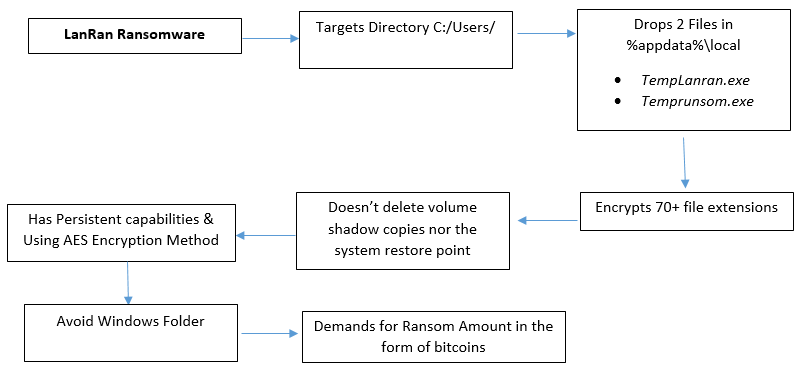
LANRAN Ransomware Overview
Recently, a security researcher has found the new ransomware “LanRan Ransomware”.
This ransomware appends the filename of the affected file by adding .LanRan2.0.5 extension in the last.
Once the encryption has been completed it shows the ransom note UI on the screen in the form of notepad & also changes the Desktop Wallpaper.
As per the ransom note, it demands 0.5 BTC in exchange for decryption. This ransomware is using AES encryption technique for encryption.
This ransomware contains some bugs in the code might be due in the development stage.
Flowchart

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
Technical Analysis of LanRan Ransomware
File Name: lan_ran.exe
MD5: E168392066C6D00C6DE6B71C82ADCDB3
SHA1: 014EFBC6F7EF15CF466D615E0B9355120AEF2C2D
SHA256: EE5EBB71405D500052076C8E1885555DE9414454839E9C26A2746B1CC97FE7EF
File Type: .EXE
Detail Description of LanRan Ransomware with Screenshots
On execution of this ransomware, it first drops 2 files in %AppData%\Local folder
- TempLanran.exe
- Temprunsom.exe
Once the files are dropped thereafter it starts the encryption process, as you can see the following process tree

Figure 1 LanRan process tree
This ransomware targets the C:\Users directory and also containing a list of specials folders to target
|
Personal Folder
|
MyPictures Folder
|
Desktop
|
MyMusic
|
|
Desktop Directory
|
Startup
|
Programs
|
ApplicationData
|
|
Favorites
|
|
As shown below, this ransomware uses AES Encryption technique with Password Hashing (SHA-256) Technique.
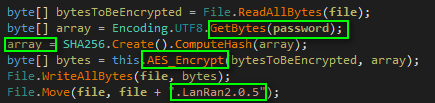
Figure 2 AES Encryption with Password Hashing
As shown below, while the encryption is running in the background it drops the ransom note on the system and changes the desktop background with a ransom note.
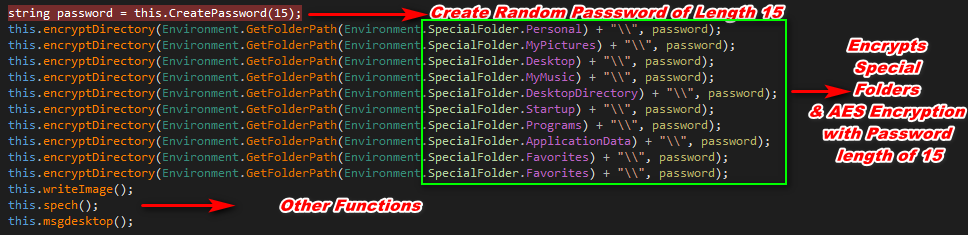
Figure 3 Encrypts Folder & Drops Ransom Notes
This ransomware encrypts only those files that matches with its file extensions list. Following is the file extensions list
“.txt .doc .docx .mp3 .xls .xlsx .ppt .sql .wmv .mp4 .mp3 .iso .dll .jar .pptx .odt .jpg .tar .gz .bmp .pbm .rtf .png .csv .sql .mdb .sln .php .avi .mov .flv .amv .mpv .mtv .asp .aspx .html .xml .psd .pdf .exe .rv .rvx .ved .wm .wmv .TXT .JPG .rar .xwmv .wma .midi .fla .pdf .wma .ico .gif .GIF .ogg .mpg .icns .RAR .png .zip .BAT .Exe .c .exe .PNG .iso .7z .7Z”
As shown below, this ransomware also tries to scan all the drive letters from “A to Z” so that they can infect all the drives on the system with the condition to avoid Windows Folder.
