Notopen@cock.li Ransomware - Detailed Analysis
A new variant of Everbe 2.0 ransomware dubbed as notopen@cock.li ransomware is a new open source threat among many countless ransomware that encrypts files to extort money from the users.
It storms through the files kept in the targeted computer and always blocks the user access via a strong encryption algorithm. Like other ransomware, it also uses AES technique to lock files and afterwards demand money via a ransom note.
Most cybercriminals threaten users and take advantage of them to raise the amount (in bitcoins and dollars). It spreads via malicious spam emails, attachments, links and most of the time; it removes Windows registry files to cut down the victim's computer performance.
The only solution to make your system functioning properly is by eliminating notopen@cock.li ransomware with a trusted anti-malware application. For this, we have designed a stepwise ransomware removal guide which not only protects you from paying but also annihilates the threat.
If you are an infected victim of the ransomware, then this guide will surely help you before your computer goes more vulnerable. However, let’s first understand how this ransomware works? How it spreads? And what could be its possible symptoms?
How Does notopen@cockl.li Ransomware Work?
Ransomware is a malicious threat of cryptovirology that takes over your computer, denies you to access your data, harms your system and then demands ransom. Eventually, being related to Arrow, Dharma and Everbe ransomware, notopen ransomware also follows the basic anatomy of ransomware attack.
In the first phase Deployment, the threat enters into your system and exploits the internet vulnerabilities. Afterwards, spreads itself through phishing emails, spam messages and drive-by downloads. Sometimes the adware and browser hijackers also let the entry of the ransomware.
Once a malicious payload delivers into the victim's system, the second phase, Installation starts. A small piece of code installs in the system via a dropper methodology which keeps the ransomware undetected.
In case of Windows system, ransomware set keys in the Windows registry files to ensure that the code starts every time with the computer. When an attack is targeted, the nefarious activities like installation, code-packing and exploitation helps the ransomware to spread slowly throughout the affected network.
Following installation, the ransomware needs a C2 server to connect with its developers. This server is a simple web-based communication that directly sends other variants of the ransomware to the victimised system. Likewise, ransomware reports back the victim's confidential information such as IP address, banking credentials and more.
The ransomware also receives keys from the ransomware developers via C2 server to lock files. Along with the files, a bunch of code injects into the victim’s system and encrypt the files. Following encryption, [.]NOT OPEN file extension appends to each file.
Now user can’t access the file and must use notopen@cock.li ransomware decryption keys. These keys unlock the file and are present on the same command and control server. To notify the user about encryption and decryption, cyber attackers launch a ransom note whenever a user tries to access the locked file.

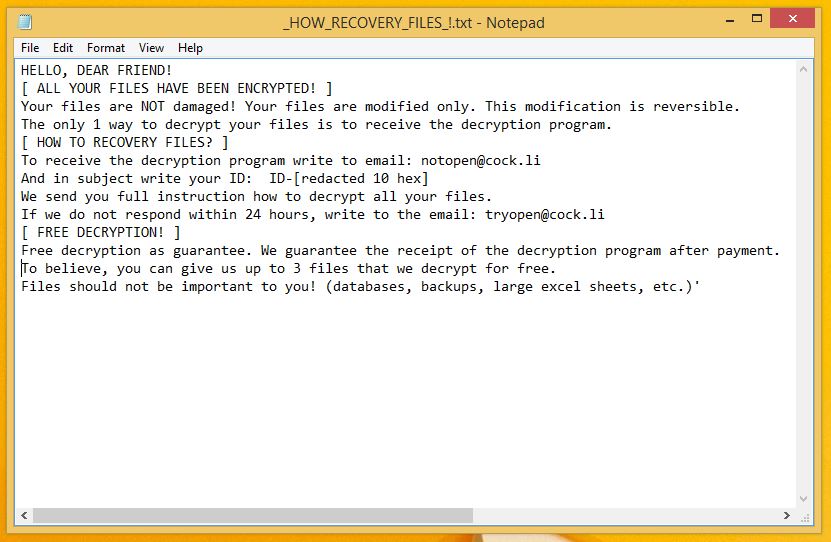
The Ransom Note Says
Your access to file is not authentic. Your files are locked but not damaged! Thus, to recover your files you must buy notopen@cock.li ransomware decryption keys and must write an email to notopen@cock.li. Otherwise, your system will compromise from the virus.
