What is IT.Books Ransomware and How to Remove it?
IT.Books is a cryptovirus that encrypts the system files and demands money as a ransom in order to restore the encrypted files. Also, the .fucked extension is added to the encrypted files. Followed by the encryption IT.Books ransomware leaves a ransom note in the form of a text file and also pops up a GUI interface screen for more details which has a theme similar to that of Jigsaw ransomware.
As the article advances you will come to know how the ransomware infected your system, followed by various removal techniques you can follow to eliminate the threat.
IT.Books Ransomware – Distribution Methods
As witnessed the IT.Books ransomware distributes itself using multiple mechanisms. A payload dropper that kick-starts the malicious script of this ransomware is been distributed around the World Wide Web, and experts have acquired a malware sample. By any chance if the file happens to be on a system and if the user clicks on it just to see what kind of file it is, the system gets infected by the ransomware.
To achieve persistence IT.Books ransomware might make entries in the Windows Registry, and could repress or launch processes in a Windows environment. Such entries are logged so that the ransomware can start automatically every time the Windows boots up.
The ransom note left behind is named as ‘READ__IT.txt’ and contains the following info:
Files has been encrypted with strong KEY
Send payment to our bitcoin address
you can visit google or local bitcoin to buy bitcoin.
BTC Address: 13vs2K5TiDAn6eLSevnds8esWZfeUhov2d
After payment click contact us you will receive Decryption KEY in less than 1 hour.
Additionally, with the ransom note, there are other instructions provided by the cyber-criminals inside the GUI interface that looks exactly like the one of Jigsaw ransomware, as shown in the below image:
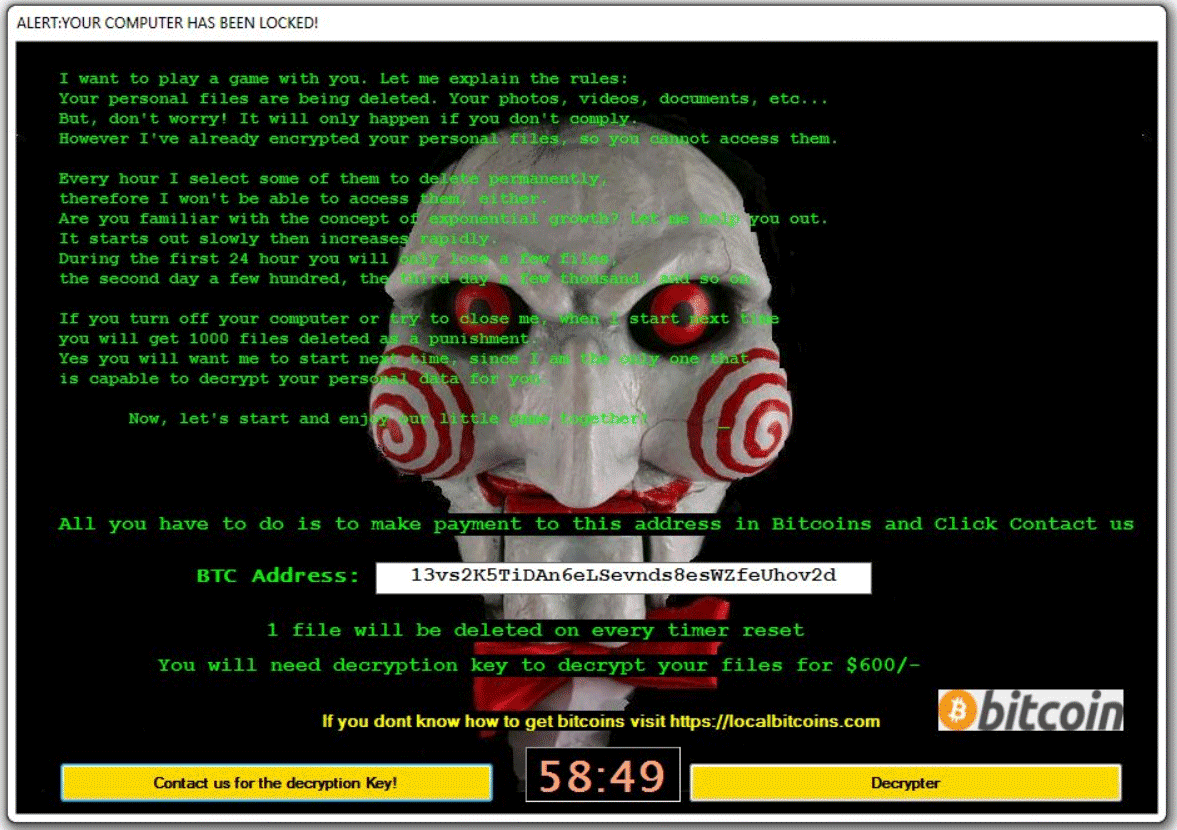
The message displayed above, coming from IT.Books ransomware virus, says that your files are encrypted. You are demanded to pay “600 US dollars” to get your files back.
