Krab Ransomware - New Variant of GandCrab Ransomware
Malicious programs are the worst cyber threat that you meet on the internet. Web criminals keep on stuffing malicious links/URLs and download buttons which when accessed installs scareware, keylogger software and ransomware.
It is important to understand how ransomware enters into the network servers to our systems despite your default internet security. Many times, your files get lost and you never get a chance to understand the functioning, infection and effects of the ransomware.
GandCrab ransomware is back with its new 4th version named Krab Ransomware that encrypts a file and has made several computer users its victim. To make it easier, you can take a look at the below table of contents.
Most cybercriminals threaten users and take advantage of them to raise the amount (in cryptocurrencies and dollars). It spreads via malicious spam emails, attachments, links and most of the time; it removes Windows registry files to cut down the victim's computer performance.
This article walks you through a stepwise process to prevent Krab ransomware from your system. Therefore, we would suggest you to follow this ransomware removal guide.
How GandCrab V4 Krab Ransomware Works?
Krab is a new variant of GandCrab and like all other ransomware, it is also file-encrypting ransomware that without your knowledge evades the system; mostly windows operating system. Once it makes a successful entry to the system, it encrypts (lock) the most stored files.
The new locked text files contain a message. It is a ransom note that informs victims about encryption and encourages them to visit cyber attackers for solutions.
The ransom note of encrypted files, typically states that your files are encrypted and you musn't pay the Bitcoin or DASH cryptocurrencies to get them restored. However, research security experts are not in favor of paying ransomware. Their strict guideline is: Never pay any cyber threat.
A ransomware lands on your network from C2 servers, inject itself in your computer and encrypts the text files, audio-video, docs, pdf, saved web pages and many more other data files. The ransomware adds .KRAB extension, change the file name.
For example, test.doc is encrypted and renamed to test.doc.KRAB.
It means your doc file named test is now locked from Krab ransomware. Whenever a user tries to open the compromised or locked file, it displays a ransom note CRAB-DECRYPT.txt
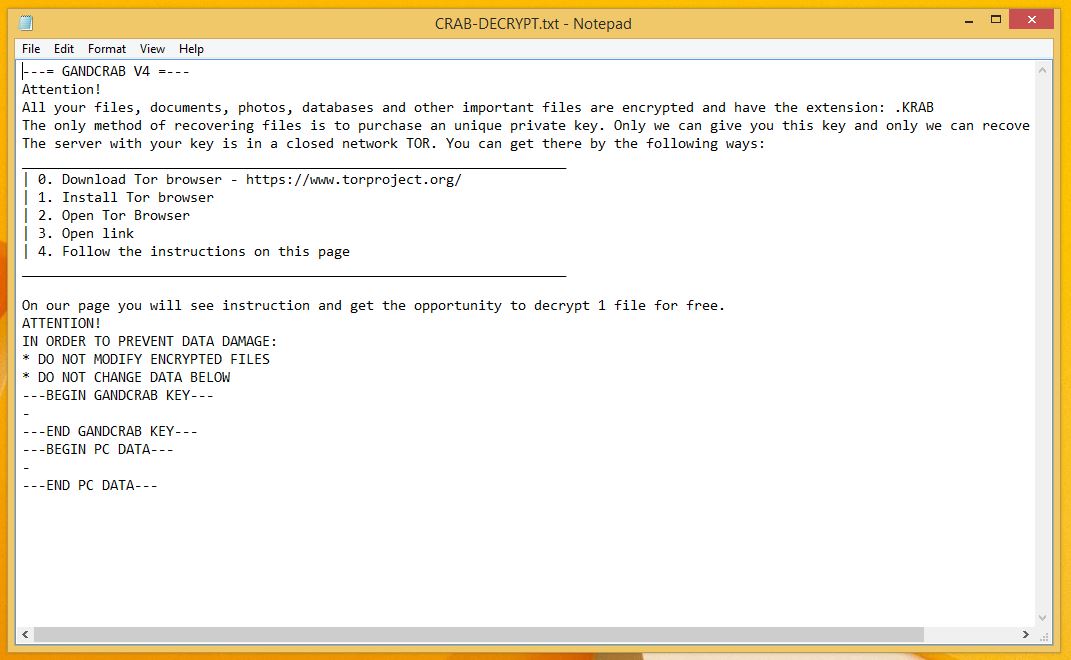
As you saw, the hackers via ransom note demand money to give you Krab Ransomware decryptor tool. If the payment is not submitted within the time frame, the demanded money will double up.
