KingOuroboros Ransomware Overview
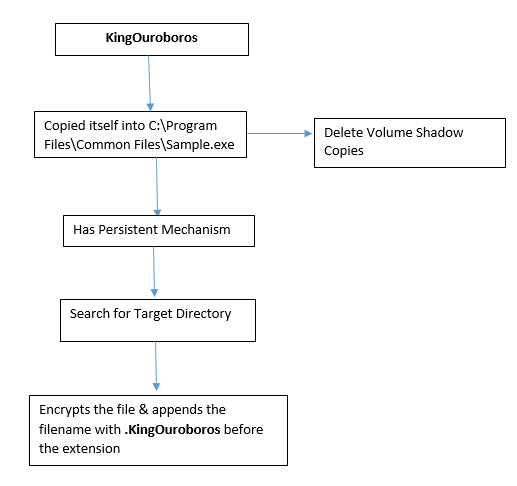
KingOuroboros is a part of the ransomware family. Recently a new variant of KingOuroboros ransomware, found by the security researcher. This ransomware deletes the backup option from the system so that user can’t go back to the restore point option.
It appends the filename of affected file by adding .king_ouroboros before the file extension. For ex: Microsoft OneDrive.king_ouroboros.lnk
This ransomware drops the ransom note on Desktop, Ransom note include the details of attacker’s e-mail id (king.ouroboros@protonmail.com) and Victim Personal ID with ransom amount information.
Flowchart
See Also: Detailed Technical Analysis Report of Paradise Ransomware Attack
Technical Analysis of KingOuroboros Ransomware
File Name: Sample.exe
MD5: 8893004B04B4436EB47E9B504B7A437F
SHA1: 29B18DE4657E00CABC41B3600E753EF51960CD21
SHA256: D4DE58E79BFCF66EA933E50FBEADA266FE32EE2CE0636419ED9EC0F60A99EA2C
File Type: .EXE
Spread Via: Email via Zip Attachment
Detail Description of KingOuroboros Ransomware with Screenshots
On execution of this ransomware its executed following sub processes
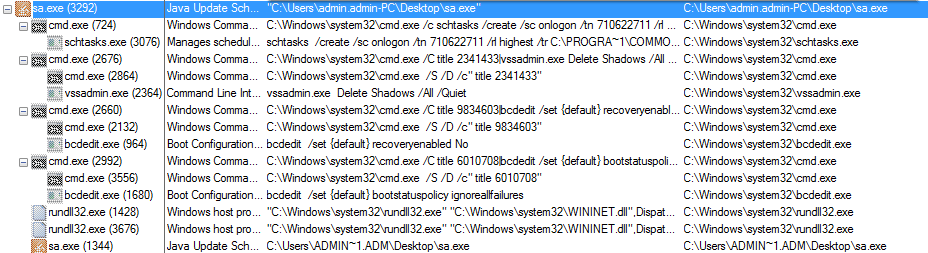
Figure 1 Process Tree
As shown above this ransomware Copy itself into different folder and create new Schedule Job by executing following commands:
Thereafter, it deletes the volume shadow copy and disable recovery mode by initiating following commands
C:\Windows\system32\cmd.exe /C title 2341433|vssadmin.exe Delete Shadows /All /Quiet
C:\Windows\system32\cmd.exe /C title 9834603|bcdedit /set {default} recoveryenabled No
C:\Windows\system32\cmd.exe /C title 6010708|bcdedit /set {default} bootstatuspolicy ignoreallfailures
Thereupon, this ransomware installs the WININET.dll by passing Service name and ordinal number as shown in the following command
"C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1
This ransomware also creates the following files at C:\Program Files\ Common files\
Sample.exe
Log.txt – (Contains Path Information which has been encrypted by this ransomware)
117226017 – (Contains Ransom Amount Info)
710622711710622711
This ransomware takes advantage of following Microsoft Cryptographic API’s to encrypt the files:
CryptGetUserKey
CryptGenRandom
CryptGenKey
CryptDestroyKey
This ransomware search for some processes with the help of CreateToolhelp32Snapshot, Process32First & Process32Next.
It contains some interesting API’s (Anti-Debugging API’s) that checks whether the malware is running under any debugger or not, below are some of them:
Isdebuggerpresent
GetSystemTime
GetTickCount
As shown below, this ransomware appends the affected filename by adding .King_Ouroboros before an extension as shown below.
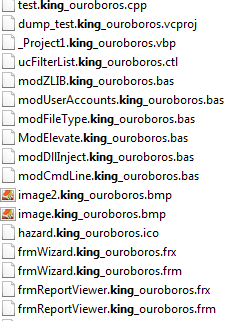
Figure 2 Extension
Once the encryption has been completed it will show the ransom note contains the details of attackers E-mail Address (King.Ouroboros@protonmail.com) and victim Personal ID. Bad actors demands 50$ of ransom for decryption, as shown below in screenshot:
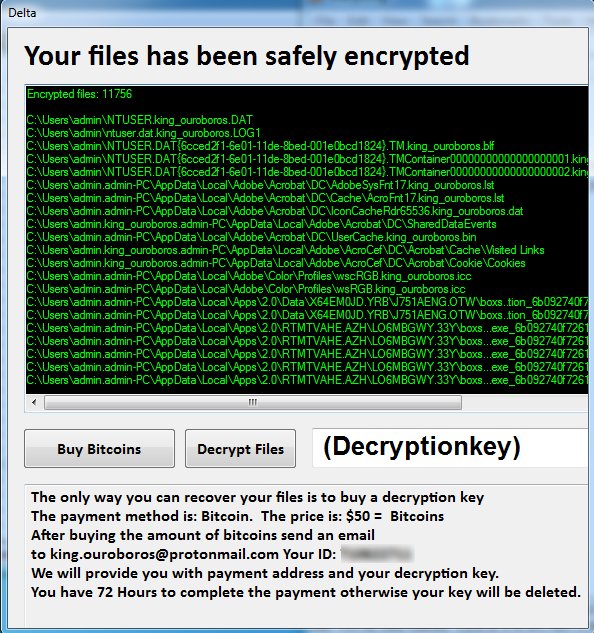
Figure 3 Ransom Note
This ransomware contains following network activities:
orangepresident[.]pw/Kim/usr[.]php?id=UEM=&k=a25pVHFlUU9rSkVhVUM2bVM5TDkx&did=MzMwMDUzNzkyNw==
104.16.54.3 : 443
104.24.125.143 : 80
Are you worried about your PC health?
Check your PC Health for Free!
IOC’s
Associated File Names & Hashes:
|
File Name
|
Hash
|
|
KingOuroboros.exe
|
8893004B04B4436EB47E9B504B7A437F
|
Associated File Paths:
C:\Program Files\ Common files\log.txt
C:\Program Files\ Common files\sample.exe
C:\Program Files\ Common files\710622711710622711
C:\Program Files\ Common files\117226017
Associated Mutexes:
\Sessions\1\BaseNamedObjects\8gf3892489g09j
8gf3892489g09j
Associated E-Mail ID
King.Ouroboros@protonmail.com
Associated Network Info
orangepresident[.]pw/Kim/usr[.]php?id=UEM=&k=a25pVHFlUU9rSkVhVUM2bVM5TDkx&did=MzMwMDUzNzkyNw==
104.16.54.3 : 443
104.24.125.143 : 80
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
