Rektware Ransomware Adds Alphanumeric Extension To Lock Files
Ransomware is becoming more popular in the world of cyber threats and security. Even researchers all around the world say that once ransomware enters into your operating system, it becomes difficult to delete and remove it.
Is it really true?
The firm research of our team shows that with the best tool against such threats, it is not difficult to get rid of ransomware.
Just a month ago this year, the discovery of new ransomware - Rektware Ransomware shocked many cybersecurity experts. The newly found rektware virus works almost like every other ransomware, but one feature is far away different!
What Makes Rektware Ransomware Virus Different From Others?
It is a ransomware type virus that enters secretly into computers and encrypts files. Unlike all other ransomware like Arena, Ligma, Rightsor, MVP, CoinHive, KCTF Locker, etc. rektware also force its victims to pay the ransom but adds an alphanumeric file extension.
The addition of a random alphanumeric extension is different when compared to the extensions of other ransomware. Rektware ransomware adds extensions like Uj3p1H, 6sfszf to the locked files.
The cyber threat enters into the computer and locks files such as photos, videos, pdf, docx, databases, etc. Now, gives a random appendix to file and blocks users’ access.
For example, kingsley.jpeg is renamed to kingsley.jpeg.Uj3p1H.
The added file extension (alphanumeric code) makes rektware different from others because neither the cyber world’s experts nor we ever saw such an extension. The extension changes with the computer, i.e. each victim will have a different extension.
It is unclear whether different files at victim’s computer shares the same extension or each locked file have a different extension.
However, many consider the uniquely generating extension as victim’s id that allows contacting attackers. The ransomware encrypts files with encrypted unique id extensions and demands money in a ransom note to all infected files.
There exists a long list of targeted filename extensions such as .jpg, .gif, .iso, .txt, .zip, .msi, .pdf, .res, .php, .lic, .cfa, and .bep.
Rektware Ransomware - Distribution Technique
The ransomware is a newly discovered cryptovirus that is currently in-development. There are a relatively less number of identified samples. It clears that a large scale attack campaign is on its way. This may allow attackers to opt for many popular methods to distribute ransomware.
Some are mentioned below;
- SPAM phishing campaigns force the users to think that they have received a legitimate notification from a well-known site. Unfortunately, it is a scam message and contains virus infected links and files.
- Hackers construct fake download portals and via file-sharing networks, they spread infected payload carriers to promote illegal content and malware files.
- Cyber attackers construct infected software installers of popular applications and promote their setup files to inject rektware ransomware.
- Large distribution campaigns of malware extensions also sometimes spread ransomware. Furthermore, in many cases, fake developer credentials and user reviews force the users into downloading them.
It quickly spreads through spam emails, websites, peer to peer file sharing, freeware (fake software updates), cracked or pirated software and social hijacking. It degrades the computer performance and compels you to pay money for your own files.
Unfortunately, the ransomware is not curable, but you can prevent it from entering into your system. For this, a robust anti-malware removal tool Malware Crusher could help you to uninstall rektware ransomware related files.

The use of AES/RSA encryption technique let cybercriminals to steal information like IP address, URL’s Search, browser history, search queries, username, ID, passwords, banking information and ATM Card information.
The ransomware harvest data module for hijacking data that can be used further to expose the victim’s identity. It also uses stealth protection mode to avoid detection form security software and firewalls.
The data collection module leads ultimately to the creation of UUID in the alphanumeric pattern. Eventually, files are targeted, encrypted and then the user access is blocked. On accessing the file, ransom note appears demanding payments to unlock files.
Whatever it is, we never recommend you to pay! Paying ransom is not a good option because once you start paying a ransom, the cyber attackers will demand more. You can see our recommendations, tips and tricks to remove rektware ransomware and decrypt your locked files.
How to Remove Rektware Ransomware?
If you can’t access your computer, then it might become impossible to remove rektware ransomware. However, system reboot in Safe Mode could give you entry into your computer followed by creating a system restore point.
