Paradise Ransomware Overview
Recently a new variant of Paradise Ransomware has been captured by the security researchers.
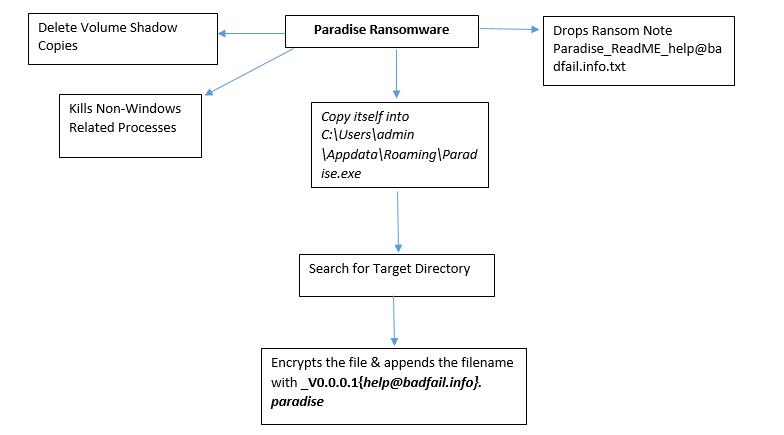
This ransomware deletes the backup option from the system so that user can’t go back to the restore point option.
In the previous variant of Paradise ransomware, it was using paradise@all-ransomware.info.paradise, info@decrypt.ws.paradise in the last during appending the filename but this time this variant appends the file name by adding _V0.0.0.1{help@badfail.info}.paradise in the last of the affected file name.
This ransomware drops ransom note in the affected scan folder but it doesn’t contain any ransom amount information.
Flowchart
Read Also: Detailed Technical Analysis of SMOKE LOADER Malware Campaign Attack

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
Technical Analysis of Paradise Ransomware
File Name: Paradise.exe
MD5: A3C124F16AFA74B9BEBDDBEC347AFE58
SHA1: C524CCED3231C4875C661B6E686C9E2181AA368F
SHA256: 220CC62A29EDE8CF7B9492213A1927003A5C268097DD57D703C9439DF2AA19A4
File Type: .EXE
Detail Description of Paradise Ransomware with Screenshots
On execution of this ransomware, it requires administrative privileges and kills all other processes except windows related processes if it found any other process is running which is not related to windows.
Thereafter this ransomware deletes the volume shadow copy and disable recovery mode by initiating the following commands
C:\Windows\System32\vssadmin.exe" delete shadows /all /Quiet
C:\Windows\System32\bcdedit.exe" /set {current} bootstatuspolicy ignoreallfailures
"C:\Windows\System32\bcdedit.exe" /set {current} recoveryenabled no
"C:\Windows\System32\bcdedit.exe" /set {default} bootstatuspolicy ignoreallfailures
At same time, it also drops following files in My Documents Folder:
ID_CLIENT_help@badfail.info.paradise
Paradise_key.bin
Paradise_key_pub.bin
Registry Modifications:
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
HKLM\Software\Microsoft\Tracing\paradise_RASMANCS
HKCU\Software\Microsoft\windows\CurrentVersion\Internet Settings\Connections
HKCU\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Network\Location Awareness
HKLM\System\CurrentControlSet\Services\Tcpip\Parameters
HKLM\System\CurrentControlSet\Control\SecurityProviders\Schannel
This ransomware takes advantage of following Microsoft Cryptographic API’s to encrypt the files:
CryptGetUserKey
CryptGenRandom
CryptGenKey
CryptDestroyKey
This ransomware searches for some processes with the help of CreateToolhelp32Snapshot, Process32First & Process32Next.
It contains some interesting API’s (Anti-Debugging API’s) that checks whether the malware is running under any debugger or not, below are some of them:
Isdebuggerpresent
GetSystemTime
GetTickCount
CheckRemoteDebuggerPresent
As shown below, this ransomware appends the affected filename by adding help@badfail.info.paradise in the last.
