Phobos Ransomware - A New Variant Of CryptoVirus Trojan
Few ransomware families like Cryptomix, Reveton, Sam Sam, etc aims to get bitcoins and dollars from the users. Not these families but every ransomware creates a situation where user get down to their needs and pay them to unlock those files which ransomware locks using an encryption algorithm.
It is not that hard to understand how ransomware enters into your system, encrypt (lock) files and further notify you their payment scheme for decrypting (unlocking) files.
However, if a user becomes little technical by learning about ransomware in a few minutes, then it would help the user in defending against the ransom families and their variants.
This article briefs you technically on Phobos Ransomware which nowadays is infiltrating systems. Here, we let you walk through a ransomware removal process which encapsulates manual preventive methods and a robust tool that fights with the ransomware.
Is Phobos Ransomware Safe?
Phobos ransomware is a high-risk encryption type virus first observed on October 2017. If few cybersecurity reports call it a cryptovirus, then some calls it a new variant of the file-locking virus.
However, like all other ransomware, it also blocks user’s access and maliciously infects files concerning an important matter to you. This ransomware is mainly used to target users in Western Europe and the United States.
The ransomware uses popular techniques like phishing, spam messages, emails, links, peer to peer networks, third-party installation, backdoor malware, pirated software, freeware and internet vulnerabilities to spread itself over the whole computer network.
With these ways, ransomware enters into the system and once the infiltration is done, Phobos ransomware encrypts files and damages your computer functionalities by using AES 256 encryption algorithm.
Once the file locks, the ransomware appends following string .ID[eight random characters].[ottozimmerman@protonmail.ch].PHOBOS extension and also creates an HTML application info.hta and a ransom note Your Files Are Encrypted!
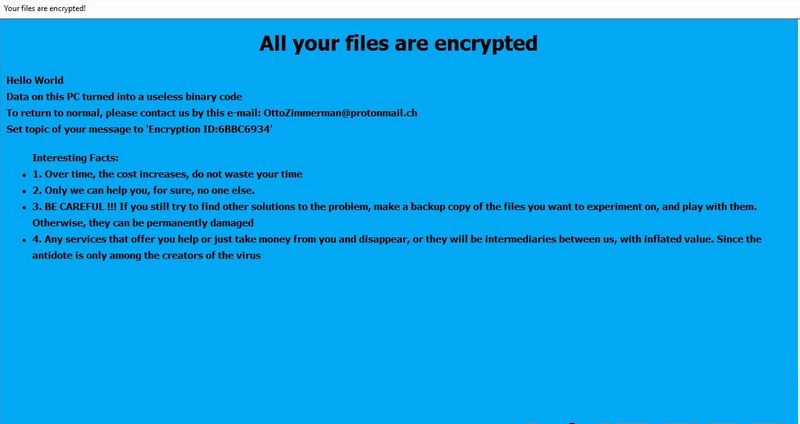
Due to HTML application, a pop-up window executes via your browser and displays a message stating that your data is encrypted and you must pay ransom to release it.
Eventually, when you try to open a locked file, ransom note text document opens asking you to contact ransomware developers to decrypt .phobos files.
The HTML application and ransom note contains the same message as follows;
Note: Seeing all this, it is simply very easy to say that Phobos ransomware encrypts all our important files, passwords, banking credentials, etc. and corrupt them in such a way that we being a user can’t access it.
What Next If You See Phobos Ransom Note
Visually ransom note looks identical in all variants of different ransomware families. Most of the users who aren’t aware of the presence of ransom note, panic after seeing the message for the first time.
Like many other ransomware, the Phobos virus accesses your windows registry keys and modifies them to make sure that ransomware works freely after infiltration.
Once the threat enters into the system, it also installs other potential threats to disrupt the functioning of the computer.
According to reports, in such a situation, if the user contacts the ransomware developers, they are forced to pay in bitcoins. However, as promised in the note the developers (cyberattackers) don’t give them decrypt .phobos files keys consequently leaving the user with the inaccessible system.
Most of the user find no other way than paying a ransom and lose their money along with the files. But, this situation is avoidable if your system holds a robust technology that has the capability to fight against Phobos ransomware.
We suggest you anti-malware or anti-viruses like Malware Crusher that can automatically prevent the entry of malicious threats and fight against the ransomware.

Phobos Ransomware Infection
The main purpose of .phobos virus is to encrypt your files and on the name of decrypt .phobos ransomware keys, cyber attackers ask you to pay bitcoins. To encrypt files, Phobos version of ransomware use AES algorithm and lock audio, video, image, database, archive files etc.
Whenever the infection initiates, the ransomware activates its payload/dropper file and perform a series of malicious activities on the victim’s computer.
-
Tamper system files and Windows registry editors
-
Delete back up files
-
Disable system recovery files
-
Run system automatically on system boot
-
Fake software update notification (which a user install thinking it as a genuine update)
-
Cause software bugs/flaws
-
Installation of rogue applications via third-party
-
Changes windows administrator permissions
-
Makes your computer to host crypto mining and cryptojacking
These infections act like indicators that would clear your confusion about the ransomware attack. If such things are happening to you, then you must take actions to prevent the infections caused by the ransomware.
For this to happen, we had prepared a Phobos ransomware removal guide. The guide is divided into three parts;
Gain Entry In Computer By Safe Mode with Command Prompt
Steps to be followed to enter the safe mode Win XP/Vista/7
- Click start, then shut down, then restart.
- While the computer is booting up at the very first screen start tapping F8 until you see the advanced boot options.
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10
- On the windows login screen, you need to press the power option.
- Now, press and hold the shift key on the keyboard, and then click Restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Restore System
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
- Now, type rstrui.exe and hit Enter again.
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
- Then, click next and followed by yes.
At present, your computer is in a state that has its file and data backed up at a safe restore point. We also suggest you to make a copy of your backed up data into some external hard drive.
It is now time, to reinstall your Windows via an external source such as pen drive, CD or DVD.
While installing Windows, allocates disk space to C,D and E drive. If asked to restore any files, select the restore point and get the backed up data into the new operating system.
Your system format is complete, also your data is backed up. Now you must create a strong firewall against such malicious threats to prevent the future attacks.
If you do not have any security software, then download Malware Crusher to prevent Phobos ransomware attacks. Also, you can use the below guides to make your system again in the working condition.

Prevent Entry Of Phobos Ransomware
Malware Crusher is the most commonly used anti-malware software for the Windows computer. It’s malware removal capabilities makes it the most impactful tool and prevents you before the ransomware starts infecting your system because:
-
It’s real-time protection feature, performs a deep scan, detects malicious software and infected encrypted files within your system.
-
The Quarantine feature of the tool removes all infected files from your computer. Additionally, keeps a record of all deleted malicious program.
- Malware Crusher also creates a shield against Ransomware, Adware, Malware, Browser Hijackers, Viruses, Extensions and Trojans from entering into your system.
-
The 24X7 online protective shield works as an anti-exploit technology and blocks the ransomware component before they hold files as a hostage.
-
Malware Crusher tirelessly visits all domains, URLs and web pages to secure your online presence from fraudulent entities.
-
Malware Crusher becomes fiercer in detecting keylogging, remote connections and saving your session data from being recorded.
To get a better security awareness on preventing cyber attacks and cyber security threats keep visiting us, forget not to download Malware Crusher.
Its 5-minute function could be a savior for your Windows computer!
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
