Rapid Ransomware stays active to encrypt new files
A new ransomware is on the rise called Rapid Ransomware that remains active after encrypting a computer to encrypt any new files that are copied into the system.
While this might not be considered as a unique behavior to Rapid, but this isn’t something we see too often.
it has infected numerous people starting from January. According to the stats, the first case was reported on January 3rd and since then over 300 cases have been reported.
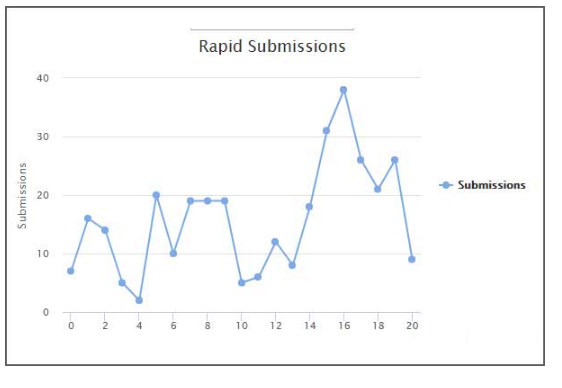
This is probably a small part of the total victims, there are many who most likely did not report the infection.
Feel free to skip ahead if a topic catches your eye:

What is Rapid ransomware?
Rapid ransomware is a file-encrypting ransomware. This ransomware evades the user’s system without their knowledge, after successfully entering the system it will encrypt (lock) the user’s data.
On encryption, it would leave a ransom note demanding the ransom in bitcoins.
On encryption, it will add the .Rapid extension to the encrypted files. It is being moved by third-party infected websites, malicious emails, P2P networks and also through RIG exploit kits.
Once after Rapid ransomware enters a system by tricking its firewall, it will check a PC for data files and encrypt them. While encoding a record, it will attach an extension in the arrangement of name.id-[id].extension. For instance, a record called test.txt would be encoded and renamed to test.txt.Rapid
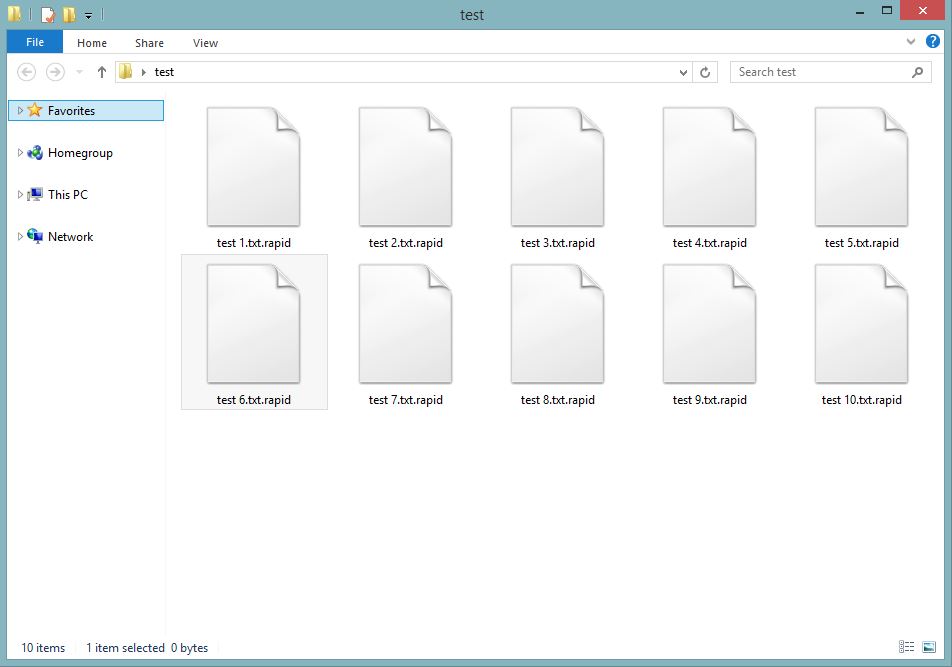
The Rapid ransomware might annex different files extensions depending on the file type audio, video, image, documents, and other files in order to make them inaccessible.