However, the story is far away from reality. The ransomware has already compromised your system due to which your files are locked. More importantly to get them back or to recover them you now need to pay ransomware developers.
The anatomy of notopen@cock.li ransomware starts with the deployment of ransomware and ends after extorting money from the user.
But if you get the chance not to pay the ransom then possibly it would be a win-win situation, i.e. Neither you need to contact cyber attackers nor required to email them. To bring it in practice, it is essential to delete notopen@cock.li ransomware without harming your computer.
For this, we have made a removal guide solely dedicated to remove notopen@cock.li ransomware.
- Unlock Your Locked Computer
- Automatic Preventive Method
- Manual Preventive Methods
Unlock Your Locked Computer
Ransomware is a very dangerous threat that sometimes even locks you out of your computer. Every time you start the computer, it freezes on the start window. In order to get in, you must reboot your system in safe mode. For this, you need to follow the below process;
- Start your computer and instantly press F8 repeatedly to enter Advanced Boot Options.
- Log on the computer as the Administrator.
- Change or remove your computer’s forgotten password in Control Panel and enable the safe mode options.
Once you have access to your computer, you can follow preventive methods to prevent the attacks of ransomware. We first will start with the automatic method.
Automatic Preventive Method
Malware Crusher is the most commonly used anti-malware tool for the Windows computer. And ransomware mostly impacts windows based computer.
Following are the removal capabilities of the tool that makes it the most watchful tool in preventing your system before the ransomware starts spreading infection;
- It’s real-time protection feature, performs a deep scan to detects malicious software, persistent threats and suspicious behaviour on your computer.
- The Quarantine feature of the tool removes all infected files from your computer. Additionally, keeps a record of all deleted malicious program and allows you to choose important programs to restore at a later time.
- Malware Crusher also creates a shield against Ransomware, Adware, Malware, Browser Hijackers, Viruses, Extensions and Trojans from entering into your system.
- The 24X7 online protective shield works as an anti-exploit technology that blocks the ransomware component before they hold files as a hostage.
- It tirelessly visits all domains, URLs and web pages to secure your online presence from fraudulent entities. Furthermore, the tool also detects the vulnerabilities of online fraudulent entities effortlessly.
- It becomes fiercer in detecting keylogging, remote connections and saves your session data from being recorded.
Malware Crusher is continuously monitoring the happenings of the cyber world. In response to the new malicious codes and javascript, the tool writes anti-malware code, diagnose ransomware and neutralize the ransomware attack. Hence, affected notopen@cock.li ransomware file recovery becomes possible.
On the other hand, manual methods can’t go deep into cleaning. However, you as a user has the liberty to follow few manual preventive methods like uninstalling programs, ending the task manager process, clearing browsing history etc.

Manual Preventive Methods
- Press Ctrl + Shift + ESC together to open Task Manager. Look for suspicious files, right click on it and click End Task.
- Now, press Windows Key + R to open RUN box window. Type appwiz.cpl on it, this opens Programs and Features window.
- Select each suspicious program and uninstall it one by one. Once the uninstallation is complete, restart your computer and again redirect yourself to Programs and Features window to check whether the application is present or not.
- When convinced, press Windows key + R to open RUN box window. Type regedit on it, hit OK and then click Yes.
- Go through HKEY, HKLM, etc. files and find all suspicious files and delete them.
- You can also delete malicious extensions from your browsers like Chrome and Firefox.
