Chrome.7Z Virus - Extremely Intrusive Threat!
With the increase in malicious threats, the attacks on computers are increasing at an alarming rate. By the virtue of threats especially viruses, cyber attackers/hackers are now capable enough to launch attacks on numerous computers from any part of the world.
Nowadays, not only major companies and firms are at risk but home-based systems are also not safe from viruses. The danger will always lurk around your system.
In the last few years, many file infector virus, web scripting virus, trojans etc were developed by cyber attackers. Recently, Internet security experts detected a new Chrome.7Z virus infiltrating the computer by adding various malicious elements.
When team HTRI received reports from experts about the existence of the Chrome.7Z virus, we immediately rolled up to get information about this virus at our labs.
It is hard to know the virus location on the computer. And when it infects your PC, the first sign you observe is the slowing down of your computer. Further, if you use some professional software to speed your computer, then nothing improves but gets worse.
What Is Chrome.7Z?
Chrome.7Z is an executable file which has no relation to any of the Windows process. It hides at C:\Program Files and monitors other applications and programs to manipulate their functionality.
The virus automatically runs in the background of your computer and makes it slow and sluggish. In addition to it, adware and browser hijackers are also bundled to it which results in displaying ads, pop-ups and browser redirections.
Since the installation setup hides custom installation mode, malicious threats also download with installers about which users don’t even know. Thus it is recommended to focus on each installation step when downloading freeware from sources on the internet.
We also suggest you to download an antimalware tool against the virus attacks because more than 70% of malicious attacks generates when users unknowingly connect to online infectious servers, domains, web pages and ads.
Is Chrome.7Z Virus a Mining Trojan?
Considering it a little parasite could become a big problem because it secretly attacks to mine CPU. It accesses your personal data, destroys files and leaves them unusable on your hard drive.
Sometimes the inevitable occurrence of malicious ads on your browser disrupts your browsing experience, eventually, install other ad-supported programs that bids for cryptocurrencies.
Your computer is used to mine cryptocurrency on behalf of the hacker.
Rather than avoiding such miners and trojan, download Malware Crusher with one click on the below button. The tools automatically secure your computer both online and offline. Moreover, it easily prevents further downloads of other unwanted and malicious programs.

Once these PUPs are installed into the computer, they pretend to be a legitimate application and aims to collect different information. The data then is used to mine the cryptocurrency when the virus injects javascript code for cryptojacking.
To understand cryptojacking of Chrome. 7Z Trojan, you can refer to this link of Coinhive Malware. It gives you a brief understanding of how a virus works when categorized as cryptomining.
Is it Possible To Remove Chrome.7Z Virus?
Yes, it is! But, it should be noticed that these intrusive threats are not easy to find on the computer. And needs a powerful tool that can work against the threats.
Therefore, a Chrome.7z virus removal guide is necessary. For this, team HTRI has specifically designed a removal process that will work against any kind of virus and other threat variants.
Automatic Preventive Method
The robust technology of a malware tool for the Windows computer acts as a security defender that prevent your system before the virus starts infecting it.
And Malware Crusher is a complete PC protection kit whose different malware removal capabilities makes it a solution for everyone's cybersecurity need.
Following are few of the removal capabilities to stop entry of any malicious threat and helps to remove chrome.7z virus.
- It’s real-time protection feature, performs a deep scan to detects malicious software and persistent threats. Also, identifies suspicious behavior on your computer.
- The Quarantine feature of the tool removes all infected files from your computer. Additionally, keeps a record of all deleted malicious program and allows you to choose important programs to restore at a later time.
- Malware Crusher also creates a shield against Ransomware, Adware, Malware, Browser Hijackers, Viruses, Extensions and Trojans from entering into your system.
- The 24X7 online protective shield works as an anti-exploit technology and blocks the ransomware component before they hold files as a hostage.
- Malware Crusher tirelessly visits all domains, URLs and web pages to secure your online presence from fraudulent entities. Furthermore, the tool detects the vulnerabilities of online fraudulent entities effortlessly.
- Malware Crusher becomes fiercer in detecting keylogging, remote connections and saving your session data from being recorded.
