What is ransomware?

Ransomware is a malicious program designed using crypto virology. This is a kind of malware that blocks you from accessing your own computer or the locked files, and the only way you could get your system back is by paying ransom.
There are two types of ransomware attacks:
1. Encrypting ransomware,
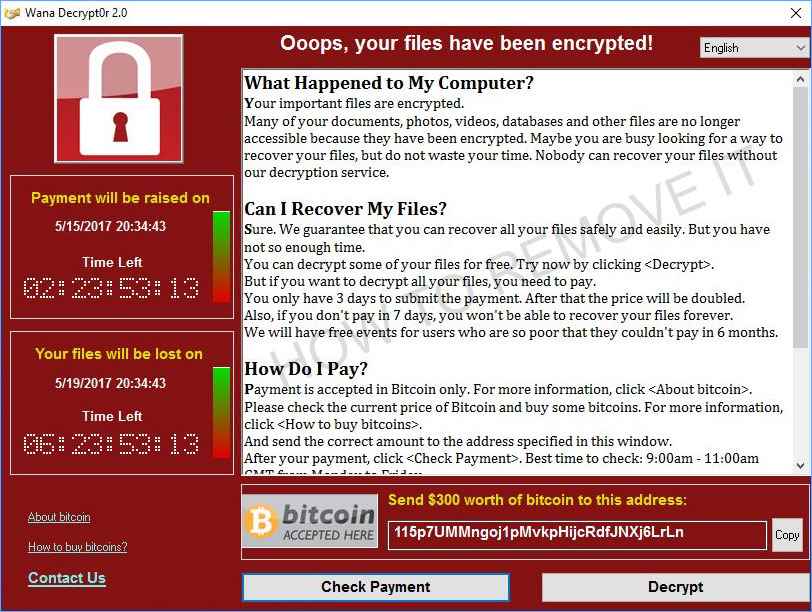
this kind of ransomware uses advanced encryption algorithms. It is scripted to block or encrypt system files and demand money from you to release them and decrypt the files with the key get after paying the ransom. Examples: Crypto Locker, Locky, CrytpoWall and more.
2. Locker ransomware,
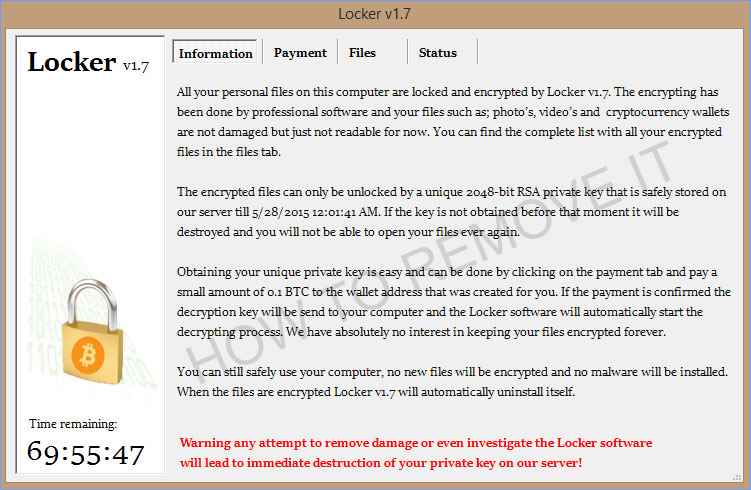
this kind of ransomware would not encrypt your files but block your operating system, which would again ask for a ransom. Examples: police-themed ransomware or Win locker. Some of these locker versions can also lock the Master Boot Record (MBR). The MBR is a section of hard drive were the operating system is located or we can say, it enables the operating system to boot up. When MBR ransomware infects, the boot process wont initiate instead of that it would generate a waring asking for a key to unlock after paying ransom. Examples include Satana and Petya families.
Once Ransomware takes control of the system, it will threaten you with a ransom note asking you to pay the ransom or it will delete all the encrypted/locked files.
Users are shown instructions for how to pay a fee to get the decryption key. The costs can range from a few hundred dollars to thousands, payable to cybercriminals in Bitcoin.
Users are provided with all the instruction on how to make the truncation to acquire the decryption key. The cost of which could vary from hundred to thousand dollars.
Usually the requested amount is in bitcoins, a crypto currency. This makes it really hard for the cyber security department to track them down.
How does ransomware work?
