Remove PyLocky Ransomware From Windows
PyLocky Ransomware also called as fake invoice generation Virus is a file-encrypting program code that usually alters data into the infected system by XOR/AES/RSA encryption technique.
It is a classified new variant of the python-based locker ransomware which may be persistent in your systems. Once the ransomware enters into your system, it demands money to decrypt the locked files.
Research from cybersecurity experts concludes;
Most of the times users pay the ransom (sometimes in BTC) but don’t get decrypting keys and ransomware decryption tools to recover their locked files. Thus, it is necessary to find out a legitimate method to remove Pylocky ransomware.
This article aids you to remove locky poser cryptovirus threats. Follow this ransomware removal guide to bring back your systems to safety.
What is PyLocky Ransomware?
It is a file-encrypting virus that claims to be used for generating fake invoice messages. The main target of this threat are people who do online shopping, avail online offers and makes online transaction deals.
Samples of the ransomware come from an IP address located in East Asia. Researchers also assume its origination somewhere nearby East Asian Cultural Sphere.
PyLocky ransomware campaign targets businesses with fake invoice messages. It also mimics locky ransomware and uses unique evasion techniques.
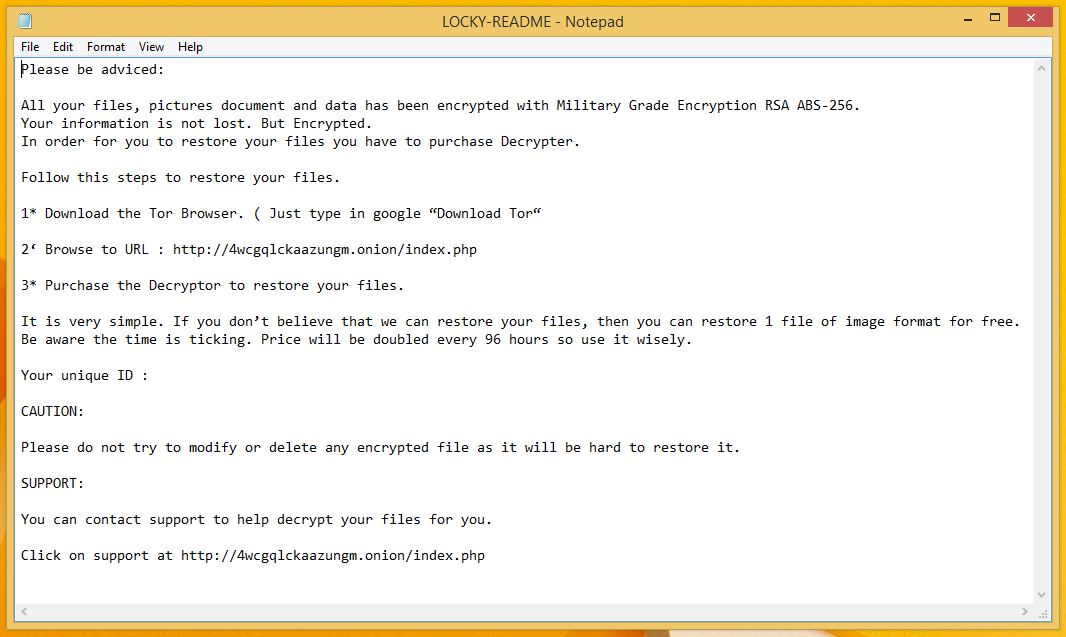
The ransom note of PyLocky, typically states that your files are encrypted and the victim must pay 10 BTC to get them restored.
Researchers also speculated that the ransomware locks your screen after which you can’t access files anymore.
How PyLocky ransomware infects system?
Cybersecurity experts confirmed that the ransomware uses XOR/AES/RSA encryption technique to modify data on infected systems. For this, the ransomware locks the file and give them .lockymap extension.
For instance, 'Nvidia GTX 1050 Ti.pptx' is renamed to 'Nvidia GTX 1050 Ti.pptx.lockymap.'
The PyLocky ransomware and other ransomware like .skype ransomware, arena ransomware, redboot ransomware, etc all use names of legitimate applications to hide their respective operations.

The .lockymap files virus could erase all the Shadow Volume Copies from the Windows operating system from the following command:
→vssadmin.exe delete shadows /all /Quiet
The widely used files by users are Audio files, Video files, Document files, Image files, Backup files, Banking credentials, etc.
Hackers and cyber attackers widely use Spam email campaigns to spread PyLocky ransomware virus on the system. The minute you open it, virus installs and infects the system.
The open safe looking emails actually lure people, but on clicking them, it downloads macro-virus in other words, a direct malware script. The developers hide malware script into well-known logos and pictures of companies.
And the requirement of a tool that can prevent the entry of file-encrypting ransomware.
Effects Of PyLocky Ransomware Ransomware
PyLocky Ransomware infected computer shows the various number of nasty irritating effects as given below:
- Polymorphic: It carries many types of cryptovirus variants, remains undetected and ordinary antivirus tool cannot locate it.
