Reveton Ransomware - New Variants and Infection Method
In 2012, a major ransomware named Reveton began spreading in European countries and fooled many law enforcement organization into illegal activities.
For example, Police Agencies claimed that the ransomware was used in downloading an unlicensed software, child pornography videos and money laundering charges.
But, there are no solid pieces of evidence about its existence! Unfortunately, in the last six years, big nations like UK, America, Canada and Russia too got attacked by different variants of reveton ransomware.
Since the primary targets of this ransomware were law enforcement bodies and the legal houses of nations, the ransomware specifically got named as Police Ransomware.
Why Is Troj/Reveton Ransomware Called Police Ransomware?
Based on Zeus ransomware, it belongs to the family of badware that locks you out of your computer unless you pay the ransom. Once you lose access to the computer, the troj/Reveton ransomware displays a window which pretends to be from law enforcement agency of your respective country.
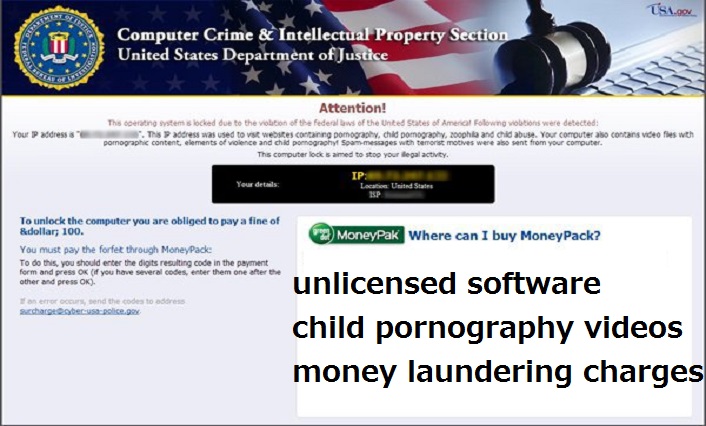
For example, in the USA the message comes from FBI and in the UK, it comes from MPS.
The message says that you broke different laws regarding pornographic material and copyright issues. In response to it, your system is locked and the government has decided to prosecute you.
In order to access your computer, you must pay a fine or else you will be jailed!
It is important to understand that these messages are fake and you are not locked out by any government organization. In other words, cyber attackers are using the country’s government name illegally to make money from the ransomware.
Also called as Trojan: W32/Reveton, upon execution, creates following files on your Windows computer:
- On Windows XP: %USERPROFILE%\StartMenu\Programs\Startup\[reveton_filename].dll.lnk
- On Windows 7: %USERPROFILE%\AppData\Roaming\Microsoft\Windows\StartMenu\Programs\Startup\[reveton_filename]dll.lnk
Finding out these files might be difficult for users because ransomware always works secretly and never allows the user to know about them. Thus, to remove Trojan: W32/Reveton ransomware virus, use Malware Crusher from below one download click button.

Reveton Ransomware Virus Coming Back Again!
Team HTRI observed a noticeable increase in reveton malware variants particularly TROJ_REVETON.SM4 and TROJ_REVETON.SM6, both equipped with the capability to lock down the users’ screen.
It is bit surprising to see reveton ransomware is coming back at those times when the crypto variants of ransomware are becoming dominant and active. Similar to the older police ransomware of 2012, new reveton ransomware use following tactics to spread itself;
- It uses Tor protocol to hide their identity and location. Also called as Onion Service Protocol, cyberattackers use web publishing and instant messaging without knowing the network identity.
- Another technique is fast flux, where bots use Domain Name System method to hide malware and phishing attempts secretly.
- Domain shadowing allows the cyber fraudster to cover a malicious website on a genuine website. And redirect users to the site which releases malware and ransomware onto the computers.
- Fake sites impersonating as the genuine ones.
- Attackers use new IP addresses, move to new locations and hide their identities.
- Domain Generation Algorithm sends new domain addresses to the attackers after pinging Domain Name Servers.
