Ardamax Keylogger Software - A Hoax, A Virus
Keylogging is not a new word in the world of internet. In general terms, we call keylogging a mechanism where companies and organizations do surveillance of their employers to keep a check what work they are doing on their computers.
It means that your actions on the computer are monitored or recorded daily with some closed source program. The software that records your action or activity is known as Keylogger Software.
Keylogger can either be a software or hardware. Keylogger software generally record key struck on keyboards while the person is unaware that their actions are getting recorded.
A keylogger records instant messages, emails and captures any kind of information you type using your keyboard. Some keylogger programs also record email addresses you use and the URLs of the websites you visit.
While the keylogger retrieves the data of a person’s action, most of the keylogger software are often used for stealing passwords and confidential information. One such keylogger software found in today’s computer is Ardamax Keylogger.
With the growing market of the internet, parents are also using keylogging software only to stay informed about their childrens' online activities.
Unfortunately, there have been several cases where keyloggers like Ardamax are a reason for the entry of viruses, malware, spyware and adware into your systems.
Ardamax Keylogger - A Controversial Tracking Tool With False Claims
Ardamax Keylogger is a spying and tracking tool that monitor what keys are struck on the keyboard. It collects the login input through keyboard information and sends it to the designated email address (possibly of cyber attackers) within certain periods of time.
Using keylogger for monitoring is a good side, however, transmitting that information to some other person in some corner of this world is the evil side. Hence, it depends on person to person how one wishes to use this keylogger software.
But, in this article, we will tell you how cybercriminals track the user’s sensitive data, like passwords, financial and personal information? How attackers use keylogger tool to their whim? Furthermore, to prevent the leak of information what you should do against Ardamax keylogger?
Ardamax claims itself as an affordable, compact, and remarkably powerful and flexible keylogger which is incorrect. It introduces its working style as - operating silently in the background while recording every keystroke and saving all records into an encrypted log file that can’t be opened by the user (if the file is found).
However, the log file is exclusively accessible only to the admin of the computer or system. Ardamax is created for the new processor and works as spyware. This is the only reason of cyber villains liking the program.
Even if you download the software from the actual source viz website, detecting the tool becomes difficult as it operates in a hidden way. If you can’t detect the program but suspect the change in your passwords and other credentials, then it is the work of Ardamax Keylogger virus injected by Ardamax software.
Once this software installs on your computer, most likely it is not found in Windows Task Manager as it keeps on changing its location to monitor your activities. Thus, there are high chances that this tool might be used against you by cybercriminals.
It is almost impossible to understand that your computer is being monitored by such a program which shows no signs of existence.
Ardamax Software Features Are Tricks To Capture Everything You Do
- It captures chats with every keystroke you make on your keyboard.
- It remains invisible as a spyware and launches viruses into your computer.
- It also does visual surveillance, capture screenshots and understands the context of users behavior.
- It remotely monitors everything and accesses your system without your permission.
- It also uses a microphone to record the audio. Along with visual surveillance, text surveillance, it also collects your audio data.
- Every piece of collected data is sent to cybercriminals via email, network and FTP server.
Three top reasons why Ardamax software entices users to download Ardamax keylogger are as follows:
- The Internet is full of dangers and misleads the children. Therefore, it suggests protecting your children online with the keylogger.
- Online dating nowadays is growing fast and to catch your cheating partner you can use this software.
- Being an employer, you can use this software to keep a watch on your employees.
All these features look nice but violate our fundamental rights of privacy. You might ask how?
The answer is if your chats, texts, videos, audios and all other formats of data are being monitored than a question should click in your mind.
Where this data is going and who is monitoring it? The answer is cybercriminals who somehow installed the software into your computer without letting you know about it. In such cases, you must install antivirus or antimalware tool so that your data remains safe and could detect program which shows no existence.

Never Compromise With Your Privacy
Ardamax keylogger infection is the result of the low system and Internet defenses. This software doesn’t need user’s interference in order to get into the system. Moreover, it infiltrates the PC when the user doesn’t follow practices of the safe browsing.
Once installed, it installs an IJE.exe file, akv.exe and QXI.exe files to %APPDATA% folder and %PROGRAMFILES% directory. Additionally, you may also notice two different Winlogon.exe processes.
Though ending the task of any legitimate command might lead to sever system issues, it is not recommended at all to cancel the task just by determining which command is genuine and which might be confusing.