- Identity Theft: It posses keyloggers to monitor your keystrokes additionally sends information to hackers. It also steals your sensitive and financial information.
- Copycat Look: Developed in a manner that it represents an original program to cheat innocent users, but doesn’t contain any genuine features of the application.
- Memory Resident: After entering into the system it remains in the memory of the system and automatically gets executed.
- Poor Detection: All the working Security application blocks, so it becomes unable to detect any other incoming threat.
- Fake scanning property: It performs bogus system scanning on the screen and shows fake results.
- Transferable: It easily duplicate itself and transmit from one infected system to another via network vulnerabilities and security checkup loopholes.
The infections caused by .Lockymap virus is intrusive and also spy on the system. Furthermore, keeps an eye on our activities before blocking access to the system. Thus, it is important to delete PyLocky Ransomware from the system.
Cybercriminals via these threats steal information like IP address, URL’s Search, browser history, search queries, username, ID, passwords, banking information and ATM Card information.
If you are an infected user of this ransomware, then our ransomware removal guide will be helpful to you to fix your system on your own.
If you do not have any security software, then download a reliable software for PyLocky ransomware removal. But before that, you can use a few manual methods to see whether they can work against ransomware or not.
How to Remove PyLocky Ransomware?
In order to remove this ransomware from your computer, you must stop all running processes and delete all unassociated files from Windows registry entries.
If any ransomware component is left on the computer, the probability of ransomware reinstalling itself will increase as soon as you boot up your computer while starting. Usually, ransomware uses random names and finding them manually becomes very difficult.
If you can’t access your computer, then it might become impossible to remove PyLocky ransomware. However, system reboot in Safe Mode could give you entry into your computer followed by creating a system restore point.
Below you can find a few popular ransomware removal methods. The methods together make a guide which helps to prevent the attacks. The guide is divided into three parts;
- Unlock Your Locked Computer
- Automatic Preventive Method
- Manual Preventive Methods

Unlock Your Locked Computer
Ransomware infections are very dangerous and could cause a complete block of your computer. The threat locks down the system and doesn’t allow you to access it. Therefore, it is important to unblock the computer. For this follow the below-mentioned process;
- Start your computer and instantly press F8(Windows 7), F5(Windows 8, 8.1 and 10) repeatedly to enter Advanced Boot Options.
- Log on the computer as the Administrator.
- Change or remove your computer’s forgotten password in Control Panel and enable the safe mode options.
Automatic Preventive Method
Malware Crusher is the most commonly used anti-malware tool for the Windows computer that scans and removes cyber threats when started manually. Be it PyLocky ransomware attack or any other popular virus or malware, Malware Crusher always keeps your Windows PC safe and secure.
It’s malware removal capabilities makes it the most impactful and vigilant tool that prevents your system before the ransomware starts spreading infection;
- It’s Real-time protection feature, performs a deep scan to detects malicious software and persistent threats. Also, identifies suspicious behavior on your computer.
- The Quarantine feature of the tool removes all infected files from your computer. Additionally, keeps a record of all deleted malicious program and allows you to choose important programs to restore at a later time.
- Malware Crusher also creates a shield against Ransomware, Adware, Malware, Browser Hijackers, Viruses, Extensions and Trojans from entering into your system.
The 24X7 online protective shield works as an anti-exploit technology and blocks the ransomware component before they hold files as a hostage.
- Malware Crusher tirelessly visits all domains, URLs and web pages to secure your online presence from fraudulent entities. Furthermore, the tool detects the vulnerabilities of online fraudulent entities effortlessly.
- Malware Crusher becomes fiercer in detecting keylogging, remote connections and saving your session data from being recorded.
Malware Crusher continuously monitors the happenings of cyberworld related security issues. In response to the malicious codes and javascript, the tool writes anti-malware code and diagnose ransomware.
After using the tool, you can follow manual methods on a regular basis to keep a watch on pre-installed applications and programs.
Manual Preventive Methods
- Press Ctrl + Shift + ESC together to open Task Manager. Look for suspicious files, right click on it and click End Task.
- Now, open RUN box window by pressing Windows key + R . Type appwiz.cpl on it, this opens Programs and Features window.
- Select each suspicious program and uninstall it one by one. Once the uninstallation is complete, restart your computer and again redirect yourself to Programs and Features window to check whether the application is present or not.
- When convinced, press Windows key + R to open RUN box window. Type regedit on it, hit OK and then click Yes.
- Go through HKEY, HKLM, etc. files and find all suspicious files and delete them.
- You can also delete malicious extensions from your browsers like Chrome and Firefox.