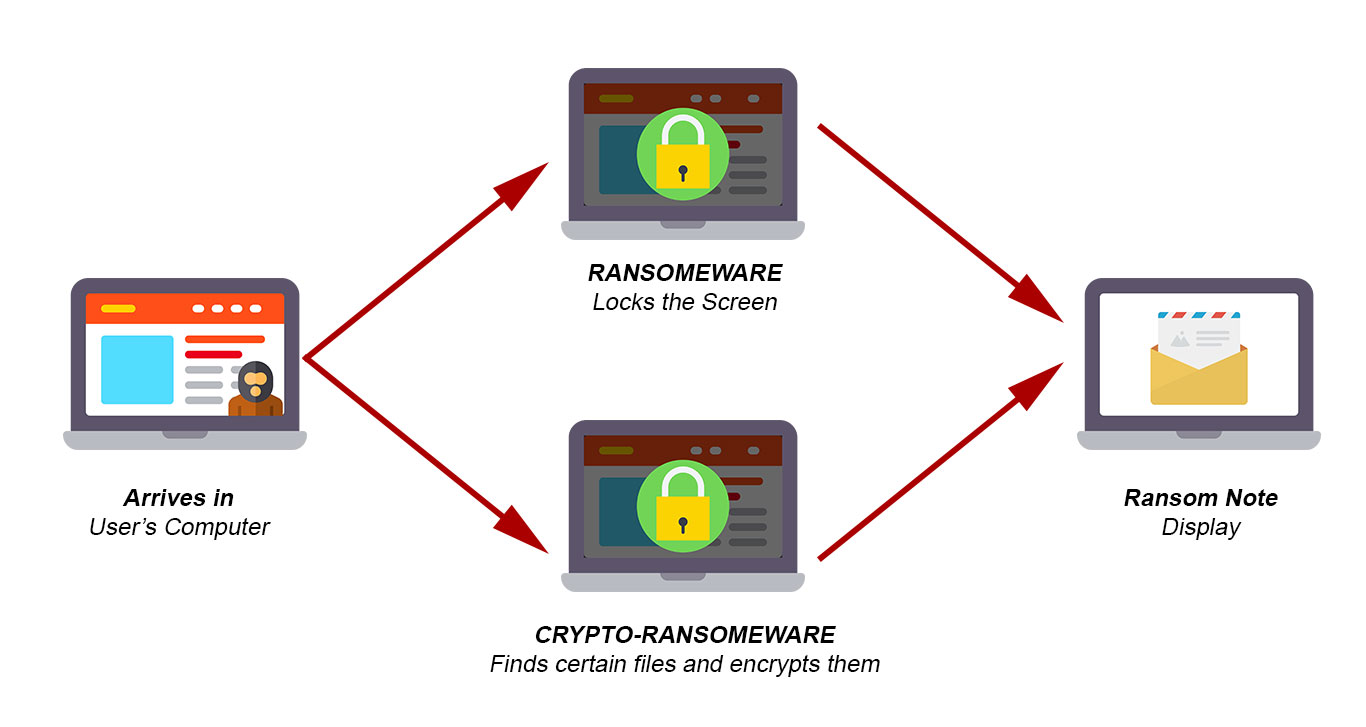
There are multiple ways ransomware could adapt to enter a system without the user’s knowledge. The most common among all is the phishing spam – malicious attachments are sent to the victim via an email.
These emails appear to be from a reputed organization or a well-known bank. Assuming it to be of some importance users open them, which later creates a backdoor for the ransomware.
Once the ransomware is in the system, it would take over the system through social engineering tricking the user to allow administrative rights to it. Some most famous ransomware like Crypto locker and NotPetya takes over the system by exploiting the loopholes in the system.
Undoubtedly, there are several things malware can do once it has taken over the victim's computer, but then again, its major target is to encrypt some important files or all of the user's data.
If you want the technical details, read the complete article for the in-depth details on how multiple ransomware encrypt files.
Experts are still trying to decode the ransomware mechanism. Unfortunately, we have not seen any positive results so far. But, a ransomware solution is mandatory!
So, the only solution to get the encrypted files back is by the decryption key which will be provided by the attackers once the ransom is paid.
In some cases, the cyber-criminals might leave a warning claiming to be from a law enforcement agency and that they are locking down your files due to the presence of adult or pirated content.
They will then charge you for violating the legal policies, this would scare the victim and he would end up paying the ransom instead of reporting it to the authorities. But most criminals don’t follow this trick.
There is also a version of ransomware in which the criminals will threaten to publicize the user data if the ransom is not paid.
What ransomware does after entering the system

Once on the system, ransomware encrypts all the documents and would lock all the information and rename the file extensions. For example, "sample.jpg" may be renamed to a filename, for example, "00A9531D13E7B26BC7E3A84F1414E6AB.extension".
Once the encryption is successful, ransomware leaves a text document with the ransom note in all the encrypted folders.
The folders that were encrypted will now have a text document with ransom note e.g. HELP_INSTRUCTION.TXT. This new document contains a message demanding ransom from the victim for the decryption key and details on how to pay the ransom through cryptocurrency.
At this point, the victims are already running on a deadline. If the ransom is not paid on time, the consequences can be harsh either the amount would be raised, or the user might lose his data.
Decryption requires a decryption key of its kind. Cybercriminals store this key on a remote server and urge the victim to make the payment in the ultimate deadline, or the decryption key will be destroyed, and then no one would be able to retrieve their data.
For now, there is no standard amount, designers of this type of ransomware infections ordinarily request something between $500 and $1500 in Bitcoins.
No matter if the demanded amount is very less, never pay - As per the records a user once attacked has been under attack several times even after paying the ransom.
There is a high possibility that you will be duped again- paying won't result in any positive outcome. Also, you will support digital offenders' organizations. Never endeavor to contact these individuals or pay any payoffs.