Few variants of Ardamax Keyloggers: Win32/KeyLogger.Ardamax [NOD32v2], ArdamaxKeylogger [Microsoft], Not-A-Virus.Monitor.Win32.Ardamax.24 [eWido], Generic.Ardamax.AF22012B [BitDefender], not-a-virus:Monitor.Win32.Ardamax.24 [Kaspersky] and Win32:Ardamax-B [Avast].
Keyloggers are not viruses because they don't replicate itself. However, it acts as a supportive program to download viruses and malware. Additionally, it is a data tracking software that must be eliminated from your computer.
Below you can find a few popular virus removal methods. The methods together make a guide which helps to prevent the attacks. The guide is divided into three parts;
- Unlock Your Locked Computer
- Automatic Preventive Method
- Manual Preventive Methods
Unlock Your Locked Computer
Virus infections are very dangerous and could cause a complete block of your computer. The threat locks down the system and doesn’t allow you to access it. Therefore, it is important to unblock the computer. For this follow the below-mentioned process;
- Start your computer and instantly press F8(Windows 7), F5(Windows 8, 8.1 and 10) repeatedly to enter Advanced Boot Options.
- Log on the computer as the Administrator.
- Change or remove your computer’s forgotten password in Control Panel and enable the safe mode options.
Once you enable the Windows manually, you now have a choice to follow both manual and automatic methods.
Automatic Preventive Method
Malware Crusher is the most commonly used anti-malware tool for the Windows computer that scans and removes cyber threats when started manually. Be it any virus attack or any other popular virus or malware, Malware Crusher always keeps your Windows PC safe and secure.
It’s malware removal capabilities makes it the most impactful and vigilant tool that prevents your system before the ransomware starts spreading infection;
- It’s real-time protection feature, performs a deep scan to detects malicious software and persistent threats. Also, identifies suspicious behavior on your computer.
- The Quarantine feature of the tool removes all infected files from your computer. Additionally, keeps a record of all deleted malicious program and allows you to choose important programs to restore at a later time.
- Malware Crusher also creates a shield against Ransomware, Adware, Malware, Browser Hijackers, Viruses, Extensions and Trojans from entering into your system.
- The 24X7 online protective shield works as an anti-exploit technology and blocks the ransomware component before they hold files as a hostage.
- Malware Crusher tirelessly visits all domains, URLs and web pages to secure your online presence from fraudulent entities. Furthermore, the tool detects the vulnerabilities of online fraudulent entities effortlessly.
- Malware Crusher becomes fiercer in detecting keylogging, remote connections and saving your session data from being recorded.
Malware crusher continuously monitors the happenings of cyberworld related security issues. In response to the malicious codes and javascript, the tool writes anti-malware code and diagnose Ardamax Keylogger virus.
After using the tool, you can follow manual methods on a regular basis to keep a watch on pre-installed applications and programs.

Manual Preventive Methods
- Press Ctrl + Shift + ESC together to open Task Manager. Look for suspicious files, right click on it and click End Task.
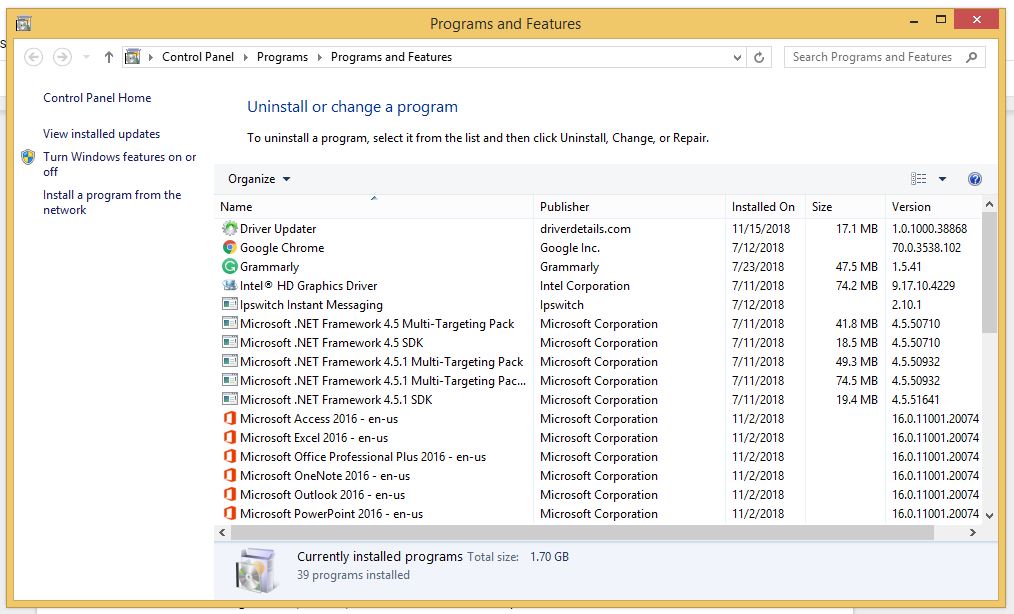
- Now, press it to open RUN box window. Type appwiz.cpl on it, this opens Programs and Features window.
