RaRansomware Ransomware Overview
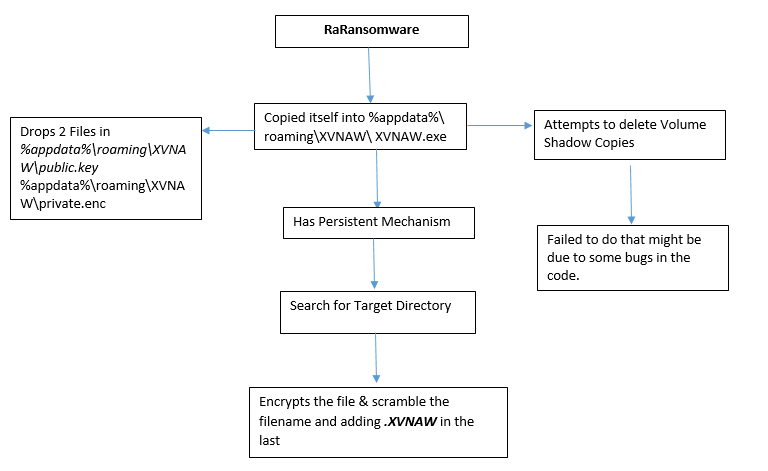
Recently, a security researcher has found a new ransomware RaRansomware. This ransomware modifies the filename of the affected file by using scrambled strings and adding .XVNAW extension in the last. For ex: UgBFAEEARABNAEUALgB0AHgAdAA=.XVNAW
This ransomware attempts to delete the volume shadow copies or System Restore point from the system but might be due to some bugs it didn’t get success in that.
Once the encryption has been completed, it shows the ransom note in the browser but it didn’t get loaded into the browser. After Restarting the system, it will recall the ransom note in the browser due to Persistent Mechanism.
Flowchart

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
Technical Analysis of RaRansomware Ransomware
File Name: Sample.exe
MD5: 550A730BFCB7D164765FD8894548D375
SHA1: 47EC45FE98C0B207AFB8B35AFB84C2755F619C5D
SHA256: 3FBDE3F4DC46B57DC0017239F0C55CFD65855E2A506CDAD250F975C41257887F
File Type: .EXE
Spread Via: Email via Zip Attachment
See Also: Detailed Technical Analysis Report of KingOuroboros Ransomware Attack
Detail Description of RaRansomware Ransomware with Screenshots
On execution of this ransomware, it deletes itself from the origin location and copies itself into %appdata%\Appdata\Roaming\XVNAW\XVNAW.exe and then it executes following sub-processes as shown below in the screenshot.
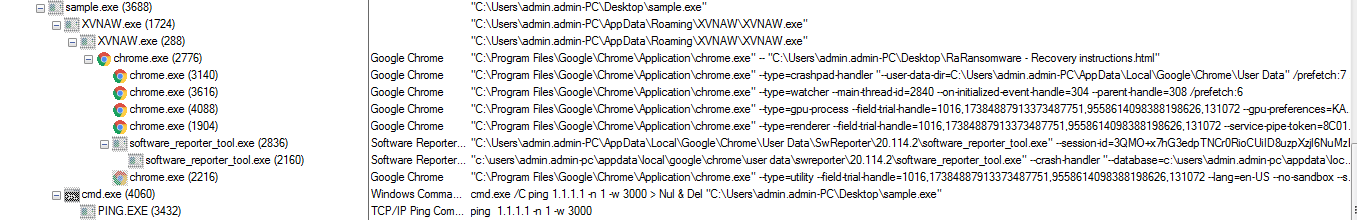
Figure 1 Process Tree
This ransomware also creates the following files at %appdata%\Appdata\Roaming\XVNAW
XVNAW.exe
Public.key
Private.enc
This ransomware takes advantage of following Microsoft Cryptographic API’s to encrypt the files:
CryptGetUserKey
CryptGenRandom
CryptGenKey
CryptDestroyKey
This ransomware searches for some processes with the help of CreateToolhelp32Snapshot, Process32First & Process32Next.