It is a watchful tool that monitors the cyber world constantly, deeply diagnose it and neutralizes all the threats by writing antimalware code. Malware Crusher's 5-minute function is a savior to prevent and fight against the virus!
You must be wondering whether there is no other source or method to fight against the threat.
However, you can follow the below manual removal guide for general purpose use like uninstalling programs, ending task manager process, etc before you use the antimalware removal tool.
Manual Preventive Methods
- Press Ctrl + Shift + ESC together to open Task Manager. Look for suspicious files, right click on it and click End Task.
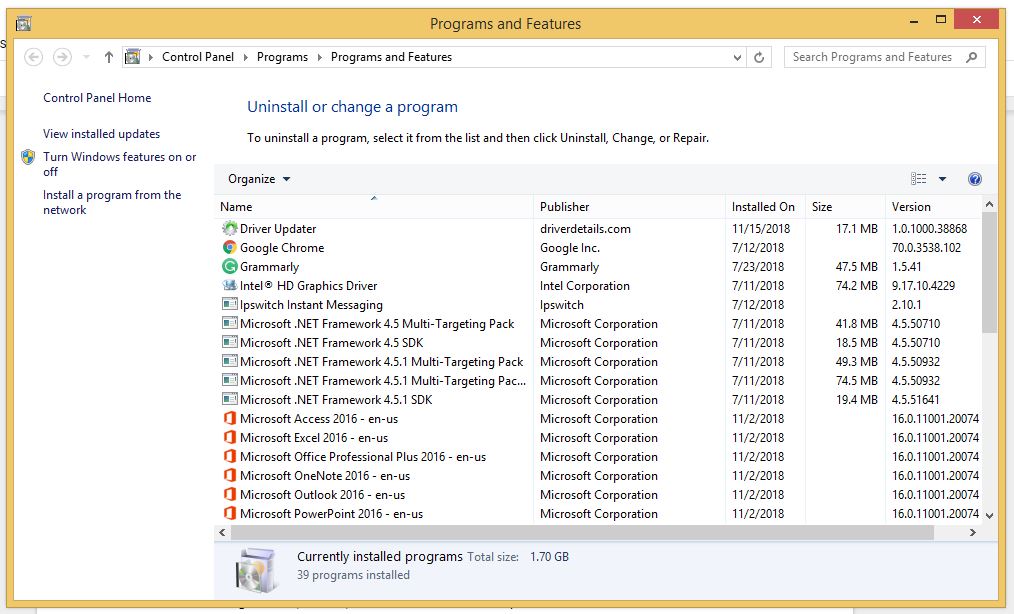
- Now, press Windows key + R to open RUN box window. Type appwiz.cpl on it, this opens Programs and Features window.
- Select each suspicious program and uninstall it one by one. Once the uninstallation is complete, restart your computer and again redirect yourself to Programs and Features window to check whether the application is present or not.
- When convinced, press Windows key + R to open RUN box window. Type regedit on it, hit OK and then click Yes.
- Go through HKEY, HKLM, etc. files and find all suspicious files and delete them.
- Delete unwanted extensions from Chrome and Firefox.
