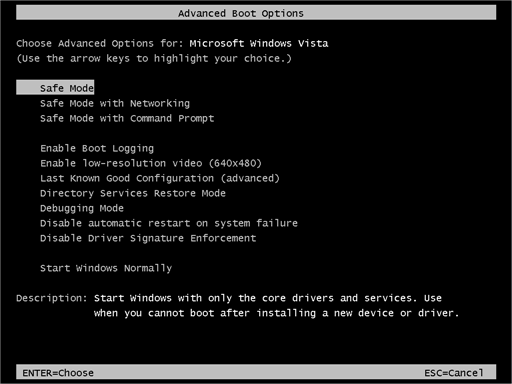
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10.
- On the windows login screen, you need to press the power option.
- Press and hold the shift key on the keyboard, and then click Restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
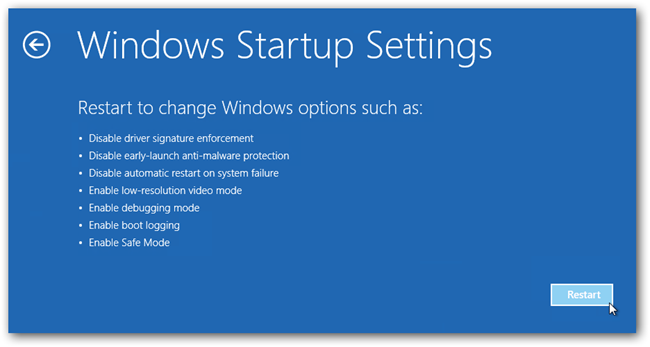
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Windows System Restore
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
- Now, type rstrui.exe and hit Enter again.
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
- Then, click Finish and followed by yes.
Here, the user must understand that the system reboot hadn’t helped you in removing the malware and restore point was created to revert the computer’s state (including system files, registry editors, installed applications, internet settings and system settings).
The above two methods only help you to get your computer back but can’t guarantee if the malware is removed. To prevent its attack, you need to download a removal tool that can prevent your computer from the Xbash malware attacks.
Automatically Prevent Xbash Malware With Tool
The robust technology of any anti-malware tool acts as a security defender for Windows and Linux based systems. And Malware Crusher is a complete PC protection kit in itself whose different removal capabilities are the solution for everyone's cybersecurity need!
Below are the few features to understand the functionality of the tool in better ways to remove Xbash malware;
- It’s real-time protection feature, performs a deep scan to detect malicious software and persistent threats. It also identifies suspicious behavior on your computer.
- The Quarantine feature of the tool removes all infected files from your computer. Additionally, keeps a record of all deleted malicious program and allows you to choose important programs to restore at a later time.
- Malware Crusher also creates a shield against Ransomware, Adware, Malware, Browser Hijackers, Viruses, Extensions and Trojans from entering into your system.
- The 24X7 online protective shield works as an anti-exploit technology and blocks the ransomware component before they hold files as a hostage.
- Malware Crusher tirelessly visits all domains, URLs and web pages to secure your online presence from fraudulent entities. Furthermore, the tool detects the vulnerabilities of online fraudulent entities effortlessly.
- Malware Crusher becomes fiercer in detecting keylogging, remote connections and saving your session data from being recorded.
It is an ever-vigilant free tool dedicated to monitoring the cyber world constantly at your home systems. With its advanced technological development, it deeply diagnoses and neutralizes the threats by writing the antimalware code.
Malware Crusher's 5-minute function could be a savior to remove Xbash malware and continues to exist and update itself against the latest malicious threats!
However, if you wish to follow a manual Xbash malware removal guide then continue reading below.

Manually Remove Xbash Malware Files
The below guide helps you to uninstall programs, end task manager processes and even takes you to Windows registry files where you can manually select and clear suspicious files.
- Press Ctrl + Shift + ESC together to open Task Manager. Look for suspicious files, right click on it and click End Task.
- Now, press Windows key + R to open RUN box window. Type appwiz.cpl on it, this opens Programs and Features window.
- Select each suspicious program and uninstall it one by one. Once the uninstallation is complete, restart your computer and again redirect yourself to Programs and Features window to check whether the application is present or not.
- When convinced, press Windows key + R to open RUN box window. Type regedit on it, hit OK and then click Yes.
- Go through HKEY, HKLM, etc. files and find all suspicious files and delete them.
Finding the suspicious and modified registry files is a difficult task without deep technical knowledge. And if you delete some useful file, your Windows operating system will not work correctly.
Thus, we advise you to use an automatic malware removal tool to prevent the attacks from a cyber threat which is a combination of ransomware, coinminer and botnets.
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
