A new version of ransomware is discovered with an unusual characteristic, and it is being called C# Ransomware.
Rather than using the originally distributed executable to perform ransomware functionality, the executables compile an encrypted C# program into the system files at runtime and launches it directly into memory.
As discovered by Team HTRI Malware experts, an encrypted string is embedded into the dropper of this infection.
The code is then decrypted using the provided decryption key.
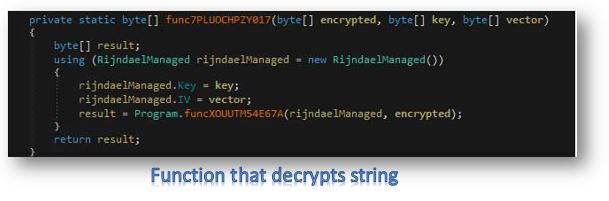
Immediately after the decryption of its executable, the decrypted source code is then sent to another function.
This newly created code is then sent to a function that compiles it using the CSharpCodeProvider class and launches it directly into memory.
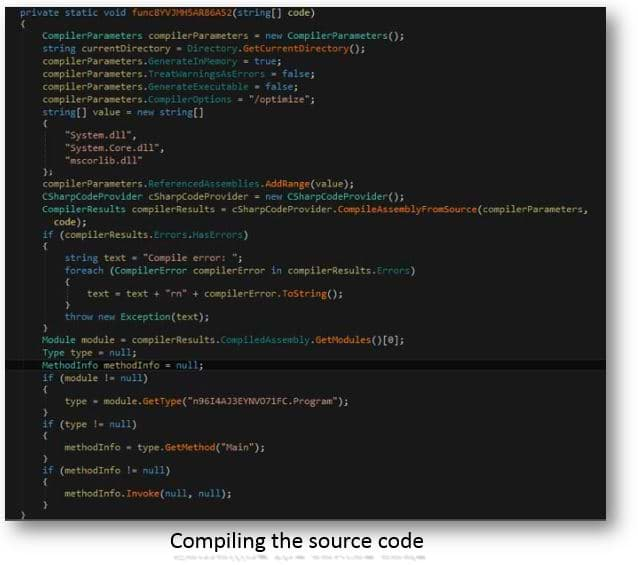
This strategy is probably followed to prevent the security software from detecting the dropper as any malicious activity is hidden behind the encrypted string.
For the ransomware itself rather than saving the decryption key to a file on the desktop, it is entirely functional. Hence, it would not be unusual to see the ransomware being distributed at some point.
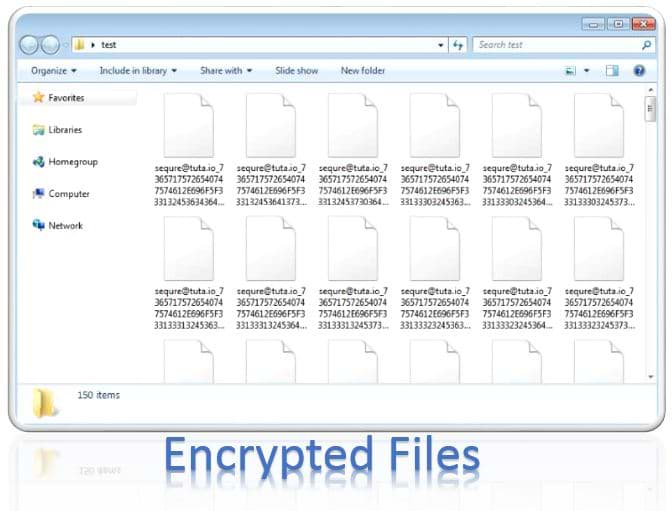
When executed, it will encrypt the files on the victim's computer and rename the files using the template sequre@tuta.io_[hex]. For example, a file called test1.jpg would be encrypted and renamed to sequre@tuta.io_31312E6A7067.
In each folder that is scanned, a ransom note named HOW DECRYPT FILES.hta is created, which provides payment instructions as shown below.
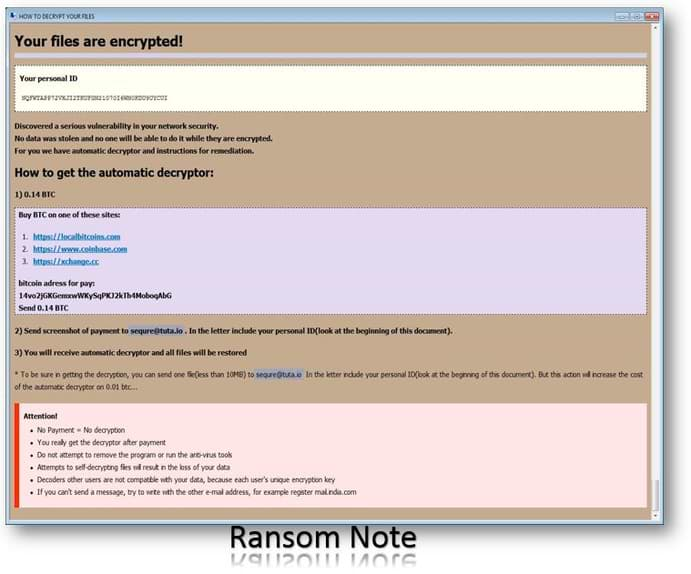
While this ransomware is still in development, it does use an interesting feature that we have not seen in ransomware before. This goes to show how attackers continue to try and think up new ways to bypass security programs that protect your computer.
Delete C# ransomware in Safe Mode with Command Prompt
Step – 1 (enter safe mode)
Steps to be followed to enter the safe mode Win XP/Vista/7
- Click start, then shutdown, then restart.
- While the computer is booting up at the very first screen, start tapping F8 until you see the advanced boot options.
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10.
- On the windows login screen, you need to press the power option.
- Now, press and hold the shift key on the keyboard, and then click Restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Step – 2 (Restore system)
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
- Now, type rstrui.exe and hit Enter again.
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
- Then, click next and followed by yes.
Restoring the system will get your windows up and running but to stay safe and prevent future intrusions we need to create a strong firewall.
For now, restoring will allow you to use your system. But, to restore it permanently, you need to create a robust firewall.
This process will prevail the Ransomware from further intrusions in your computer.
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
