Ransomware Protection Bypassed Using DLL Injection - Windows 10
Microsoft launched Windows 10 with a protection feature against ransomware called Controlled Folder Access that is used to prevent any modifications to system files in protected folders by an unknown program.
Last week at the DerbyCon security conference, a security expert displayed how a ransomware can use DLL injection to bypass the Controlled Folder Access ransomware security feature.
How a DLL injection can bypass the Controlled Folder Access
Controlled Folder Access is a feature in Windows 10 that permits you to protect files and folders so that any required modification can only be done by a whitelisted application.
The whitelisted applications are the ones that are whitelisted by Microsoft by default or the once that are specified by you.
Soya Aoyama, a security expert at Fujitsu System Integration Laboratories Ltd., seeing that the explorer.exe application is whitelisted in Controlled Folder Access figured out a way to insert a malicious DLL into Explorer when it starts. As the Explorer is whitelisted, the injected DLL will launch and be able to bypass the ransomware security feature.
Aoyama relied on the fact which is to achieve this, it will load DLLs when explorer.exe starts under the HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers registry key.
The HKEY_CLASSES_ROOT tree is a merge of registry information found in HKEY_LOCAL_MACHINE and HKEY_CURRENT_USER. When performing the merge, Windows gives the data in the HKCU tree precedence.

This means that if a key is present in HKCU, it would be preferred over the same key in HKLM, and be the data merged into the HKEY_CLASSES_ROOT tree. We know this can be a bit confusing, so you can go through this document for further details.
By default, when explorer starts it loads Shell.dll from the HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{90AA3A4E-1CBA-4233-B8BB-535773D48449}\InProcServer32 key. To load the malicious DLL into explorer.exe instead, Aoyama simply created a HKCU\Software\Classes\CLSID\{90AA3A4E-1CBA-4233-B8BB-535773D48449}\InProcServer32 key and set its default value to the malicious DLL.
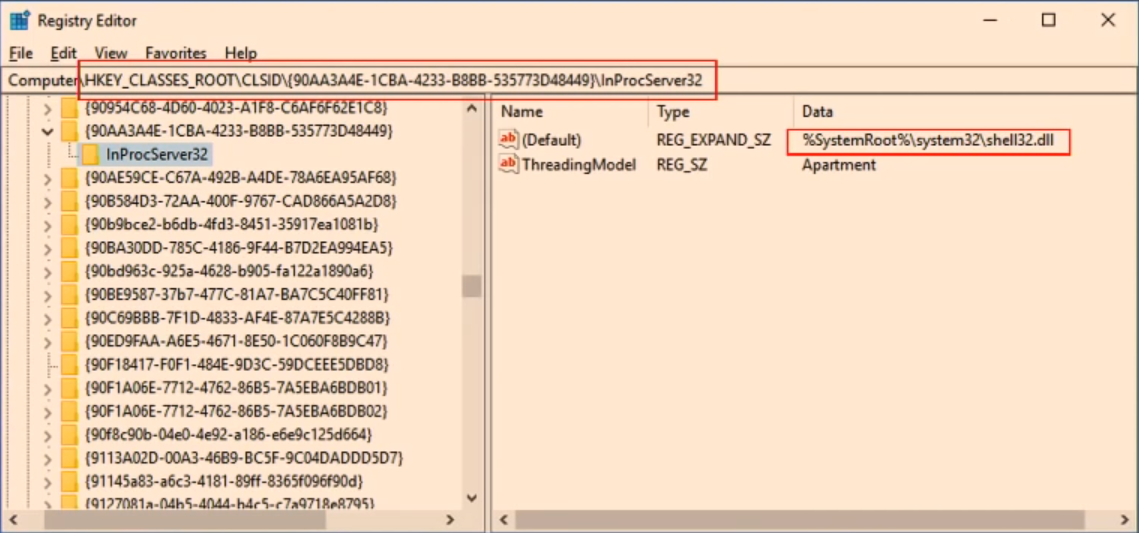
Now when Explorer.exe is terminated and restarted, the malicious DLL will initiate inside explorer.exe rather than Shell.dll. You can see an example of the DLL injected into explorer.exe below.