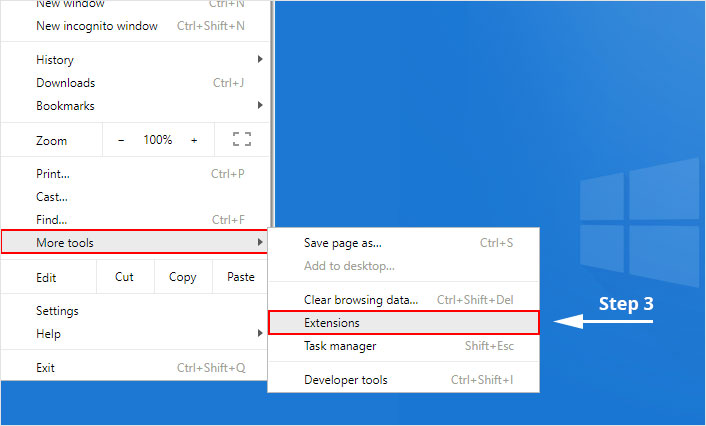
1. Click on the Customize and control menu icon at the top right corner of Google Chrome.
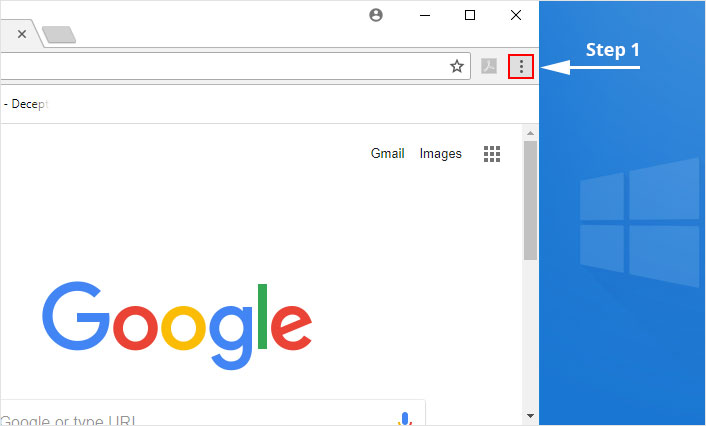
2. Select "More tools" from the menu.
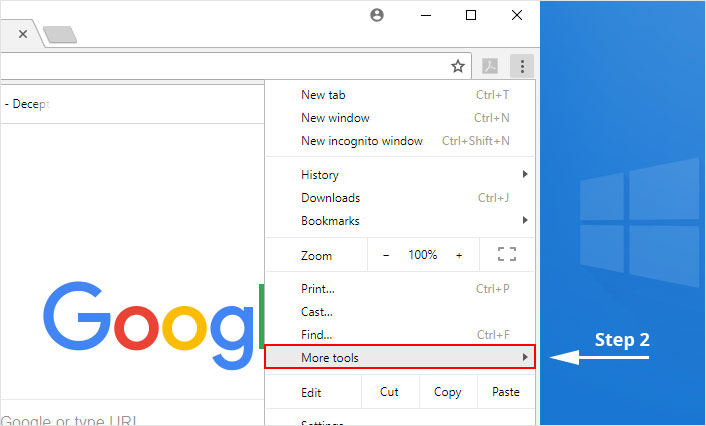
3. Select "Extensions" from the side menu.
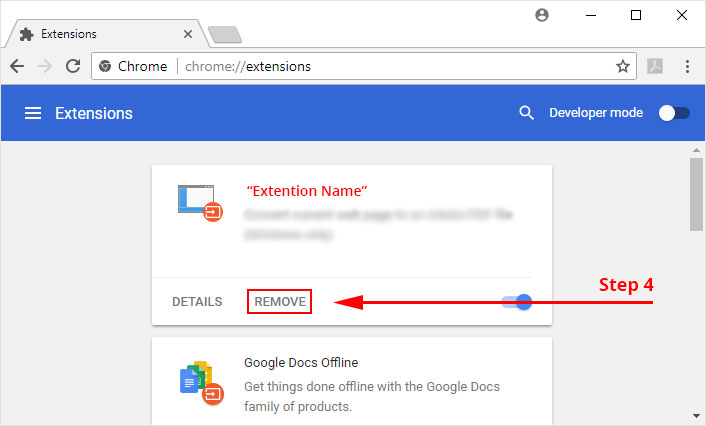
4. Click the remove button next to the extension you wish to remove.
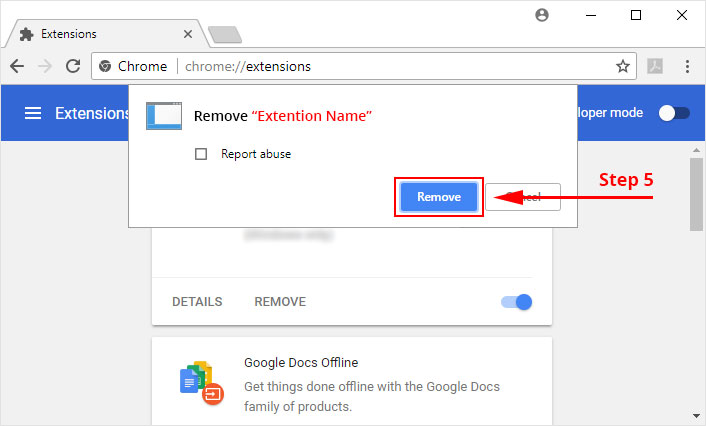
5. It will confirm again, click “remove” and the extension is finally out of the system.
Now that we have successfully eliminated the malicious browser extension, we need to create a robust firewall to avoid any such thing that makes our system and privacy vulnerable to various online threats.