1. Click on the Customize and control menu icon at the top right corner of Google Chrome.
2. Select "More tools" from the menu.
3. Select "Extensions" from the side menu.
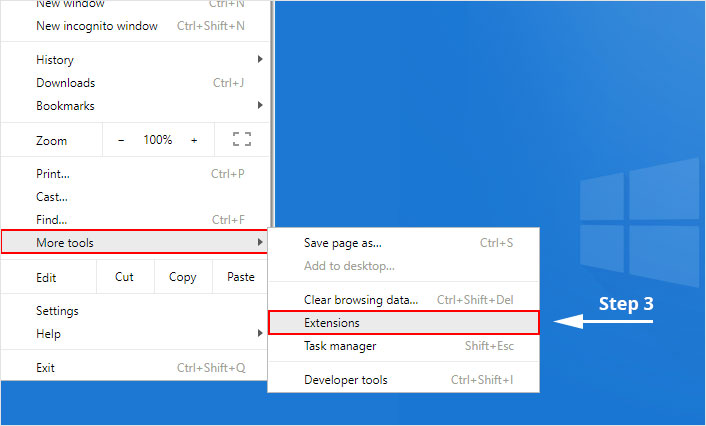
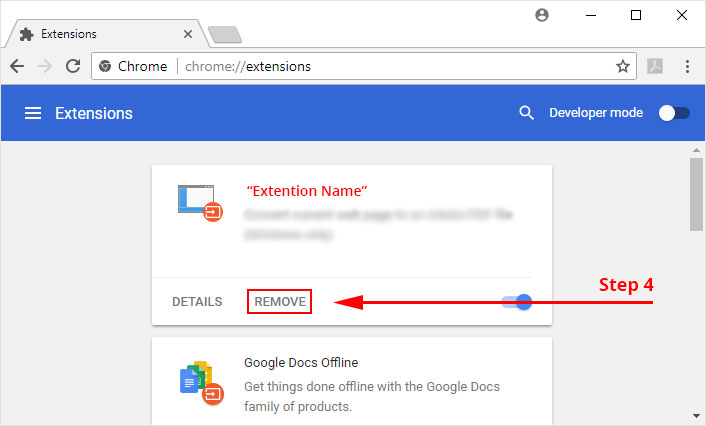
4. Click the remove button next to the extension you wish to remove.
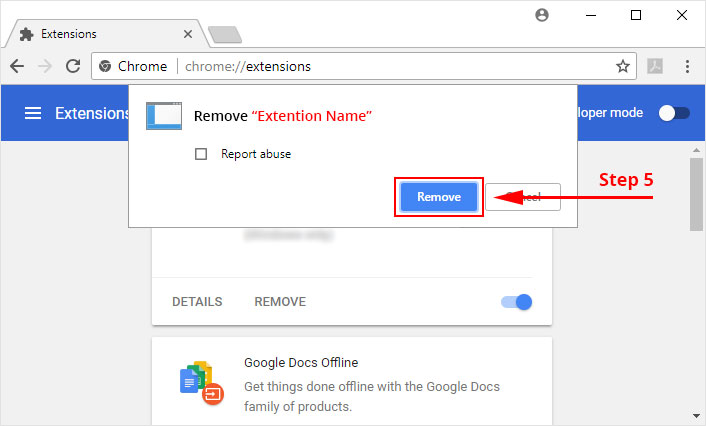
5. It will confirm again, click “remove” and the extension is finally out of the system.
Now that we have successfully eliminated the malicious browser extension, we need to create a robust firewall to avoid any such thing that makes our system and privacy vulnerable to various online threats.
1. Click on the “menu” button at the top right corner.
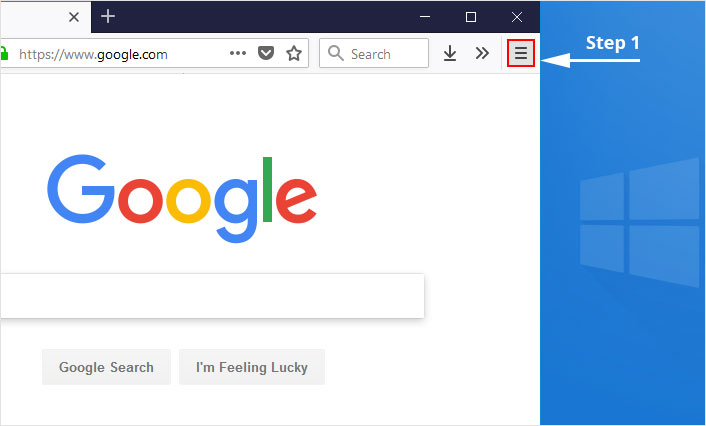
2. Select “Add-ons” from the menu.
3. Click the “Remove” button next to the extension you wish to get rid of.
Now that we have successfully eliminated the malicious browser extension, we need to create a robust firewall to avoid any such thing that makes our system and privacy vulnerable to various online threats.
The manual method sometimes might not work at Windows OS because finding suspicious and modified registry files in registry editors is a difficult task. On the other hand, if a useful file deletes, then the windows stop working properly.
That’s why it is highly recommended to use an automatic tool to prevent and remove PyLocky ransomware attacks and infections on your computer. If you wish to get more news and awareness on the happenings of the cybersecurity, then keep visiting us.
To get a better security awareness on preventing cyber-attacks and internet security threats, keep visiting us and forget not to download Malware Crusher. Its 5-minute function could become a savior for your Windows computer.
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
