Remove Arena Ransomware Without Paying Money
.Arena ransomware is a file-encrypting malware that usually gets inside the system via malicious email and process data encryption.
A new variant of the CryptoMix ransomware should not be confused with CrySiS variant appending .arena extension.
Most of the times ransomware files demand payments in Bitcoins to free your system.
Unfortunately, that’s a rare case because once any ransomware enters into your system, neither you can do anything nor you can sit back and relax.
Once it enters, .id-[ID].sindragosa@bigmir.net].arena file extension blocks other files and encrypt them with ransomware. To fight against this ransomware, you must learn to decrypt arena files.
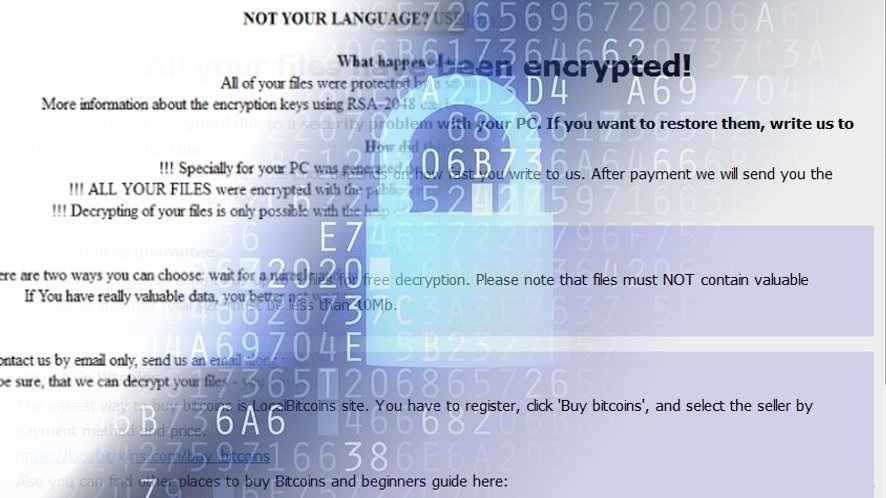
Belonging to a CrySis Family, this ransomware firstly detected in August 2017 has undergone through several updates in arena files.
Encrypted Files Messages
- All your data is locked! Do you want to return? Write email {e-mail address}
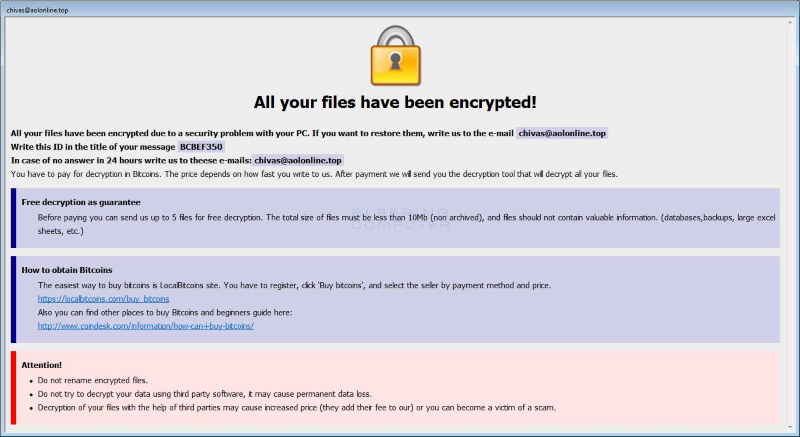
- All your files are encrypted! due to security problems in your PC. to restore, write an e-mail at chivas@aolonline.top
- You have to pay for arena ransomware decryptor files in Bitcoins. The price depends on how early you write to us. After payment is done, we will send you the .arena ransomware decrypt tool to help you get your files back.
- Free decryption as a guarantee. Before paying, send us 5 files for free decryption. The size must be less than 10Mb (non-archived), should not contain any valuable information. (databases, backups, large excel sheets, etc.)
- Attention! Do not rename or edit encrypted files.
- Don’t decrypt your data by using any malware removal tool as it might cause permanent data loss.
- Pay ransom to delete arena files rather than using permanent removal tools.
Almost all the file messages are forcing the victim to contact ransom and to pay the ransom. On the other hand, the messages warn you not to use virus removal tools.

