Jigsaw Ransomware Overview
Jigsaw is a part of the ransomware family. This is a new variant of Jigsaw ransomware, recently found by the security researcher. It encrypts the victim machine by using AES encryption method.
This ransomware targets only 15 File extensions.
It appends the filename of the affected file by adding .fun in the last. As per the ransom note, this ransomware will delete some files in every hour if the user didn’t pay the ransom amount on time.
This ransomware demands 100$ in bitcoins at following bitcoin address: 1Hd3tU8MDmuVotMgGJTJ7svzvPey6bfUgm
Flowchart

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
Technical Analysis of Jigsaw Ransomware
File Name: Jigsaw.exe
MD5: 07046473F9BC851178EBC155D0BB916B
File Type: .EXE
Detail Description of Jigsaw Ransomware with Screenshots
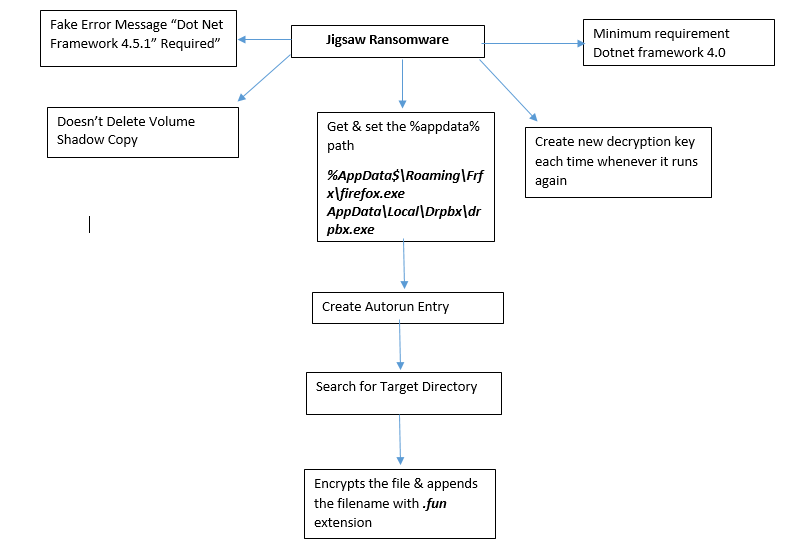
As shown below, this ransomware has a minimum requirement of dot net framework 4.0
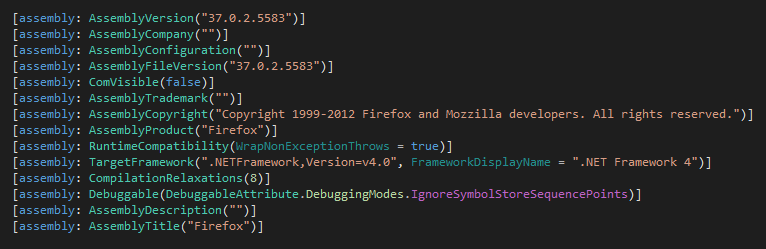
Figure 1 Assembly Information
On execution of this ransomware it first gets & set the %appdata% path & copy itself into at following location:
%AppData$\Roaming\Frfx\firefox.exe
AppData\Local\Drpbx\drpbx.exe
Thereafter, it creates the Autorun entry in the registry so, that at each boot time it gets self-started.
HKCU\Software\Microsoft\Windows\CurrentVersion\Run firefox.exe=C:\Users\admin.admin-PC\AppData\Roaming\Frfx\firefox.exe
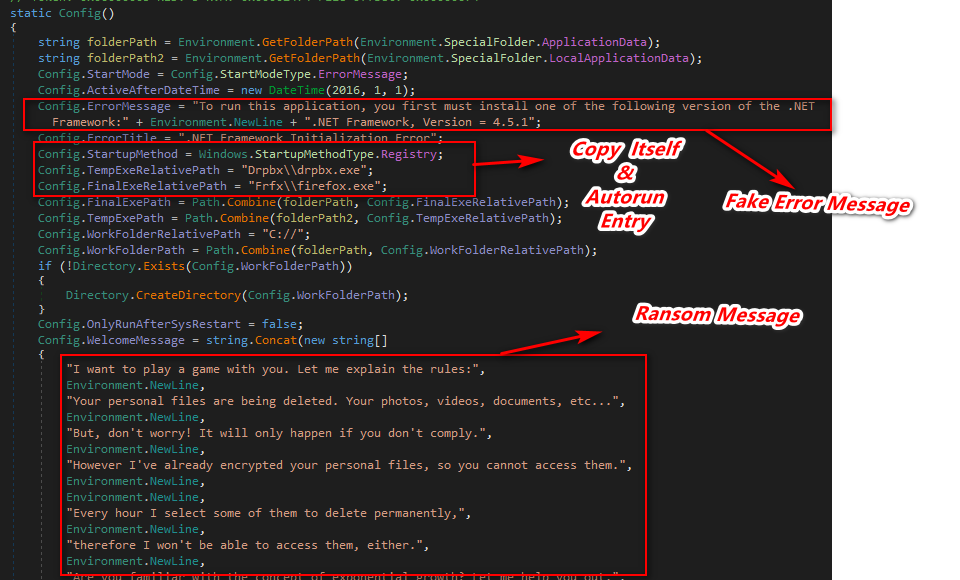
Figure 2 Configuration Information
As per the above configuration code, this ransomware generates the fake error message of Dot Net Framework 4.5.1 Requirement.