What should be your next move?
By any chance, if you believe that your computer could be infected with this infection, do not hesitate to eliminate IT.Books ransomware.
This is the most straightforward approach to end its movement on your operating system.
If you let this malware remain on your PC, this ransomware can cause significantly more harm by encoding another bit of your documents.
Since quite possibly this infection is back online, we highly recommend you to run a full system scan with Malware Crusher.

Thinking of paying the ransom? Stop thinking, it’s a clean no!
Despite the fact that we highly suggest not paying the ransom, we understand that a few organizations would not have the capacity to get away without the information that has been put away on the encrypted PCs, so unfortunately in such cases, paying the ransom will be the only option to advance the business. Also, we can just advice you to not pay the amount.
Remember that you can never be sure whether the criminals would give you a working decryption key.
Things you must know about a ransomware attack
There have been incidents showing the users were hit by the same ransomware for the second time, even though they have already paid the ransom.
From here, all that we can say is if you don’t act quickly and the right way, you might not get a second chance.
So, the best solution for this is to get rid of the ransomware using the steps given at the bottom of this article.
Remove IT.Books Ransomware in Safe Mode with Command Prompt
Step – 1 (enter safe mode)
- Steps to be followed to enter the safe mode Win XP/Vista/7
- Click start, then shut down, then restart.
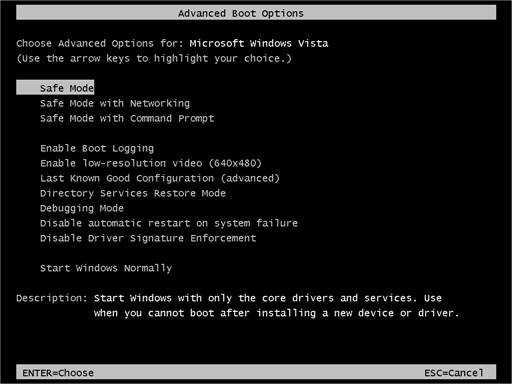
- While the computer is booting up at the very first screen start tapping F8 until you see the advanced boot options.
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
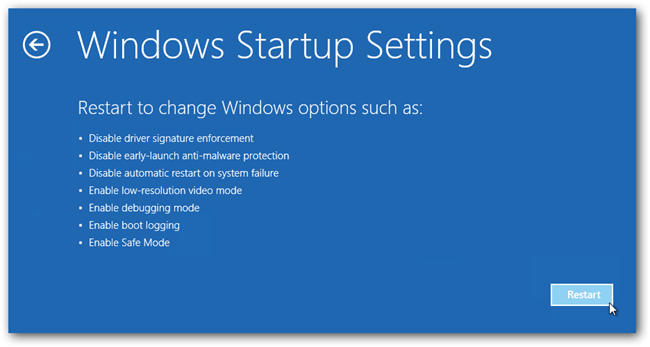
Steps to be followed to enter safe mode in Win 8/10.
- On the windows login screen, you need to press the power option.
- Now, press and hold the shift key on the keyboard, and then click Restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Step – 2 (Restore system)
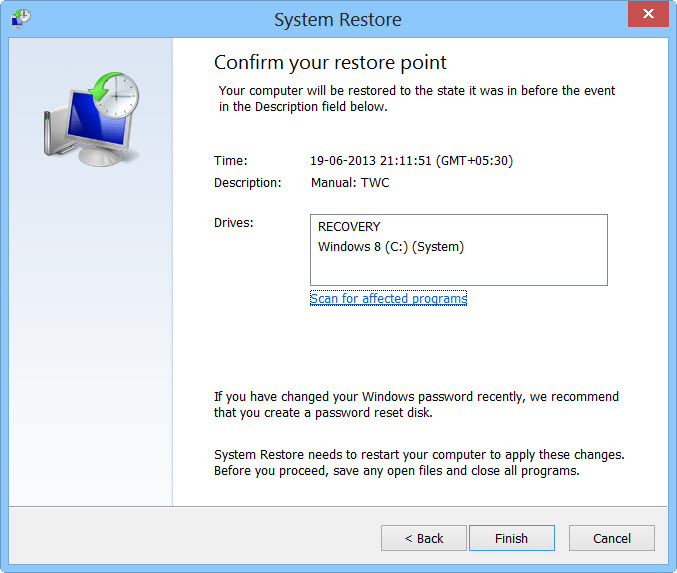
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
- Now, type rstrui.exe and hit Enter again.
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
- Then, click next and followed by yes.
After temporarily disabling the ransomware, we need to create a strong firewall to fight against such intrusions and prevent them in the future.
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