It sounds bit fishy and odd, however, it shows cyber attackers and hackers fear from malware removal tool. We recommend you Malware Crusher to remove .arena ransomware permanently from your system.
Arena Ransomware: Changes and Variants
Different versions of ransomware demand different ransom amounts. This could vary from 0,20 to 0,73 BitCoins approximately equals to $5000.
Cyber Security experts never recommend paying developers of ransomware, as this encourages them to create new variations of the ransomware. Below are few infamous versions of this ransomware;
.id-{id}.[trump123@cock.li].arena
.id-{id}.[VanDamme@aolonline.top].arena
.id-{id}.[mikecoins@qq.com].arena
.id-{id}.[support@decrypt.ws].arena
.id-{id}.[batmanbitka1@cock.li].arena
.id-{id}.[luckyman@cock.li].arena
.id-{id}..[suppyes@cock.li].arena
.id-{id}.[chivas@aolonline.top].arena
.id-{id}.[m.heisenberg@aol.com].arena
.id-{id}.[sindragosa@bigmir.net].arena
Where id stands for 8 digits alphanumeric identification. Ransomware after encryption creates text document files such as FilesEncrypted.txt.
Latest versions of ransomware aren’t decryptable manually; however, there is a chance to restore your encrypted files by decrypting arena files.
Overall the encryption methods are same as the above variants and filename continue to be _HELP_INSTRUCTION.TXT or FilesEncrypted.txt.
When a file is encrypted by the ransomware like .skype ransomware and arena, they modify the filename and append .arena extension.
There are around 1024 encryption keys used to encrypt the victim's files. This let ransomware to work entirely offline with no network communication to hack into the user’s computer.
Victims reports on the ransomware
Recently, we received information from a user victimized from Arena attack. He was asked to pay 2000 euros for data recovery. However, after spending 1000 euros, he didn’t receive any decryption key.
Warning: The creation of .arena ransomware is to fraud the user for money from the computer users. Instead of keeping their promise, hackers demand more money and leaves without giving decrypt files.
Instead of wasting your time and money on deals with cybercriminals, we strongly recommend installing decrypt tool Malware Crusher. It is the easiest and safest method to eliminate the ransomware.
There are two well-known ransomware families - Crysis/Dharma and CryptoMix.
Both append .arena file name extension. CrySis Variant attach .id-[id].[email].arena form while CryptoMix Version edits the file name with a hexadecimal string.
Though at the moment, there is no decryption available for both versions, you can restore the data by deleting arena files.
Unfortunately, ransomware attacks implications are beyond the cost of the ransom and it could let you face;
- Cost of replacing compromised devices
- Loss of proprietary data
- System downtime, which affects the ability to operate
- Reputational damage
- Potential legal penalties arising from poor security or handling of data

Impacts Of Arena Ransomware
It easily spreads through spam emails, websites, peer to peer file sharing, freeware, cracked or pirated software and social hijacking. It degrades the computer performance and compels you to pay money for your own files within some time limit.
Once victimized, the ransomware attacks your system and web browsers settings in the following ways;
- It consumes high CPU power and lowers down the overall performance of your computer.
- The computer boots up for no reason, freezes while you are working.
- Slow internet browsing speed might cause the internet to stop unexpectedly.
- Fake alert messages and notifications pop-ups to asking you to pay the ransom.
- It leads to irrelevant web search redirections and highly affects your web browsing experience.
- It steals your browsing information and personal data such as IP addresses, banking details, passwords and login credentials.
- It also changes your Windows Registry editors to remain undetected from anti-viruses and anti-malware. Automatic download of executable files from unknown sources and unsecured websites.
- Sending emails and maintaining your online presence on Social media though you aren’t logged in.
Cybercriminals via these threats steal information like IP address, URL’s Search, browser history, search queries, username, ID, passwords, banking information and ATM Card information.
Though ransomware removal is a complicated task, it can be completed by removing Arena file extension on your own.
If you do not have any security software, then download a reliable software for Arena ransomware removal. But before that, you can use a few manual methods to see whether they can work against ransomware or not.
Temporarily Disable Arena Ransomware
Windows Safe Mode Options
Steps to be followed to enter the safe mode Win XP/Vista/7.