1. Click on the Customize and control menu icon at the top right corner of Google Chrome.
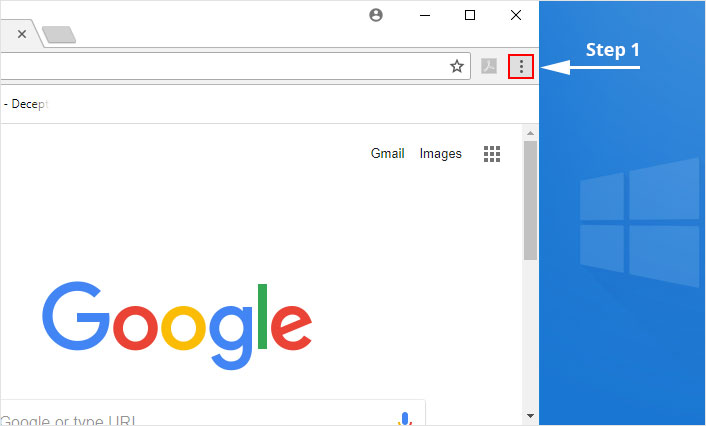
2. Select "More tools" from the menu.
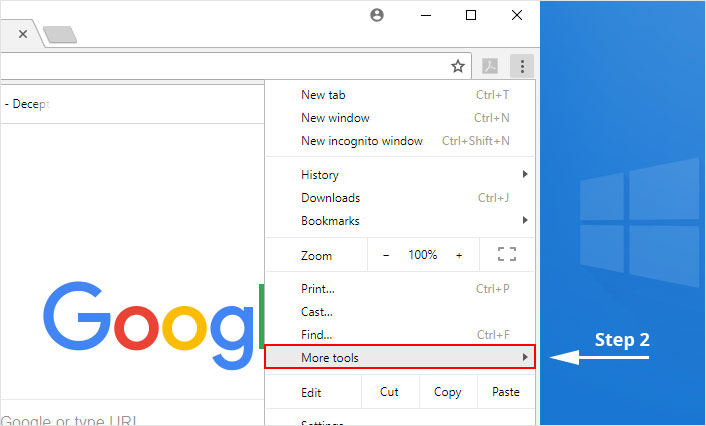
3. Select "Extensions" from the side menu.
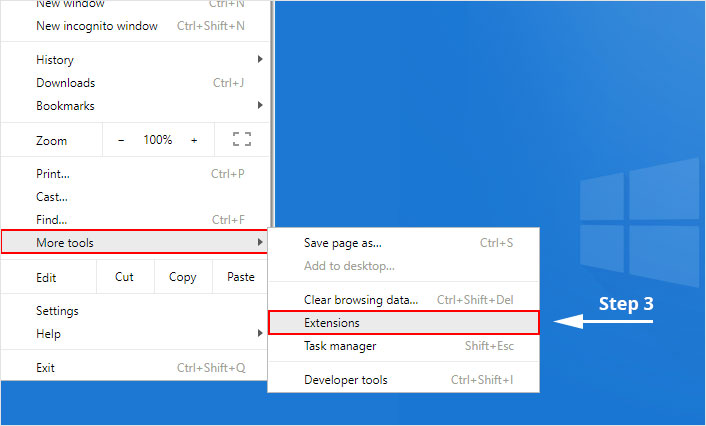
4. Click the remove button next to the extension you wish to remove.
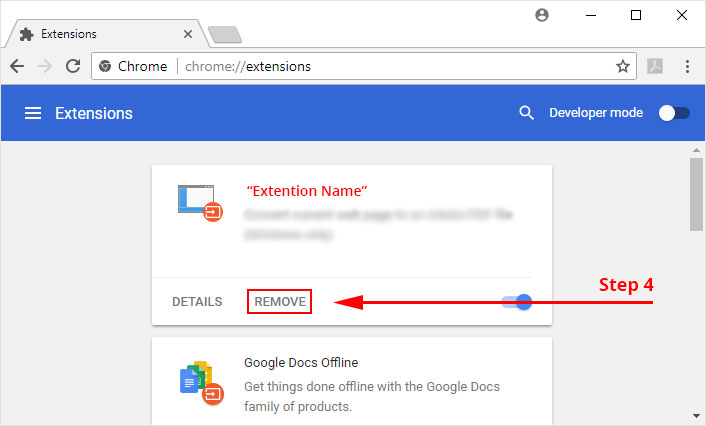
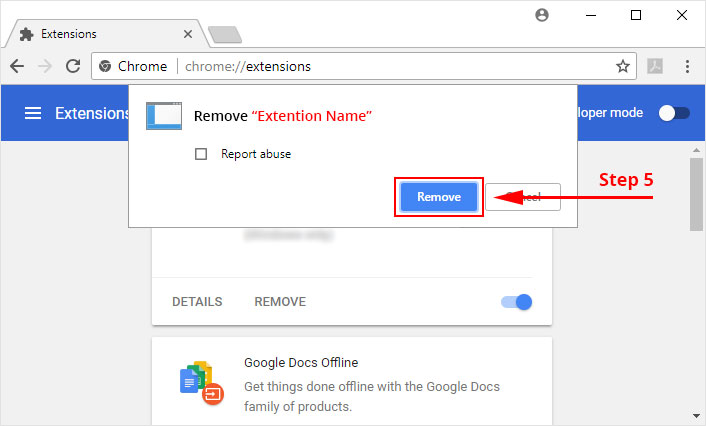
5. It will confirm again, click “remove” and the extension is finally out of the system.
Now that we have successfully eliminated the malicious browser extension, we need to create a robust firewall to avoid any such thing that makes our system and privacy vulnerable to various online threats.
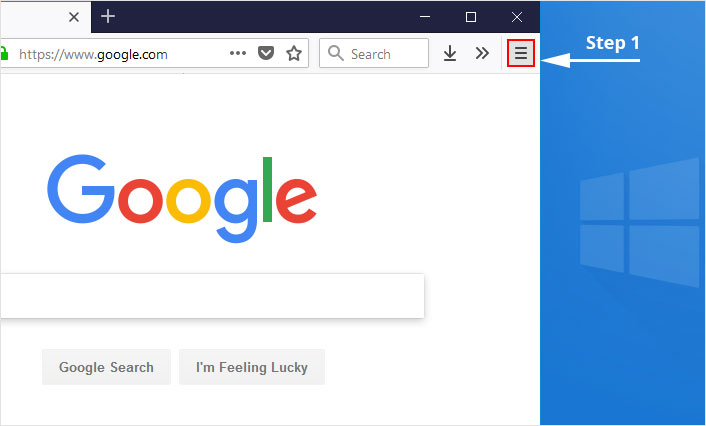
1. Click on the “menu” button at the top right corner.