After encrypting the files, it leaves a ransom note that goes by different names. Despite the many names, the ransom note remains the same.
A victim is asked to pay the ransom in Bitcoins, but first, they will have to contact the hackers via one of the email addresses given in the ransom note.
What should be your next move?
By any chance, if you believe that your computer could be infected with this infection, do not hesitate to eliminate ransomware. This is the most straightforward approach to end its movement on your operating system.
If you let this malware remain on your PC, this ransomware can cause significantly more harm by encoding another bit of your documents.
Since quite possibly this infection is back online, we highly recommend you to run a full system scan with Malware Crusher.
Thinking of paying the ransom? Stop thinking, it’s a straight NO!
Despite the fact that we highly suggest not paying the ransom, we understand that a few organizations would not have the capacity to get away without the information that has been put away on the encrypted PCs, so unfortunately in such cases, paying the ransom will be the only option to advance the business.
Also, we can just advice you to not pay the amount. Remember that you can never be sure whether the criminals would give you a working decryption key.
Things you must know about a ransomware attack
There have been incidents showing the users were hit by the same ransomware for the second time, even though they have already paid the ransom.
From here, all we can say is if you don’t act quickly in the right way, you might not get a second chance.
So, the best solution for this is to get rid of the ransomware using the steps given at the bottom of this article.

Temporarily Disable Rapid ransomware in Safe Mode using Command Prompt
Step – 1 (enter safe mode)
- Steps to be followed to enter the safe mode Win XP/Vista/7
- Click start > then shut down > then restart.
- While the computer is booting up at the very first screen start tapping F8 until you see the advanced boot options.
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10.
- On the windows login screen, you need to press the power option.
- Now, press and hold the shift key on the keyboard, and then click Restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Step – 2 (Restore system)
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
- Now, type rstrui.exe and hit Enter again.
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
- Then, click next followed by yes.
IOCs
Hashes:
125c2bcb0cd05512391a695f907669b2f55a8b69c9d4df2ce1b6c9c5a1395b61
Files Associated with the Rapid Ransomware:
%AppData%\info.exe
%AppData%\How Recovery Files.txt
%AppData%\recovery.txt
Registry Entries Associated with the Rapid Ransomware:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Encrypter"="%AppData%\info.exe"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "userinfo"="%AppData%\recovery.txt"
Rapid Ransomware Email Addresses:
frenkmoddy@tuta.io
jpcrypt@rape.lol
support@fbamasters.com
unlockforyou@india.com
rapid@rape.lol
fileskey@qq.com
fileskey@cock.li
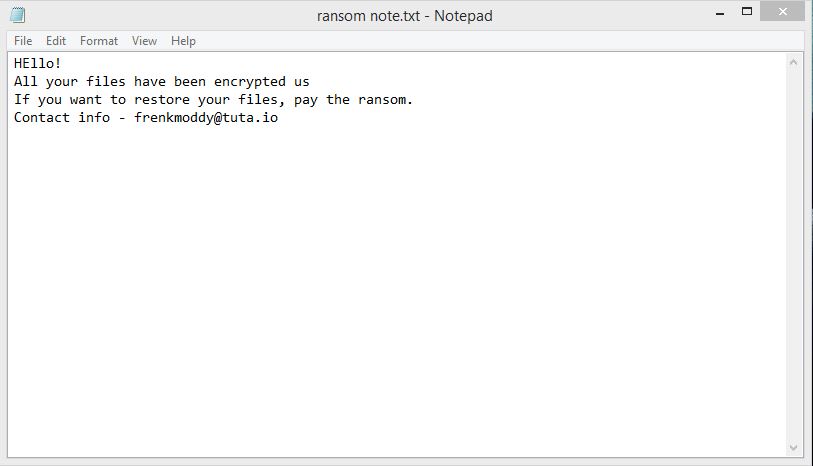
Rapid Ransomware Ransom Note:
Hello!
All your files have been encrypted us
If you want to restore your files, pay the ransom.
Contact info - frenkmoddy@tuta.io
After temporarily disabling the ransomware, we need to create a strong firewall to fight against such intrusions and prevent them in future.
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