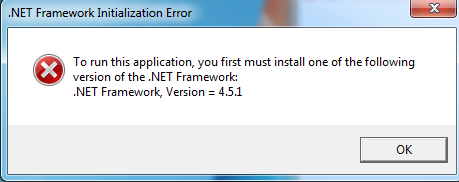
Figure 3 Fake Dot Net Requirement
This ransomware targets only 15 file extensions:
.jpg .jpeg .gif .png .bmp .txt .doc .docx .pdf .xls .xlsx .csv .rar .zip .7zip
This ransomware appends the affected filename by adding .fun in the last & shows the ransom screen that contains the Welcome Message with Countdown Time & Input Fields.
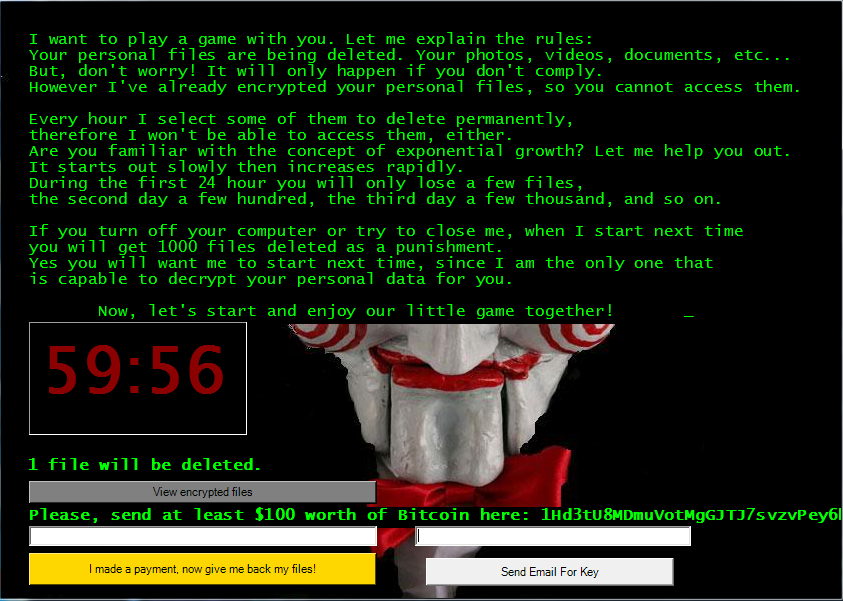
Figure 4 Ransom Message Screen
The victim can also see the list of encrypted files by pressing the button (“View Encrypted Files”)
Figure 5 Encrypted Files List
The victim can easily restore the files by going back to the old restore point because this ransomware doesn’t delete any Volume Shadow Copies.
Every time this ransomware creates the different decryption key & then it try to connect their C&C (Command & Control) server to check whether the payment has been done or not.
As per the ransom note victim has demanded 100$ in the form of bitcoins at following bitcoin address:
1Hd3tU8MDmuVotMgGJTJ7svzvPey6bfUgm
IOC’s
Associated File Names & Hashes:
|
File Name
|
Hash
|
|
Sample.exe
|
07046473F9BC851178EBC155D0BB916B
|
Associated URL’s:
http://demourl.co.nf/pwd/write.php?info=PC-admin%20cEpFtlMNwZUsZLNuGPQTiT==
Associated File Paths:
%AppData$\Roaming\Frfx\firefox.exe
AppData\Local\Drpbx\drpbx.exe
Associated Registry:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run firefox.exe=C:\Users\admin.admin-PC\AppData\Roaming\Frfx\firefox.exe
Associated Bitcoin Address:
1Hd3tU8MDmuVotMgGJTJ7svzvPey6bfUgm
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