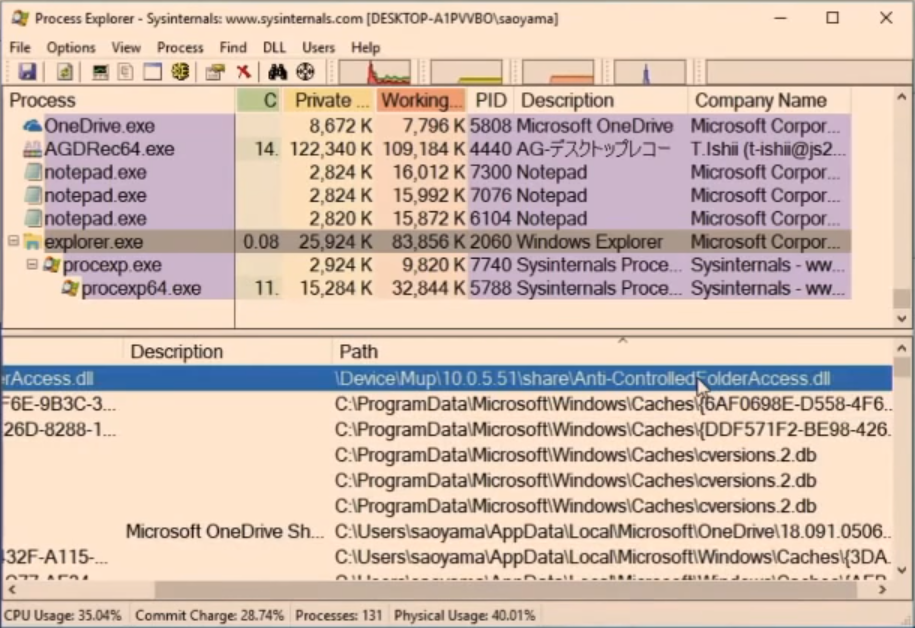
Regrettably, this didn’t just bypass the Controlled Folder Access, but Windows Defender also failed in detecting it. To be honest, according to Aoyama's tests, AV’s that failed to detect are Avast, ESET, Malwarebytes Premium, and McAfee - all of which come with a ransomware protection.
For more detailed information and to see Aoyama's DerbyCon talk and demonstration, you can view the video below.
MSRC responds to a vulnerability report
Aoyama before giving this presentation mentioned that he had responsibly disclosed this vulnerability to Microsoft Security Response Center, with a proof on the concept that can be used to bypass Controlled Folder Access.
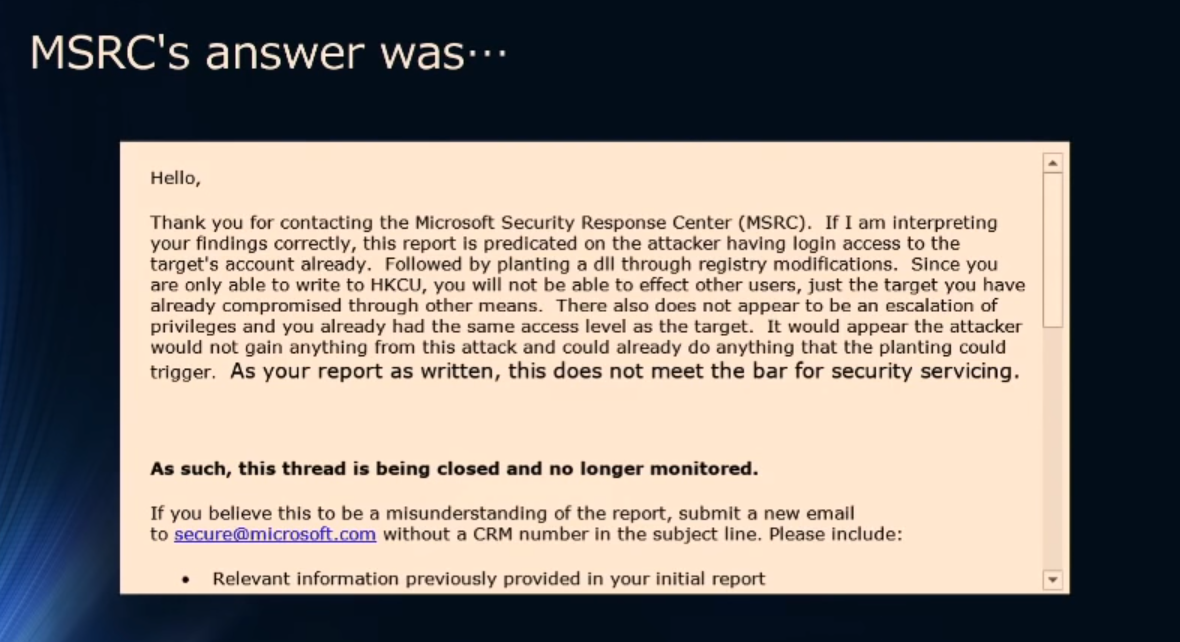
Microsoft, however, didn’t feel that it could be a loophole in their security or that it requires a fix.
"If I am interpreting your findings correctly, this report predicated on the attacker having login access to the target's account already," stated Microsoft's response to Aoyama. "Followed by planting a DLL through registry modifications. Since you are only able to write to the HKCU, you will not be able to affect other users, just the target you have already compromised through other means. There also does not appear to be an escalation privilege and you already had the same access level as the target."
Unfortunately, a ransomware never needed the administrator’s permission to encrypt a victim's computer. Yes, it does need the permission for clearing shadow volume copies, but a malware developer can use other methods or exploit kits to execute vssadmin.
What this does is, it authorizes the malware to install into the system without administrative rights and still be able to bypass the ransomware protection of Controlled Folder Access. And that’s definitely not a good thing.
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