- Select each suspicious program and uninstall it one by one. Once the uninstallation is complete, restart your computer and again redirect yourself to Programs and Features window to check whether the application is present or not.
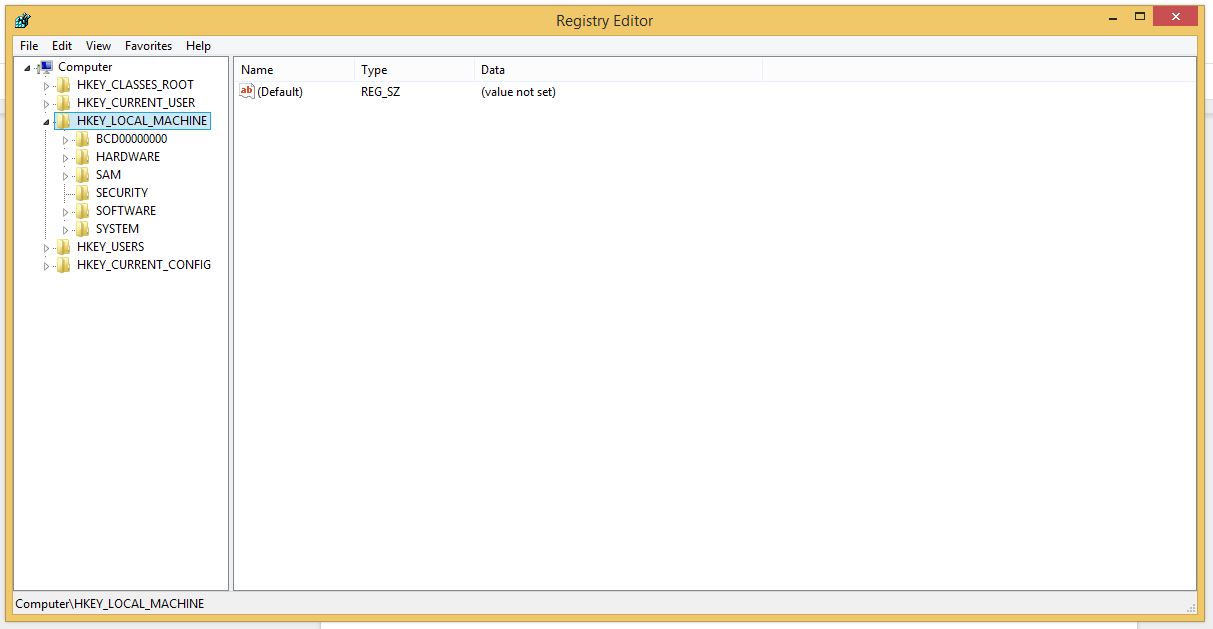
- When convinced, press Windows key + R to open RUN box window. Type regedit on it, hit OK and then click Yes.
- Go through HKEY, HKLM, etc. files and find all suspicious files and delete them.
- You can also delete malicious extensions from your browsers like Chrome and Firefox.