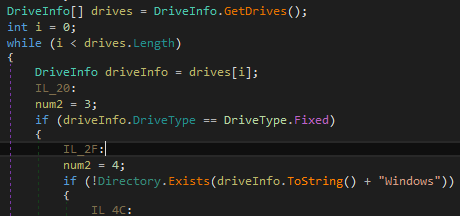
Figure 4 Drive Folder
As shown below, this ransomware attempts to create the persistence entry in the registry, but due to bugs in the code didn’t created it.
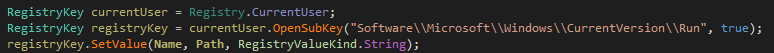
Figure 5 Autorun Entry
This ransomware doesn’t delete any volume shadow copies or system restore point from the system might be due to in development stage.
As shown below after getting infected with LanRan Ransomware, we can still recover our files without contacting to malware actor, if the system has any restore point available or Folder Snapshots are available then we can easily recover our files.
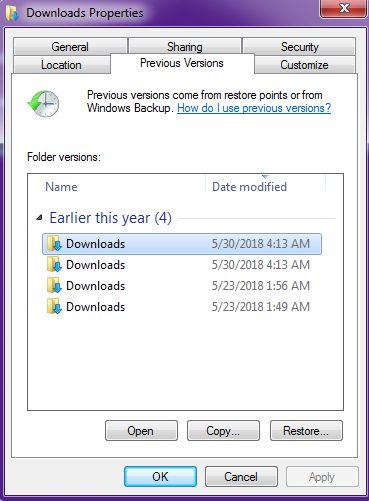
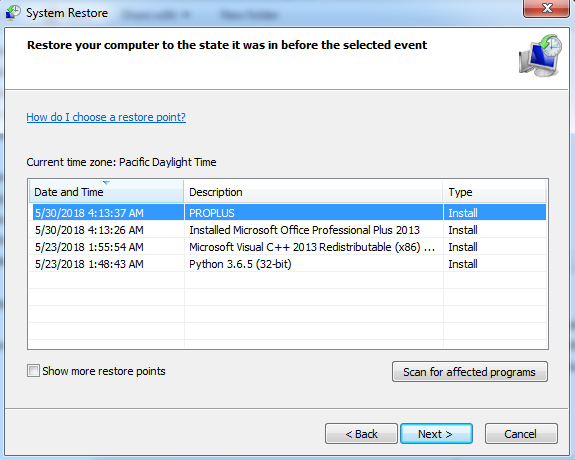 Figure 5 Restore Points
Figure 5 Restore Points
As shown below, While the ransomware is running in the background it appends the affected filename by adding “.LanRan2.0.5” in the last.
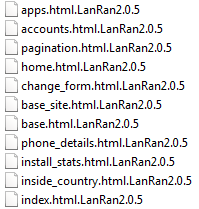
Figure 6 LanRan File Extension
As shown below, once the encryption has been completed it shows the ransom note in the form of a notepad.
This ransomware also drops the ransom note on the Desktop in form of a text file and also changes the desktop wallpaper.
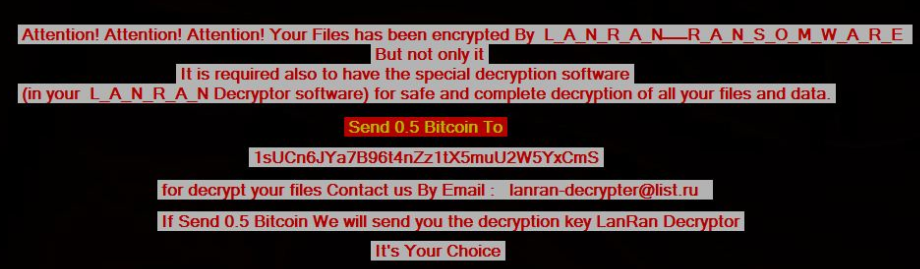
Figure 7 Wallpaper Ransom Note
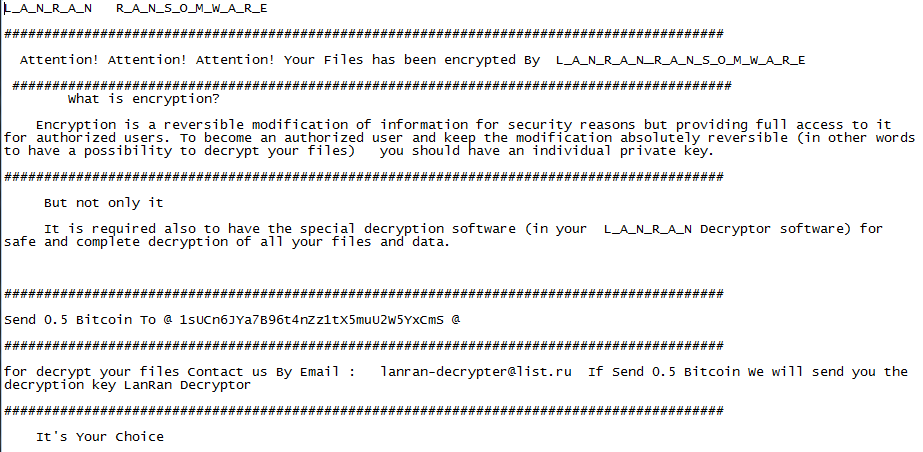
Figure 8 Notepad Ransom Note
As shown below, this ransomware looks for the specific folder “C:/Users/Cerberos/Desktop” to drop the ransom note. If this location didn’t exist on the system, it will throw the following error
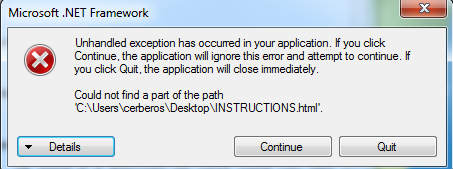
Figure 9 Ransom Note Location Error
If the ransomware founds the specified location, it drops the instructions.html ransom note. While opening the instructions.html it opens the following ransom note in the browser.