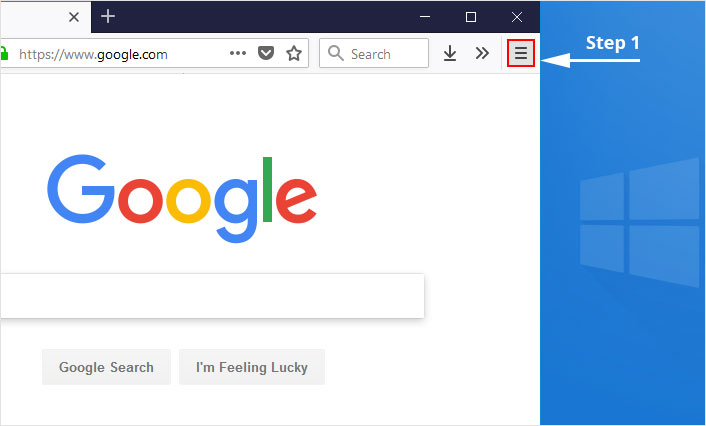
1. Click on the “menu” button at the top right corner.
2. Select “Add-ons” from the menu.
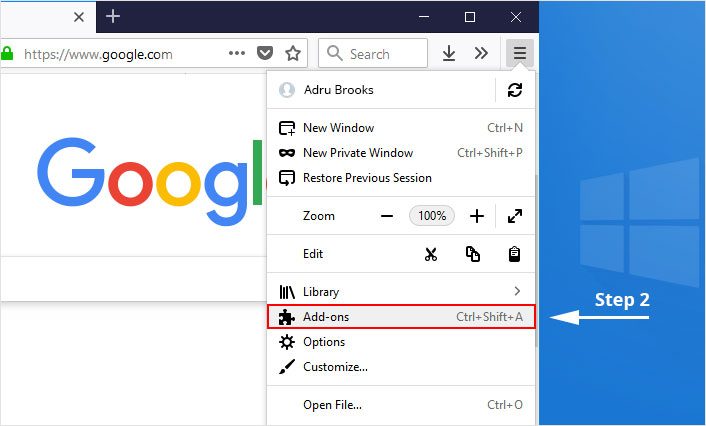
3. Click the “Remove” button next to the extension you wish to get rid of.
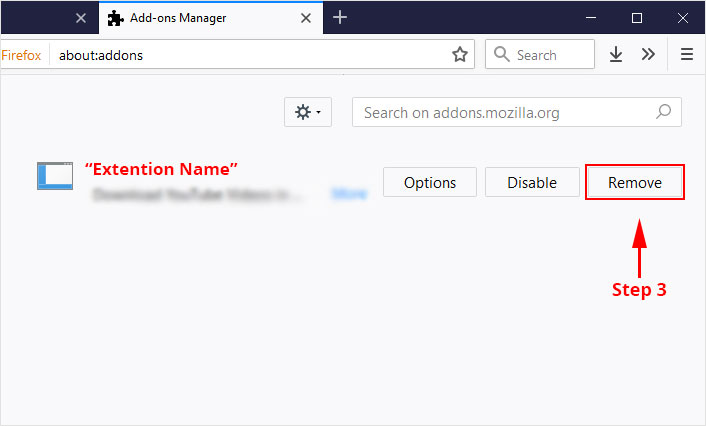
Now that we have successfully eliminated the malicious browser extension, we need to create a robust firewall to avoid any such thing that makes our system and privacy vulnerable to various online threats.
The manual method might not work in some instances at Windows OS because it is difficult to find the suspicious and modified registry files. On the other hand, if you delete some useful file, the windows will not work properly.
That’s why we would highly recommend an automatic tool to prevent virus attacks on your computer.
If you want to get more awareness about the happenings of the cyber world related to attacks and security programs, then keep visiting us to get daily updates and notifications.

Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