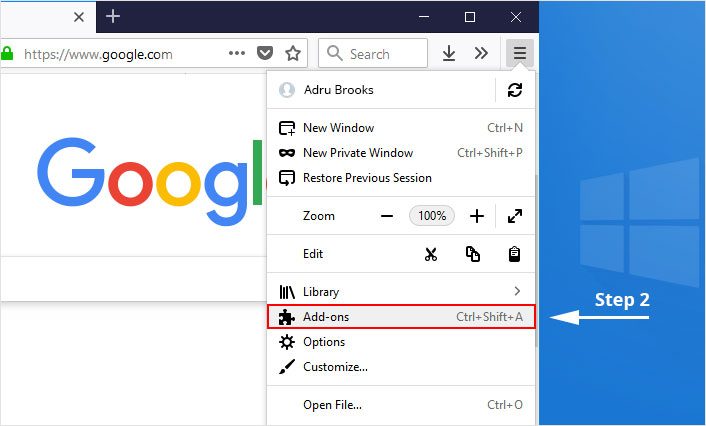
2. Select “Add-ons” from the menu.
3. Click the “Remove” button next to the extension you wish to get rid of.
Now that we have successfully eliminated the malicious browser extension, we need to create a robust firewall to avoid any such thing that makes our system and privacy vulnerable to various online threats.
The manual methods sometimes might not work at Windows OS because finding suspicious and modified registry files in registry editors is a difficult task. On the other hand, if a useful file is deleted, the windows stop working properly.
That’s why it is highly recommended to use an automatic tool to prevent ransomware attacks on your computer. If you wish to get more news and awareness on the happenings of the cybersecurity, then keep visiting us.
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