- Click start, then shutdown, then restart.
- While the computer is booting up at the very first screen start tapping F8 until you see the advanced boot options.
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10.
- On the windows login screen, you need to press the power option.
- Now, press and hold the shift key on the keyboard, and then click restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
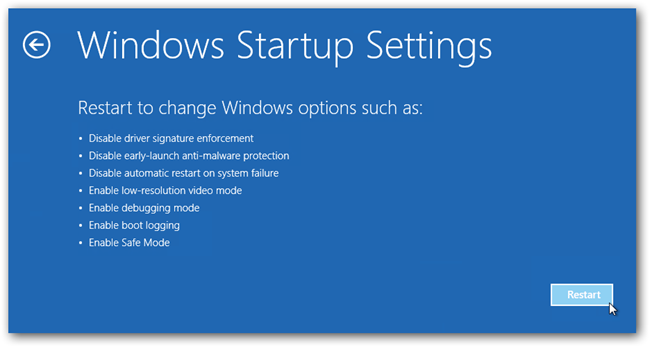
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Windows System Restore
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
- Now, type rstrui.exe and hit Enter again.
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
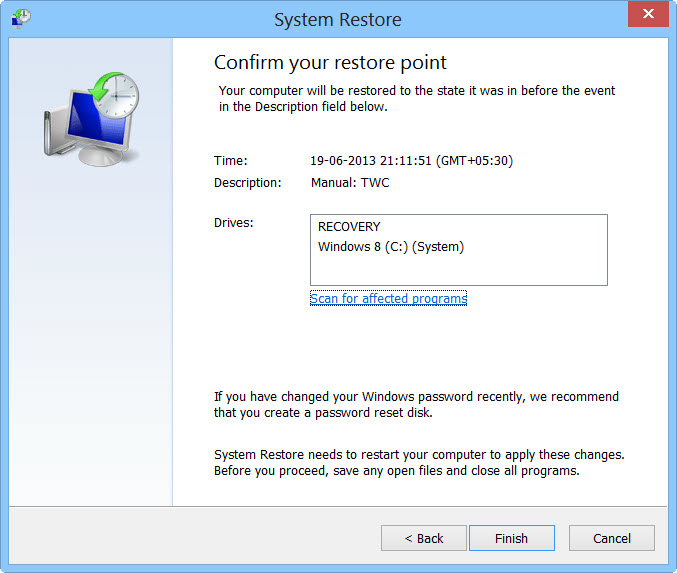
- Then, click next and followed by yes.
But here's something you should never forget: Following these steps, you might get rid of the malware from your PC and restore admin rights, but it won't decode your documents.
After temporarily disabling the ransomware, we need to create a strong firewall to fight against such intrusions and prevent them in future. For this, you must follow the automatic arena ransomware removal tool guide.
Arena Ransomware Removal by Automatic Method
You see a ransomware note after the ransomware infects your system. Instead of paying the ransom you try to solve the issue by uninstalling and removing unwanted programs, registry file editors from your operating system. However, you don't get success and Arena remains on your computer.
The reason is the Encryption - Decryption technique! The ransomware encryption of your files and doesn't allow to access them anymore. That’s why locked files are decrypted using genuine cybersecurity tool.
Malware Crusher is one of those with which you can remove arena ransomware before it collects your information and money.
It can be your permanent ally due to its following removal capabilities;
- It’s a real-time protection feature, performs a deep scan, detects malicious software, infected encrypted files within your system.
- The Quarantine feature of the tool removes all infected files from your computer in addition to keeping a record of all deleted malicious program.
- Malware Crusher becomes fiercer in detecting keylogging, remote connections and saving your session data from being recorded.
- Malware Crusher also creates a shield against Ransomware, Adware, Malware, Browser Hijackers, Viruses, Extensions and Trojans from entering into your system.
- Malware Crusher tirelessly visits all domains, URLs and web pages to secure your online presence from fraudulent entities.

Furthermore, use a cloud storage facility that has high-level encryption and better multiple-level authentication.
To get a better security awareness on cybersecurity threats keep visiting us, forget not to download Malware Crusher. Its 5-minute function could be a savior for your Windows computer.
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
