What is GoldenEye ransomware?
GoldenEye ransomware is a new infection being widespread. And it comes from none other than the developers of Petya and Mischa ransomware itself. In spite of being named after the James Bond film franchise, the ransomware has no connections with it.
This is nothing but an updated version of Petya and Mischa ransomware, and it uses the same technique to encrypt and corrupt the user's data stored on the hard drive. Once the infection is on a system, it will randomly pick a ".exe" file type and save its executables into that file or uses the name of that file and stores it into %APPDATA% folder.
Every time an infected computer is turned on this file executes itself and the ransomware now goes live blocking all the system files. The initial step is to encrypt the system files with AES encryption type in CBC mode. The encryption has 32 bytes long decryption key which is nearly impossible to crack by any means and till date, there are no programs created that can reverse this encryption
While under attack the GoldenEye ransomware adds a specific file extension type to the victim's files and folders just so that they know which files are being compromised. Once all the user's files are encrypted the next step would be to initiate a lower level attack which would leave the traces of Petya ransomware on the system by bypassing the User Account Control(UAC).
To execute the Ransomware the UAC has to be set maximum. In any case if the UAC is set to minimum or default the malware bypasses and sets it maximum. Setting the UAC to maximum would bring up a pop-up which would keep showing up till the user clicks on both the options “YES” and “NO”. The option “YES” will install Petya and the “NO” is for Mischa. Either ways your computer is now screwed.
Also read: How To Remove Startpage.com Browser Redirect
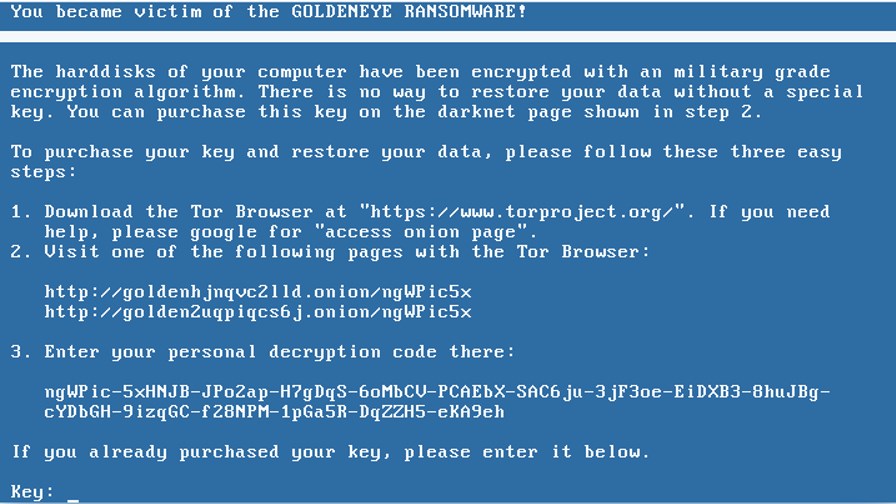
The GoldenEye ransomware leaves a ransom not behind by the name “YOUR_FILES_ARE_ENCRYPTED.TXT” with all the details in it including the steps to be followed to make the payment.
The Ransom Note:
How did GoldenEye ransomware infect your computer?
To distribute GoldenEye ransomware hackers usually utilize spam emails (irresistible attachments), third-party programs, third-party websites, freeware programs, freeware games, and trojans. Once opened, these malicious attachments (for instance, MS Office reports, JavaScript records, etc.) download and install malware. The latest version of GoldenEye ransomware was detected to be a German version. Unofficial software downloads, (for example, freeware download sites, free document facilitating sites, torrents, eMule, and so forth.) regularly introduce malicious executables as genuine programming. In doing such, these sources fool users into downloading and running malware. These malware's essentially open "entryways" for other malware to invade the system. These are the most widely recognized approaches to distribute ransomware.
If you are a victim of goldeneye ransomware, we highly recommend that you follow the steps below and get rid of the infection using safe mode and then create a strong firewall against any such attempts.
Remove GoldenEye ransomware in Safe Mode with Command Prompt
Step – 1(enter safe mode)
- Steps to be followed to enter the safe mode Win XP/Vista/7
- Click start, then shutdown, then restart.
- While the computer is booting up at the very first screen start taping F8 until you see the advanced boot options.
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10.
- On the windows login screen you need to press the power option.
- Now, press and hold the shift key on the keyboard, and then click restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Step – 2 (Restore system)
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
- Now, type rstrui.exe and hit Enter again.
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
- Then, click next and followed by yes.
After temporarily disabling the ransomware, we need to create a strong firewall to fight against such intrusions in future.
Also read: How To Remove Bud Ransomware Virus From PC
Steps to be followed:
- Enable ad-blocker: Pop-ups and advertisements are the quickest and most reliable resources for the hackers to hijack the computer. So, enabling the ad-blocker would be a step towards blocking all the malicious websites or advertisements from popping up on the screen.
- Recommended Updates: Do not postpone any updates. If there is any recommendation from the computer to update the operating system, drivers or any security software you have do not delay it. Moreover, according to survey older version tend to be an easier target.
- Third-party installation: Avoid installing programs from untrusted websites because malware is bounded with such programs. If you still wish to install such program look for a trusted third-party website, read user review about the website before trying it.
- Frequent Back up: Make a habit of backing up all your personal data frequently as it assures the security of it, an attacker can crash your computer, wipe out all your personal data or might corrupt it so that the backup would be helpful in such emergency.
- Log out of all the websites once you are done using it, i.e., Banking websites, social websites. You could be leaving all your personal data vulnerable if you are using a public network.
- Make sure you are using a secure connection before viewing any website have a look for the padlock icon before the website URL.
- Use an authentic firewall, anti-malware, and Antivirus: It’s better to stay ahead, why wait for the malware to hit your computer. We recommend that you install an Antivirus like McAfee or a good Malware Removal Tool like Free Malware RemovalTool. Apart from this, we would suggest a regular updating of these software’s to detect and avoid latest infections.
