RotorCrypt Ransomware Overview
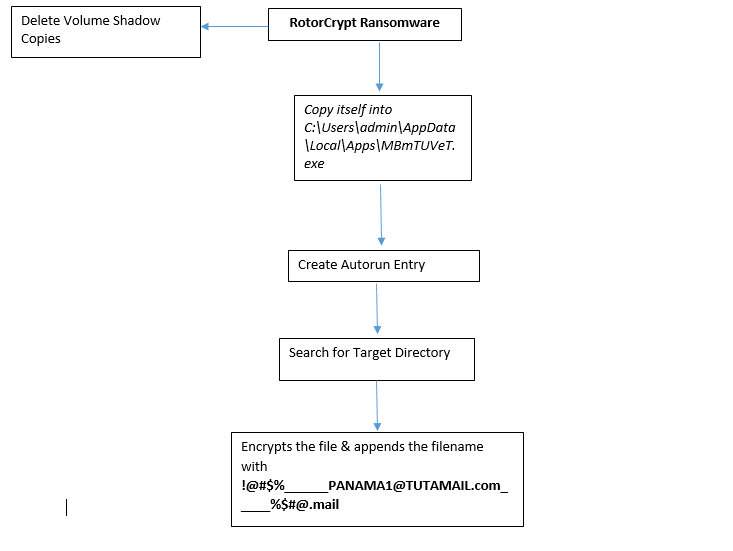
RotorCrypt is a part of the ransomware family. This is a new variant of RotorCrypt ransomware, recently found by the security researcher (Michael Gillespie). This ransomware deletes the backup option from the system so that the user can’t go back to the restore point option.
In previous variant of rotorcrypt ransomware was using ________INKOGNITO8000@TUTAMAIL.COM_________.SPG file extension in the last but this time it appends the filename of the affected file by adding !@#$%______PANAMA1@TUTAMAIL.com_____%$#@.mail in the last.
This ransomware doesn’t contain any ransom information nor it drops any ransom note.
Flowchart

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
Technical Analysis of RotorCrypt Ransomware
File Name: RotorCrypt.exe
MD5: E120C26A601EE0ECEB84068728910E89
SHA1: 2e074045c334a5e59a536b1397d6a4d63437c10b
SHA256: 3637c9f27d8599d1c79a1de6f4eb2bf2795f831d43d9d4b0c821e73bdbebafcf
File Type: .EXE
Spread Via: Email
Detail Description of RotorCrypt Ransomware with Screenshots
On execution of this ransomware its executed following subprocesses
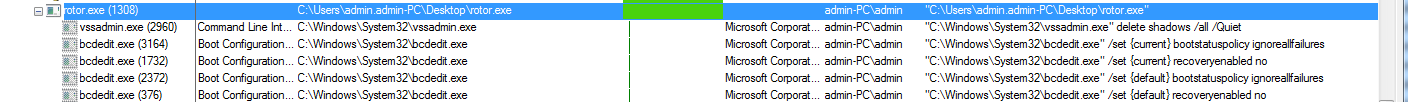
Figure 1 Process Tree
As shown above this ransomware deletes the volume shadow copy and disable recovery mode by initiating following commands
C:\Windows\System32\vssadmin.exe" delete shadows /all /Quiet
C:\Windows\System32\bcdedit.exe" /set {current} bootstatuspolicy ignoreallfailures
"C:\Windows\System32\bcdedit.exe" /set {current} recoveryenabled no
"C:\Windows\System32\bcdedit.exe" /set {default} bootstatuspolicy ignoreallfailures
Thereupon this ransomware copy itself into at following location:
C:\Users\admin\AppData\Local\Apps\MBmTUVeT.exe
Thereafter, it creates the Autorun entry in the registry so, that at each boot time it gets self-started.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run DcNGTEFm= C:\Users\admin\AppData\Local\Apps\MBmTUVeT.exe

Figure 2 Persistent Mechanism
This ransomware takes advantage of following Microsoft Cryptographic API’s to encrypt the files:
CryptGetUserKey
CryptGenRandom
CryptGenKey
CryptDestroyKey
It also searches for some processes with the help of CreateToolhelp32Snapshot, Process32First & Process32Next.
It contains some interesting API’s (Anti-Debugging API’s) that checks whether the malware is running under any debugger or not, below are some of them:
Isdebuggerpresent
GetSystemTime
GetTickCount
As shown below, this ransomware appends the affected filename by adding !@#$%______PANAMA1@TUTAMAIL.com_____%$#@.mail in the last.

Figure 3 Extension
It doesn’t drop any ransom note nor it contains any ransom amount information.
This ransomware also doesn’t contain any network activities.
IOC’s
Associated File Names & Hashes:
|
File Name
|
Hash
|
|
Sample.exe
|
E120C26A601EE0ECEB84068728910E89
|
Associated File Paths:
C:\Users\admin\AppData\Local\Apps\MBmTUVeT.exe
Associated Registry:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run DcNGTEFm= C:\Users\admin\AppData\Local\Apps\MBmTUVeT.exe
Are you worried about your PC health?
Check your PC Health for Free!
[tips_prevents]