Shockingly, at present, there is no program capable of decrypting ransomware, and the only way to retrieve your data is through the backup.
Who is a target for ransomware attacks?
There are a few distinctive ways criminals pick the associations they target with ransomware. At times it's a matter of uncertainty: for example, they may target colleges since they tend to have a basic level of security and a unique client base that completes a considerable measure of file sharing, making it lot simpler and vulnerable to ransomware attacks.
Then again, a few associations become the favorite target since they appear to pay the ransom rapidly. For example, government organizations and medical facilities frequently require prompt access to their documents. Law offices and different associations with sensitive information might pay willingly to maintain their reputation — and these associations might be defenseless against leakware attacks.
But don't feel like you're safe if you don't fit these categories: as we noted, some ransomware spreads automatically and indiscriminately across the internet.
Should you pay the ransom to stop ransomware?
When talking hypothetically, most law implementation organizations will recommend not to pay the ransom demanded, on the rationale that doing as such just urges cyber-criminals to make more ransomware. All things considered, numerous associations that get themselves harrowed by malware rapidly quit thinking about the "greater good" and start analyzing the most cost-effective strategy, measuring the cost of the payoff against the estimation of the compromised information.
As per examine from Trend Micro, while 66 percent of organizations say they could never pay a payment as a state of rule, but 65 percent really do pay the ransom to stop ransomware attack.
Ransomware creators keep costs generally low — more often than not amongst $500 and $1,500, a sum organization can for the most part bear to pay without prior warning.
Some especially advanced malware will distinguish the nation where the contaminated PC is running and modify the payoff to coordinate that country's economy, requesting more from organizations in rich nations and less from those in poor locales.
There are frequently rebates offered for acting quick, in order to urge casualties to pay rapidly before contemplating it. The value point is set, so it's sufficiently high to be justified regardless of the criminal's while, yet low enough that it's regularly less expensive than what the casualty would need to pay to reestablish their PC or gain access to the lost data.
On account of that, a few organizations are starting to manufacture the potential need to pay ransom into their security designs: for example, some vast UK based companies that are generally not involved with digital money are holding some Bitcoin specifically for recovering data from such attacks.
There are a few things you should keep in mind here, remembering that the general population you're managing are, apparently, criminals. To begin with, what resembles ransomware might not have really scrambled your information by any means; ensure you aren't managing alleged "scareware" before you send any cash to anyone.
What's more, second, paying the thieves doesn't guarantee ransomware prevention. Also, there is no assurance you'll recover your documents. More often the offenders just take the money and run and might not have even built decrypting mechanism in the ransomware.
Be that as it may, any such malware will rapidly gain a reputation and won't produce income, most of the time — Gary Sockrider, chief security technologist at Arbor Networks, calculates around 65 to 70 percent of the time — the criminals come through and your information is reestablished.
Ransomware examples
While ransomware has actually been around since the '90s, it's just in the last five years it has gained detection and its reputation. Generally, as a result of the accessibility of untraceable installment strategies like Bitcoin.
A portion of the most exceedingly awful offenders have been:
CryptoLocker, a 2013 assault that propelled the cutting-edge ransomware age and infected up to 500,000 machines at its stature
TeslaCrypt, which focused gaming records and saw steady change amid its rule of fear
SimpleLocker, the primary far-reaching ransomware assault that concentrated on cell phones
WannaCry, which spread self-governing from PC to PC utilizing EternalBlue, an adventure created by the NSA and afterward stolen by programmers
NotPetya, which additionally utilized EternalBlue and may have been a piece of a Russian-coordinated cyberattack against Ukraine
Locky, which began spreading in 2016, was "comparable in its method of assault to the famous saving money program Dridex."
Also, this rundown is simply going to get longer. Indeed, even as this article was being assembled, another rush of ransomware, named BadRabbit, spread crosswise over media organizations in Eastern Europe and Asia.
Things you must know about a ransomware attack

There have been incidents showing the users were hit by the same ransomware for the second time, even though they have already paid the ransom. From here, all that we can say is if you don’t act quickly and the right way, you might not get a second chance.
So, the best ransomware solution is to use the steps given at the bottom of this article.
Ransomware Removal
Temporarily Disable any ransomware in Safe Mode with Command Prompt
Step – 1 (enter safe mode)
1. Steps to be followed to enter the safe mode Win XP/Vista/7
2. Click start, then shutdown, then restart.
3. While the computer is booting up at the very first screen start tapping F8 until you see the advanced boot options.
4. In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10.
1. On the windows login screen, you need to press the power option.
2. Now, press and hold the shift key on the keyboard, and then click restart.
3. Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
4. Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Step – 2 (Restore system)
1. Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
2. Now, type rstrui.exe and hit Enter again.
3. Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
4. Then, click next and followed by yes.
But here's something you should never forget: Following these steps you might get rid of the malware from your PC and restore admin rights, it won't decode your documents.
After temporarily disabling the ransomware, we need to create a strong firewall to fight against such intrusions and prevent them in future.
Hence, always have a ransomware detection and prevention installed in your computer! For the same, team HTRI recommend one of the best Ransomware removal tool (trusted by 10 million users).
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