It contains some interesting API’s (Anti-Debugging API’s) that checks whether the malware is running under any debugger or not, below are some of them:
Isdebuggerpresent
CheckRemoteDebuggerPresent
GetSystemTime
GetTickCount
As shown below, this ransomware modifies the affected filename by scrambling the filename and adding .XVNAW extension in the last.

Figure 2 Extension
This ransomware attempts to encrypt only specific files that matches with its extension criteria. It has more than 135+ Files Extensions.
.TIOX .TPOV .mid .wma .flv .mkv .mov .avi .asf .mpeg .vob .mpg .wmv .fla .swf .wav .qcow2 .vdi .vmdk .vmx .gpg .aes .ARC .PAQ .tar .bz2 .tbk .bak .tar .tgz .rar .zip .djv .djvu .svg .bmp .png .gif .raw .cgm .jpeg .jpg .tif .tiff .NEF .psd .cmd .bat .class .jar .java .asp .brd .sch .dch .dip .vbs .asm .pas .cpp .php .ldf .mdf .ibd .MYI .MYD .frm .odb .dbf .mdb .sqSTR_W .SQLITEDB .SQLITE3 .asc .lay6 .lay .ms11 .sldm .sldx .ppsm .ppsx .ppam .docb .mml .sxm .otg .odg .uop .potx .potm .pptx .pptm .std .sxd .pot .pps .sti .sxi .otp .odp .wks .xltx .xltm .xlsx .xlsm .xlsb .slk .xlw .xlt .xlm .xlc .dif .stc .sxc .ots .ods .hwp .dotm .dotx .docm .docx .DOT .max .xml .txt .CSV .uot .RTF .pdf .XLS .PPT .stw .sxw .ott .odt .DOC .pem .csr .crt .key wallet .dat
This ransomware excludes the following folder from its encryption folder list
Program Files
Windows
Program Files(x86)
Application Data
Temp
Recycle Bin
As shown below, while reading memory strings we came to know that this ransomware attempts to delete the volume shadow copies or system restore point from the system but might be due to some bugs, it didn’t succeed to delete the volume shadow copies.
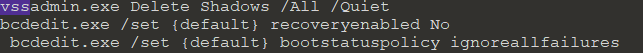
Figure 3 Memory Strings
As shown below, after getting infected with RaRansomware, we can still recover our files without contacting to malware actor, if the system has any restore point available or Folder Snapshots are available then we can easily recover our files.
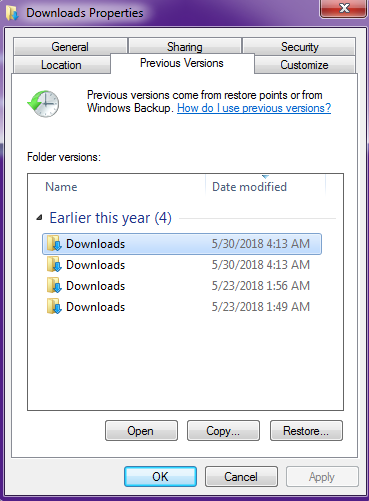
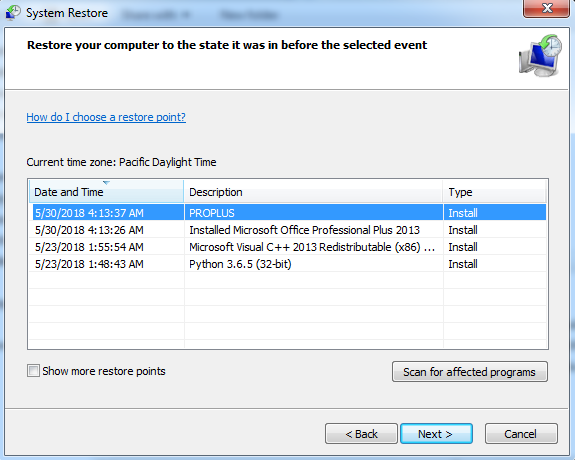
Figure 4 Restore Points
As shown above, the victim can easily restore the files by going back to the system restore point or restoring to previous folder option.