A user with the infected system won’t be able to suspect the attack of the ransomware due to the lack of knowledge about the variants and their techniques.
However, it would be great to let technology (ransomware removal tools) fight with the technology (ransomware)! But, for that, you must detect few the presence of the reveton virus on your network and computer.
Detect Reveton Ransomware Presence On Your Network
According to the new Internet Security reports, ransomware remains a major growing threat since 2016. New variants have already changed the file encryption techniques in addition to the distribution techniques of ransomware.
For this, you need to watch out for multiple symptoms, here you can take a look at a few of them;
- Watch out for unknown file extensions.
- Watch out for renamed multiple file names.
- Watch out for a freeware program that gives fake software updates and pirated software.
- Degrades your computer’s performance.
- Automatic spam phishing campaigns and emails.
- Construct fake download portals.
- Large distribution campaigns of malware extensions.
Once victimized, the ransomware attacks your system, web browsers settings and corrupts hard drive of the computer. Applications do not respond sometimes and adequately claims to lack few important program files.
Cybercriminals via these threats steal information like IP address, URL’s Search, browser history, search queries, username, ID, passwords, banking information and ATM Card information.
Therefore, we suggest victims to follow the below-mentioned automatic ransomware removal tool guide for deleting Police Ransomware easily and completely.
Prevent Reveton Ransomware Automatically
The robust technology of any anti-malware tool for the Windows computer acts as a security defender that protects and prevent your system before the ransomware starts infecting it.
And Malware Crusher is a complete PC protection kit whose different malware removal capabilities makes it a solution for everyone's cybersecurity need.
Following is the glimpse of the removal capabilities to stop entry of any malicious entry into your Windows system;
- It’s real-time protection feature, performs a deep scan to detects malicious software and persistent threats. Also, identifies suspicious behavior on your computer.
- The Quarantine feature of the tool removes all infected files from your computer. Additionally, keeps a record of all deleted malicious program and allows you to choose important programs to restore at a later time.
- Malware Crusher also creates a shield against Ransomware, Adware, Malware, Browser Hijackers, Viruses, Extensions and Trojans from entering into your system.
- The 24X7 online protective shield works as an anti-exploit technology and blocks the ransomware component before they hold files as a hostage.
- Malware Crusher tirelessly visits all domains, URLs and web pages to secure your online presence from fraudulent entities. Furthermore, the tool detects the vulnerabilities of online fraudulent entities effortlessly.
- Malware Crusher becomes fiercer in detecting keylogging, remote connections and saving your session data from being recorded.
It is an ever-vigilant tool dedicated to monitoring the cyber world constantly, deeply diagnose and neutralize the threats by writing antimalware code. Round the clock monitoring of your system with this tool gives you a safer and protected version of your system, you wouldn't need multiple antiviruses!
Malware Crusher's 5-minute function could be a savior for your Windows computer!
You must be wondering whether there is no other source or manual removal method to fight against the ransomware. Then let's tell you that ransomware is so infectious that manual method can't yield you correct results.
However, you can follow the below manual removal guide for general purpose use like uninstalling programs, ending task manager process, etc before you use the antimalware removal tool.

Remove Files of Reveton Ransomware Manually
- Press Ctrl + Shift + Esc simultaneously. This will get you the Windows Task Manager. Here, make sure that you are looking into the application tab and now search for Police ransomware related files. If present, then select it and click on End Task.
- Now you can close the task manager.
- Now, we need to open control panel from the start menu or by holding Windows key + R key at the same time. This would bring up the “RUN” box now in this box you need to type control and hit ok.
- Here, in the control panel click on Add/Remove program.
- This will show the list of all the installed program.
- Look for a program you find suspicious and click on it to uninstall reveton.
The manual method might not work in some instances at Windows OS as the ransomware might have advanced into its second phase or else could have modified specific system files to stay hidden from the user.
In such conditions, we would highly recommend an automatic tool to prevent ransomware attacks on your computer.
To get more security awareness about cyber world and cyber attacks, keep visiting us to get knowledge and guide on malware removal tips.
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