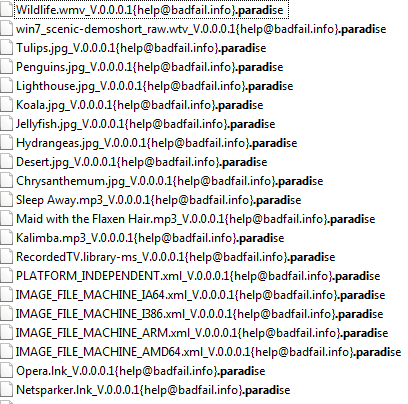
Figure 1 Extension
This ransomware drops ransom notes in every affected scan folder but it doesn’t contain any ransom amount information.
Ransom note contains the following information:
To decrypt your files, please contact us by mail -- help@badfail.info and help@badfail.info
Your UserID is: {%userid%}
with respect to Ransomware Paradise Team
Once the encryption has been completed on the system, it launches the following ransom note on the User’s screen.
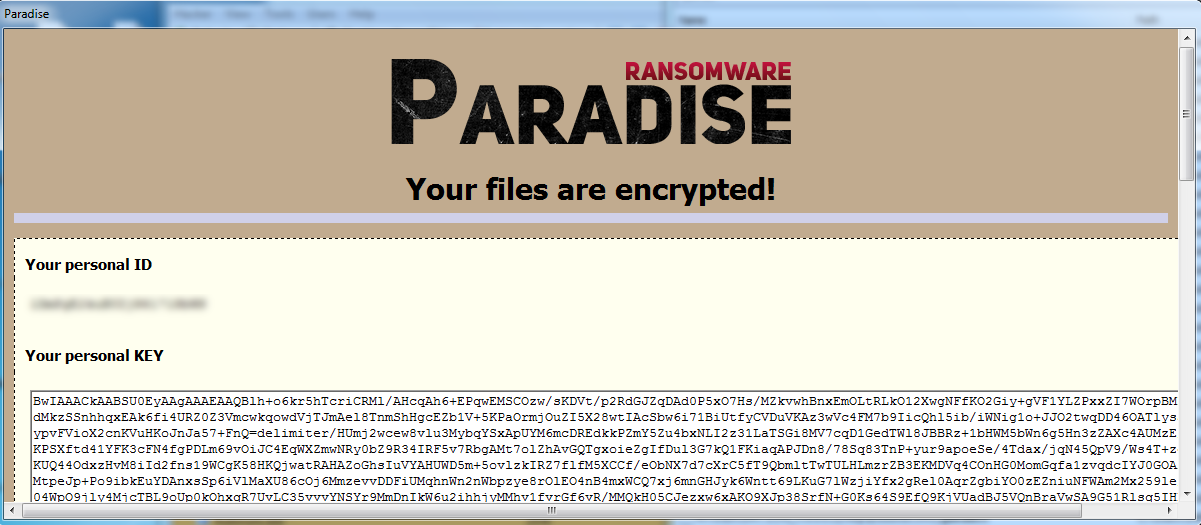
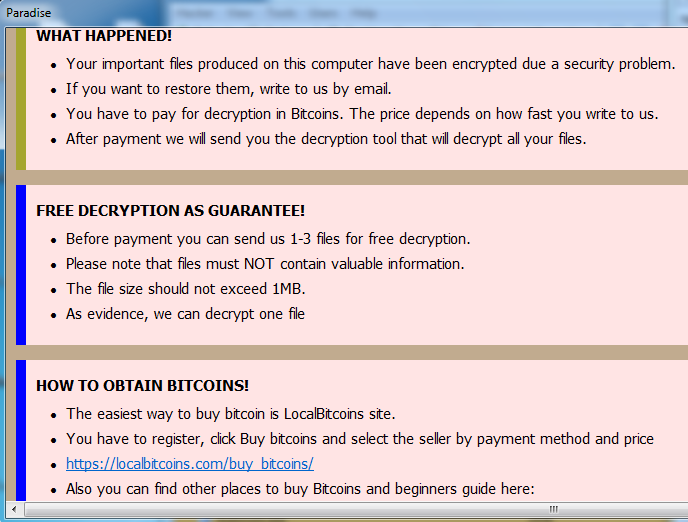
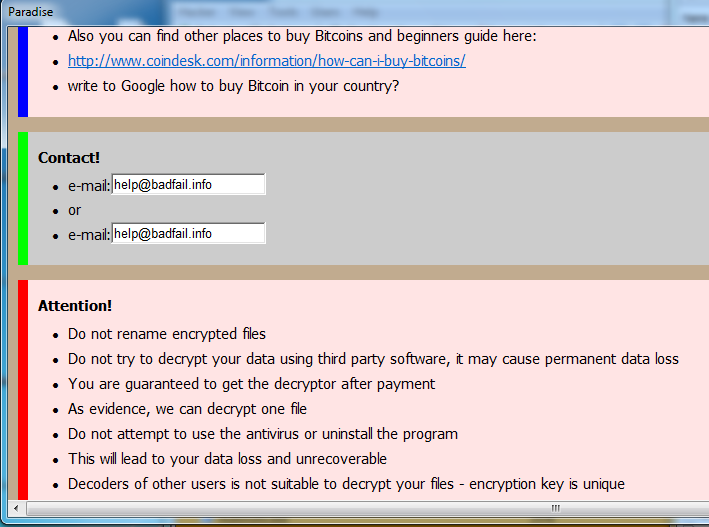
Figure 2 Ransom Note
IOC’s
Associated File Names & Hashes:
|
File Name
|
Hash
|
|
Paradise.exe
|
A3C124F16AFA74B9BEBDDBEC347AFE58
|
Associated File Paths:
C:\Users\admin \Appdata\Roaming\Paradise.exe
Associated Registry Info:
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
HKLM\Software\Microsoft\Tracing\paradise_RASMANCS
HKCU\Software\Microsoft\windows\CurrentVersion\Internet Settings\Connections
HKCU\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Network\Location Awareness
HKLM\System\CurrentControlSet\Services\Tcpip\Parameters
HKLM\System\CurrentControlSet\Control\SecurityProviders\Schannel
HKLM\SOFTWARE\Microsoft\Tracing\paradise_RASAPI32\EnableFileTracing
HKLM\SOFTWARE\Microsoft\Tracing\paradise_RASAPI32\EnableConsoleTracing
HKLM\SOFTWARE\Microsoft\Tracing\paradise_RASAPI32\FileTracingMask