Once the encryption has been completed it will show the ransom note in the browser that contains the steps to contact malware actor to get the decrypted files back.
It might be due to some bugs in the code ransom note didn’t get loaded into the browser until the system has not restarted.
This ransomware has persistent mechanism capabilities as it creates the following entry in the registry:
HKCU\Software\Microsoft\Windows\Current Version\Run
XVNAW Oklahoma Tire & Supply Company c:\users\admin.admin-pc\appdata\roaming\xvnaw\xvnaw.exe
And due to this, it launches the ransomware at boot time, as shown below after restarting the system ransomware is easily loaded the ransom note in the browser.
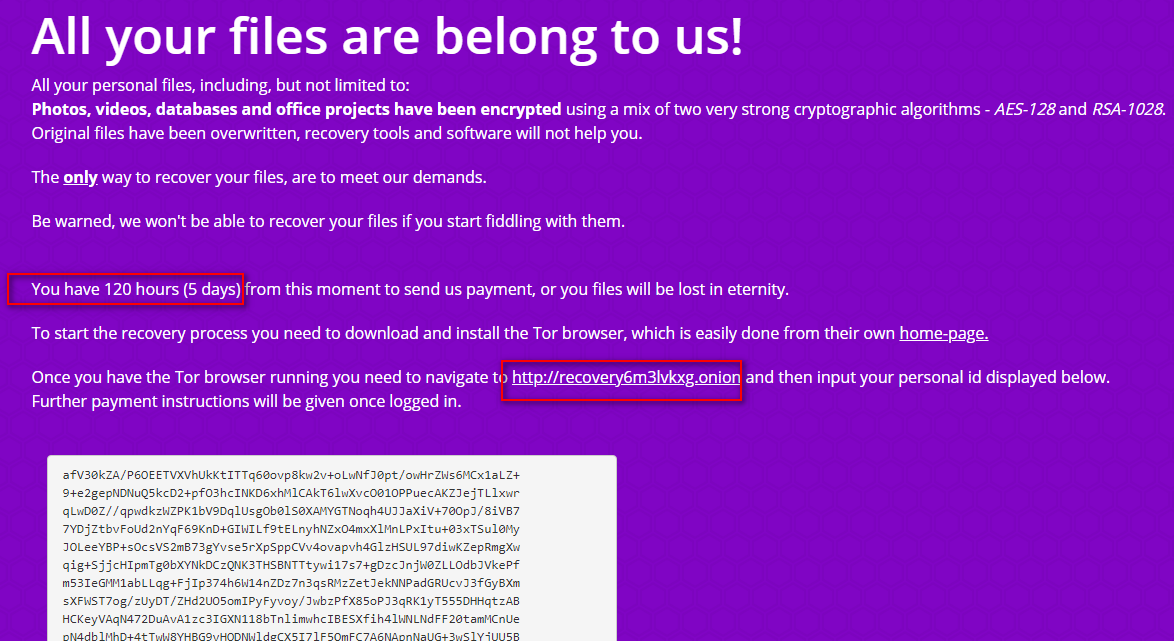
Figure 5 Ransom Note
As shown above, as per the ransom note, this ransomware uses 2 cryptographic algorithms
AES-128 & RSA-1028 which makes the encryption strong. It also mentions its time limitation to get back the decrypted files.
As per the ransom note, the victim has only 120 Hours or maximum 5 Days to recover the files by sending the payment to the malware actor.
Malware actor has chosen the anonymous channel mode so that it can hide their identity. Malware actor is using TOR Onion link; which is only accessible by TOR Browser.
If the victim wants to contact with the malware actor then it needs to install the TOR Browser first and then navigate to the given onion link in the ransom note, thereafter it needs to put his personal ID to get further instructions for the payment.
But we will always suggest to our users to never pay any ransom to any malware actor as it encourages them.
It’s better to take backup on a regular interval. As we know this ransomware didn’t delete any system restore point or Previous folder option. So by going back to the system restore point, we can easily recover our files.
By entering the given link (hxxp://recover6m3Ivkxg.onion) in TOR Browser to get the payment information, we get the connection has timed out the error.