However, there is no need to pay money after reading the note. We recommend this because the developers won’t give you .KRAB files decryptor and your money will go waste.
Recently, we received information from a victim of GandCrab attack. He was asked a heavy amount for the data recovery. But, cyber attackers fooled him, even didn’t gave him the required decrypting keys.
Moreover, during research, it was also found that the ransomware is distributed from fake software crack tools and crack sites like Crack_Ghost_Mouse_Auto_Clicker.exe.
We recommend using an anti-malware tool like Malware Crusher against the ransomware variant that is capable to prevent the entry of this high-class infection

Effects Of Krab Ransomware
The Krab Ransomware infected computer shows the various number of nasty irritating effects as given below:
- It carries many types of cryptovirus variants, remains undetected which an ordinary antivirus tool cannot locate.
- It posses keyloggers to monitor your keystrokes, additionally sends information to hackers. It also steals your sensitive and financial information.
- Copycat Look: Developed in a manner that it represents an original program to cheat innocent users, but doesn’t contain any genuine features of the application.
- After entering into the system, it remains in the memory of the system and automatically gets executed.
- Fake scanning property: It performs bogus system scanning on the screen and shows fake results.
- Transferable: It easily duplicate itself and transmit from one infected system to another via network vulnerabilities and security checkup loopholes.
The infections are intrusive and also spy on the system. Furthermore, keeps an eye on our activities before blocking access to the system. Thus, it is important to remove krab ransomware from the system.
Cybercriminals via these threats steal information like IP address, URL’s Search, browser history, search queries, username, ID, passwords, banking information and ATM Card information.
Krab Ransomware Encrypted Files Messages
- All your data is locked! Do you want to return? Write email {e-mail address}
- You have to pay for ransomware decryptor files in Bitcoins. The price depends on how early you write to us. After payment is done, we will send you the decrypting tool to help you get your files back.
- Free decryption as a guarantee. Before paying, send us 5 files for free decryption. The size must be less than 10Mb (non-archived), should not contain any valuable information. (databases, backups, large excel sheets, etc.)
- Attention! Do not rename or edit encrypted files.
- Don’t decrypt your data by using any malware removal tool as it might cause permanent data loss.
- Pay ransom to recover encrypted files rather than using permanent removal tools.
Almost all the file messages force the victim to contact ransom and to pay the ransom. On the other hand, you should get warned from these messages.
Latest versions of the ransomware weren’t decryptable manually; however, there is a chance to restore your encrypted files if you follow the process mentioned in this guide.
Unlock Computer In Safe Mode with Command Prompt
Steps to be followed to enter the safe mode Win XP/Vista/7
- Click start, then shut down, then restart.
- While the computer is booting up at the very first screen start tapping F8 until you see the advanced boot options.
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10
- On the windows login screen, you need to press the power option.
- Now, press and hold the shift key on the keyboard, and then click Restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Restore System
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
- Now, type rstrui.exe and hit Enter again.
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
- Then, click next and followed by yes.
At present, your computer is in a state that has its file and data backed up at a safe restore point. We also suggest you to make a copy of your backed up data into some external hard drive.
It is now time, to reinstall your Windows via an external source such as pen drive, CD or DVD.
While installing Windows, allocates disk space to C,D and E drive. If asked to restore any files, select the restore point and get the backed up data into the new operating system.
Your system format is complete, also your data is backed up. Now you must create a strong firewall against such malicious threats to prevent the future attacks.
If you do not have any security software, then download Malware Crusher to prevent Krab ransomware attacks.

Prevent Entry Of Krab Ransomware
Malware Crusher is the most commonly used anti-malware software for the Windows computer. It’s malware removal capabilities makes it the most impactful tool and prevents you before the ransomware starts infecting your system because:
- It’s real-time protection feature, performs a deep scan, detects malicious software and infected encrypted files within your system.
- The Quarantine feature of the tool removes all infected files from your computer. Additionally, keeps a record of all deleted malicious program.
- Malware Crusher also creates a shield against Ransomware, Adware, Malware, Browser Hijackers, Viruses, Extensions and Trojans from entering into your system.
- The 24X7 online protective shield works as an anti-exploit technology and blocks the ransomware component before they hold files as a hostage.
- Malware Crusher tirelessly visits all domains, URLs and web pages to secure your online presence from fraudulent entities.
- Malware Crusher becomes fiercer in detecting keylogging, remote connections and saving your session data from being recorded.
To get a better security awareness on preventing cyber attacks and cyber security threats keep visiting us, forget not to download Malware Crusher.
Its 5-minute function could be a savior for your Windows computer!
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