HKLM\SOFTWARE\Microsoft\Tracing\paradise_RASAPI32\ConsoleTracingMask
HKLM\SOFTWARE\Microsoft\Tracing\paradise_RASAPI32\MaxFileSize
HKLM\SOFTWARE\Microsoft\Tracing\paradise_RASAPI32\FileDirectory
HKLM\SOFTWARE\Microsoft\Tracing\paradise_RASMANCS\EnableFileTracing
HKLM\SOFTWARE\Microsoft\Tracing\paradise_RASMANCS\EnableConsoleTracing
HKLM\SOFTWARE\Microsoft\Tracing\paradise_RASMANCS\FileTracingMask
HKLM\SOFTWARE\Microsoft\Tracing\paradise_RASMANCS\ConsoleTracingMask
HKLM\SOFTWARE\Microsoft\Tracing\paradise_RASMANCS\MaxFileSize
HKLM\SOFTWARE\Microsoft\Tracing\paradise_RASMANCS\FileDirectory
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyEnable
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyServer
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyOverride
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\SavedLegacySettings
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\UNCAsIntranet
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\AutoDetect
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\UNCAsIntranet
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\AutoDetect
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\02FAF3E291435468607857694DF5E45B68851868
Are you worried about your PC health?
Check your PC Health for Free!
Associated Email:
help@badfail.info
Associated Network Info:
http://146.185.241.35/api/Encrypted.php
77.123.139.190 (api.2ip.ua)
190.139.123.77.colo.static.dcvolia.com
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