Figure 10 Browser Ransom Note
As shown below, this ransomware also contains the voice code that speeches the ransom note
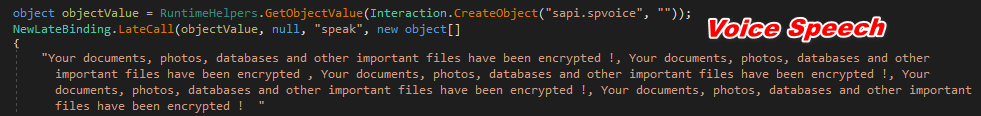
Figure 11 Voice Speech Ransom Note
As shown above, in the ransom note, ransomware creator has demanded ransom amount of 0.5 Bitcoin and also mentioned his Bitcoin Address (“1sUCn6JYa7B96t4nZz1tX5muU2W5YxCmS”) & Email Address (“lanran-decrypter@list.ru”) to contact them.
As shown below, none of the victims has paid any ransom amount on the given bitcoin address till yet & this bitcoin address doesn’t have any transaction history also.
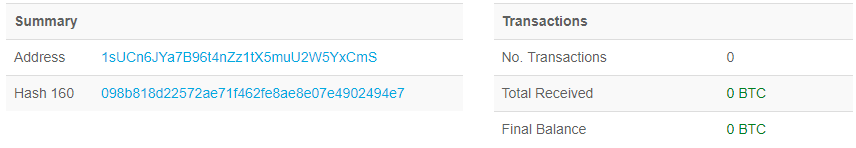
Figure 12 Bitcoin Address Information
During analysis we have found that this ransomware didn’t work properly might be due to in development stage and also contains some bugs in the code which can be easily rectify by anyone.
Are you worried about your PC health?
Check your PC Health for Free!
IOC’s
Associated File Names & Hashes:
Filename:LanRan.exe
MD5: E168392066C6D00C6DE6B71C82ADCDB3
SHA1: 014EFBC6F7EF15CF466D615E0B9355120AEF2C2D
CRC32: 8DA25561
SHA-256: EE5EBB71405D500052076C8E1885555DE9414454839E9C26A2746B1CC97FE7EF
Filename:TempLanRan.exe
MD5:3061A661FF7B83F0E30952D06EE22AB9
SHA1:A11F06AF9E3686751D6DF821F0DEB3068B0295F7
CRC32:D93F3094
SHA-256:654F2CD5292C9A25567238840A0E6215E7E8EF87367D676B5EB25DDB71B03E4A
Filename:Temprunsom.exe
MD5:F11B9F67C1433C073599A27FC1ADE14F
SHA1:F7D9BD50DFAA2A422E95F003CBD9DE498C651A2A
CRC32:6C62C2D0
SHA-256:38D8BCF1693BE2705B2A5BA647C5371BC56AC2CBACC44E739AAE33C282E1F583
Filename:@___README___@.txt
MD5:9213FB1B65565F8D5CA5857293D9DC52
SHA1:10F33BA3F38F06B200F779358B3ED00EC8CE9B99
CRC32:2AD12CA9
SHA-256:CD67AA52D41B9F0189A76CB2A8256934075FA26DF69886D9765D83FCDFA6674F
Filename:img.jpg
MD5:4EE0646461B01405B722581618BDC4B6
SHA1:D24ACEE6BA1E5F0802844A87E158BC78E4246B4C
CRC32:CB5AA10A
SHA-256:17CF70C6714E0368C28E8F7FF71BE3238FBA4BF7AB8D38107CD4DB007E9BE21F
Associated Contact ID:
lanran-decrypter@list.ru
Associated Bitcoin Address:
1sUCn6JYa7B96t4nZz1tX5muU2W5YxCmS
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