Once you are into your computer, perform a full system scan using Malware Crusher after downloading it. This ransomware affects Windows including Windows XP, Windows Vista, Windows 7, and Windows 8.
Follow the below ransomware removal guide to get entry into your system.
Windows Safe Mode Options
Steps to be followed to enter the safe mode Win XP/Vista/7.
- Click start, then shut down, then restart.
- The computer boots up at the very first screen, start pressing the F8 key until you see the advanced boot options.
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10.
- On the windows login screen, you need to press the power option.
- Press and hold the shift key on the keyboard, and then click Restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
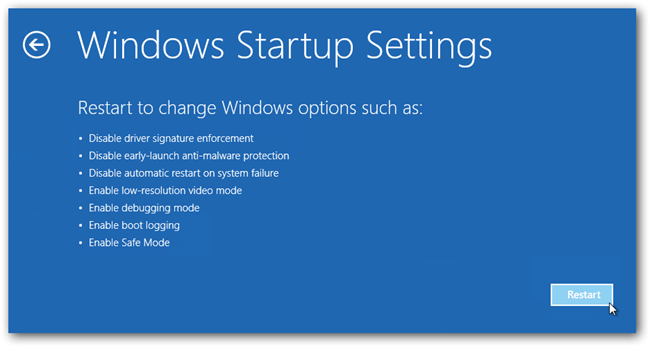
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Windows System Restore
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
- Now, type rstrui.exe and hit Enter again.
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
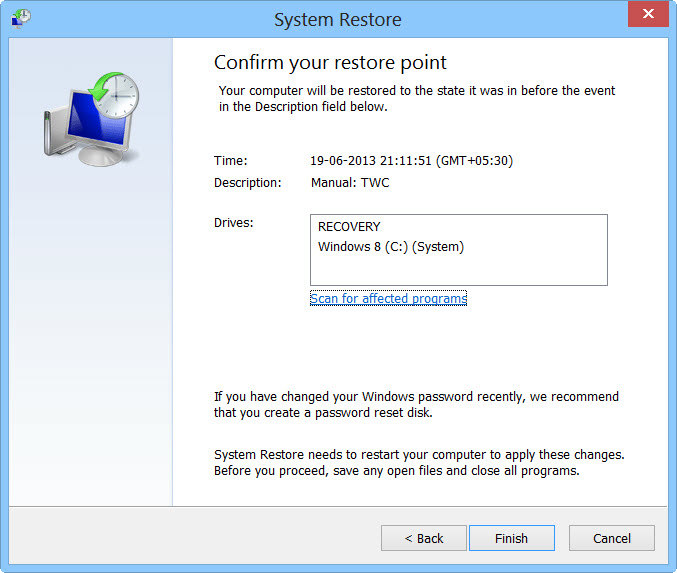
- Then, click Finish and followed by yes.
If you are a non-technical person and couldn’t follow the above process, then use automatic rektware virus removal tool.

Prevent Rektware Ransomware Virus Automatically
Malware Crusher is the most commonly used anti-malware tool for the Windows computer. It’s malware removal capabilities makes it the most impactful tool and prevents your system before the ransomware starts infecting it because:
- It’s real-time protection feature, performs a deep scan, detects malicious software and infected encrypted files within your system.
- The Quarantine feature of the tool removes all infected files from your computer. Additionally, keeps a record of all deleted malicious program.
- Malware Crusher also creates a shield against Ransomware, Adware, Malware, Browser Hijackers, Viruses, Extensions and Trojans from entering into your system.
- The 24X7 online protective shield works as an anti-exploit technology and blocks the ransomware component before they hold files as a hostage.
- Malware Crusher tirelessly visits all domains, URLs and web pages to secure your online presence from fraudulent entities.
- Malware Crusher becomes fiercer in detecting keylogging, remote connections and saving your session data from being recorded.
To get a better security awareness on preventing cyber-attacks and cybersecurity threats, keep visiting us and forget not to download Malware Crusher. Its 5-minute function could be a savior for your Windows computer!
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