1. Click on the Customize and control menu icon at the top right corner of Google Chrome.
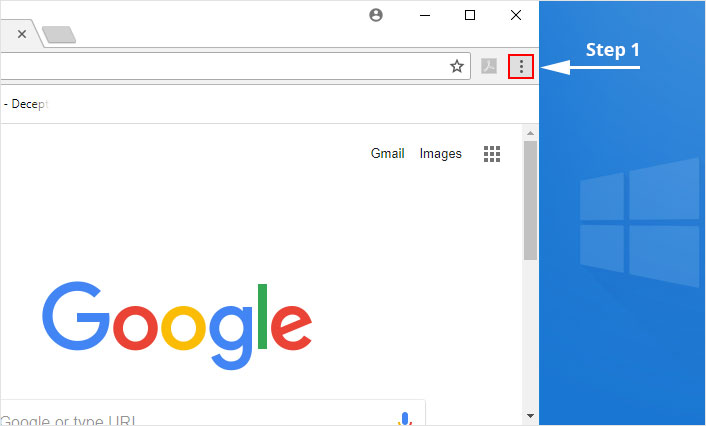
2. Select "More tools" from the menu.
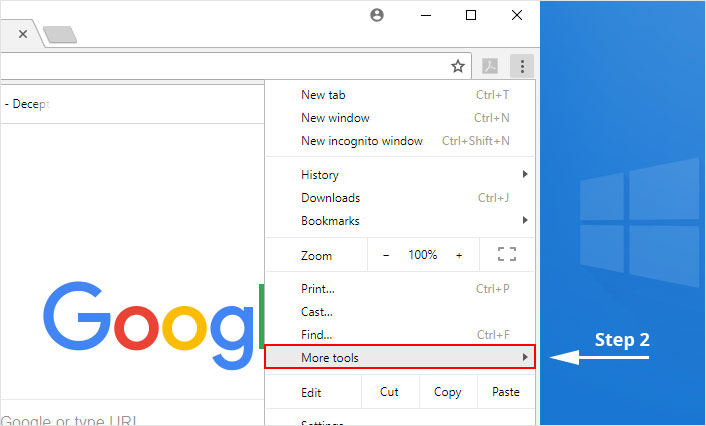
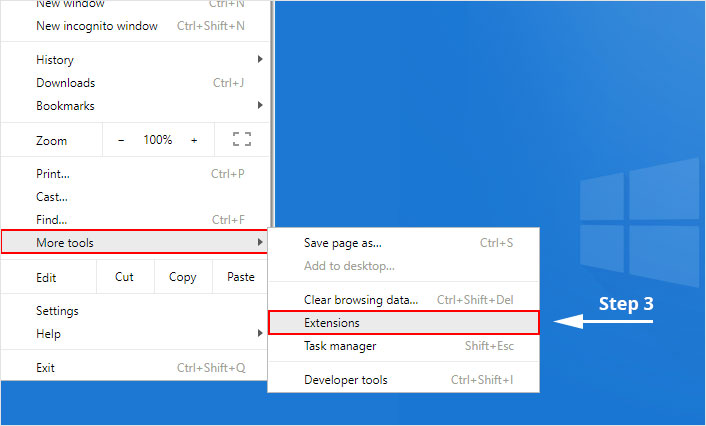
3. Select "Extensions" from the side menu.
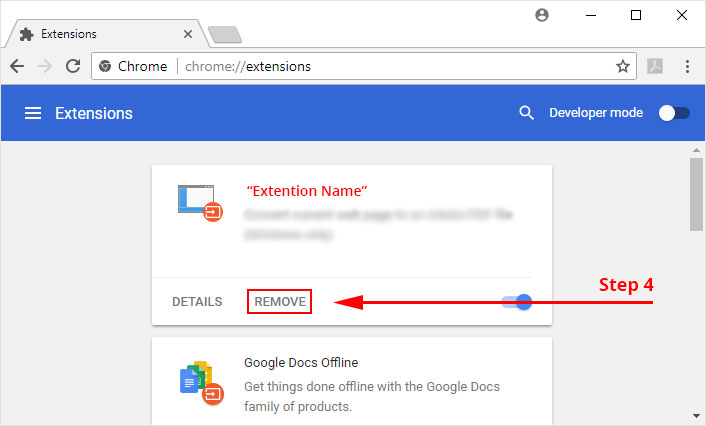
4. Click the remove button next to the extension you wish to remove.
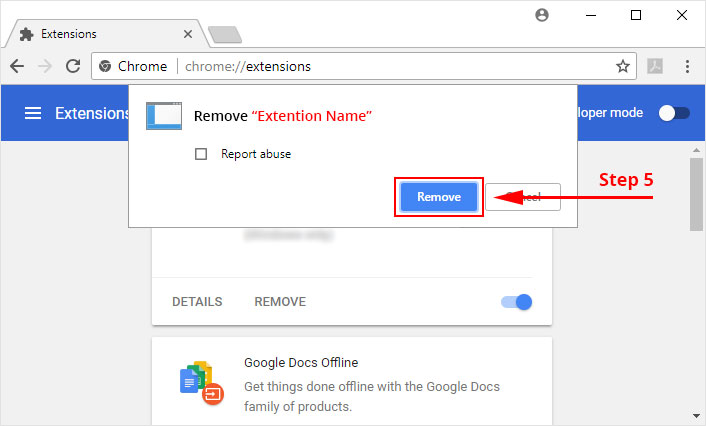
5. It will confirm again, click “remove” and the extension is finally out of the system.
Now that we have successfully eliminated the malicious browser extension, we need to create a robust firewall to avoid any such thing that makes our system and privacy vulnerable to various online threats.