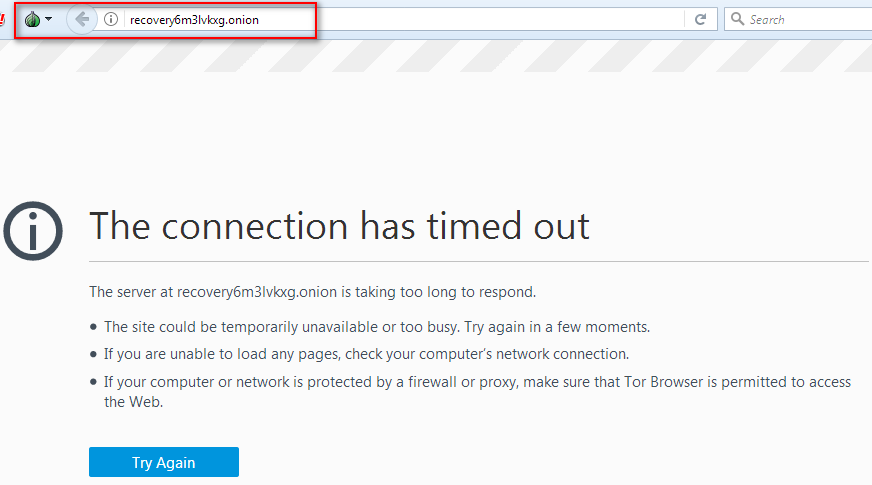
Figure 6 Timed Out Error
This ransomware contains following network activities:
hxxp://bitly[.]com/2u086NE
hxxp://www[.]parenting[.]com[.]tw
hxxp://recover6m3Ivkxg.onion
hxxp://www[.]download[.]windowsupdate[.]com/msdownload/update/v3/static/trustedr/en/authrootstl[.]cab
Are you worried about your PC health?
Check your PC Health for Free!
IOC’s
Associated File Names & Hashes:
|
File Name
|
Hash
|
|
RaRansomware.exe
|
550A730BFCB7D164765FD8894548D375
|
Associated File Paths:
%appdata%\Appdata\Roaming\XVNAW\XVNAW.exe
%appdata%\Appdata\Roaming\XVNAW\public.key
%appdata%\Appdata\Roaming\XVNAW\private.enc
Associated Registry:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\XVNAW
HKLM\SOFTWARE\Microsoft\Tracing\_RASAPI32\EnableFileTracing
HKLM\SOFTWARE\Microsoft\Tracing\_RASAPI32\EnableConsoleTracing
HKLM\SOFTWARE\Microsoft\Tracing\_RASAPI32\FileTracingMask
HKLM\SOFTWARE\Microsoft\Tracing\_RASAPI32\ConsoleTracingMask
HKLM\SOFTWARE\Microsoft\Tracing\_RASAPI32\MaxFileSize
HKLM\SOFTWARE\Microsoft\Tracing\_RASAPI32\FileDirectory
HKLM\SOFTWARE\Microsoft\Tracing\_RASMANCS\EnableFileTracing
HKLM\SOFTWARE\Microsoft\Tracing\_RASMANCS\FileDirectory
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyEnable
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\SavedLegacySettings
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\UNCAsIntranet
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\AutoDetect
HKCU\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\LanguageList
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\P3P\History
HKCU\Software\Microsoft\Windows\Current Version\Run/
XVNAW Oklahoma Tire & Supply Company c:\users\admin.admin-pc\appdata\roaming\xvnaw\xvnaw.exe
HKLM\SOFTWARE\Microsoft\EnterpriseCertificates\Trust\Certificates
HKLM\SOFTWARE\Microsoft\EnterpriseCertificates\Trust\CRLs
HKLM\SOFTWARE\Microsoft\EnterpriseCertificates\Trust\CTLs
Associated Network Info
hxxp://bitly[.]com/2u086NE
hxxp://www[.]parenting[.]com[.]tw
hxxp://recover6m3Ivkxg.onion
hxxp://www[.]download[.]windowsupdate[.]com/msdownload/update/v3/static/trustedr/en/authrootstl[.]cab
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