1. Click on the “menu” button at the top right corner.
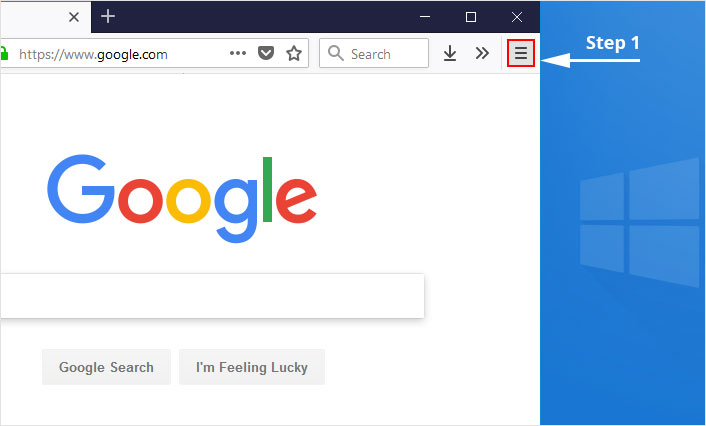
2. Select “Add-ons” from the menu.
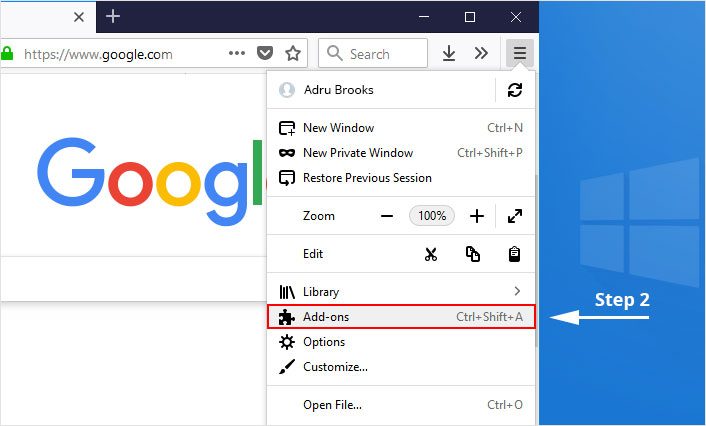
3. Click the “Remove” button next to the extension you wish to get rid of.
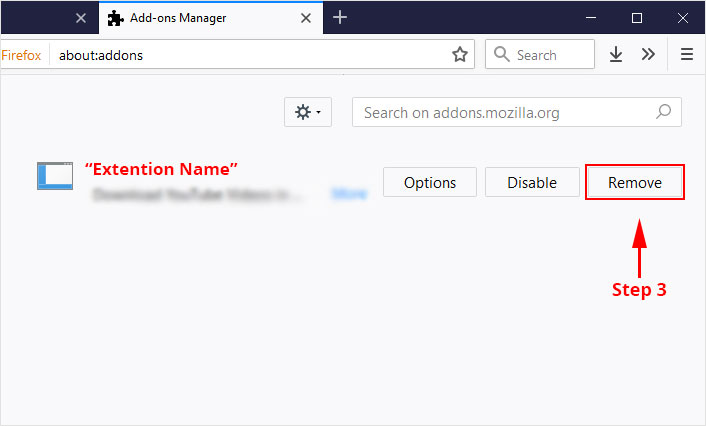
Now that we have successfully eliminated the malicious browser extension, we need to create a robust firewall to avoid any such thing that makes our system and privacy vulnerable to various online threats.
The manual method sometimes might not work at Windows OS because finding suspicious and modified registry files in registry editors is a difficult task. On the other hand, if a useful file deletes, then the windows stop working properly.
That’s why it is highly recommended to use an automatic tool to prevent and remove the software and its virus infections from your computer. If you wish to get more news and awareness on the happenings of the cybersecurity, then keep visiting us.
To get a better security awareness on preventing cyber-attacks and internet security threats, keep visiting us and forget not to download Malware Crusher. Its 5-minute function could become a savior for your Windows computer.
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
